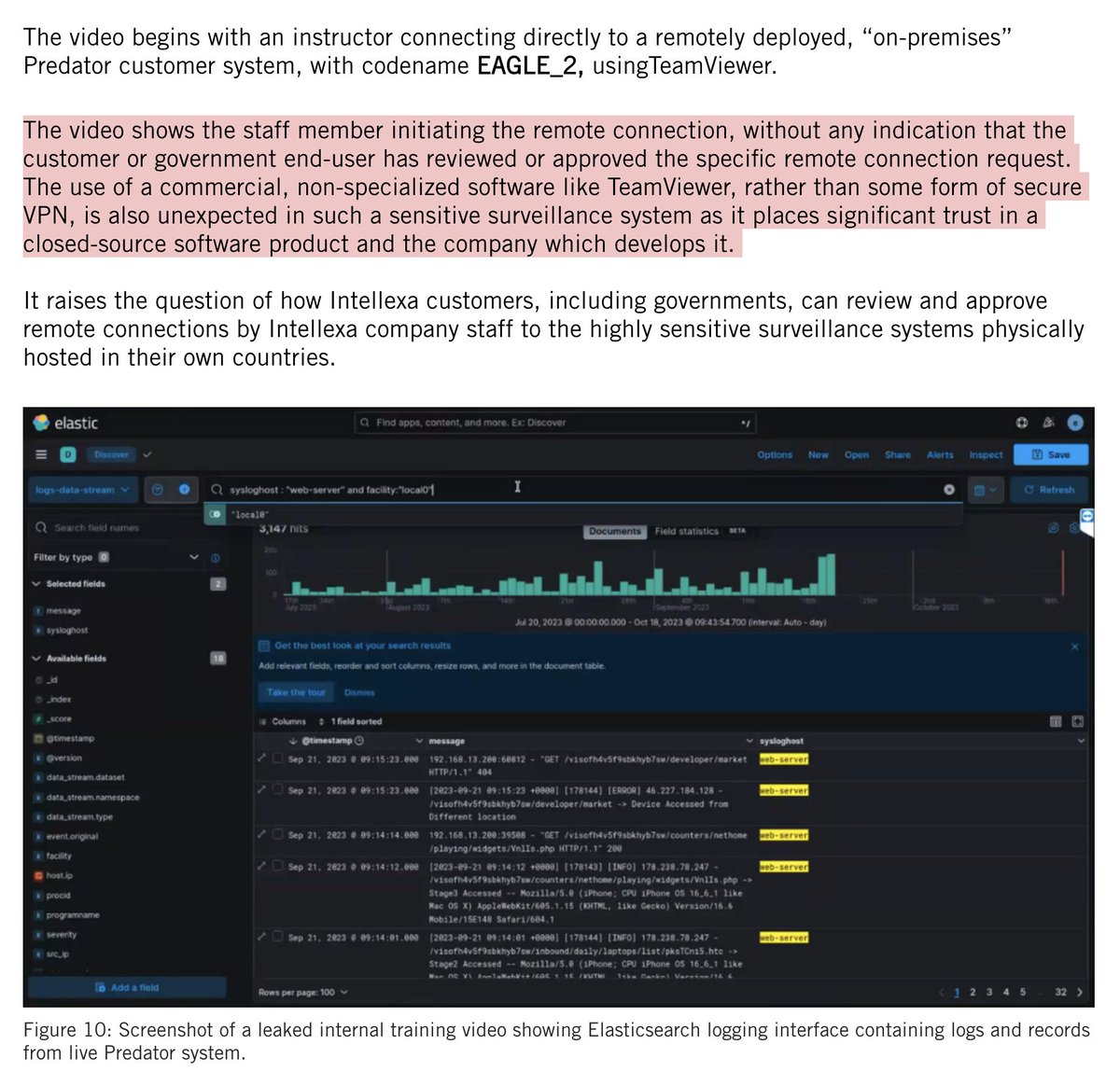
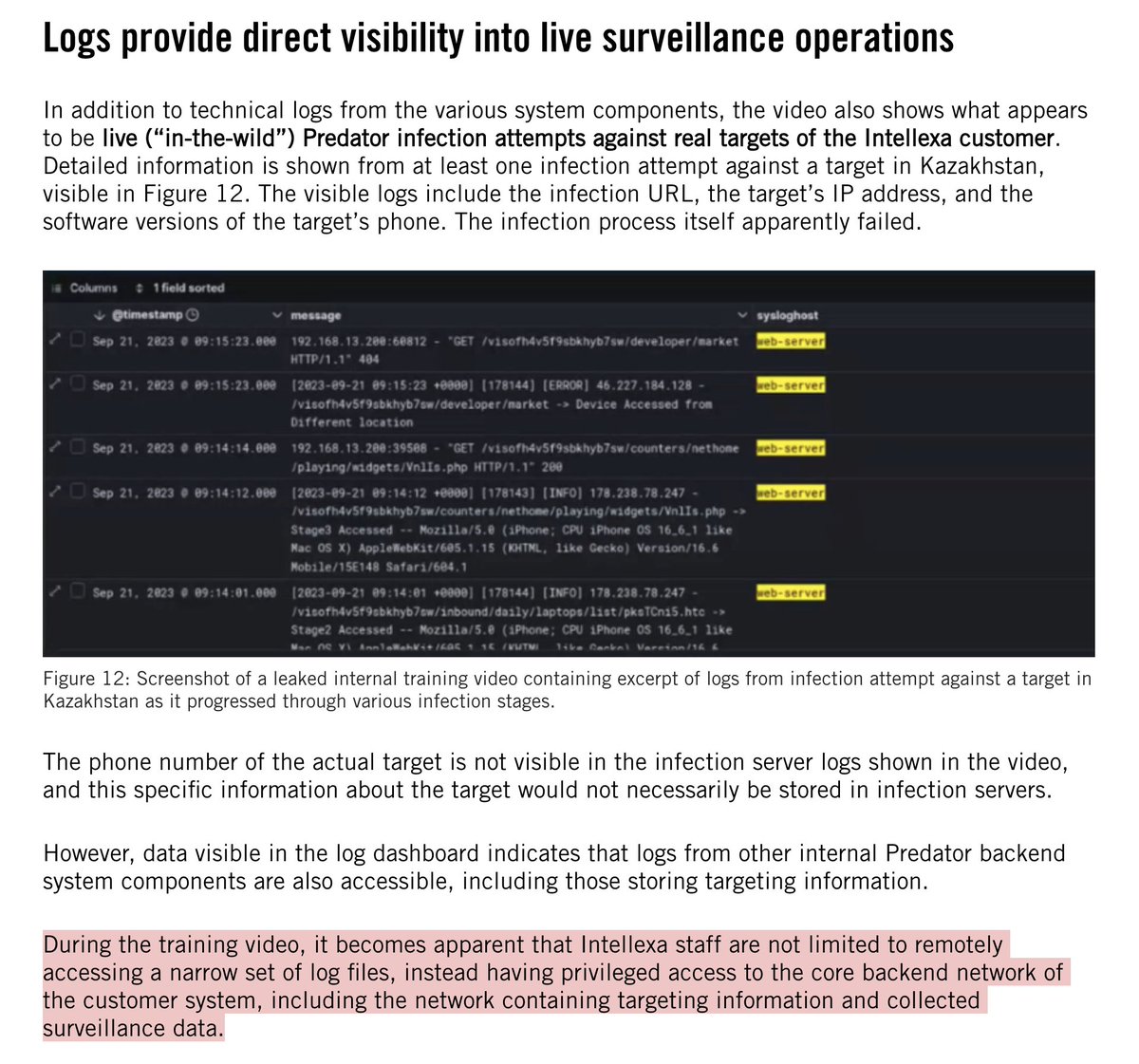
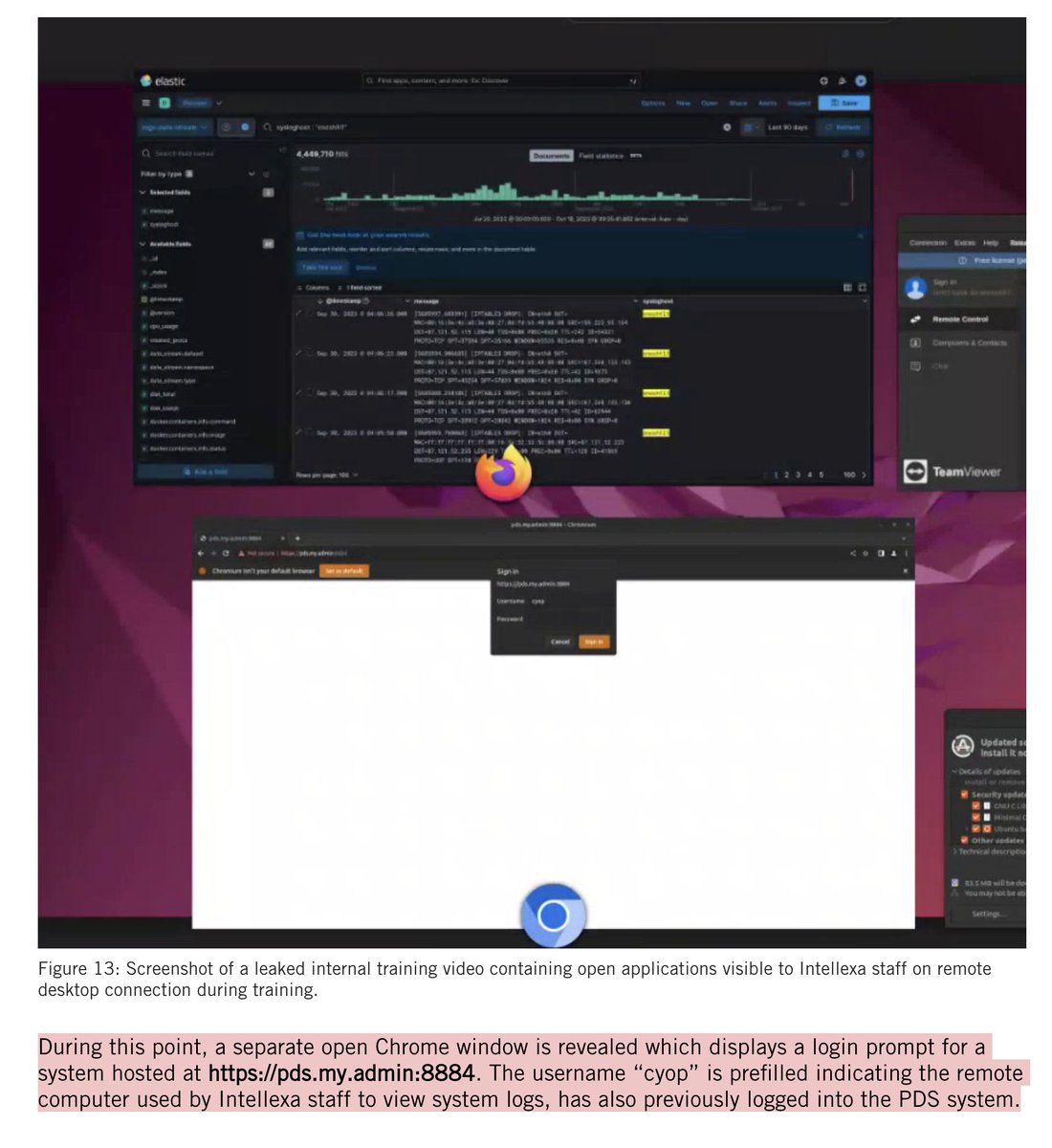
The "no guns on #January6th" line keeps cropping up.
It's flat wrong.
It's flat wrong.
https://twitter.com/jsrailton/status/1368400253372817409
There were plenty of guns on #January6th
