Given the sanctions against Russia, it seems that CAs are now ceasing issuance for Russian domains and even going so far as to revoke certificates previously issued for Russian domains. Here are some for a Russian bank revoked by Thawte CA: crt.sh/?id=5828347935
Several others have been reported:
crt.sh/?id=5828347935
crt.sh/?id=6218871547
crt.sh/?id=4582341817
crt.sh/?id=2713661323
crt.sh/?id=5828347935
crt.sh/?id=6218871547
crt.sh/?id=4582341817
crt.sh/?id=2713661323
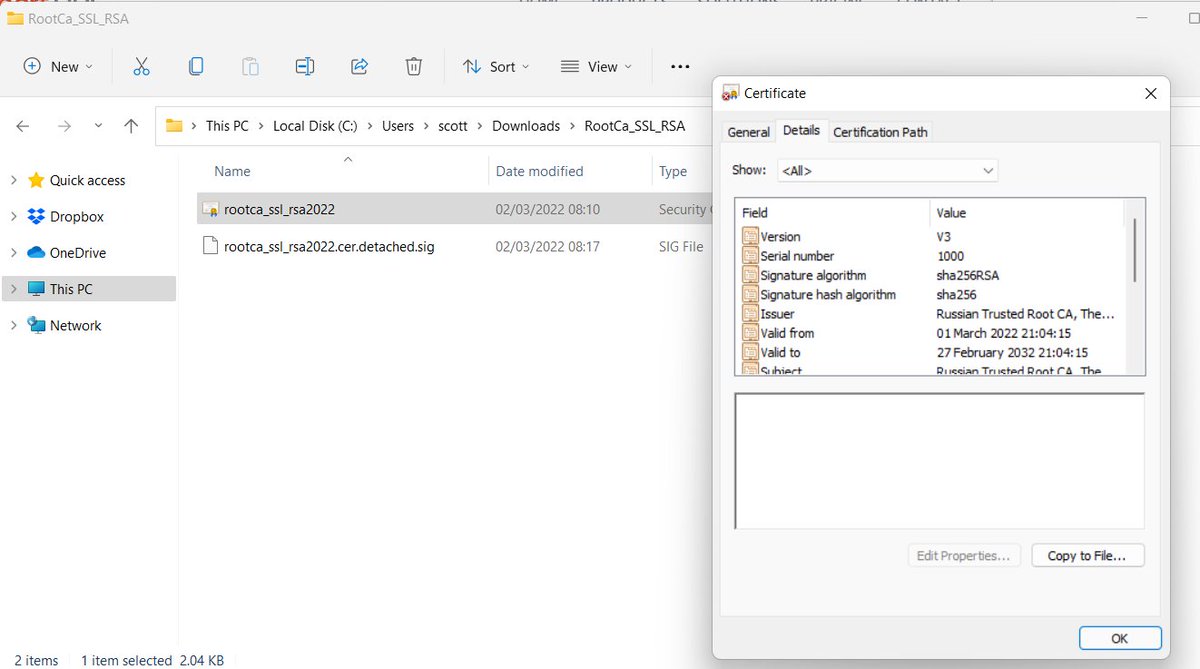
This is of course problematic because websites still need certificates and they have to come from somewhere. It seems now that Russia intends to setup a government operated CA. You can download the Root Certificate at the 3rd button here: gosuslugi.ru/tls
The Root CA doesn't have any name constraints which means it's capable of issuing certificates for any domain that exists, not just Russian domains. This has raised the concern that it could be used to intercept and decrypt the traffic of Russian citizens. pastebin.com/1fxQXTuc
There's a bug on Bugzilla and a discussion on MDSP already:
bugzilla.mozilla.org/show_bug.cgi?i…
groups.google.com/a/mozilla.org/…
bugzilla.mozilla.org/show_bug.cgi?i…
groups.google.com/a/mozilla.org/…
On a technical level, this wouldn't be any different from the efforts by the Kazakhstan government to intercept and decrypt the traffic of citizens in 2019 and again in 2020:
blog.mozilla.org/netpolicy/2020…
blog.mozilla.org/netpolicy/2020…
I've found several examples of Let's Encrypt certificates issued to Russian sites that are revoked, but there's no indication of whether this is related to sanctions or not just yet. No statement from LE.
search.censys.io/certificates/2…
search.censys.io/certificates/9…
search.censys.io/certificates/c…
search.censys.io/certificates/2…
search.censys.io/certificates/9…
search.censys.io/certificates/c…
• • •
Missing some Tweet in this thread? You can try to
force a refresh