
Yesterday, the U.S. Treasury Department announced extensive sanctions against Russian businesses and elites following the country’s invasion of Ukraine. This has prompted many to ask Chainalysis how Russia may attempt to use cryptocurrency to evade sanctions.
As is true in traditional finance, some may use crypto for sanctions evasion. But the inherent transparency of blockchains combined with Chainalysis data & tools gives governments and crypto businesses the ability to identify transactions by sanctioned entities and take action.
It’s unlikely that individuals designated in yesterday’s sanctions would move large quantities of crypto now. Russian elites and financial authorities have likely been preparing for sanctions, and would have carried out those transactions slowly over the past few months.
Chainalysis is monitoring for on-chain indicators of crypto-based sanctions evasion by Russian actors. We will alert our partners in government of any relevant activity and provide public updates where possible. So far, on-chain tx vols across the region are stable.
However, exchange order book data reveals one interesting trend. Over the last few days, there’s been a large uptick in transaction volumes for trading pairs involving the Russian ruble and Ukrainian hryvnia (credit @KaikoData). 

Between 2/19 and 2/24, ruble trade pairs’ daily tx volumes have grown 8.6x to $124M USD, while hryvnia volumes have grown 8.2x to $42M. Note: This dataset includes five large exchanges for which @KaikoData offers ruble and hryvnia trade pair data. 

While it’s possible the tx volume represents illicit actors converting funds into cryptocurrency, it could also be driven by individuals in both countries reacting to the recent devaluation of the ruble and hryvnia and attempting to preserve their savings.
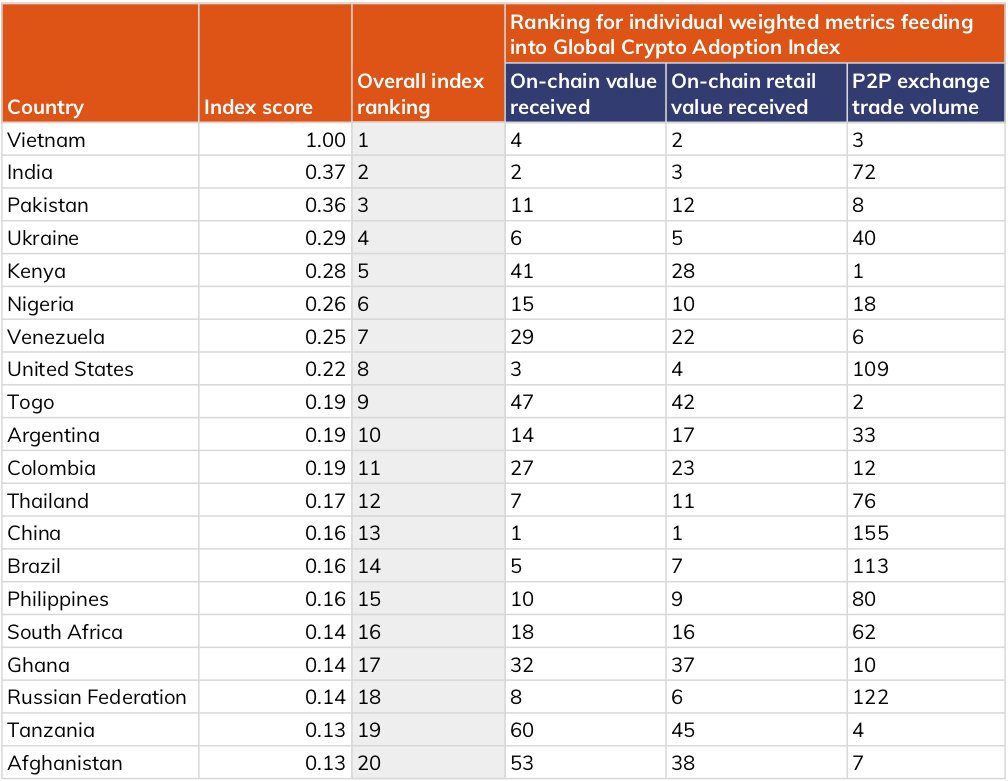
Cryptocurrency adoption and literacy are high in both Ukraine and Russia, as they rank 4th and 18th respectively on Chainalysis’ Global Crypto Adoption Index. We therefore might expect to see citizens turn to crypto in the face of currency devaluation. bit.ly/2XEUHO3 
We’ll also be monitoring the cryptocurrency activity of Russian cybercriminal groups. Already, the prolific ransomware gang #Conti has voiced its intent to support Russia in its war efforts and carry out cyberattacks on enemy states.
