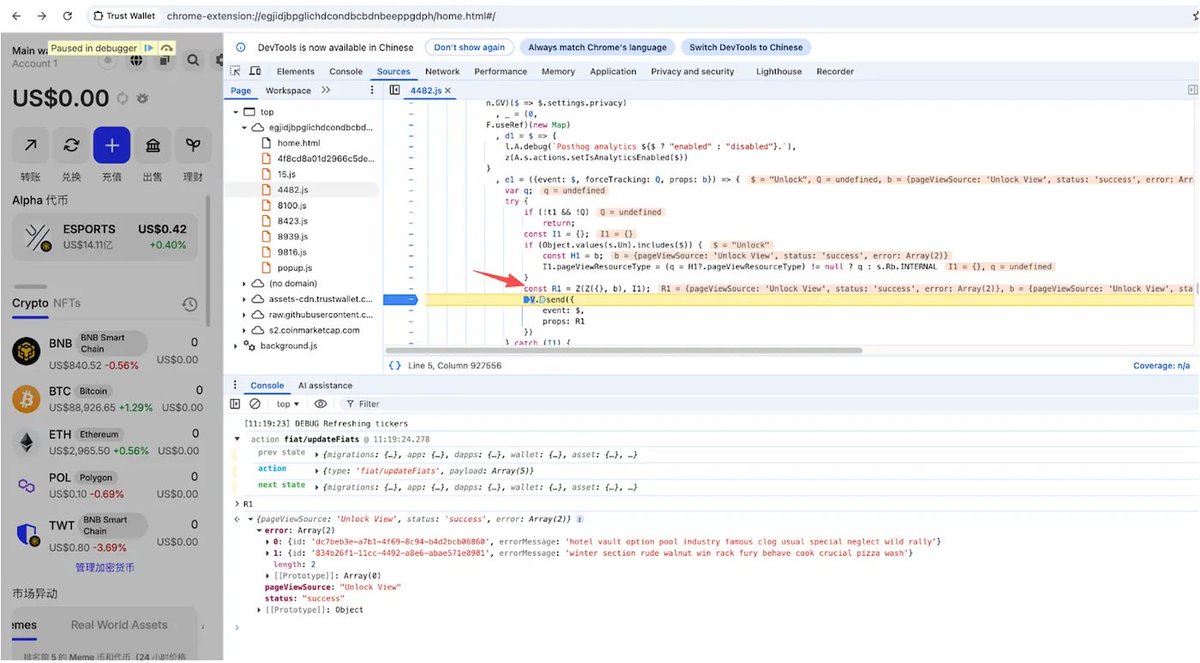
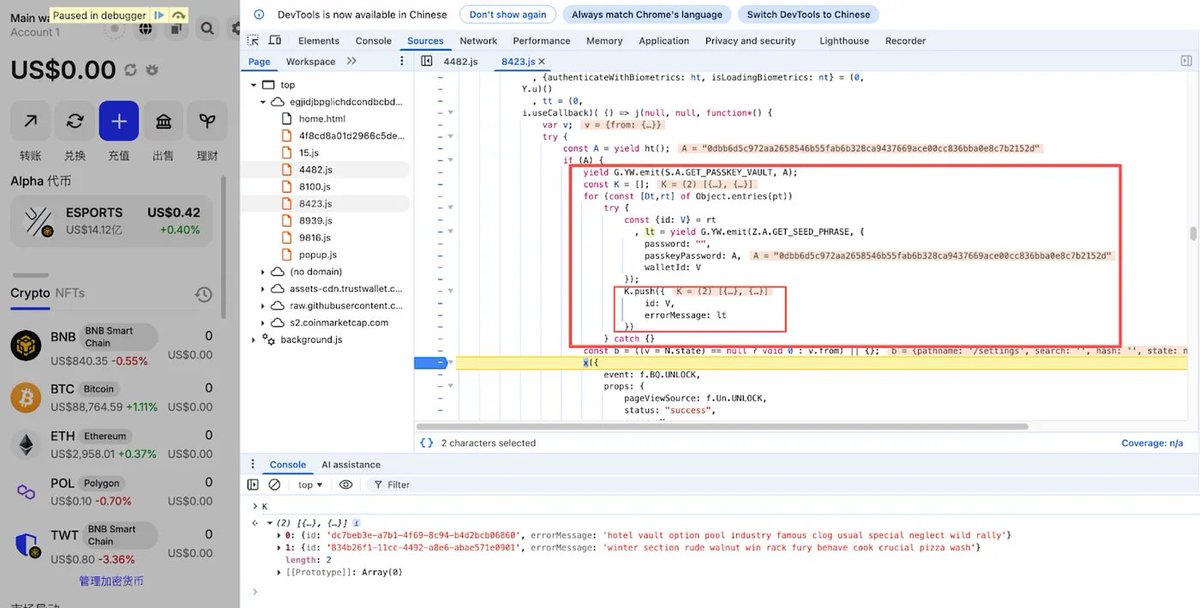
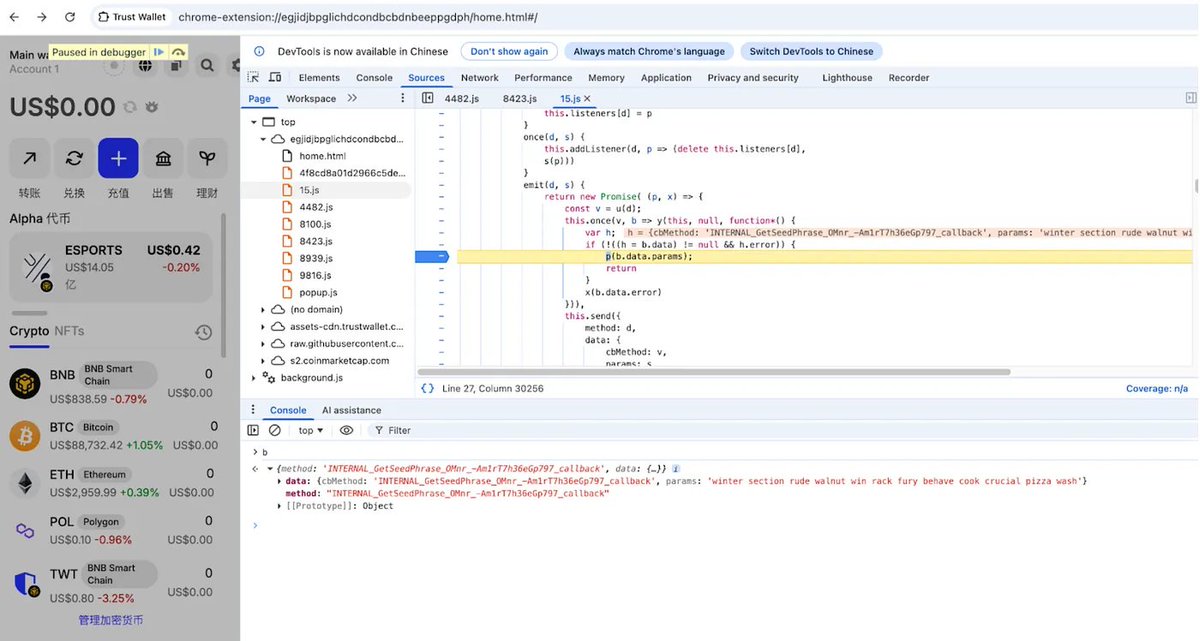
Quick 🧵on @FTX_Official Hack
Total stolen so far: $417M
Hackers address on:
ETH / BSC / Avalanche: 0x59ab..d32b
Solana: 6sEk..hSHH
Thread Coverage:
1/Assets Stolen
2/ Swapped / Bridged Funds
2/ Assets Frozen
3/ Platforms Used
4/ Notable Transactions
5/Suspected Whitehats
Total stolen so far: $417M
Hackers address on:
ETH / BSC / Avalanche: 0x59ab..d32b
Solana: 6sEk..hSHH
Thread Coverage:
1/Assets Stolen
2/ Swapped / Bridged Funds
2/ Assets Frozen
3/ Platforms Used
4/ Notable Transactions
5/Suspected Whitehats

Swapped/Bridged Funds
ETH Network: Swap Alts for $ETH and $DAI via various DEX, and bridge 5,000,000 $MATIC to Polygon Network via Polygon Bridge.
