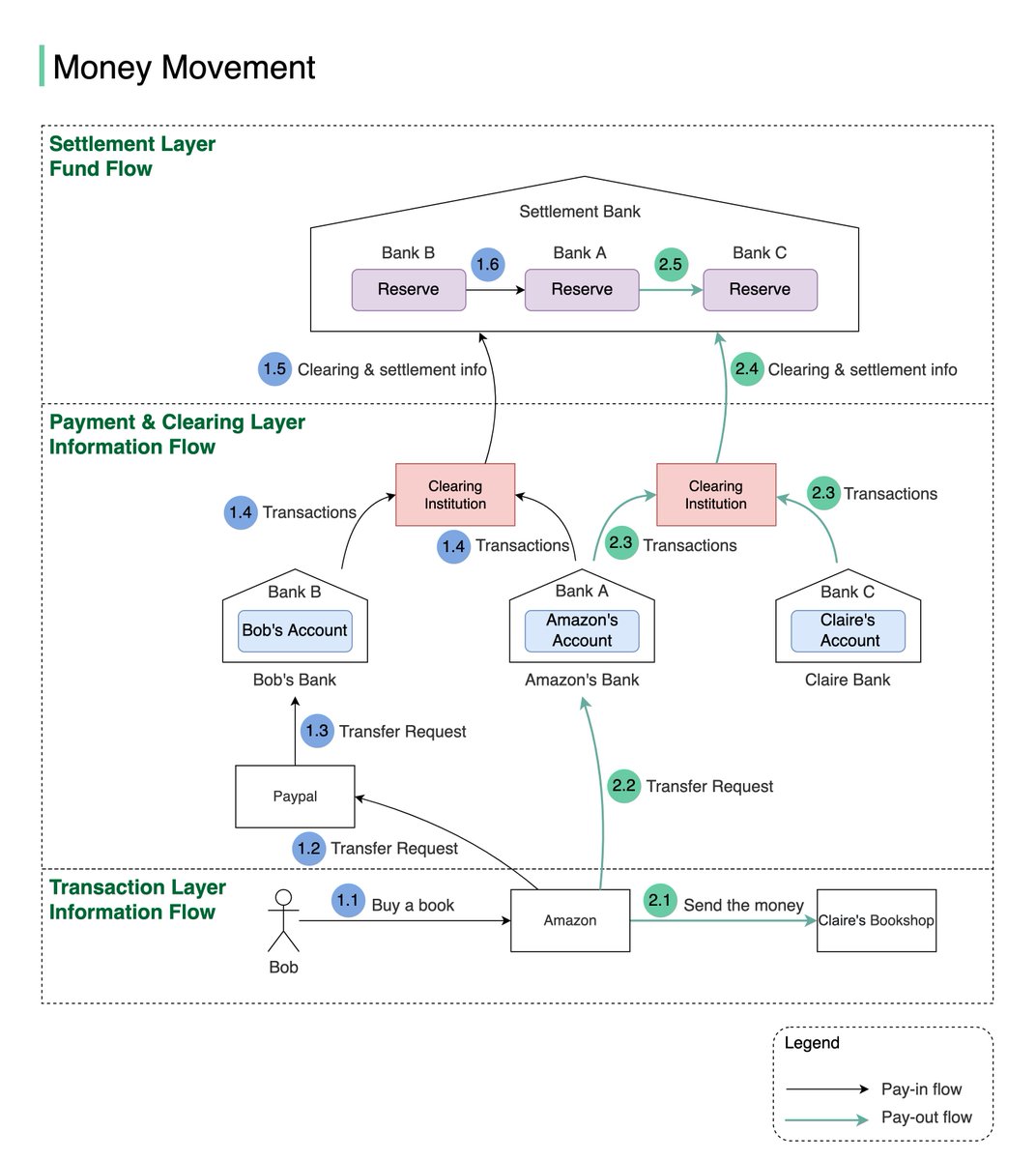
I'm the author of the best-selling book System Design Interview-An Insider’s Guide. 11 days ago, two fraudsters hijacked the "Buy Now" button on Amazon, fulfilling all orders with a different book. I'm helpless to do anything. A sad story on self-publishing: a thread.