https://twitter.com/ddd1ms/status/1497247507474272257
This wouldn’t be a surprising development. In addition to accounting for the majority of ransomware activity, cybercriminal groups allied with the Russian government launched attacks against the Ukrainian government in the weeks leading up to the invasion. bit.ly/3hjK61C
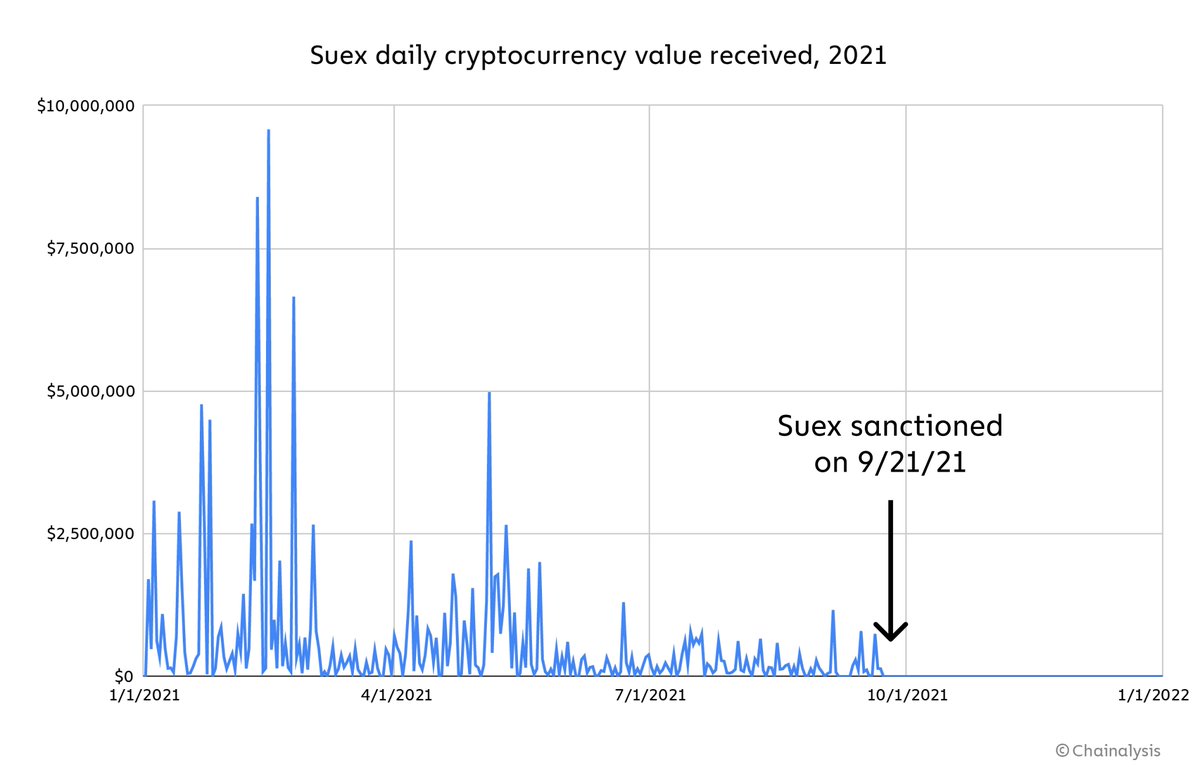
Overall though, we’re optimistic that the cryptocurrency industry can counter attempts by Russian actors to evade sanctions with crypto. Compliance pros have already proven effective in this regard, as we see from the effects of sanctions on Russian crypto businesses like Suex. 
Follow us for more updates on cryptocurrency activity related to Russia’s invasion of Ukraine. You can also download our 2022 Crypto Crime Report for more research on Russian cybercrime, including trends in ransomware and money laundering. bit.ly/3JxuW52
• • •
Missing some Tweet in this thread? You can try to
force a refresh







