Nice new #coercion method from @filip_dragovic
using Microsoft's Distributed File System (MS-DFSNM) protocol on \PIPE\netdfs.
PoC: github.com/Wh04m1001/DFSC…
It works nicely👌
using Microsoft's Distributed File System (MS-DFSNM) protocol on \PIPE\netdfs.
PoC: github.com/Wh04m1001/DFSC…
It works nicely👌
@filip_dragovic [#thread 🧵] Here is a complete explanation of what you see here:
On the left I have my attacking machine and on the right I have a Windows Server that I use as a Domain Controller.
On the left I have my attacking machine and on the right I have a Windows Server that I use as a Domain Controller.

[#thread 🧵] In the top left terminal of my attacking machine is the program to exploit this new vulnerability.
In the bottom left is Responder, a tool allowing to mimic the authentication step of many windows protocols in order to show the hashes (NTLMv1, NTLMv2, etc ...)
In the bottom left is Responder, a tool allowing to mimic the authentication step of many windows protocols in order to show the hashes (NTLMv1, NTLMv2, etc ...)

[#thread 🧵] Firstly I put my Windows Server and my attacking machine in the same network so they can communicate.
Then in the top left terminal, I started the proof of concept code from @filip_dragovic found here: github.com/Wh04m1001/DFSC… with this command line:
Then in the top left terminal, I started the proof of concept code from @filip_dragovic found here: github.com/Wh04m1001/DFSC… with this command line:

[#thread 🧵] The IP 192.168.2.51 being my attacking machine where I listen with Responder, and 192.168.2.1 being the IP of my Windows Server.
When starting this script, it will authenticate and connect to the remote pipe named \PIPE\netdfs:
When starting this script, it will authenticate and connect to the remote pipe named \PIPE\netdfs:

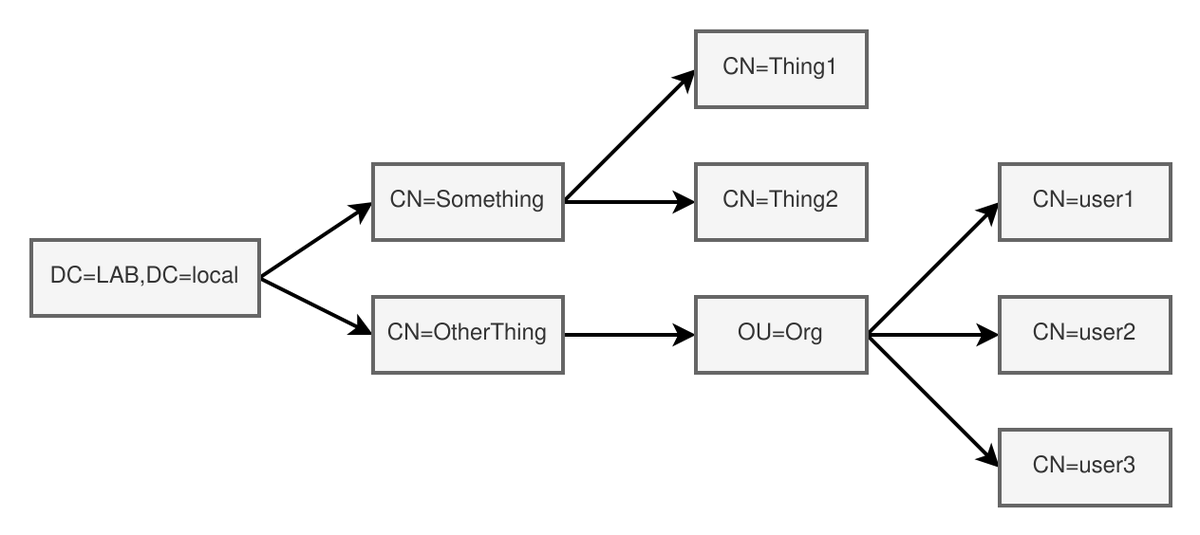
[#thread 🧵] This pipe is connected to the protocol MS-DFSNM (docs.microsoft.com/en-us/openspec…) and allows to call RPC functions of this protocol.
It will then call the remote #NetrDfsRemoveStdRoot function on the Windows Server (192.168.2.1) with the following parameters:
It will then call the remote #NetrDfsRemoveStdRoot function on the Windows Server (192.168.2.1) with the following parameters:

[#thread 🧵] This will force the Windows Server (192.168.2.1) to authenticate to the SMB share \\192.168.2.51\test\ and authenticate using its machine account (DC01$).
That's what we see in #Responder on the bottom left terminal of my attacking machine:
That's what we see in #Responder on the bottom left terminal of my attacking machine:

[#thread 🧵] Now that we have the hash of the machine account DC01$, we can relay it to authenticate elsewhere as DC01$ and perform privileged actions where we can.
This kind of vulnerabilities allows to quickly get from user to #domain #administrator in unprotected domains!
This kind of vulnerabilities allows to quickly get from user to #domain #administrator in unprotected domains!
[#thread 🧵] Various references:
- Protocol MS-DFSNM: docs.microsoft.com/en-us/openspec…
- Proof of concept code from @filip_dragovic: github.com/Wh04m1001/DFSC…
-
- Protocol MS-DFSNM: docs.microsoft.com/en-us/openspec…
- Proof of concept code from @filip_dragovic: github.com/Wh04m1001/DFSC…
-
https://twitter.com/filip_dragovic/status/1538154721655103488
• • •
Missing some Tweet in this thread? You can try to
force a refresh