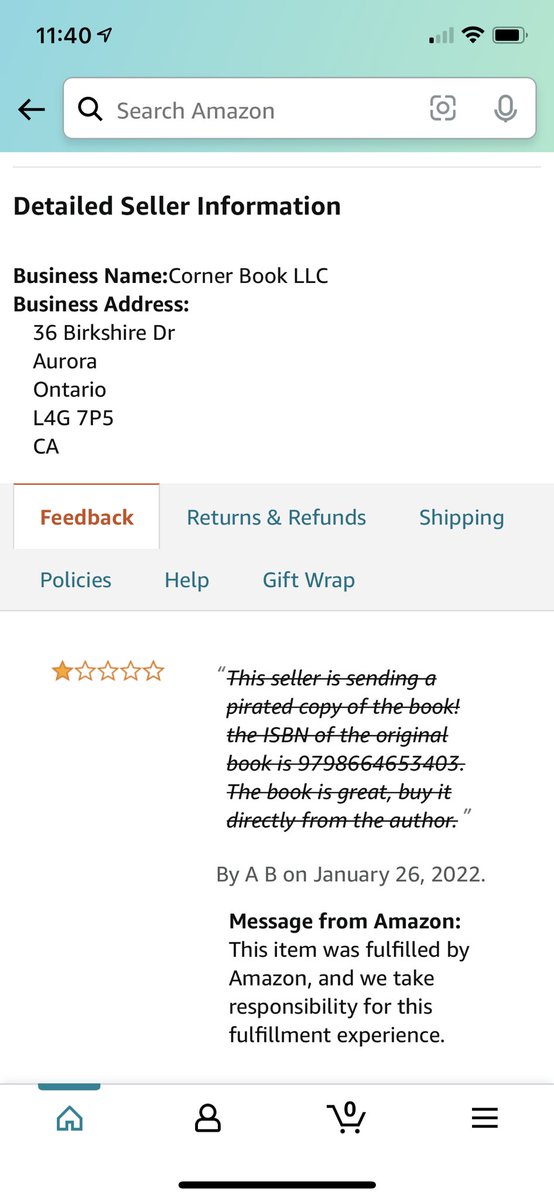
How do I know Amazon fulfills pirated copies? I clicked on the “Buy Now” button and bought them. One had similar content but with a different layout and was printed on inferior quality paper. My book has 309 pages: the pirated one only 276 pages and a completely different ISBN. 



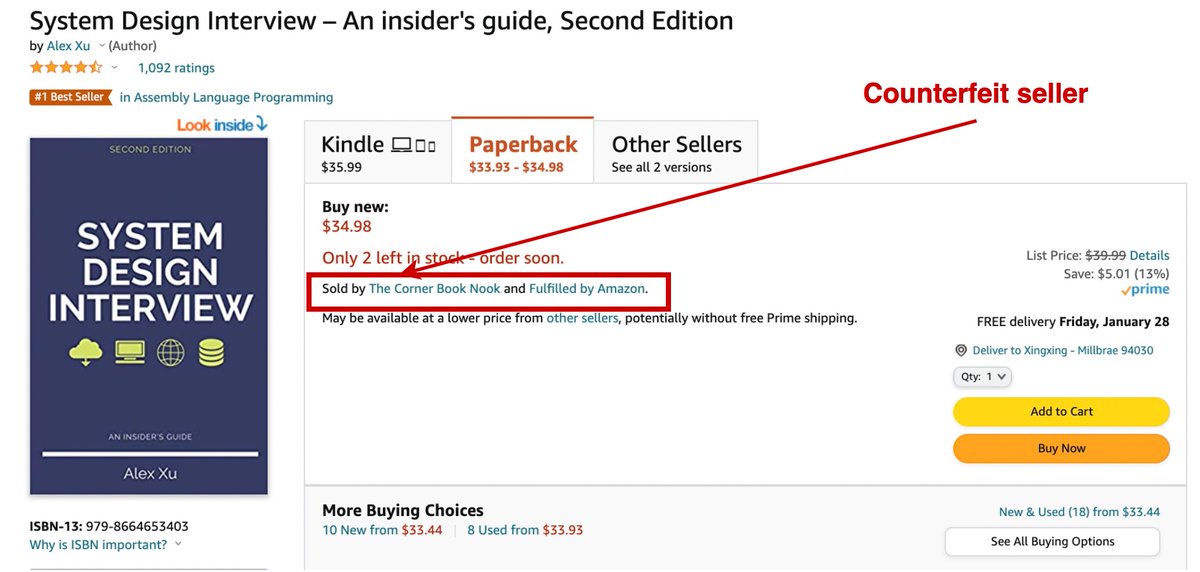


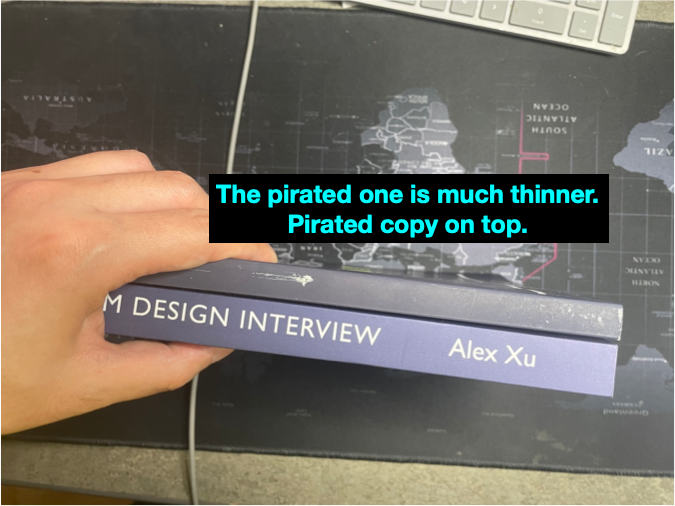
