1/ #ThreatHunting: @Avast mentions in its Q1 Threat Report that one-third of their observed rootkit activity are due to the Ring-3 rootkit R77.
Here are two hunting approaches to detect R77 on an infected system. 🧵
#CyberSecurity
Here are two hunting approaches to detect R77 on an infected system. 🧵
#CyberSecurity

2/ R77 is an open-source rootkit that attempts to hide the existence on the infected system at various levels (screenshot).
As stated on the GitHub repo, e.g., all entities where the name starts with "$77" are hidden.
github.com/bytecode77/r77…
As stated on the GitHub repo, e.g., all entities where the name starts with "$77" are hidden.
github.com/bytecode77/r77…

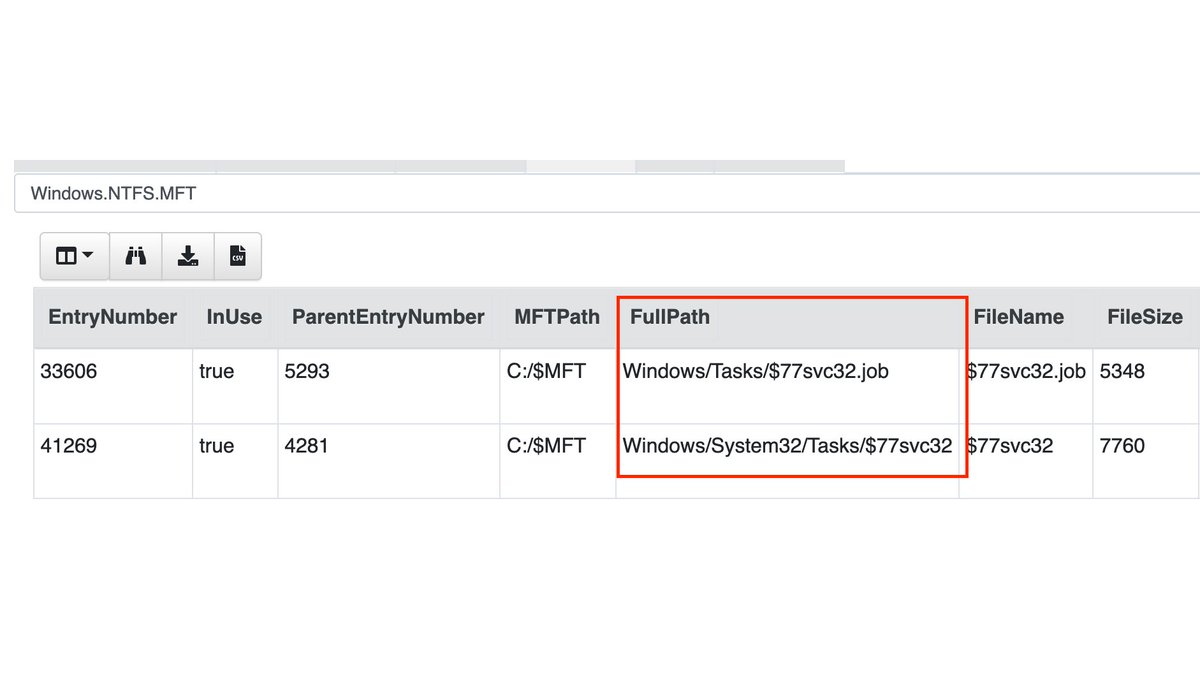
3/ The installer creates two scheduled tasks for the 32-bit and the 64-bit r77 service, according to the GitHub Readme.
After running the installer on our lab system, no new scheduled task is visible inside the Tasks folder.
After running the installer on our lab system, no new scheduled task is visible inside the Tasks folder.

4/ But if we use the MFT-Hunt of @velocidex and search for the keyword $77 in the MFT, we get two hits! 
