[#thread 🧵] For this 23rd day of #CyberAdvent, we will talk about the LDAP structure and its naming contexts. 🦋 

[#thread 🧵(2/10) ] LDAP is a directory structure (a tree) containing objects with their attributes: 
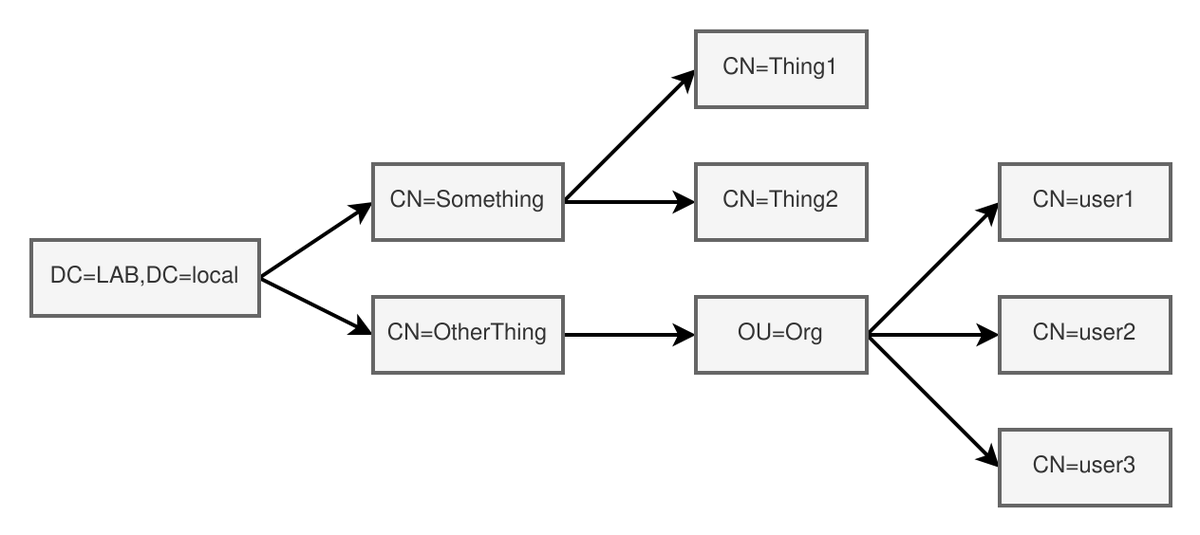
[#thread 🧵(3/10) ] You can search for objects in the LDAP with a query on a specified base object and a search scope. In return, you will then get a list of matching objects with the attributes you selected.
docs.microsoft.com/en-us/windows/…
docs.microsoft.com/en-us/windows/…
[#thread 🧵(4/10) ] There is three values for the search scope, BASE, LEVEL, SUBTREE.
- BASE: Only search in the given object.
- LEVEL: Search in the objects at the same level as the the given object.
- BASE: Search in the subtree of the given object.
- BASE: Only search in the given object.
- LEVEL: Search in the objects at the same level as the the given object.
- BASE: Search in the subtree of the given object.

[#thread 🧵(5/10) ] When I wrote ldap2json, I was trying to export the whole LDAP data all at once, so I decided to use a SUBTREE search on the DC=LAB,DC=local root object of my domain and I got a weird behavior: 

[#thread 🧵(6/10) ] I noticed CN=Configuration,DC=LAB,DC=local did not appear in the results of SUBTREE search on DC=LAB,DC=local. But I could request it directly without problems. Why shouldn't they appear in the results ? Yesterday @cnotin pointed me towards naming contexts. 

[#thread 🧵(7/10) ] The naming contexts (or directory partitions) are independent partitions of data inside the LDAP, hence we cannot find them in a SUBTREE query as we would have to switch partitions to access them.
docs.microsoft.com/en-us/windows/…
docs.microsoft.com/en-us/windows/…
[#thread 🧵(8/10) ] Fortunately, the list of naming contexts is given in the RootDSE object of the LDAP server and returned when we connect to it. I was able to get all of the naming contexts easily from the ldap_server object like this: 

[#thread 🧵(9/10) ] Therefore in order to dump the whole LDAP data, I first needed to execute a query on RootDSE to get the list of naming contexts, and then iterate over the naming contexts to dump the data of each partition: 

[#thread 🧵(10/10) ] I hope this thread has helped you understand the naming contexts! I was really confused about this until @cnotin explained it to me. Many thanks to him 🥳🎉
• • •
Missing some Tweet in this thread? You can try to
force a refresh