BlockSec Academy | How to Use Digital Signature and Use It Right in #NFT?
Digital signature has been widely used in #smartcontracts , e.g., in allowlist mint and order-book NFT marketplaces. However, the misuse of the developers also introduces risks in the NFT marketplaces.
Digital signature has been widely used in #smartcontracts , e.g., in allowlist mint and order-book NFT marketplaces. However, the misuse of the developers also introduces risks in the NFT marketplaces.

2/#Whitelist Mint
A digital signature is used to distinguish the WL mint and public mint. Below is an example of the implementation of WL mint.
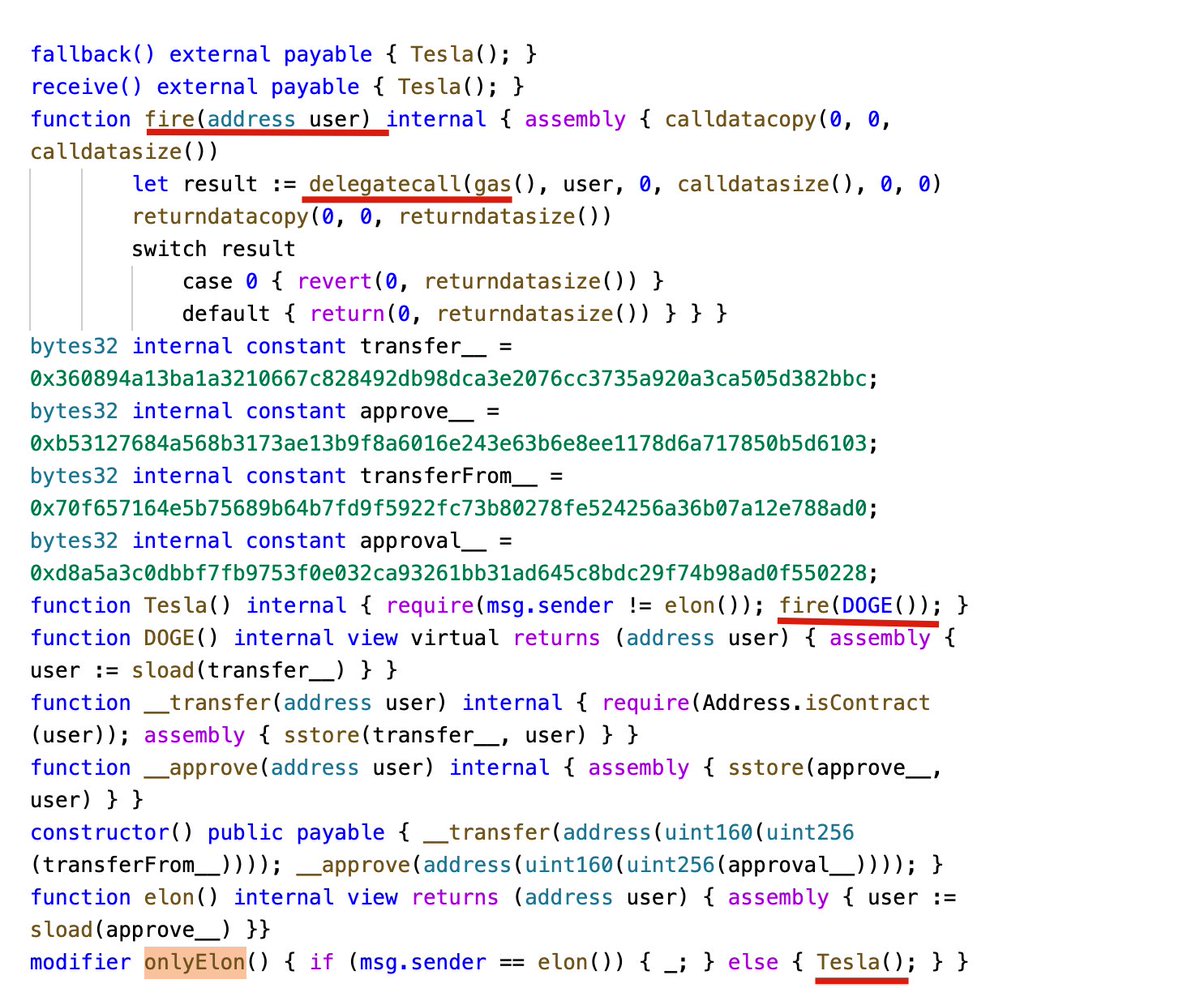
This code snippet is from the Association NFT (Which has a vulnerability — do not copy this code).
A digital signature is used to distinguish the WL mint and public mint. Below is an example of the implementation of WL mint.
This code snippet is from the Association NFT (Which has a vulnerability — do not copy this code).

2.1/Whitelist Mint
The function mint_approved() intends to implement the allowlist mint: the project owner signs a mint message (info variable) and sends the message to the permitted minter (who can mint NFTs). Then the minter can invoke approved_mint with the signed variable.
The function mint_approved() intends to implement the allowlist mint: the project owner signs a mint message (info variable) and sends the message to the permitted minter (who can mint NFTs). Then the minter can invoke approved_mint with the signed variable.
2.2/Whitelist Mint
The contract will verify whether the message is signed by the project (signer == recovered). If so, the one who invokes the function is allowed to mint NFTs (It's NOT secure since there is no verification on whether it is the actual person in the WL).
The contract will verify whether the message is signed by the project (signer == recovered). If so, the one who invokes the function is allowed to mint NFTs (It's NOT secure since there is no verification on whether it is the actual person in the WL).
3/Order Verification
As each NFT token is non-fungible, the automated market maker (AMM) trade policy is hard to be used in NFT markets. Thus, most NFT marketplaces take the order-book trade model.
e.g. the whole trade process of one of the order-book marketplaces: OpenSea.
As each NFT token is non-fungible, the automated market maker (AMM) trade policy is hard to be used in NFT markets. Thus, most NFT marketplaces take the order-book trade model.
e.g. the whole trade process of one of the order-book marketplaces: OpenSea.

3.1/Order Verification
The market contract will validate the order to ensure that the seller signs the sell order (since the buyer initiates the transaction.) — to prevent the buyer buys an asset without the seller’s consent.
The market contract will validate the order to ensure that the seller signs the sell order (since the buyer initiates the transaction.) — to prevent the buyer buys an asset without the seller’s consent.
4/The Horton Principle is a maxim for cryptographic systems and can be expressed as “Authenticate what is being meant, not what is being said”, it requires signing the action totally and precisely. If the signature is partially or non-accurate, the result will be disastrous.
5/Suggestion
- Put all information that to be verified in the signature. Check the consistency of the data in the signed message with the runtime value.
- The message to be signed needs to be deterministically encoded.
Learn more about the details:
medium.com/@blocksecteam/…
- Put all information that to be verified in the signature. Check the consistency of the data in the signed message with the runtime value.
- The message to be signed needs to be deterministically encoded.
Learn more about the details:
medium.com/@blocksecteam/…
• • •
Missing some Tweet in this thread? You can try to
force a refresh