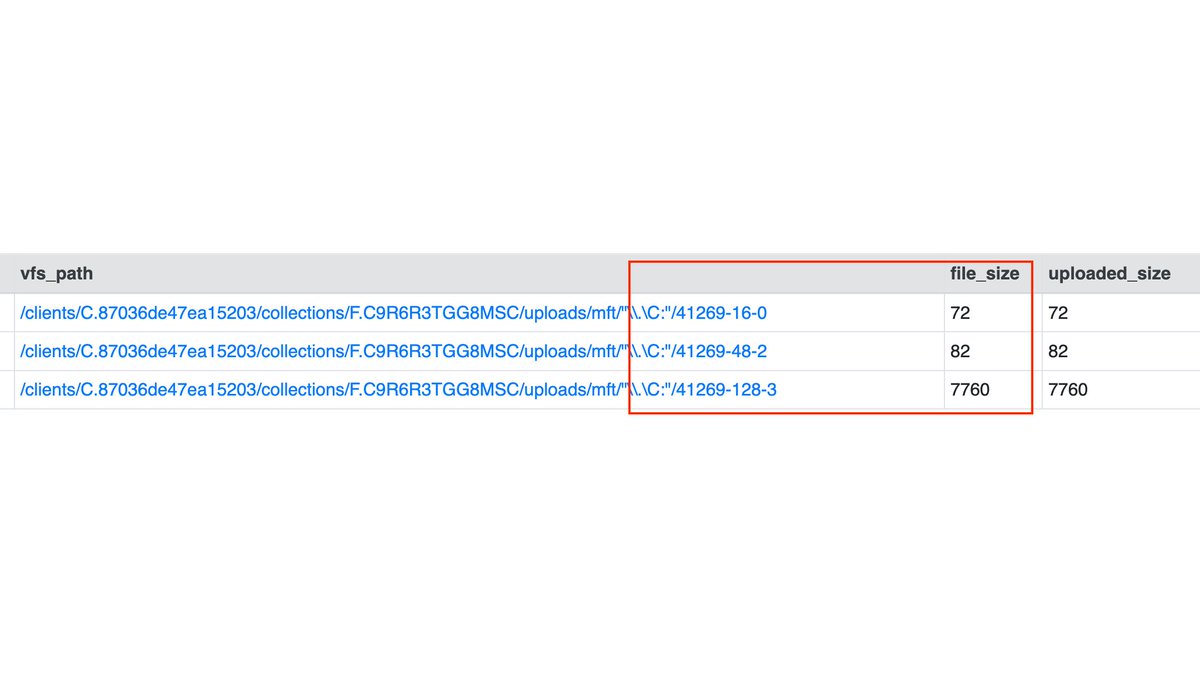
5/ Now that we have the MFT EntryNumber of the Scheduled Task created by the rootkit installer, we can export the task file with Velociraptor (NTFS.Recover). 
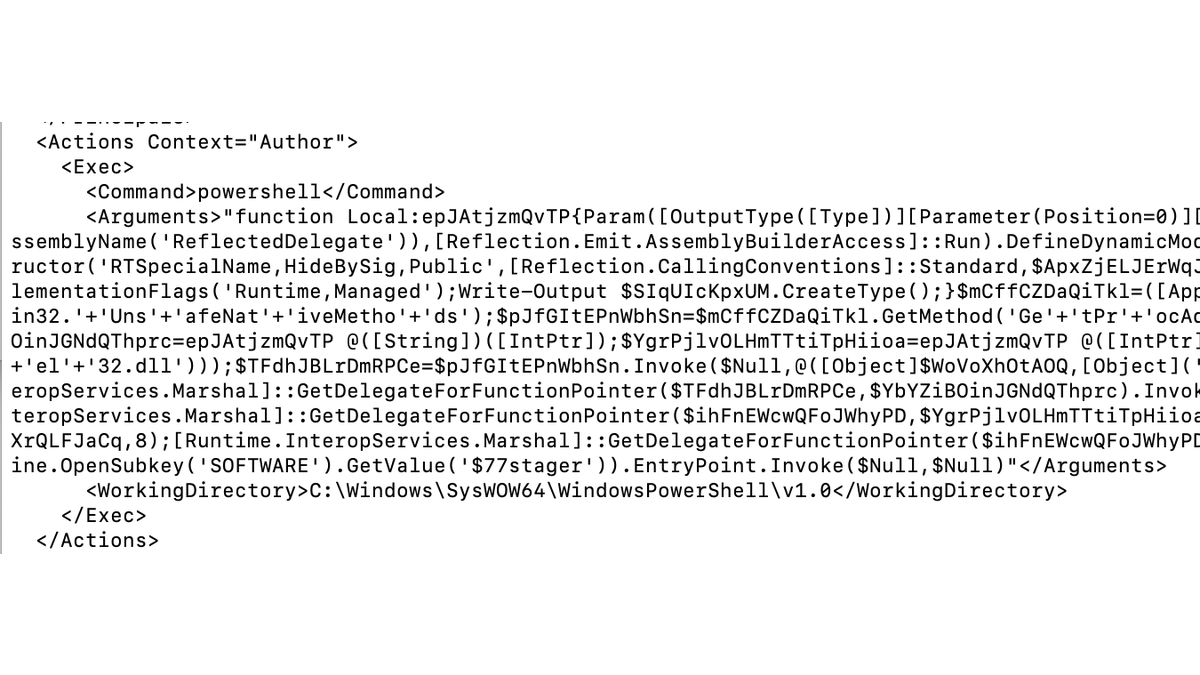
6/ After exporting the scheduled task, we see that the job is running obfuscated PowerShell code.
