In the upcoming #BloodHound 4.1 release, we are introducing 3 new edges. Let me explain why this is actually more impactful than it may sound: 🧵
Let's say you have a basic graph with 3 nodes all connected to each other (this is called a Strongly Connected Graph). We'll call these nodes 1, 2 and 3: 

How many possible paths are there? We can determine that by searching through non-cyclic trees originating from each node. For example, if we start at 1, we can visit 2 then 3, or 3 then 2: 

We need to do this for nodes 2 and 3 as well. Then we can count up the total number of paths, which is 6: 

Here, there are 6 distinct paths (you can count this easily by counting the nodes in the bottom row). Don't forget we must repeat this for each node, so our total number of paths in this graph becomes 24 (6*4): 

Here's what it looks like to explore possible paths from just one originating node:
See the pattern yet? You can calculate the number of possible paths for an SCG of 5 nodes with:
5*4*3*2*1 = 120
This is known as the factorial of 5.
Let's keep going.
5*4*3*2*1 = 120
This is known as the factorial of 5.
Let's keep going.
If we calculate the factorial (number of distinct paths in a strongly connected graph) for up to 10 nodes, our table looks like this: 

How bad can this get? The factorial of 100 is approximately 9.3x10¹⁵⁷.
That number is so big, it's actually larger than the estimated number of particles in the observable universe.
That number is so big, it's actually larger than the estimated number of particles in the observable universe.
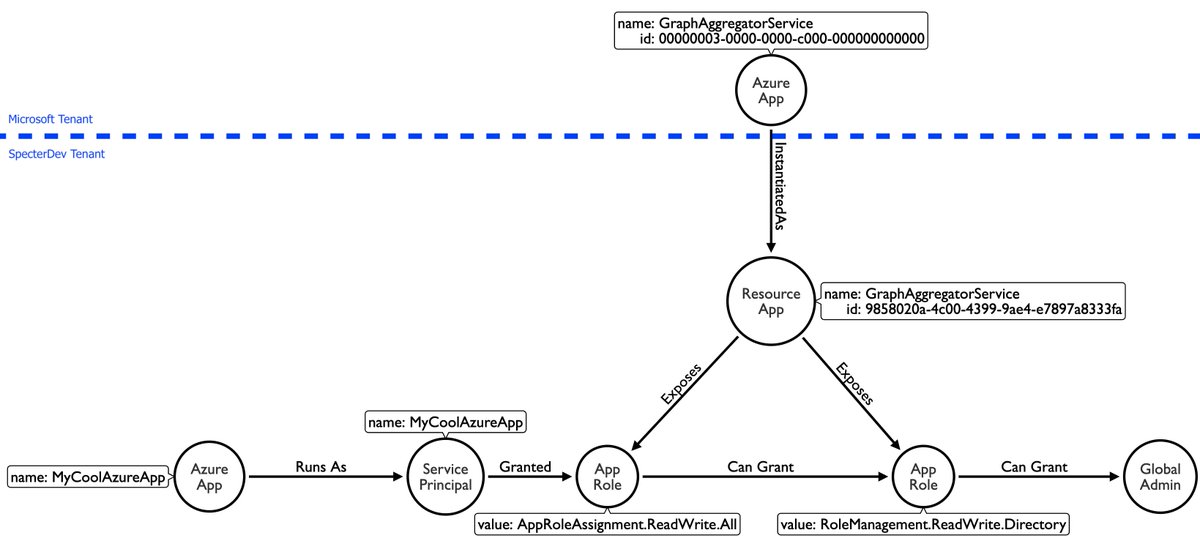
Back to BloodHound. Adding 3 new edge types will in fact introduce an unimaginably high number of new attack paths.
In our DerbyCon talk from 2017, we explained, visually, the impact of adding ACLs into the graph here:
In our DerbyCon talk from 2017, we explained, visually, the impact of adding ACLs into the graph here:
We're adding 3 new edges in 4.1, with several other new types planned for this year. Want to hear about it first? Register for and attend our webinar on February 9th: specterops.zoom.us/webinar/regist…
Correction: [1,3,2,3] should be [1,3,2,4]
[2,3,4] and [2,4,3] should be [2,1,3] and [2,3,1], thanks to @derekmelber for pointing this out!
• • •
Missing some Tweet in this thread? You can try to
force a refresh