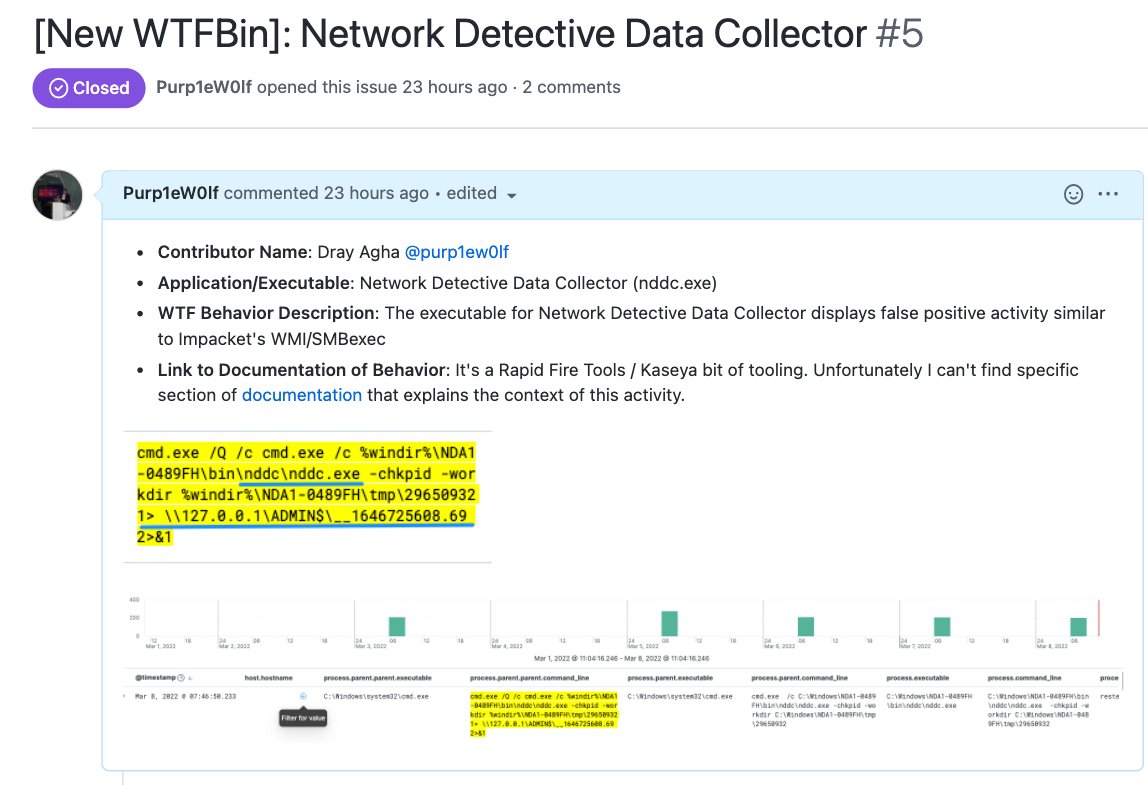
As a security investigator, what are your thoughts when you see this result in your SIEM? 🚨
Bad, right?
Let’s discuss how we can conclude something is a false positive, and what we can do with that information🧵
Bad, right?
Let’s discuss how we can conclude something is a false positive, and what we can do with that information🧵

When drafting some internal docs the other morning, I wanted a screenshot of an Elastic search.
Without intending to start any drama, I searched for a string associated with Impacket's lateral movement tools :
*\\\\127.0.0.1\\ADMIN*
github.com/SecureAuthCorp…
Without intending to start any drama, I searched for a string associated with Impacket's lateral movement tools :
*\\\\127.0.0.1\\ADMIN*
github.com/SecureAuthCorp…

I expected some internal test data, or even results from previously identified activity.
So you can imagine my surprise when I saw results that were from a handful of hours ago
So you can imagine my surprise when I saw results that were from a handful of hours ago