"I'm the one in the video with the gun right here"
-John Emanuel Banuelos speaking to the police.
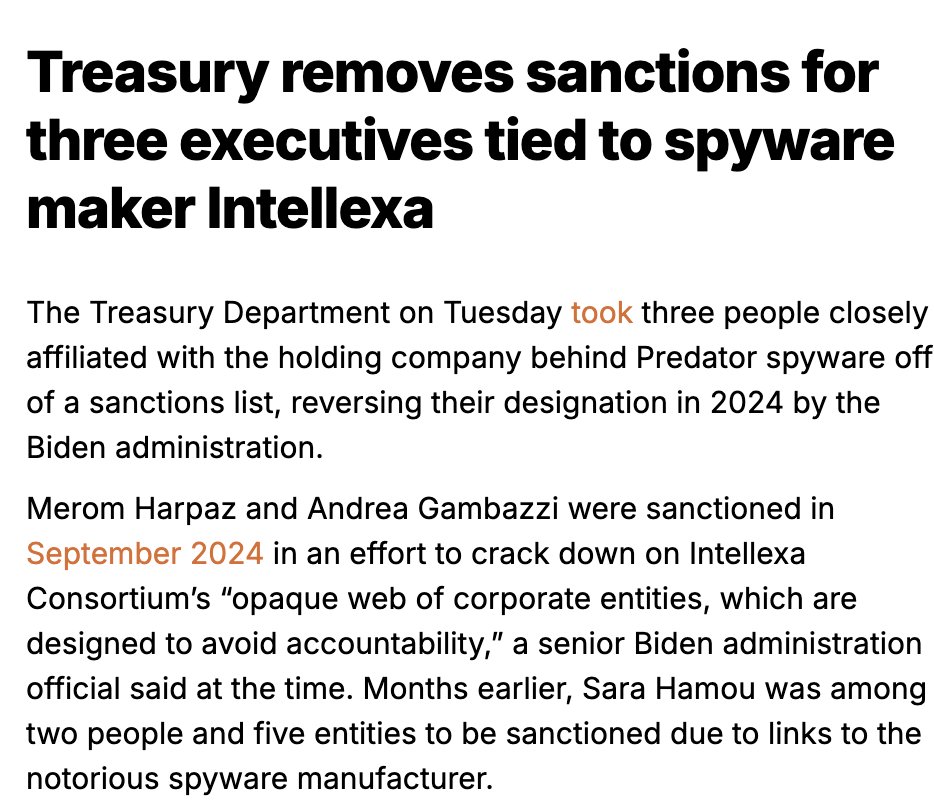
Story: @ryanjreilly
nbcnews.com/politics/polit…
"I'm the one in the video with the gun right here"
-John Emanuel Banuelos speaking to the police.
Story: @ryanjreilly
nbcnews.com/politics/polit…

