Real-World #PingCastle Finding #8: Non-admin users can add computers to a domain. A customer called us because he discovered two new computer objects. Such new computer objects can be a sign of more targeted attacks against the #ActiveDirectory.
1/8
#CyberSecurity #dfir
1/8
#CyberSecurity #dfir

The computer names are relatively unique, and one quickly finds a GitHub repository with corresponding exploit code.
The code tries to exploit the two vulnerabilities CVE-2021-42278 and CVE-2021-42287 (from an authenticated user directly to DA).
2/8
github.com/WazeHell/sam-t…
The code tries to exploit the two vulnerabilities CVE-2021-42278 and CVE-2021-42287 (from an authenticated user directly to DA).
2/8
github.com/WazeHell/sam-t…

Inside the exploit code, a new computer name is generated following the pattern SAMTHEADMIN-(random number from 1 to 100), precisely the naming scheme we see in the client's AD.
3/8
3/8

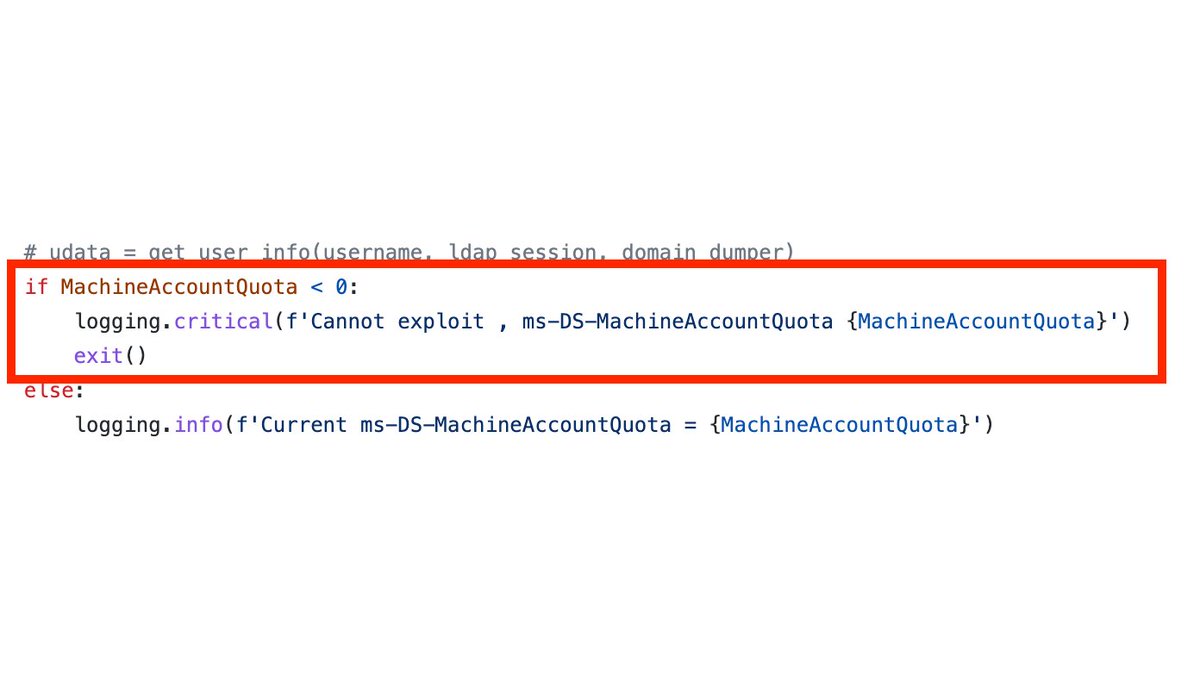
Ping Castle also checks the value of MachineAccountQuota, and outputs a corresponding finding if the value is < 0.
"This default configuration represents a security issue as regular users shouldn't be able to create such accounts, and administrators should handle this task."
6/8
"This default configuration represents a security issue as regular users shouldn't be able to create such accounts, and administrators should handle this task."
6/8

The recommendation is to adjust the value of MachineAccountQuota and only allow authorized users to add computers to the domain.
7/8
7/8

The customer found the computer objects by reviewing the AD objects - an excellent hint that such unusual objects may be part of an ongoing attack, and to periodically review the objects inside the AD.
8/8
8/8
• • •
Missing some Tweet in this thread? You can try to
force a refresh