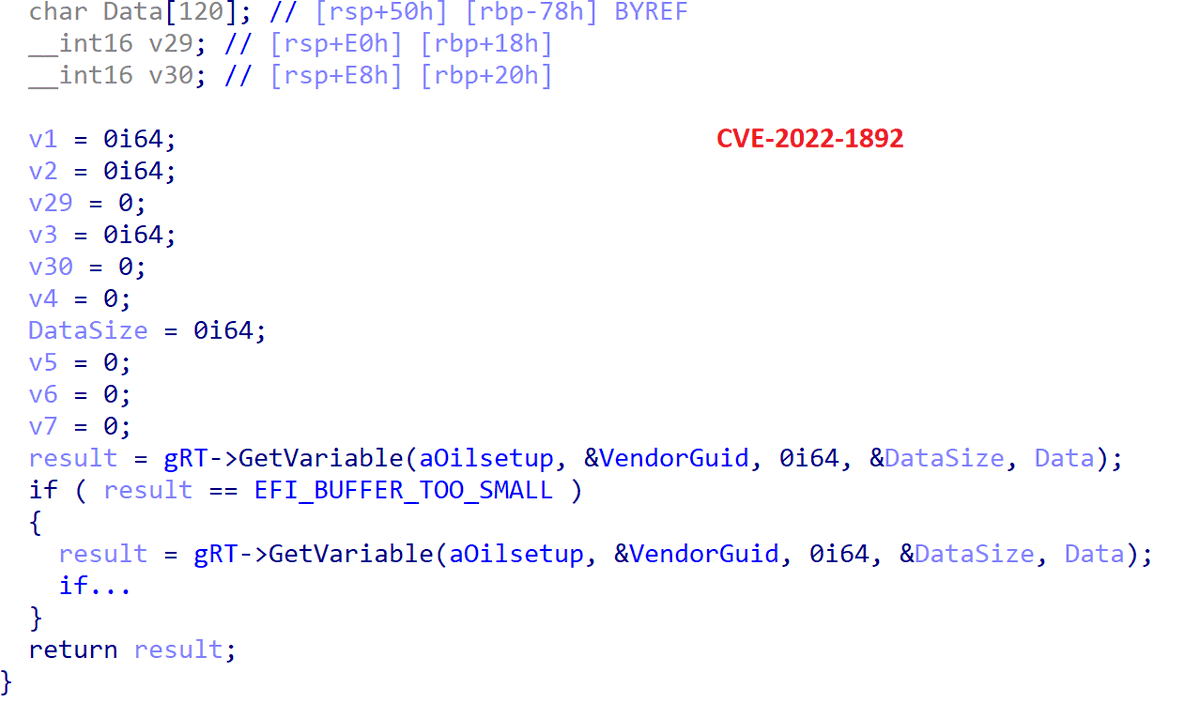
#ESETresearch #BREAKING A signed Mac executable disguised as a job description for Coinbase was uploaded to VirusTotal from Brazil 🇧🇷. This is an instance of Operation In(ter)ception by #Lazarus for Mac. @pkalnai @dbreitenbacher 1/7 

Malware is compiled for both Intel and Apple Silicon. It drops three files: a decoy PDF document Coinbase_online_careers_2022_07.pdf, a bundle FinderFontsUpdater.app and a downloader safarifontagent. It is similar to #ESETresearch discovery in May. 2/7
https://twitter.com/ESETresearch/status/1521735320852643840
However, this time the bundle is signed July 21 (according to the timestamp) using a certificate issued in February 2022 to a developer named Shankey Nohria and team identifier 264HFWQH63. The application is not notarized and Apple has revoked the certificate on August 12. 3/7 

Another change is in the downloader, safarifontagent, as it connects to a different C&C server (https://concrecapital[.]com/%user%.jpg) The C&C server did not respond at the time we analyzed this threat. 4/7 

The Windows counterpart of this threat dropping the exact same decoy (2B4E8F1927927BDC2F71914BA1F12511D9B6BDBDB2DF390E267F54DC4F8919DD) was spotted August 4 by @h2jazi. 5/7
https://twitter.com/h2jazi/status/1555205042331947011
IoCs:
FE336A032B564EEF07AFB2F8A478B0E0A37D9A1A6C4C1E7CD01E404CC5DD2853 (Extractor)
798020270861FDD6C293AE8BA13E86E100CE048830F86233910A2826FACD4272 (FinderFontsUpdater)
49046DFEAEFC59747E45E013F3AB5A2895B4245CFAA218DD2863D86451104506 (safarifontagent)
... 6/7
FE336A032B564EEF07AFB2F8A478B0E0A37D9A1A6C4C1E7CD01E404CC5DD2853 (Extractor)
798020270861FDD6C293AE8BA13E86E100CE048830F86233910A2826FACD4272 (FinderFontsUpdater)
49046DFEAEFC59747E45E013F3AB5A2895B4245CFAA218DD2863D86451104506 (safarifontagent)
... 6/7
• • •
Missing some Tweet in this thread? You can try to
force a refresh