How bad is the issue? I estimate between 60%-80% of the copies sold in the past 11 days are pirated books fulfilled by Amazon. You can see the “Buy Now” button hijacking in action here: amzn.to/3tX4r4b
In what is ironic, I pay for Amazon ads on search pages that result in these scammers fulfilling orders. 
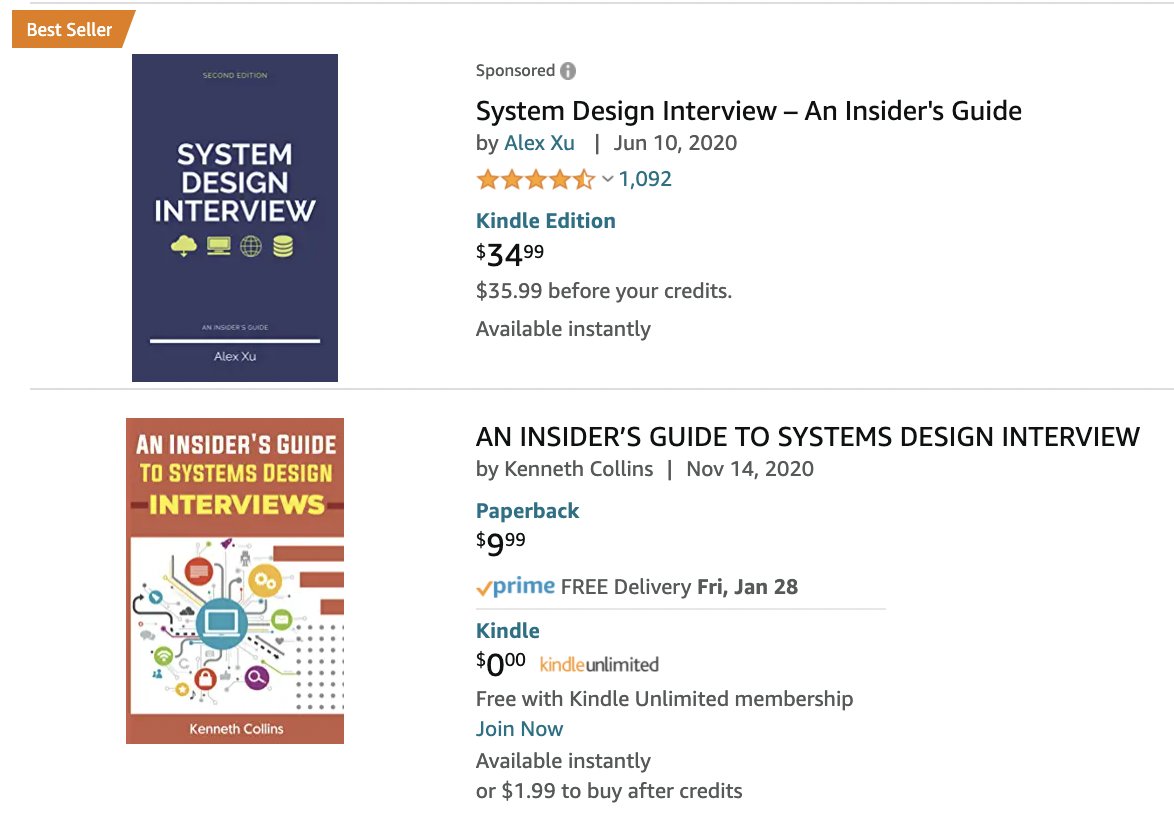
After doing more research, I’ve found this is a very widespread issue for tech books selling above $20. So many fellow authors have complained about it in the past, but