Evidence of lateral movement?! In front of my very eyes!!
So I honed in the host machine in question. The aim here was to contextualise the activity, and identify what other facets of the adversarial campaign were visible
But the results were complicated....
So I honed in the host machine in question. The aim here was to contextualise the activity, and identify what other facets of the adversarial campaign were visible
But the results were complicated....
@HuskyHacksMK later commented on this with the exact mix of emotions I was feeling. 
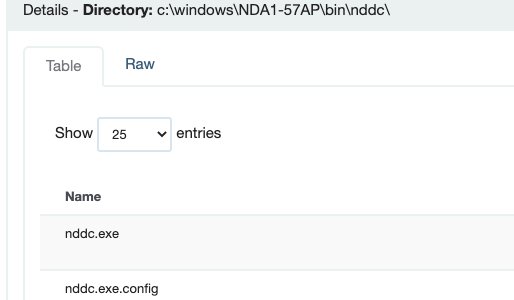
An executable - nddc.exe - was directly associated with this lateral movement-like activity.
Instead of MORE malicious evidence, the existing 'malicious' evidence was brought into question.
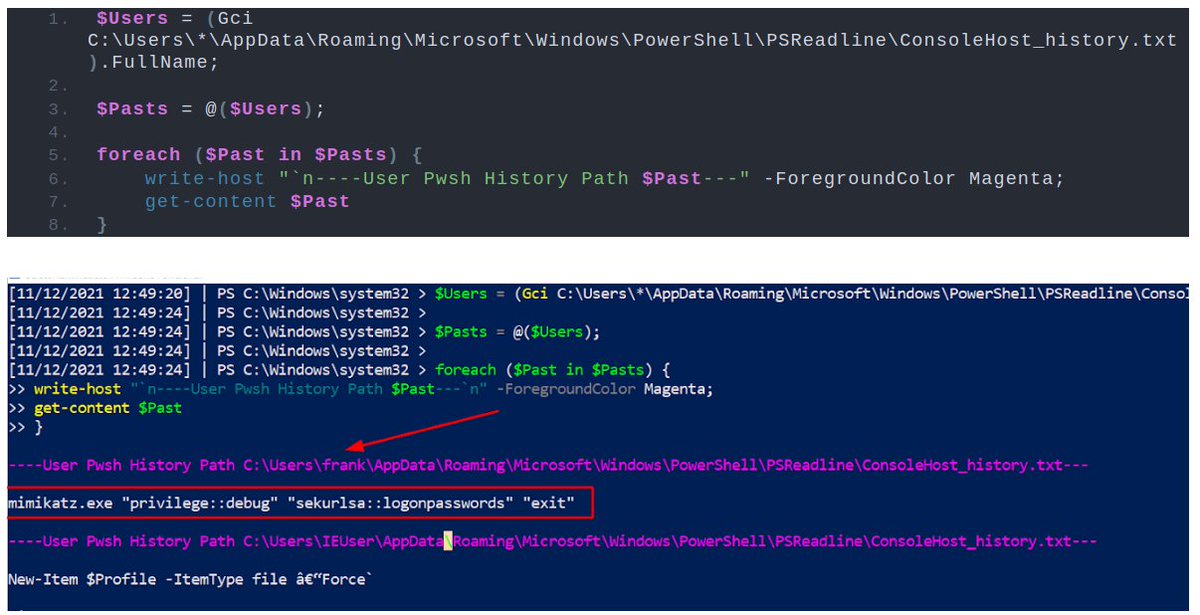
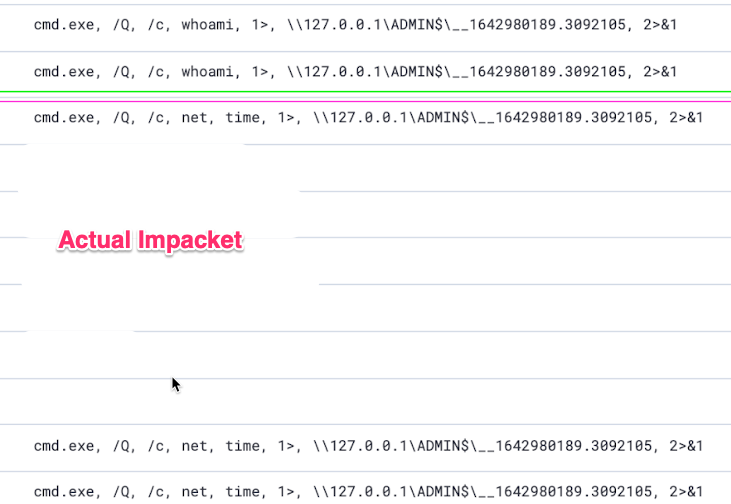
For comparison, I have included what Impacket's WMIExec would look like in the SIEM

