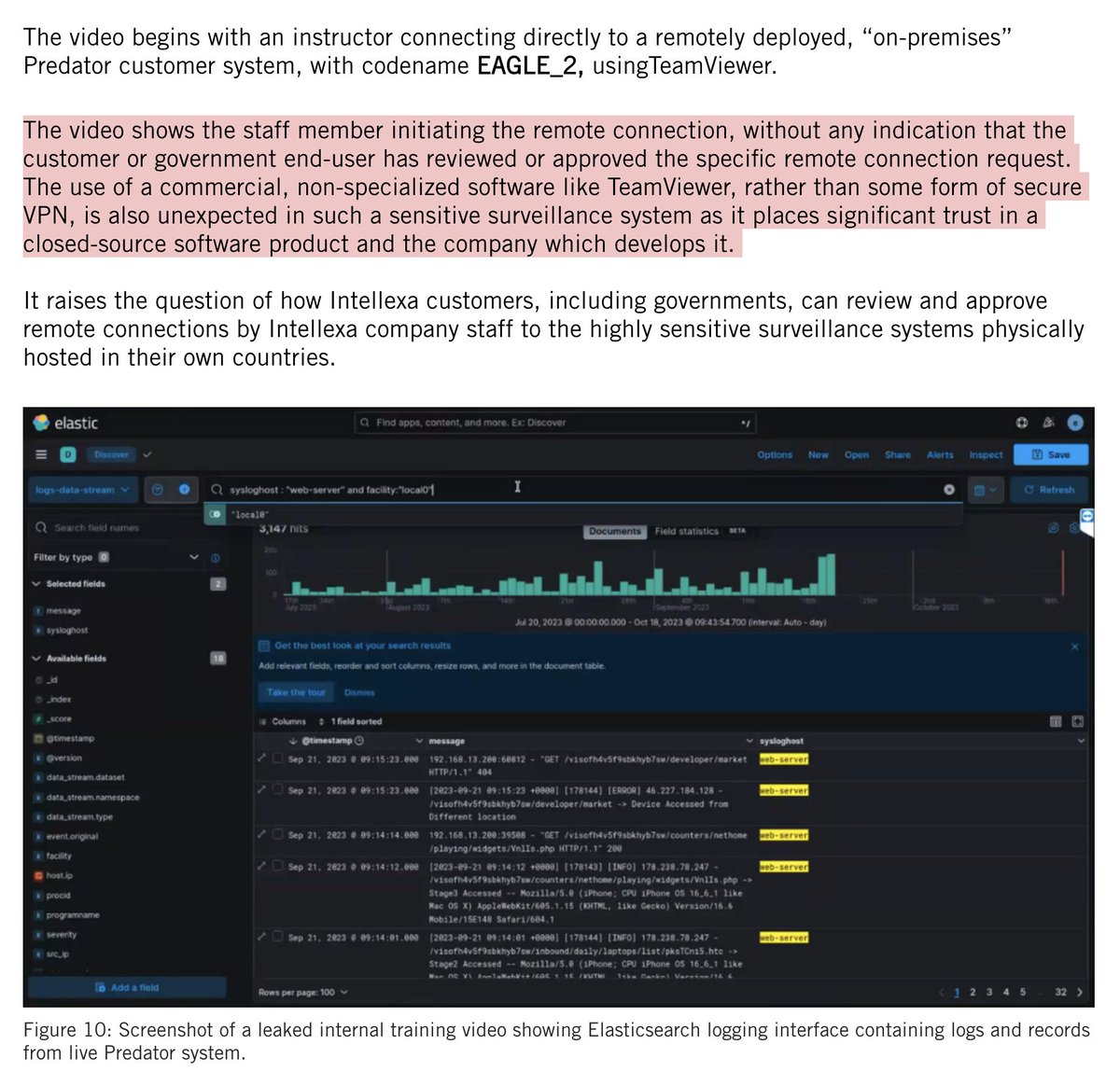
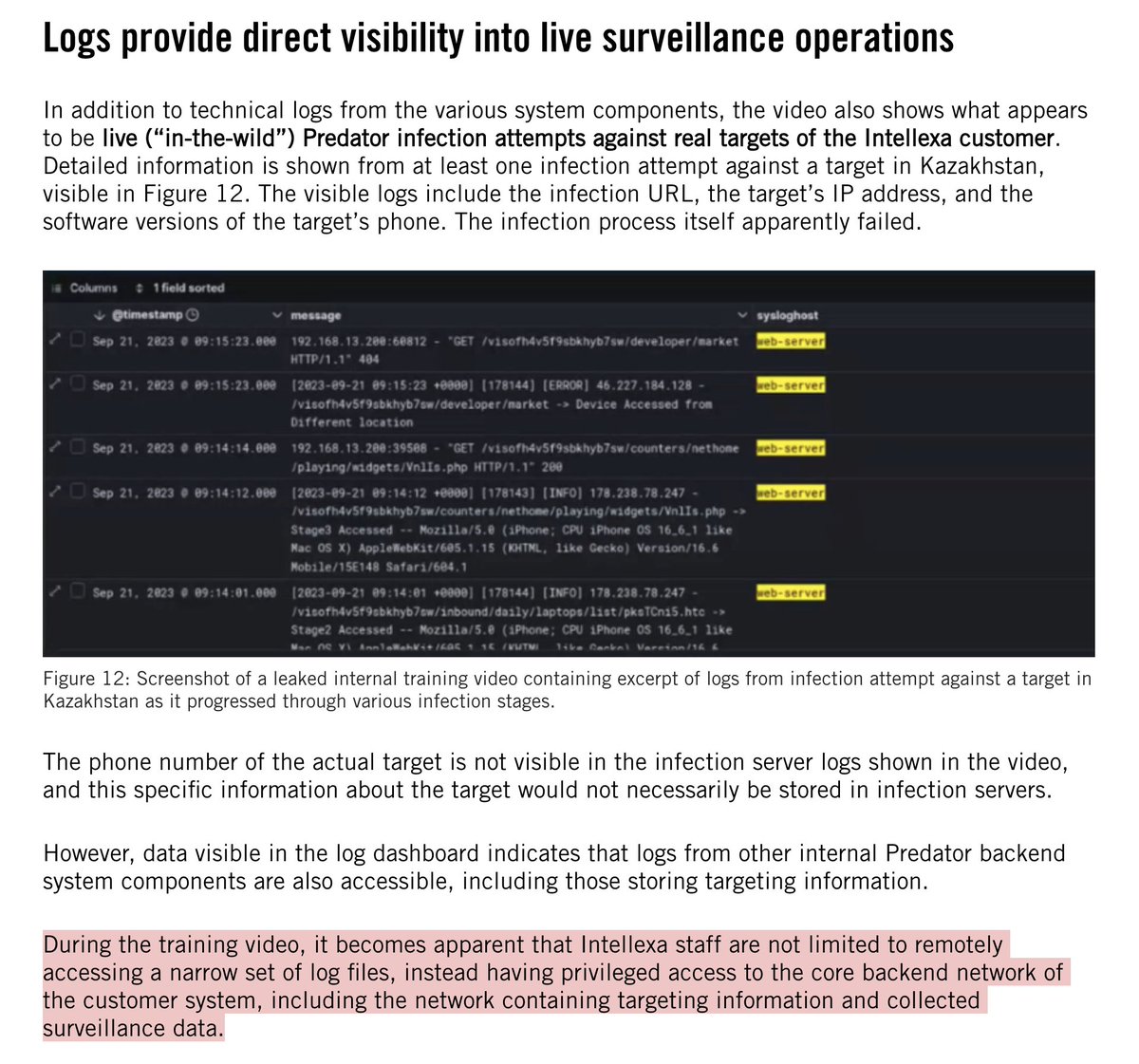
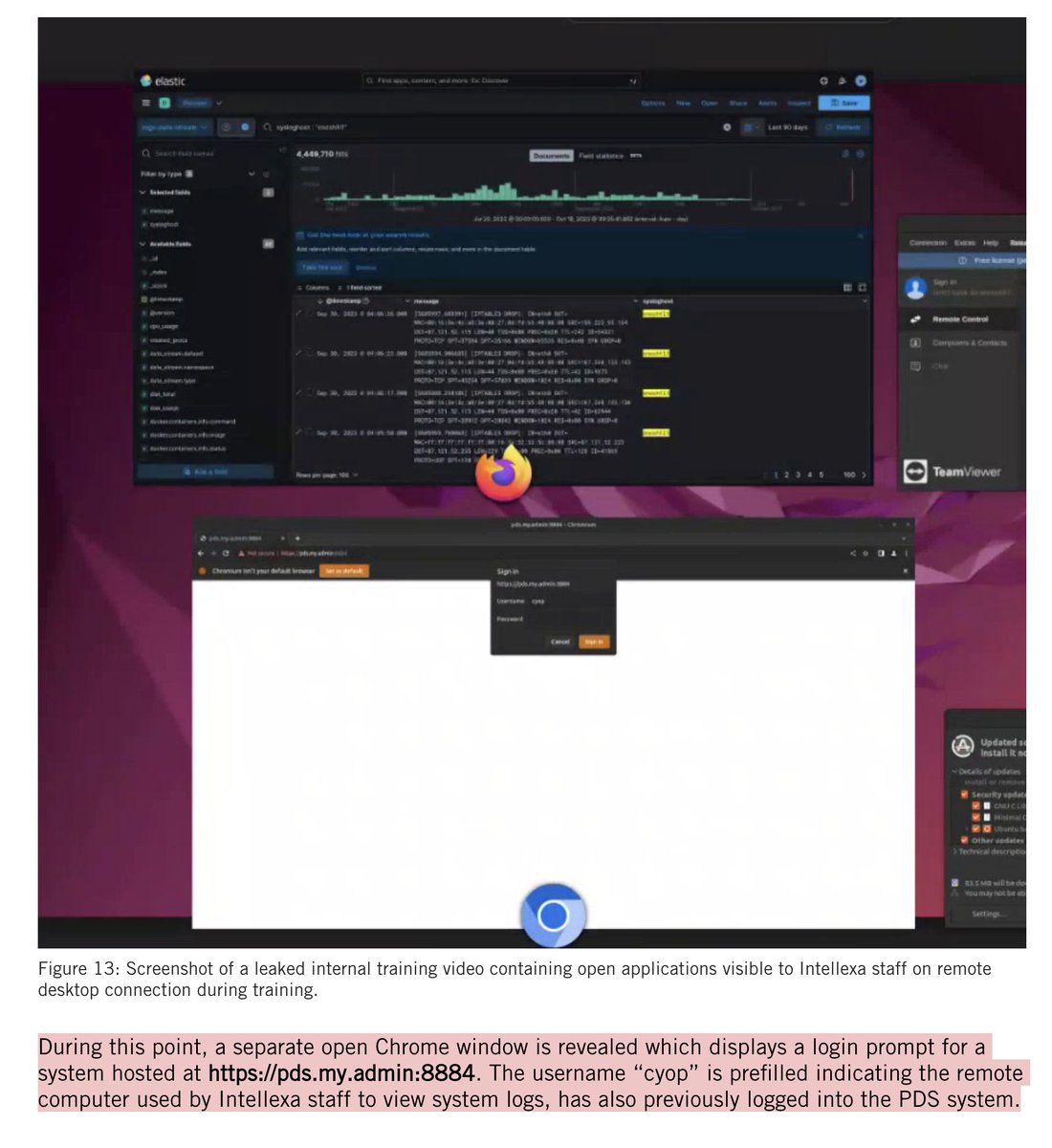
Re: @elonmusk's starlink donation.
Good to see.
But remember: if #Putin controls the air above #Ukraine, users' uplink transmissions become beacons... for airstrikes.
Some background 1/
Good to see.
But remember: if #Putin controls the air above #Ukraine, users' uplink transmissions become beacons... for airstrikes.
Some background 1/
2/ #Russia has decades of experience hitting people by targeting their satellite communications.
In 1996, Chechen president Dzhokhar Dudayev was careful, but Russian aircraft reportedly found his satphone call & killed him with a missile strike.
rferl.org/a/1067831.html
In 1996, Chechen president Dzhokhar Dudayev was careful, but Russian aircraft reportedly found his satphone call & killed him with a missile strike.
rferl.org/a/1067831.html