BSC Network: Bridge tokens to ETH network via Stargate, Multichain
Solana: Bridge 7,964 $ETH to ETH network via Wormhole Bridge
ETH Network: Swap Alts for $ETH and $DAI via various DEX, and bridge 5,000,000 $MATIC to Polygon Network via Polygon Bridge.
BSC Network: Bridge tokens to ETH network via Stargate, Multichain
Solana: Bridge 7,964 $ETH to ETH network via Wormhole Bridge
Assets Frozen
So far, $USDT on the #Avalanche and #Solana has been frozen by @Tether_to.
The only other assets that can be frozen are the 33,184.98 $PAXG tokens on the $ETH network.
So far, $USDT on the #Avalanche and #Solana has been frozen by @Tether_to.
The only other assets that can be frozen are the 33,184.98 $PAXG tokens on the $ETH network.

Platforms Used:
@1inch
@CurveFinance
@CoWSwap
@PancakeSwap
@MultichainOrg
@StargateFinance
@KyberSwap
@1inch
@CurveFinance
@CoWSwap
@PancakeSwap
@MultichainOrg
@StargateFinance
@KyberSwap
Notable Transactions
1/FTX Accounts Drainer bridged 4,375 ETH from BSC to Polygon via Multichain.
Current Status: "Big Amount"
anyswap.net/explorer/tx?pa…
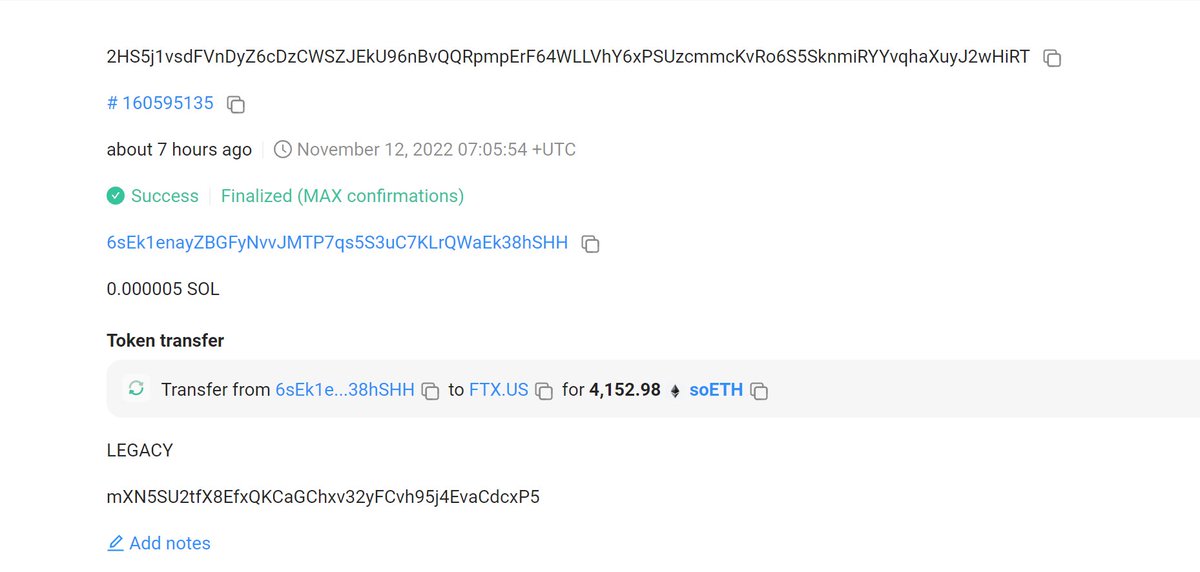
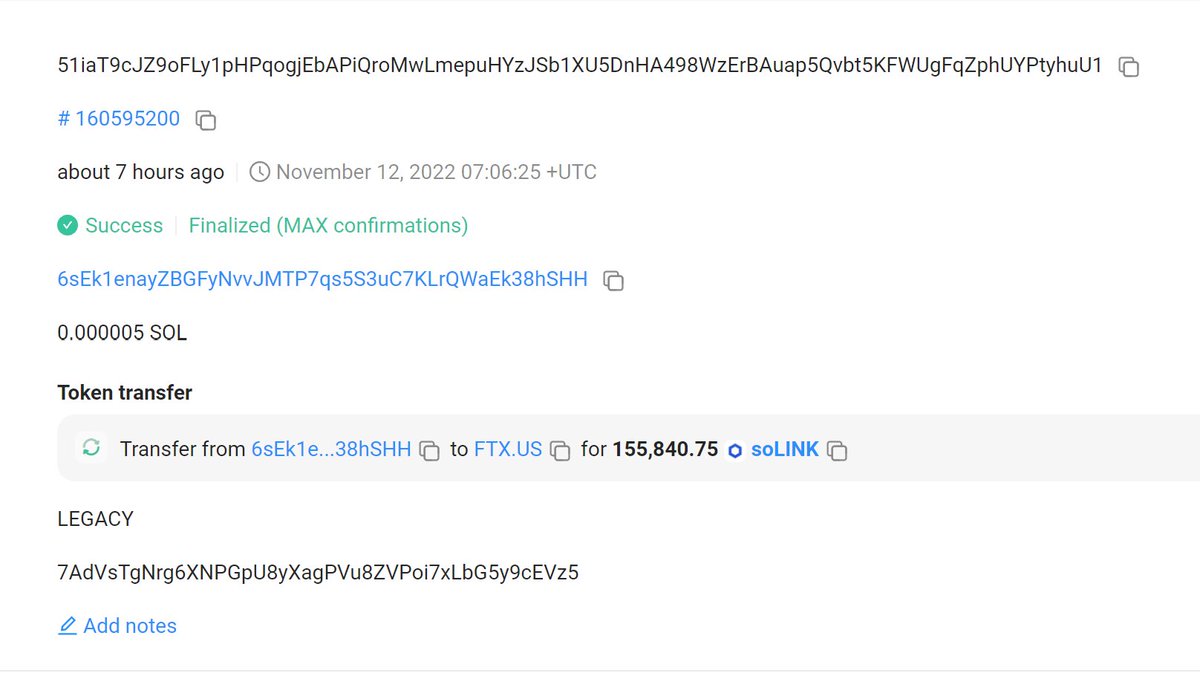
2/Solana chain, Drainer returned 3,138.99 BTC, 4,152.98 soETH and 155,840.75 soChainlink back to FTX US hot wallet.


1/FTX Accounts Drainer bridged 4,375 ETH from BSC to Polygon via Multichain.
Current Status: "Big Amount"
anyswap.net/explorer/tx?pa…
2/Solana chain, Drainer returned 3,138.99 BTC, 4,152.98 soETH and 155,840.75 soChainlink back to FTX US hot wallet.