So one technique to find this rootkit is to parse the MFT for keywords like "$77".
So one technique to find this rootkit is to parse the MFT for keywords like "$77".
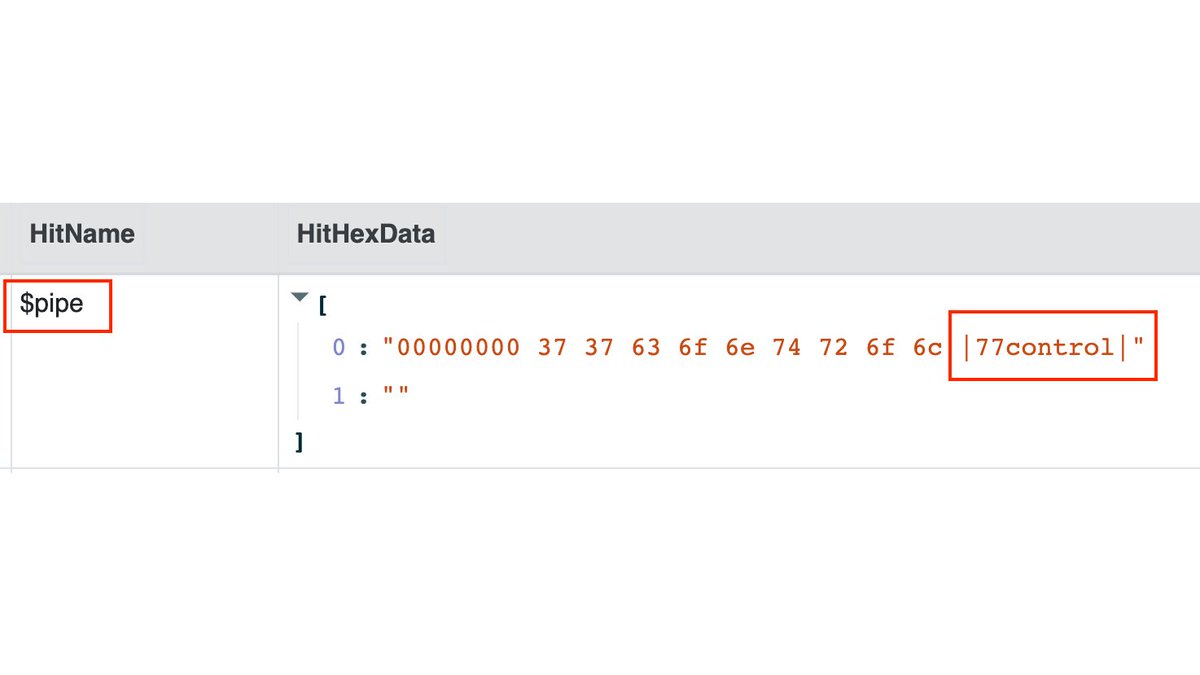
7/ The R77 test console shows that named pipes are used for communication (with the pipe name "$77control"). 