Instead of MORE malicious evidence, the existing 'malicious' evidence was brought into question.
For comparison, I have included what Impacket's WMIExec would look like in the SIEM

My next step was to go the host itself. Initially, I was going to reverse engineer the executable under the assumption it was malicious.
But something felt 'off' about treating it like malware.
It seemed too legit in it's directory placement
But something felt 'off' about treating it like malware.
It seemed too legit in it's directory placement
Some like to turn to Google straight away. This is a valid approach
Before I go down search tunnels, I let the 'data speak'. This means I do not impose a hypothesis or conclusion but let the evidence guide me.
Google will add context, but it will not let YOUR data speak. 📢
Before I go down search tunnels, I let the 'data speak'. This means I do not impose a hypothesis or conclusion but let the evidence guide me.
Google will add context, but it will not let YOUR data speak. 📢
Instead, I leveraged global prevalence as @MaxRogers5 would advise.
If a significant number of machines display the same behaviour, this is an informative finding.
And we got back fascinating results: other machines in other domains are also displaying this behaviour, uniformly

If a significant number of machines display the same behaviour, this is an informative finding.
And we got back fascinating results: other machines in other domains are also displaying this behaviour, uniformly
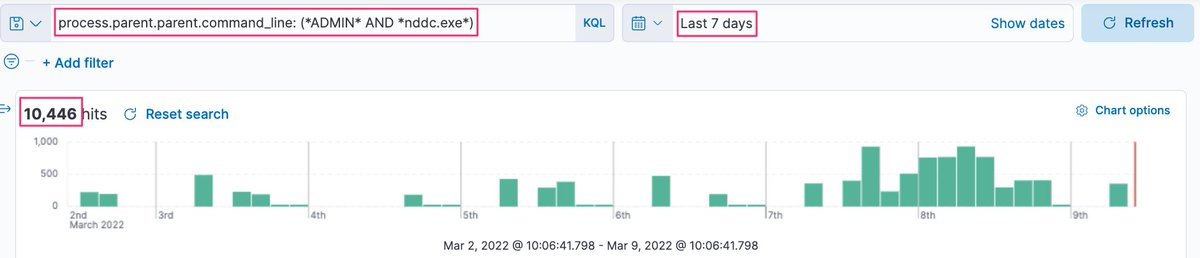
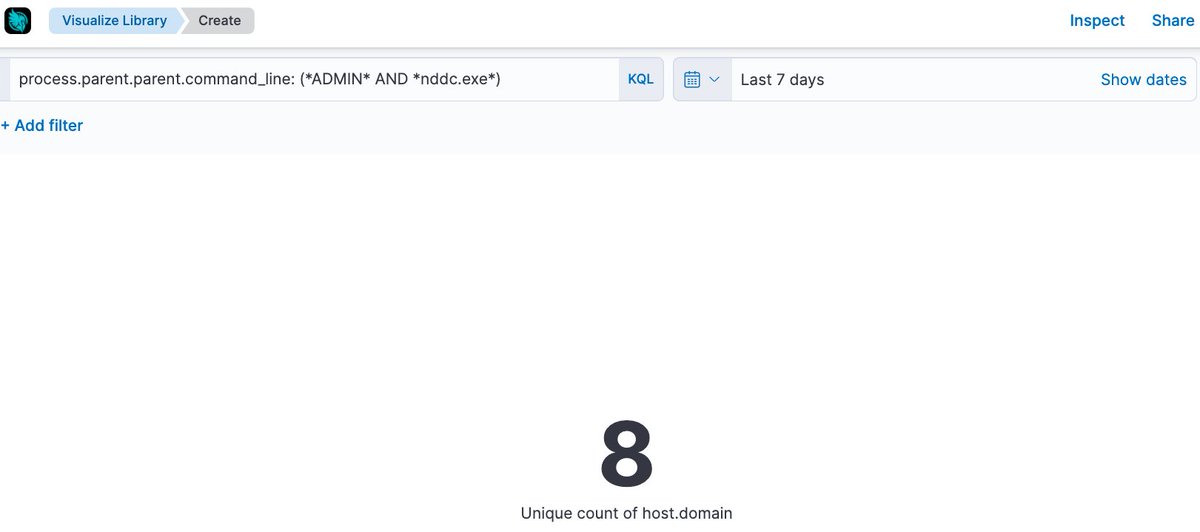
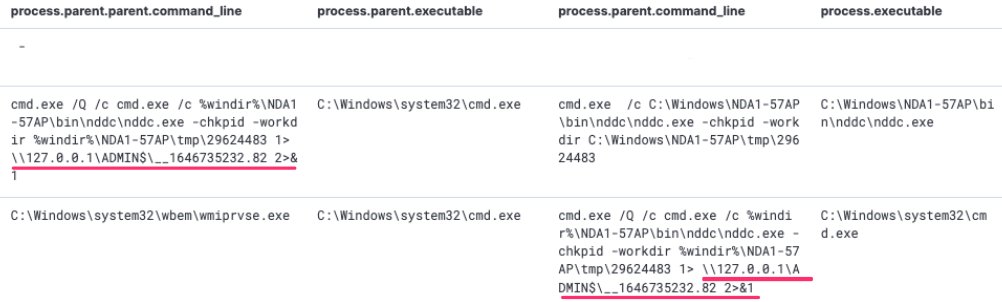
Drilling down further on a machine, we can see that this weird NDDC.exe activity also has a ‘beaconing’ pattern, which suggests it is scheduled with precise regularity 
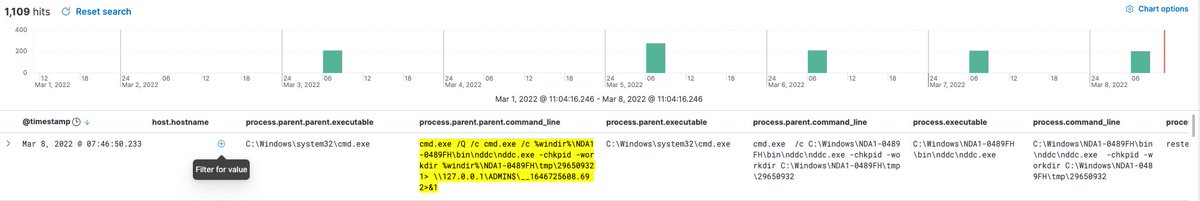
Once I've saturated the raw data and it can't tell me any more, I turn to google to fill in the gaps.
My initial searches were just to ascertain what NDDC is.
I find out its Network Detective Data Collector, a Kaseya-related tool.
This by itself doesn't absolve the activity.