Amazon turns a blind eye. Here are some examples, and the story of @ttorres as well. 


https://twitter.com/ttorres/status/1484649055963824131
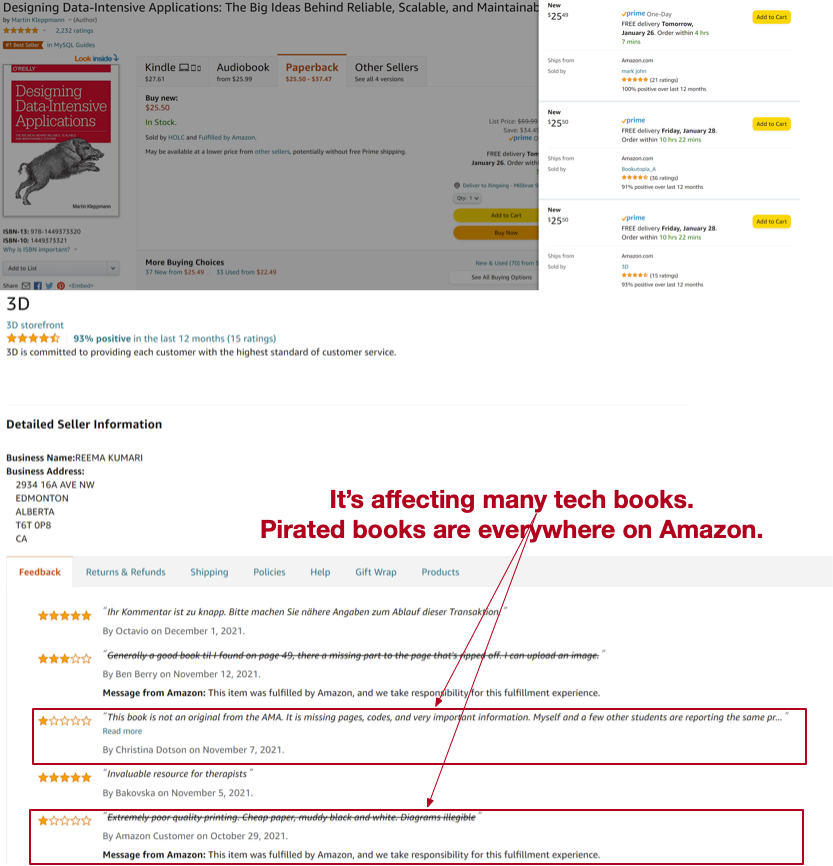
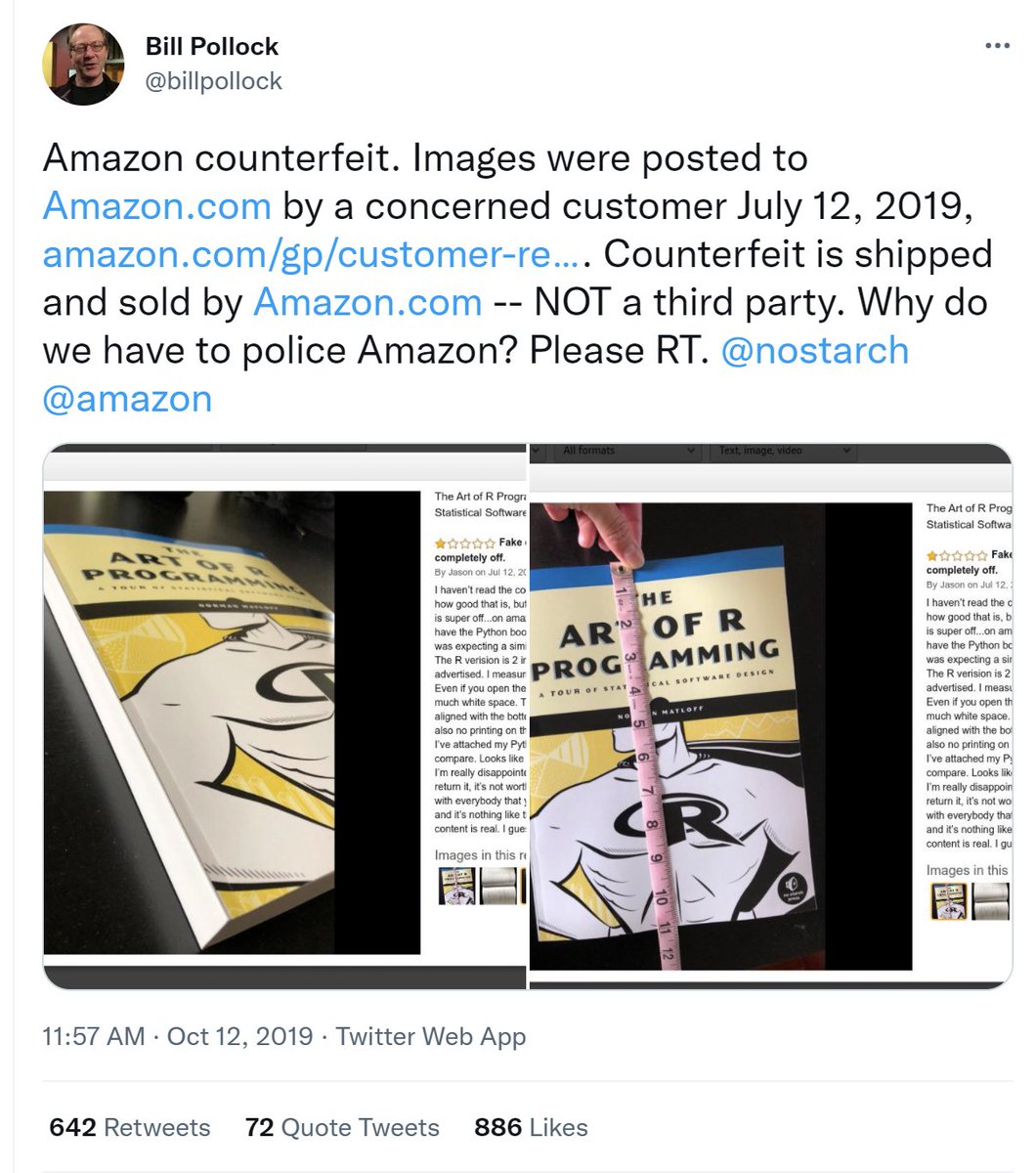
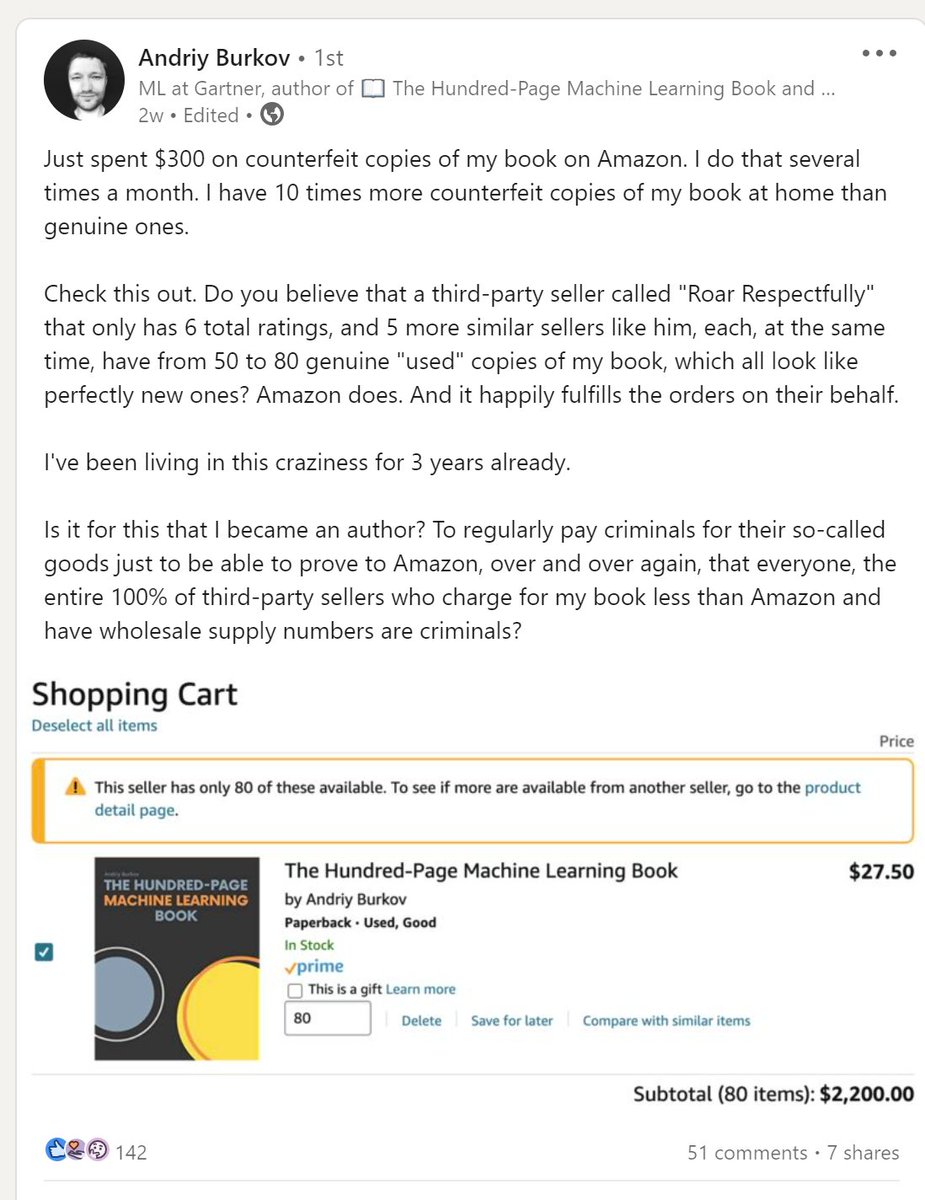
I’ve called Amazon KDP, Author central, Amazon product team but nothing has changed. The scammers are making a profit, while as the author and copyright holder on the books, I can’t do anything. Meanwhile, customers receive knockoffs and often incorrect books.
Being a full-time indie tech author is already hard and Amazon ignoring copyright claims makes our lives even harder. I have a hard time understanding why Amazon turns a blind eye towards this blatant scam so common for so many tech books and tech authors.
Do you have suggestions? Please also help share this as widely as possible. In the meantime, I suggest being VERY careful when buying any paperback tech books on Amazon. Double-check who the seller is. Only buy books sold and fulfilled by Amazon.
I greatly appreciate the overwhelming support after posting this. Some update: Amazon has removed one seller. The other seller sold out their copies for today but is not removed. Hope this can get resolved soon. Thank you all for helping raise awareness of this widespread issue!
• • •
Missing some Tweet in this thread? You can try to
force a refresh