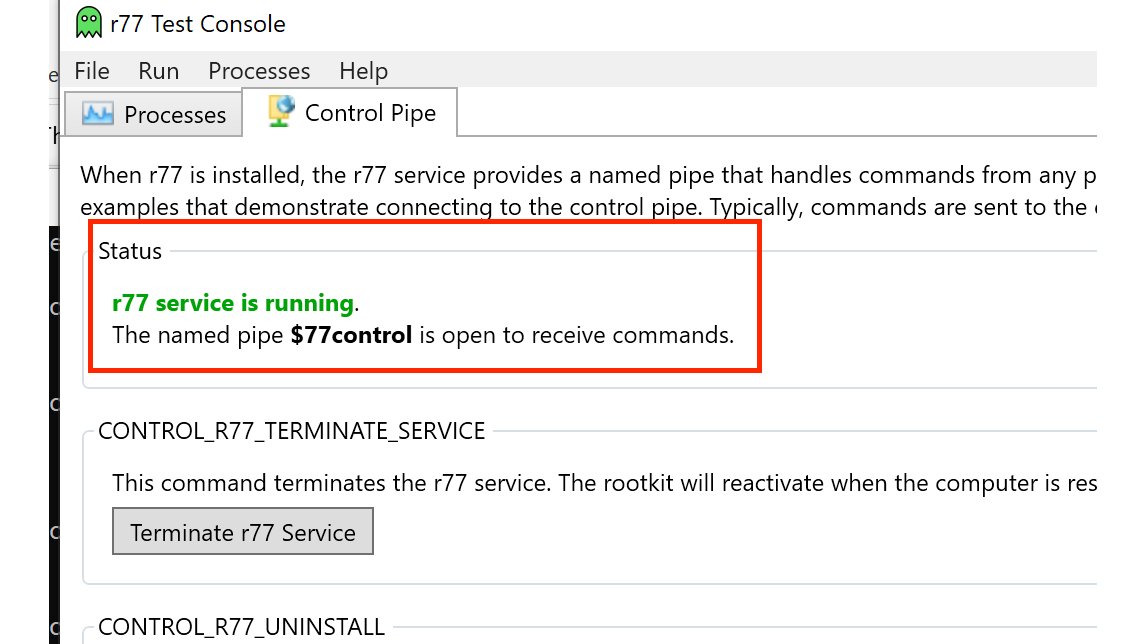
8/ We can now search specifically for this pipe name in memory (with the Velociraptor Hunt Yara.PhysicalMemory) 
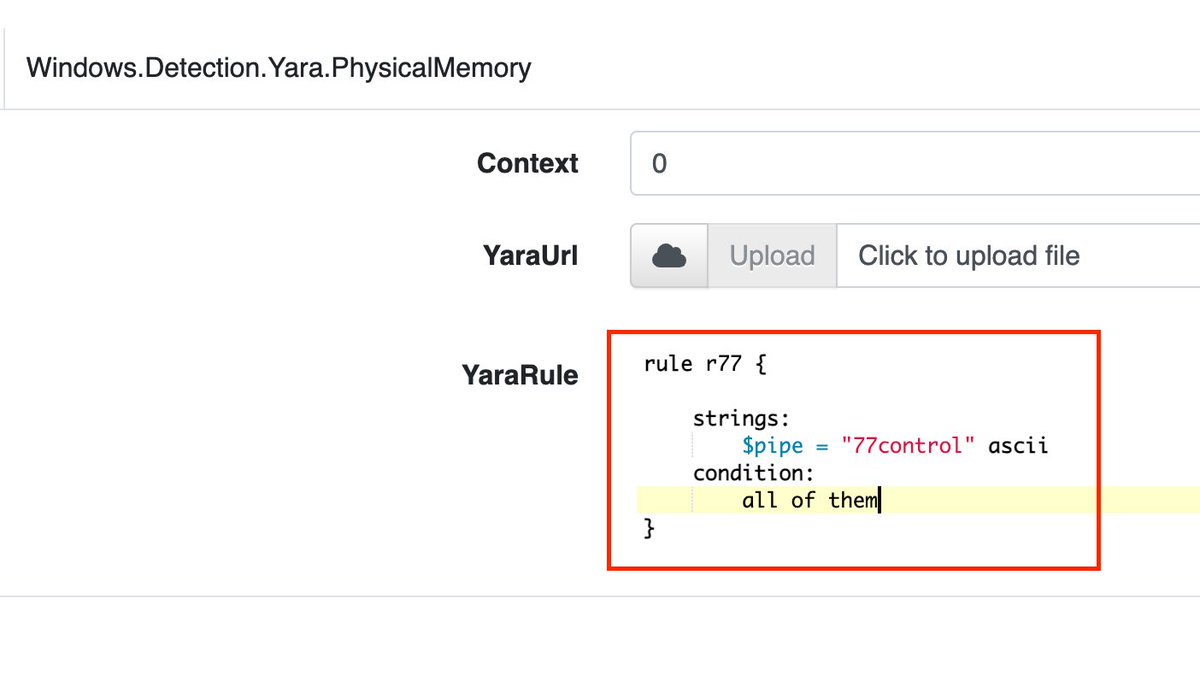
10/ Although this rootkit hides its presence with various techniques, it is relatively easy to find out if a system is infected with R77, as the two examples with the MFT and the NamedPipes have shown. 😎
• • •
Missing some Tweet in this thread? You can try to
force a refresh