My initial searches were just to ascertain what NDDC is.
I find out its Network Detective Data Collector, a Kaseya-related tool.
This by itself doesn't absolve the activity.
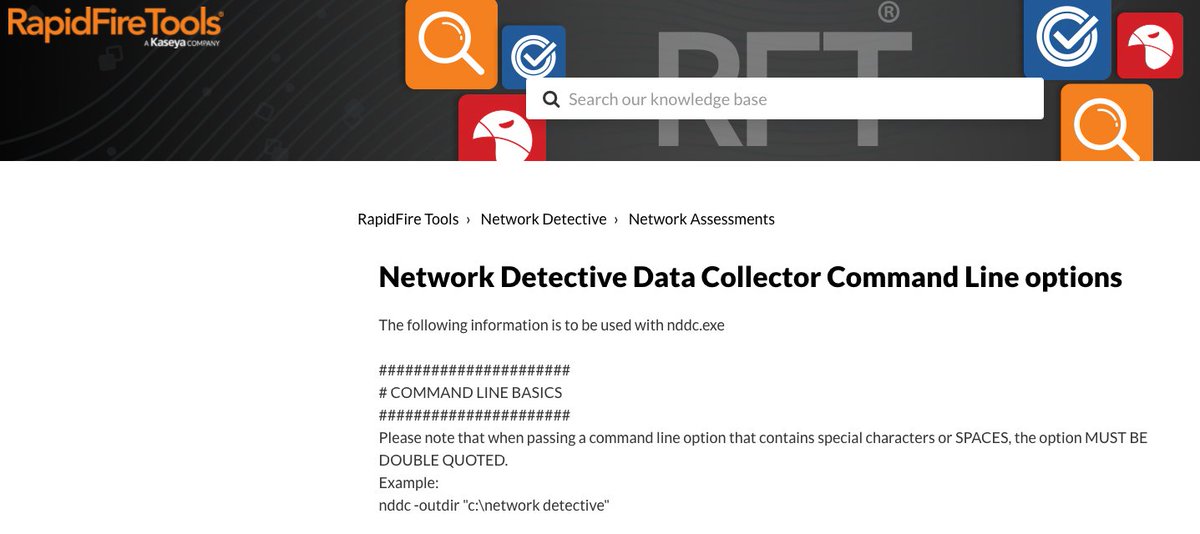
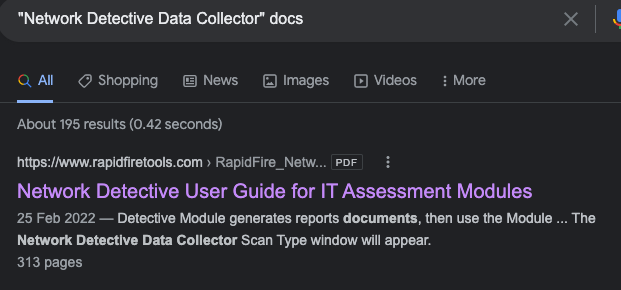
Reading the docs justifies why Network Detective (nddc.exe) behaves this way with SMB shares during a network audit.
It doesn't really explain HOW though.
rapidfiretools.com/nd/RapidFire_N…

