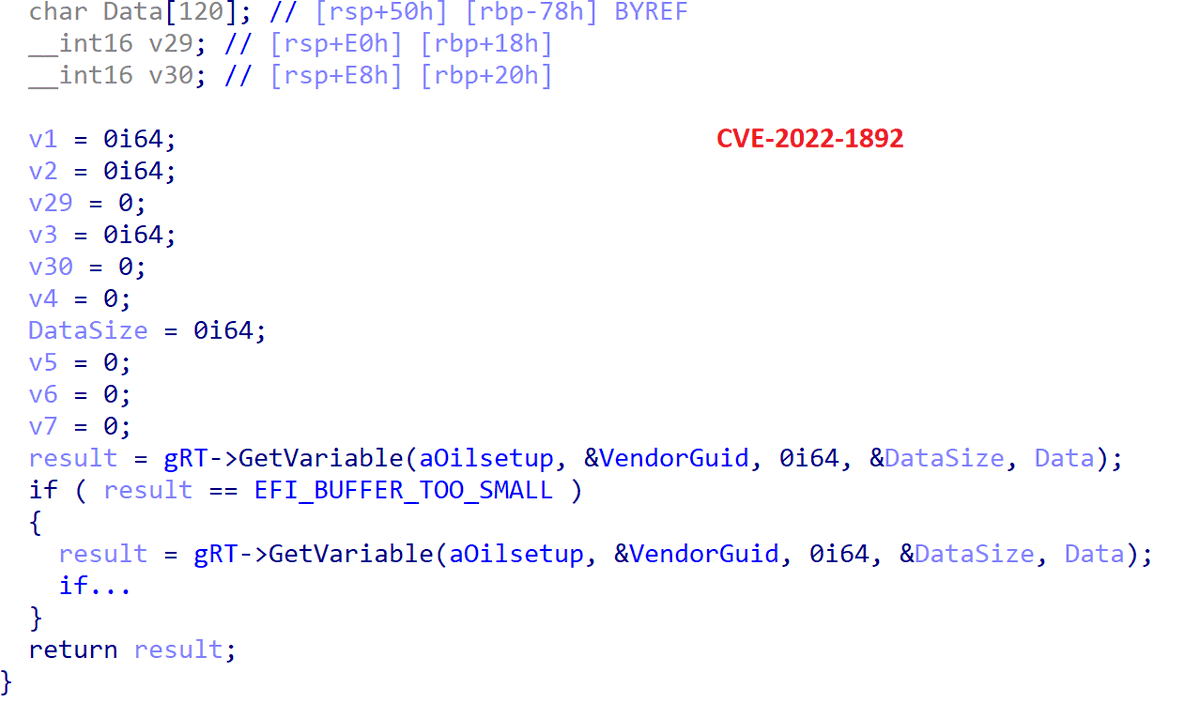
#ESETresearch has discovered #Lazarus attacks against targets in 🇳🇱 and 🇧🇪, spreading via spearphishing emails and exploiting the CVE-2021-21551 vulnerability to disable the monitoring of all security solutions on compromised machines @pkalnai welivesecurity.com/2022/09/30/ama…
@pkalnai The attack started with spearphishing emails connected to fake job offers, targeting an aerospace company in the Netherlands, and a political journalist in Belgium. The attackers then deployed a VMProtect-ed version of #BLINDINGCAN, a fully featured HTTP(S) backdoor. 2/6 
@pkalnai Notably, the attackers used a rootkit named FudModule.dll, that modifies kernel variables and removes kernel callbacks to disable monitoring of all security solutions on the system. This is the first recorded abuse of the CVE-2021-21551 vulnerability in Dell DBUtil drivers. 3/6
@pkalnai We also detected a 32-bit dropper, a trojanized version of the sslSniffer from the wolfSSL project. At the time of the attack, the dropper was validly signed with a certificate issued to "A" MEDICAL OFFICE, PLLC., which has since expired. 4/6 

@pkalnai Interestingly, this component uses an unusual decryption algorithm HC-128 with a 128-bit key as the first parameter and, for its 128-bit initialization vector, the string ffffffffffffffff. 5/6 

@pkalnai This research was presented at @virusbtn in Prague. #VB2022 abstract: virusbulletin.com/conference/vb2…
IoCs available on our GitHub: github.com/eset/malware-i… 6/6


IoCs available on our GitHub: github.com/eset/malware-i… 6/6



• • •
Missing some Tweet in this thread? You can try to
force a refresh