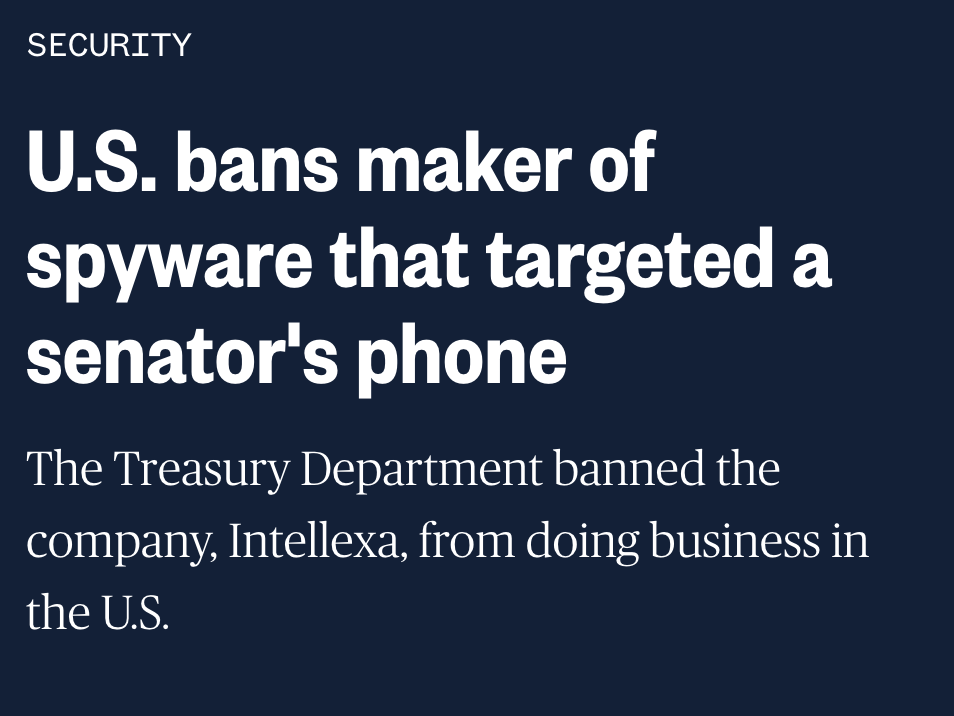
And who can forget Lonnie Coffman, who brought a small arsenal to DC?




