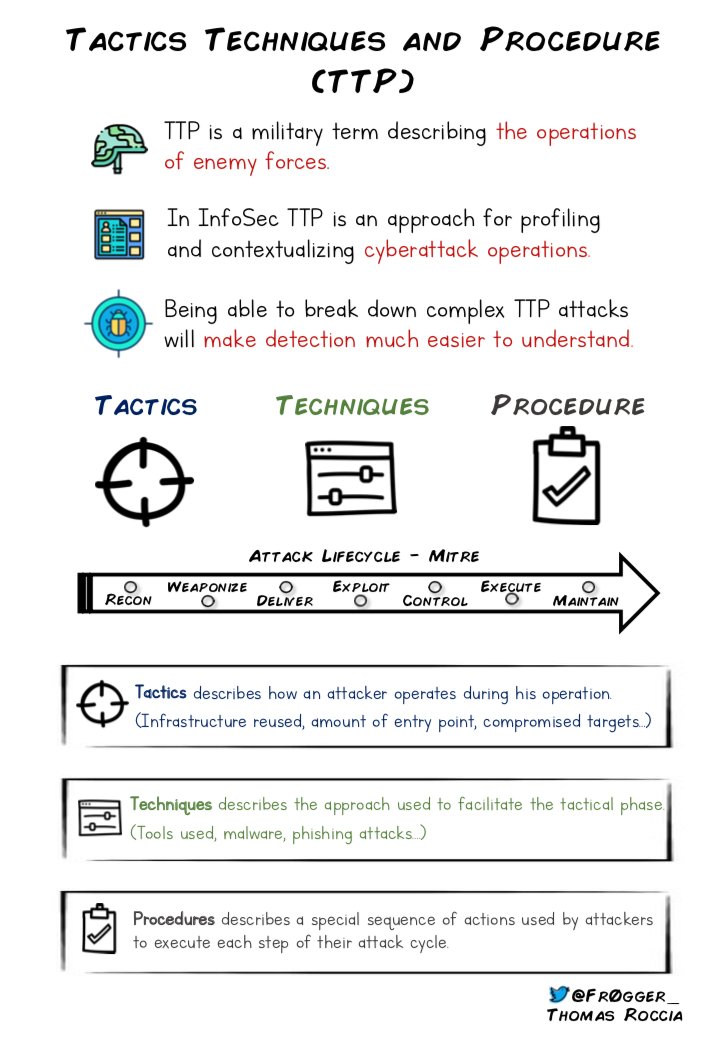
📢I recently investigated a campaign targeting the cryptocurrency industry. I wrote a detailed report that includes TTP, IOC and more. Here is a thread about this attack! 🧵👇
@MsftSecIntel @MicrosoftAU #infosec #cryptocurrency #threatintelligence #apt
microsoft.com/en-us/security…
@MsftSecIntel @MicrosoftAU #infosec #cryptocurrency #threatintelligence #apt
microsoft.com/en-us/security…
The attack started on Telegram to identify the targets, then they deployed a weaponized Excel document which finally delivered the final backdoor through multiple mechanisms. ☠☠️ #infosec #malware #backdoor 

🧐To identify the targets, the threat actor sought out members of cryptocurrency investment groups on Telegram.
👀They created fake profiles using details from employees of the company OKX. #infosec #Cryptocurency
👀They created fake profiles using details from employees of the company OKX. #infosec #Cryptocurency

🤝After gaining the trust of the target, the threat actor sent a weaponized Excel document to the target containing further details on the fees to appear legitimate.
💀The macro is obfuscated and abuses UserForm to store data and variables. #infosec #threatintel #malware
💀The macro is obfuscated and abuses UserForm to store data and variables. #infosec #threatintel #malware

☠️The macro then dropped another Excel sheet and executed it in invisible mode. This sheet was encoded in base64 and dropped into C:\ProgramData\Microsoft Media\ as VSDB688.tmp. #malware 

👾The VSDB688.tmp file then downloaded a PNG file from OpenDrive containing three executables: a legitimate Windows file, a malicious DLL, and a XOR encoded backdoor. #malware 



💀The legitimate file was used to sideload the malicious DLL, which acted as a proxy to the legitimate DLL and loaded the XOR encoded backdoor. #backdoor 

The malicious wsock32.dll is loaded by logagent.exe through DLL side-loading and uses DLL proxying to call the legitimate functions from the real wsock32.dll. The screenshot shows the redirection of the function in the malicious dll. #malware #infosec 

☠️The malicious wsock32.dll loads and decodes the final implant into the memory with the GUID name which is used to remote access the infected machine. #malware 

🧐We identified several related attacks that deployed the same payload in trojanised applications. #cryptocurrency #malware #threatintel 

🛡️Recent targeted attacks on the cryptocurrency industry highlight the need for organizations to prioritize cybersecurity and remain vigilant against potential threats.
@Volexity recently published a similar report about this attack.
volexity.com/blog/2022/12/0…
@Volexity recently published a similar report about this attack.
volexity.com/blog/2022/12/0…
More details including detection, IOCs, hunting rules and @MITREattack techniques are available in the blog. #infosed #threatintel #malware 👇
microsoft.com/en-us/security…
microsoft.com/en-us/security…
Thanks to @ravitiwari1989 @r3srch3r @fancy_4n6 and @bmcder02 for their help in the analysis and detection! ❤️
Thanks @BleepinComputer @LawrenceAbrams @serghei for quoting our investigation! 🙂
bleepingcomputer.com/news/security/…
bleepingcomputer.com/news/security/…
• • •
Missing some Tweet in this thread? You can try to
force a refresh