It doesn't really explain HOW though.
rapidfiretools.com/nd/RapidFire_N…

The hypothesis and objectives you start with in an investigation may morph as time goes on 🥼⏳
Our investigation changed from focusing on activity that looked like Impacket's WMIexec to focusing on Network Detective's auditing practices.
Our investigation changed from focusing on activity that looked like Impacket's WMIexec to focusing on Network Detective's auditing practices.
Others had run malware analysis on nddc.exe, but no one had yet documented this false positive.
Remember I mentioned how I don't turn to Google first?
This isn't to flex.
It's just that I know for obscure and weird shit, Google won't help me as much as the raw data will.


Remember I mentioned how I don't turn to Google first?
This isn't to flex.
It's just that I know for obscure and weird shit, Google won't help me as much as the raw data will.
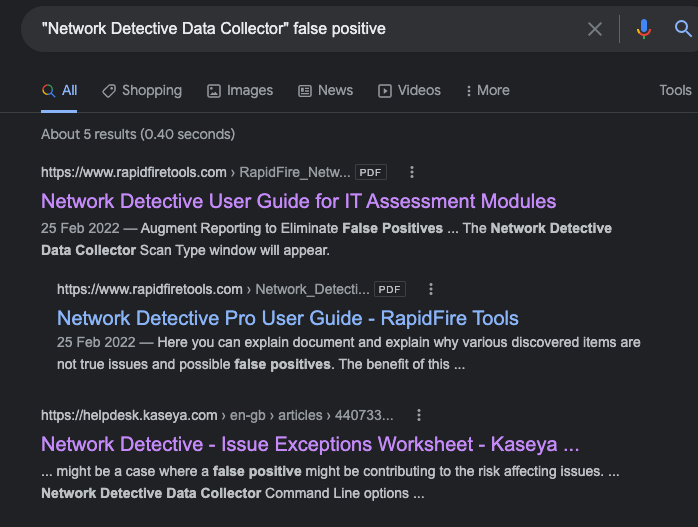
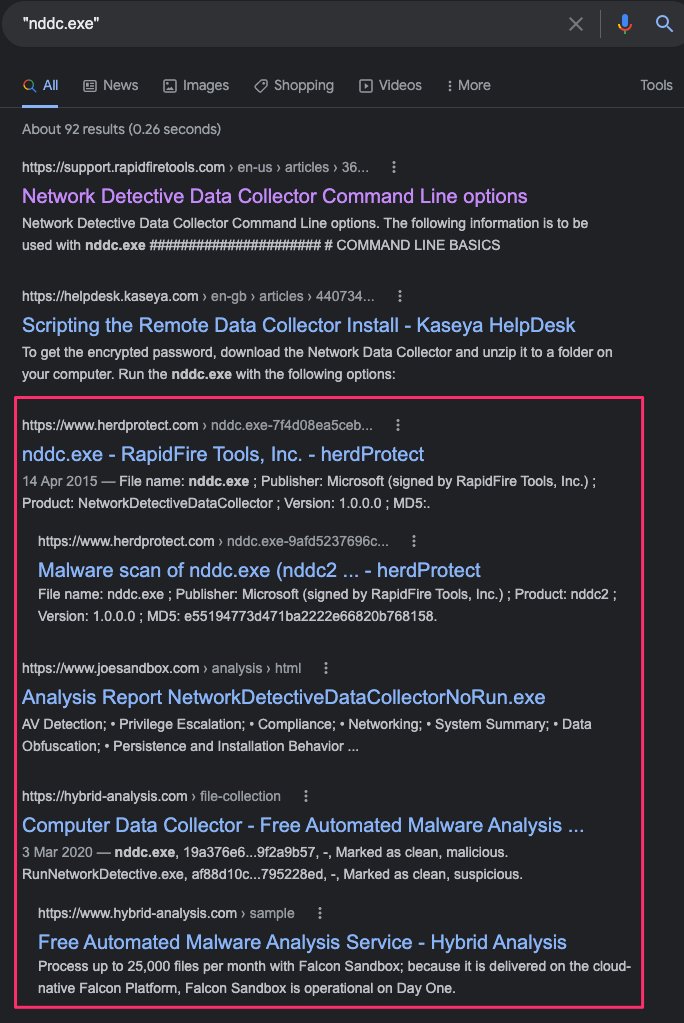
Network Detective's activity was a false positive; similar to Impacket’s lateral movement but not malicious
Lets document and share our novel findings about this false positive.
@mttaggart's WTFBins is an excellent resource we can contribute to: wtfbins.wtf