3/ Satellite phones tend to send signals out in all directions.
Making them easy targets.
The technology for locating & intercepting them is well-honed.
This is different from starlink...

Making them easy targets.
The technology for locating & intercepting them is well-honed.
This is different from starlink...


4/ In more recent years, other kids of tech has entered the conflict-zone game. Like VSATs.
In Syria, Libya, etc etc. VSATs have played a pivotal role in communications. Everyone uses them.
They have a more *directional* signal & typically provide broadband data.
In Syria, Libya, etc etc. VSATs have played a pivotal role in communications. Everyone uses them.
They have a more *directional* signal & typically provide broadband data.

5/ Still, here are various ways to spot, geolocate, & drop a missile on VSAT satellite internet terminals...
...and #Russia has recent battle-tested experience doing just this in Syria, where ISIS, FSA and everyone else has used them.
Pic: random .ru airstrike.
...and #Russia has recent battle-tested experience doing just this in Syria, where ISIS, FSA and everyone else has used them.
Pic: random .ru airstrike.

6/In Syria, ISIS reportedly came up w/ various tactics to avoid being killed by strikes against their satellite internet terminals.
E.g. Distancing dishes from their installations, covertly taking a connection from civilian internet cafes' VSATs, etc..
Deadly cat & mouse.
E.g. Distancing dishes from their installations, covertly taking a connection from civilian internet cafes' VSATs, etc..
Deadly cat & mouse.
7/ Takeaway: early in a conflict w/disrupted internet, satellite internet feels like a savior.
But it quickly introduces *very real, deadly new vulnerabilities*
If you don't understand them, people die needlessly until they learn & adapt.
This has happened again. And again.
But it quickly introduces *very real, deadly new vulnerabilities*
If you don't understand them, people die needlessly until they learn & adapt.
This has happened again. And again.
8/ I've skipped some tech like BGANs, but why should you take anything I say seriously?
Well: I've researched the role & risks of internet & satellite communications during armed conflicts...for a decade.
I'm writing this thread because I see a familiar mistake looming. Again.
Well: I've researched the role & risks of internet & satellite communications during armed conflicts...for a decade.
I'm writing this thread because I see a familiar mistake looming. Again.
9/ Want to read more about connectivity risks in armed conflict?
I wrote this case study to persuade policymakers & militaries to not encourage brave people to paint targets on their backs without knowing the risks.
LINK: digital-commons.usnwc.edu/cgi/viewconten…



I wrote this case study to persuade policymakers & militaries to not encourage brave people to paint targets on their backs without knowing the risks.
LINK: digital-commons.usnwc.edu/cgi/viewconten…




10/ A well-resourced military tracks a massive variety of radio emissions during a war.
Even if capabilities are not initially specced out for a novel new communications protocol, if the transmission is interesting enough / the users worth killing, it will be worked on...
Even if capabilities are not initially specced out for a novel new communications protocol, if the transmission is interesting enough / the users worth killing, it will be worked on...
11/ People asking about tracking cellphones.
Cellphones are a giant-blinking-risk in a conflict zone. They emit a powerful signal that spills in every direction.
Most countries' militaries have suites of capabilities for them, from things in the air...to things in backpacks.
Cellphones are a giant-blinking-risk in a conflict zone. They emit a powerful signal that spills in every direction.
Most countries' militaries have suites of capabilities for them, from things in the air...to things in backpacks.
12/ Every tech should be considered & evaluated.
But if well-meaning people rush an untested-in-war new tech into an active conflict zone like #Ukraine & promote it as "safer"...
They may get people killed.
Russia has big electronic ears.
But if well-meaning people rush an untested-in-war new tech into an active conflict zone like #Ukraine & promote it as "safer"...
They may get people killed.
Russia has big electronic ears.
13/ Remember: encryption doesn't prevent GEOLOCATION based on radio emissions.
A smartphone or satcom user can be on encrypted call, using a VPN, etc. etc. correctly believing that nobody is LISTENING to them... right up until the instant they are nabbed.
A smartphone or satcom user can be on encrypted call, using a VPN, etc. etc. correctly believing that nobody is LISTENING to them... right up until the instant they are nabbed.

14/ Connectivity in #Ukraine is necessary.
Now that Starlink devices are headed into an active conflict zone, though, *possible* risks are about to get battle tested.
I hope that OPSEC is front of mind as decisions are made about terminal distribution, use & placement,
Now that Starlink devices are headed into an active conflict zone, though, *possible* risks are about to get battle tested.
I hope that OPSEC is front of mind as decisions are made about terminal distribution, use & placement,
15/ Speaking of... many correspondents in #Ukraine probably have the usual clutch of satphones & BGANs with them.
Many surely remember the tragic death of Marie Colvin & Rémi Ochlik.
I hope everyone is taking great care.
By @JillianYork & @trevortimm
eff.org/deeplinks/2012…
Many surely remember the tragic death of Marie Colvin & Rémi Ochlik.
I hope everyone is taking great care.
By @JillianYork & @trevortimm
eff.org/deeplinks/2012…

• • •
Missing some Tweet in this thread? You can try to
force a refresh