@fastly have been working on building their own Certificate Authority called Certainly. Their request to be included in the Mozilla Root Store was made in Aug last year [1]. Nothing unusual about that, but becoming a new Root CA is a *long* process..
[1] bugzilla.mozilla.org/show_bug.cgi?i…
[1] bugzilla.mozilla.org/show_bug.cgi?i…
I've you've attended our TLS/PKI Training [2], you'll know all about this process, but it will take a few years before the new Root CA is widely trusted.
[2] feistyduck.com/training/pract…
cc: @feistyduck @ivanristic
[2] feistyduck.com/training/pract…
cc: @feistyduck @ivanristic
The first delay is getting approved by all of the Root Stores operators. The second delay is actually distributing the new Root Certificates to all clients via updates. I've talked extensively about this problem in the past! [3][4][5][6]
[3] scotthelme.co.uk/impending-doom…
[4] scotthelme.co.uk/complexities-c…
[5] scotthelme.co.uk/cross-signing-…
[6] scotthelme.co.uk/building-certi…
[4] scotthelme.co.uk/complexities-c…
[5] scotthelme.co.uk/cross-signing-…
[6] scotthelme.co.uk/building-certi…
We know of how much of an issue this can be, specifically the distribution part, thanks to @letsencrypt and their recent deployment [7][8] of their own Root CA Certificates.
[7] scotthelme.co.uk/lets-encrypt-p…
[8] scotthelme.co.uk/lets-encrypts-…
[7] scotthelme.co.uk/lets-encrypt-p…
[8] scotthelme.co.uk/lets-encrypts-…
According to the Certainly CPS [9], we will be getting two new Root CA Certificates. I doubt we will be seeing server certificates issued from these roots and being widely trusted for another few years.
[9] certainly.com/repository/Cer…
[9] certainly.com/repository/Cer…
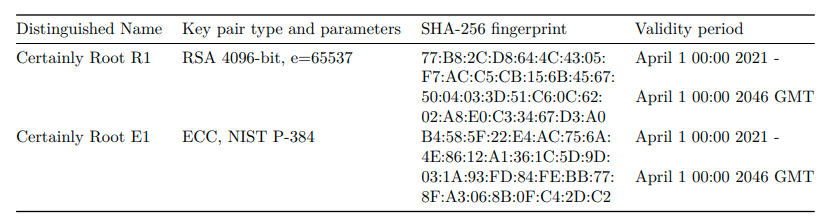
It all sounds very similar to @letsencrypt so far, and it is, but so is the solution to waiting years for your new Root CAs to be widely trusted/distributed. A cross-signature! [10] In an interesting twist, it seems it will be provided by @GoDaddy.
[10] groups.google.com/a/mozilla.org/…
[10] groups.google.com/a/mozilla.org/…
The proposed setup for the new cross-signed Intermediates even looks very similar to the legacy setup of the @letsencrypt cross-signatures from @IdenTrustGov [11].
[11] letsencrypt.org/2020/09/17/new…
[11] letsencrypt.org/2020/09/17/new…

I'm hoping, though, that there won't be the same issues [12][13][14] for Certainly as the Let's Encrypt transition from their cross-signed intermediates to their own intermediates.
[12] scotthelme.co.uk/lets-encrypt-t…
[13] scotthelme.co.uk/lets-encrypt-p…
[14] scotthelme.co.uk/lets-encrypt-r…
[12] scotthelme.co.uk/lets-encrypt-t…
[13] scotthelme.co.uk/lets-encrypt-p…
[14] scotthelme.co.uk/lets-encrypt-r…
This is largely because the Starfield Root CA that @GoDaddy will use for the cross-sign doesn't expire until 2037 [15][16], giving Certainly ~15 years to get their roots approved and distributed.
[15] crt.sh/?id=221795
[16] search.censys.io/certificates/2…
[15] crt.sh/?id=221795
[16] search.censys.io/certificates/2…
Contrast that to @letsencrypt who issued their Root CA in 2015 [17][18] and had their cross-signed intermediates signed by a Root CA expiring in 2021 [19][20]. They only had ~6 years to get their Root approved and distributed, and it didn't go off without a hitch... [21]
[17] search.censys.io/certificates/9…
[18] crt.sh/?q=96bcec06264…
[19] search.censys.io/certificates/0…
[20] crt.sh/?q=0687260331a…
[21] scotthelme.co.uk/lets-encrypt-r…
[18] crt.sh/?q=96bcec06264…
[19] search.censys.io/certificates/0…
[20] crt.sh/?q=0687260331a…
[21] scotthelme.co.uk/lets-encrypt-r…
This means we shouldn't have to worry too much about the Certainly transition from their cross-signed intermediates to their own Root CA in the future as they will have plenty of time, and it should go a little more smoothly than the Let's Encrypt transition did!
One thing I don't know, but I have asked in MDSP [22] and I'm waiting for the comment to be approved, is whether or not Certainly will be a publicly accessible CA or just for use by Fastly customers.
[22] groups.google.com/a/mozilla.org/…
[22] groups.google.com/a/mozilla.org/…
Maybe @fastly could even clarify that here for us? The @GoDaddy announcement of the cross-signatures doesn't exclude the possibility, but it also doesn't confirm it. It would be *awesome* to see yet another free, publicly accessible ACME CA out there!!
@fastly @GoDaddy Certainly is even built on Boulder [23], the CA software that powers Let's Encrypt!
[23] github.com/letsencrypt/bo…
[23] github.com/letsencrypt/bo…

There are currently 3 alternatives to @letsencrypt that I know of who offer free certificates via ACME [24][25][26]. Adding another one would be epic! 🔐🌍💚
[24] scotthelme.co.uk/having-a-backu…
[25] scotthelme.co.uk/introducing-an…
[26] scotthelme.co.uk/heres-another-…
cc: @buypass @zerosslHQ @sslcorp
[24] scotthelme.co.uk/having-a-backu…
[25] scotthelme.co.uk/introducing-an…
[26] scotthelme.co.uk/heres-another-…
cc: @buypass @zerosslHQ @sslcorp
@letsencrypt @buypass @zerosslHQ @sslcorp Update: My comment was approved, let's see what happens! groups.google.com/a/mozilla.org/…
• • •
Missing some Tweet in this thread? You can try to
force a refresh