#ESETResearch discovered and reported to the manufacturer 3 vulnerabilities in the #UEFI firmware of several Lenovo Notebooks. The vulnerabilities allow disabling UEFI Secure Boot or restoring factory default Secure Boot databases (incl. dbx): all simply from an OS. @smolar_m 1/9
Reported vulnerabilities – #CVE-2022-3430, #CVE-2022-3431, and #CVE-2022-3432 – affect various Lenovo Yoga, IdeaPad and ThinkBook devices. All affected devices with an active development support have been fixed after we reported them to the manufacturer. 2/9
While disabling UEFI Secure Boot allows direct execution of unsigned UEFI apps, restoring factory default dbx enables the use of known vulnerable bootloaders (e.g., #CVE-2022-34301 found by @eclypsium) to bypass Secure Boot, while keeping it enabled.
eclypsium.com/2022/08/11/vul… 3/9
eclypsium.com/2022/08/11/vul… 3/9
As in our previous discovery (#CVE-2021-3971, #CVE-2021-3972),current vulnerabilities weren’t caused by flaws in the code. The affected drivers were meant to be used only during the manufacturing process but were mistakenly included in the production.
https://twitter.com/ESETresearch/status/15163653390801469444/9
The reported vulnerabilities can be exploited by simply creating special NVRAM variables. @NikolajSchlej recently posted a nice explanation of why and how firmware developers should avoid storing security-sensitive components in NVRAM variables:
https://twitter.com/NikolajSchlej/status/15842657428576788485/9
The first of the vulnerabilities, #CVE-2022-3430, is found in the DXE driver WmiSetupUnderOsDxe which checks for the “L05WSBD” NVRAM variable and performs an action based on its value. To disable UEFI Secure Boot, L05SecureBootData.Action value should be set to 2. 6/9 

For #CVE-2022-3431, the value of the variable is irrelevant. The DXE driver BootOrderDxe simply disables UEFI Secure Boot if NVRAM variables “BootOrderSecureBootDisable” or “BootOrderDualBootMode” exist. 7/9 



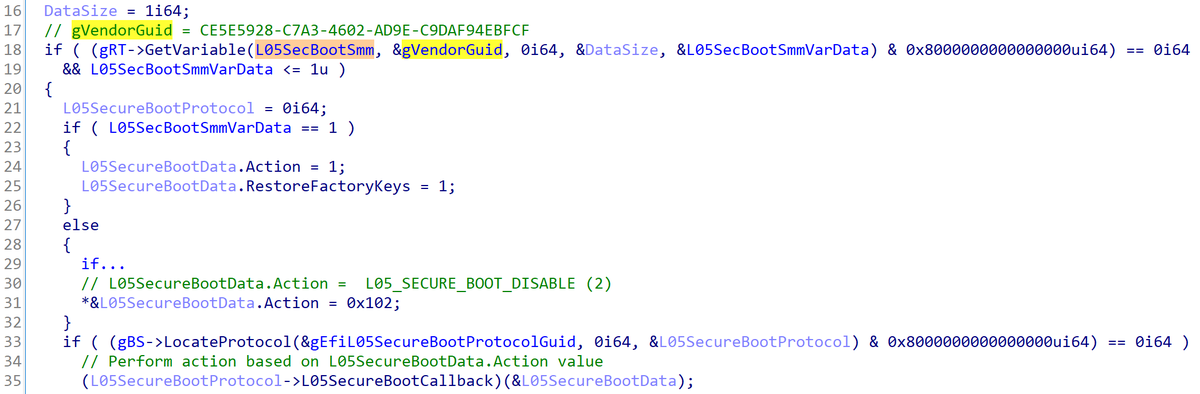
Lastly, #CVE-2022-3432 relates to the BdsDxe DXE driver. This driver retrieves the value of the “L05SecBootSmm” NVRAM variable and if the value is 0, it disables UEFI Secure Boot. If the value is 1, it enables Secure Boot and restores factory keys/databases. 8/9 
For those using one of the affected devices, we highly recommend updating to the latest firmware version. To see if you are affected by these vulnerabilities and for the firmware update instructions, visit Lenovo Advisory. support.lenovo.com/us/en/product_… 9/9
• • •
Missing some Tweet in this thread? You can try to
force a refresh