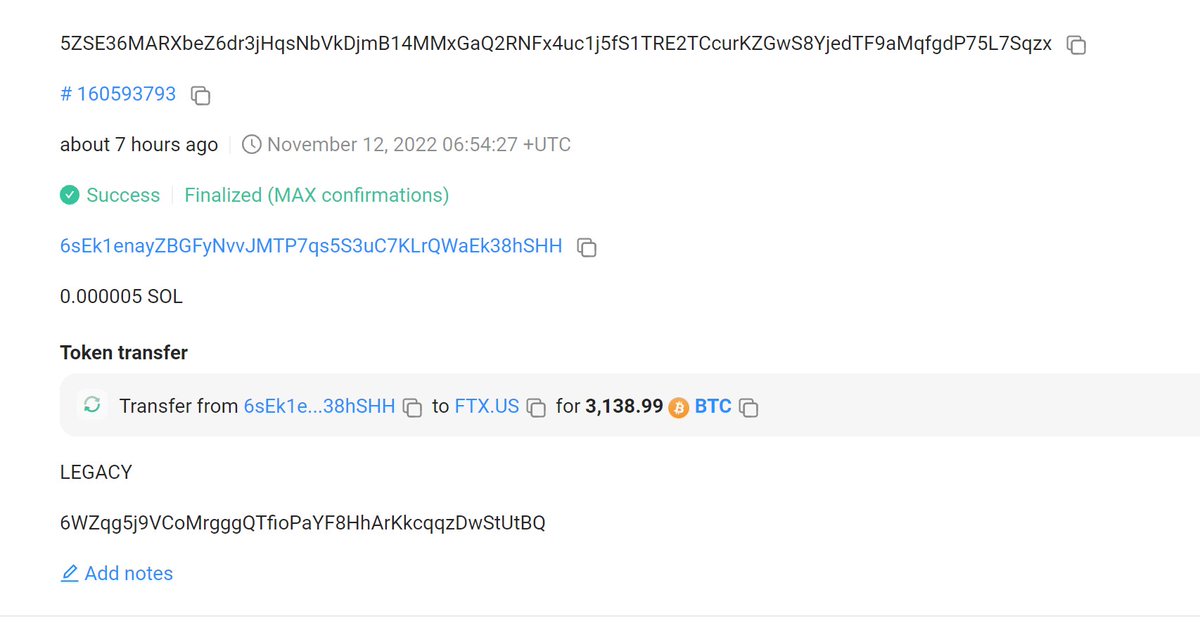
Suspected Whitehats
EOA 1: 0xd801..a969
Contract 1: 0x97f9..1E5c
Contract 1 is a multi-signature contract address, labeled as FTX by @etherscan.
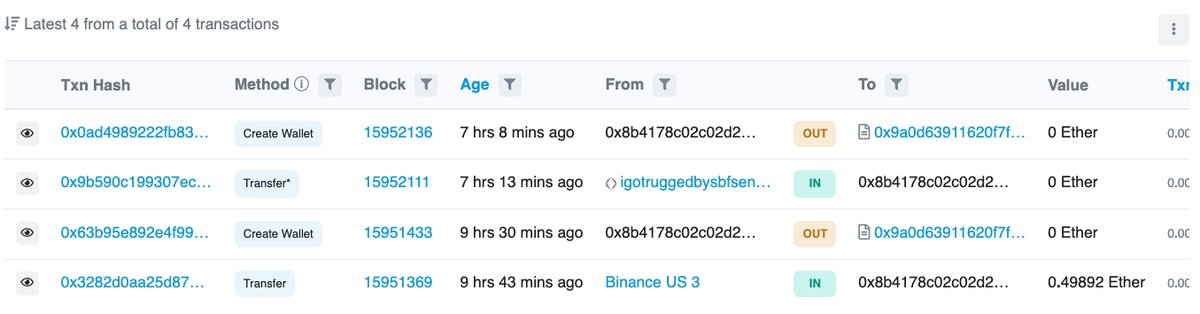
EOA 2: 0x8b41..ae4a
Contract creation fees originated from @BinanceUS.
EOA 1: 0xd801..a969
Contract 1: 0x97f9..1E5c
Contract 1 is a multi-signature contract address, labeled as FTX by @etherscan.
EOA 2: 0x8b41..ae4a
Contract creation fees originated from @BinanceUS.
