#ESETresearch uncovers #CloudMensis, spyware for macOS using cloud storage as a way to communicate back and forth its operators. @marc_etienne_
welivesecurity.com/2022/07/19/i-s… 1/7
welivesecurity.com/2022/07/19/i-s… 1/7
We’ve analysed two #CloudMensis stages, the first download and runs the featureful spy agent. Both uses cloud storage using an authentication token. 2/7 

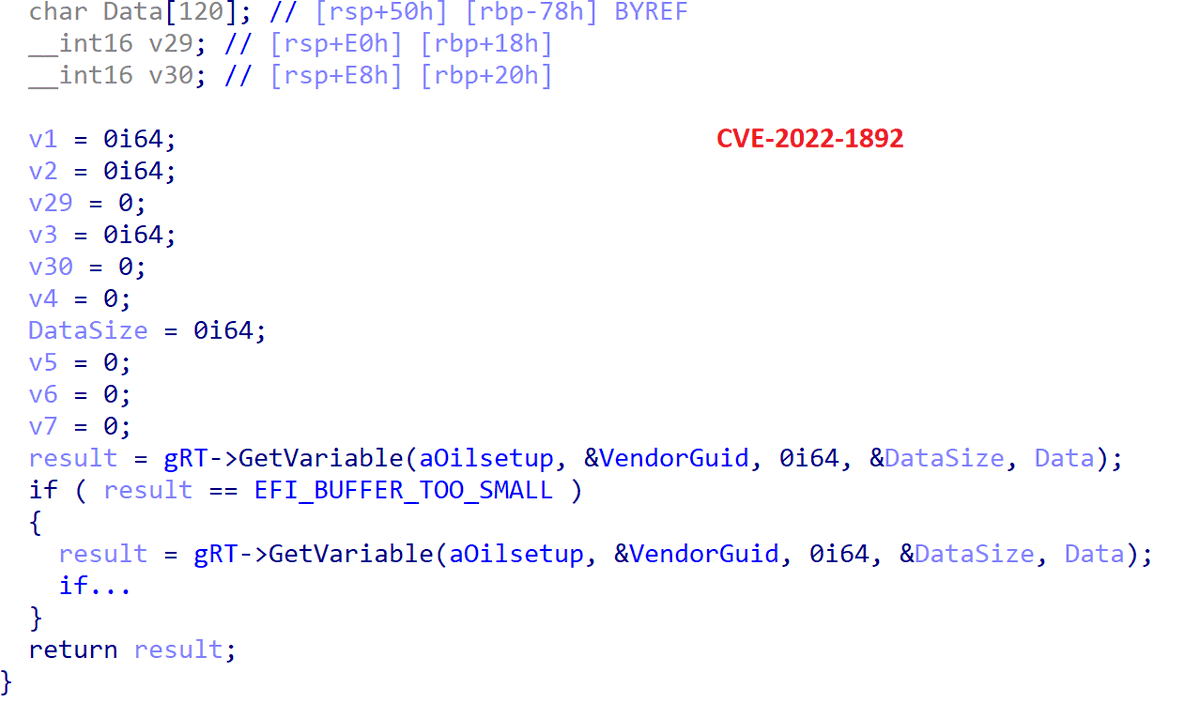
On vulnerably Macs, CloudMensis exploits a known vulnerability known as CVE-2020-9934, to bypass TCC and gain access to keyboard events and screen captures. 3/7 

We think CloudMensis may have been distributed using Safari exploit in the past because unexecuted code is present to cleanup traces after a successful exploit. 4/7 

According to the file extensions in the default configuration, operators of CloudMensis are interested in documents, spreadsheets, audio recordings, pictures, and email messages. 5/7 

Metadata from the cloud storage used by CloudMensis suggest there were at most 51 victims using this configuration between February 4th
and April 22nd. 6/7

and April 22nd. 6/7


Textual IoCs and MISP JSON available on GitHub, and more details on the blog. #ESETresearch
github.com/eset/malware-i… 7/7
github.com/eset/malware-i… 7/7
• • •
Missing some Tweet in this thread? You can try to
force a refresh