Lets document and share our novel findings about this false positive.
@mttaggart's WTFBins is an excellent resource we can contribute to: wtfbins.wtf
And the end result of our investigation was to contribute to an awesome, growing repo of false positive behaviours. 
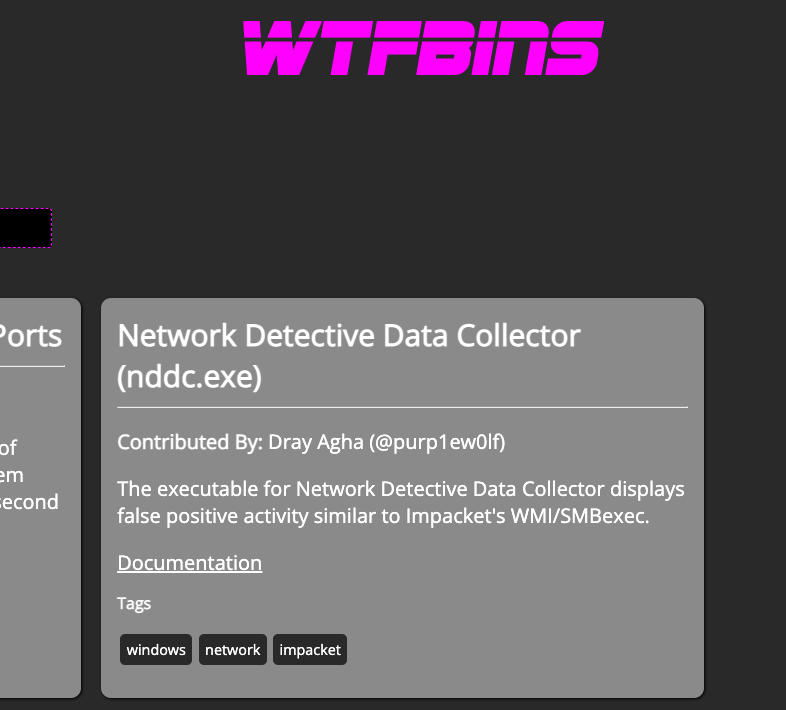
The efforts of our investigation on Network Detective mean the infosec community may not have to go to these lengths next time.
Instead, they can benefit from our findings! 🤝
This is what it's all about: contributing back to the community that we all borrow tools and tips from
Instead, they can benefit from our findings! 🤝
This is what it's all about: contributing back to the community that we all borrow tools and tips from

In conclusion, we pulled on a suspicious thread that we ultimately unraveled as legitimate (but weird), and shared our findings with our peers via WTFbins.
I hope this thread proves useful!
I can't wait to see @mttaggart's WTFbins grow!
I hope this thread proves useful!
I can't wait to see @mttaggart's WTFbins grow!
https://twitter.com/mttaggart/status/1501347849434324995?s=20&t=6ueZjdiomf0E0AmvPS2frw
• • •
Missing some Tweet in this thread? You can try to
force a refresh