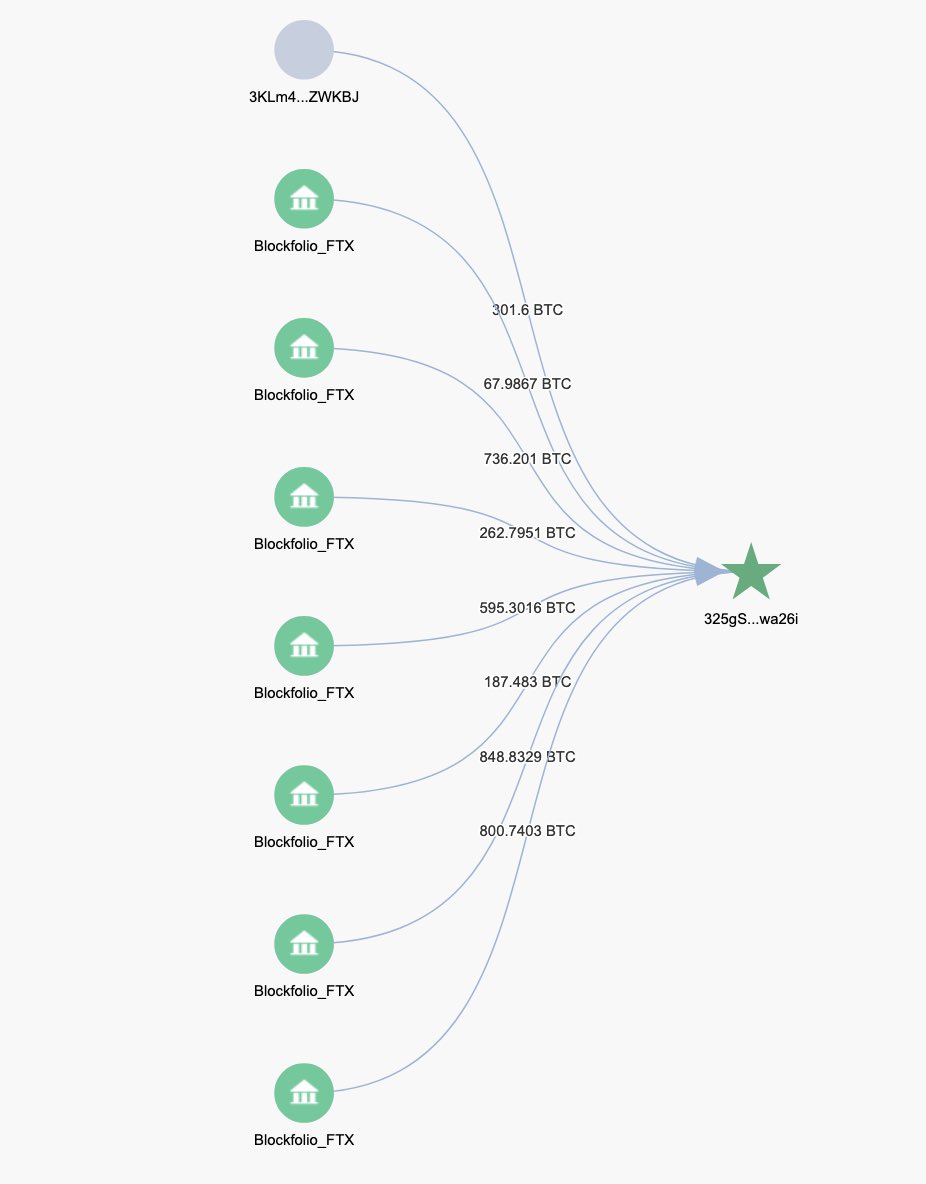
Update, FTX Bitcoin wallet was affected too. 3871.69 $BTC was stolen as well. That’s another ~$65 million.
All funds were sent to 325gSHHe7UGvzEc9kGx43VqPboXUVwa26i

All funds were sent to 325gSHHe7UGvzEc9kGx43VqPboXUVwa26i
https://twitter.com/ErgoBTC/status/1591431824290480130?s=20&t=blGUMLBuwAUb5Y_UzK4phg
• • •
Missing some Tweet in this thread? You can try to
force a refresh