
1/ @ESET (see tweet below) has reported that #Emotet uses LNK attachments for the initial infection vector.
We can download a sample from Bazaar by @abuse_ch for doing our own analysis (sample from 2022-05-02).
bazaar.abuse.ch/sample/ce7191e…
#CyberSecurity
We can download a sample from Bazaar by @abuse_ch for doing our own analysis (sample from 2022-05-02).
bazaar.abuse.ch/sample/ce7191e…
#CyberSecurity
https://twitter.com/ESETresearch/status/1518923380782739458
2/ exiftool works very well to find out the path and command line arguments of the malicious LNK file: 

3/ The analyzed sample from @Netskope calls PowerShell directly. However, in our sample, cmd.exe is called first, then PowerShell with a base64 encoded command argument.
Picture taken from here - an analysis worth reading:
netskope.com/blog/emotet-ne…
Picture taken from here - an analysis worth reading:
netskope.com/blog/emotet-ne…

4/ This infection mechanism is an excellent opportunity to point out that PowerShell script block logging should be enabled globally.
The @splunk Threat Research Team has written a blog with related detections. Even if Splunk is not used as SIEM, have a look at the detections.
The @splunk Threat Research Team has written a blog with related detections. Even if Splunk is not used as SIEM, have a look at the detections.
/5 For example, hunt inside the PS logs for the keyword "$DoIt", a function of the DKMC framework we also see repeatedly in our IR cases, or hunt for the keyword IWR (Invoke-WebRequest), which Emotet uses for downloading the second stage code.
splunk.com/en_us/blog/sec…
splunk.com/en_us/blog/sec…

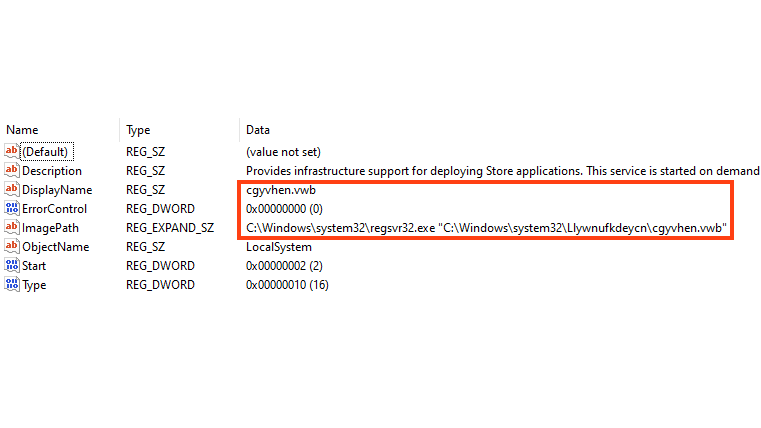
7/ Coming back to Emotet, collect all ASEP (Auto-Start Extensibility Points) in your network and specifically look for services that have regsrv32.exe in the ImagePath.
#ThreatHunting
#ThreatHunting
8/ The random names in the System32 directory should be easy to find.
(Image taken from the Netskope blog, see the third tweet for the link).
Good luck 🍀
(Image taken from the Netskope blog, see the third tweet for the link).
Good luck 🍀
• • •
Missing some Tweet in this thread? You can try to
force a refresh