https://twitter.com/TomJackmanWP/status/1509971310176354305




And then there's Christopher Alberts, indicted for violence against an officer... and carrying a gun with him on #January6th.
His Taurus semiautomatic had a round in the chamber and 12 in the clip.
justice.gov/usao-dc/defend…



His Taurus semiautomatic had a round in the chamber and 12 in the clip.
justice.gov/usao-dc/defend…




Guy Reffitt helped lead a push at the Capitol.
He was found guilty of a bevy of crimes... including bringing a loaded gun.
And threatening his own son to keep him quiet.
A holster under his jacket is visible in footage by @FordFischer.
justice.gov/usao-dc/pr/tex…



He was found guilty of a bevy of crimes... including bringing a loaded gun.
And threatening his own son to keep him quiet.
A holster under his jacket is visible in footage by @FordFischer.
justice.gov/usao-dc/pr/tex…




And let's not forget the #OathKeepers who brought & stashed a load of serious weaponry in a nearby hotel for their "Quick Reaction Force"
Source: storage.courtlistener.com/recap/gov.usco…

Source: storage.courtlistener.com/recap/gov.usco…


[VIOLENT FOOTAGE] I could go on posting about guns at the #January6th insurrection...
But don't be distracted by the "no guns" lie from the absolute wave of violence that was visited upon the #Capitol & DC police using every available weapon.
But don't be distracted by the "no guns" lie from the absolute wave of violence that was visited upon the #Capitol & DC police using every available weapon.
• • •
Missing some Tweet in this thread? You can try to
force a refresh