I've been in this industry basically my whole life and I still don't know what some of these phrases actually mean but as you install it, you get Marketing :)
"ENTERPRISE GRADE".. marketing people should use a dictionary etc. this doesn't make sense as a phrase to anyone ;) but… twitter.com/i/web/status/1…


"ENTERPRISE GRADE".. marketing people should use a dictionary etc. this doesn't make sense as a phrase to anyone ;) but… twitter.com/i/web/status/1…


ok weeeeeeeeeeeeeeeeeee we have the product installed!
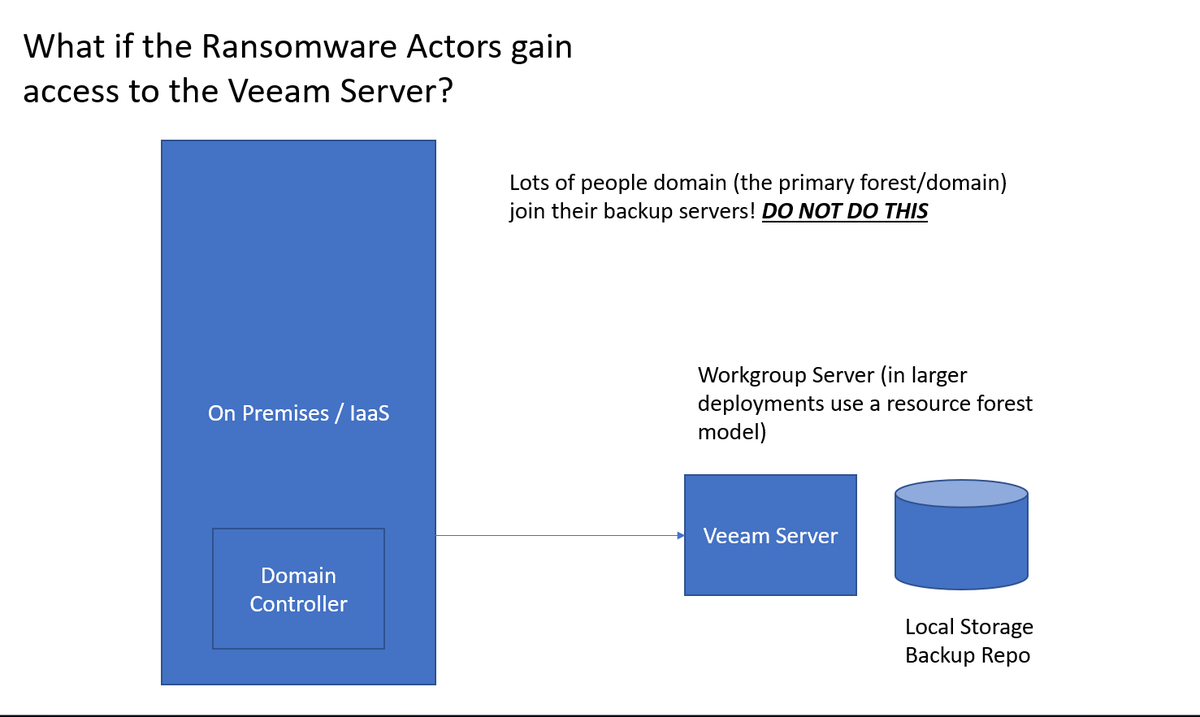
Now in a biz env. we would normally want a resource forest. We could have made this a domain controller for the lab but workgroup mode so we will be accepting the risk of sending NTLM authentication. We are however NOT… twitter.com/i/web/status/1…
Now in a biz env. we would normally want a resource forest. We could have made this a domain controller for the lab but workgroup mode so we will be accepting the risk of sending NTLM authentication. We are however NOT… twitter.com/i/web/status/1…

ok let's go tweeps! PROTECT all teh things with @Veeam ! 

(they aren't paying me nor did they ask me to write any of this stuff, I just like the software) but it's nice to be able to get pricing quickly, for larger deployments you will need to go through the human sales process 



oh ooops i'm sleepy and on autopilot, we want to use a REFS file system with 64K cluster sizes for this! (not NTFS) 
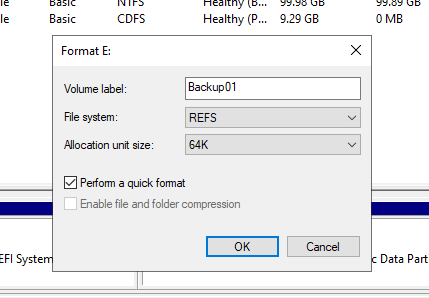
now this is in the lab and i'm doing this fast. think about your storage! i'm just gonna use the new virtual disk i just made for this demo 

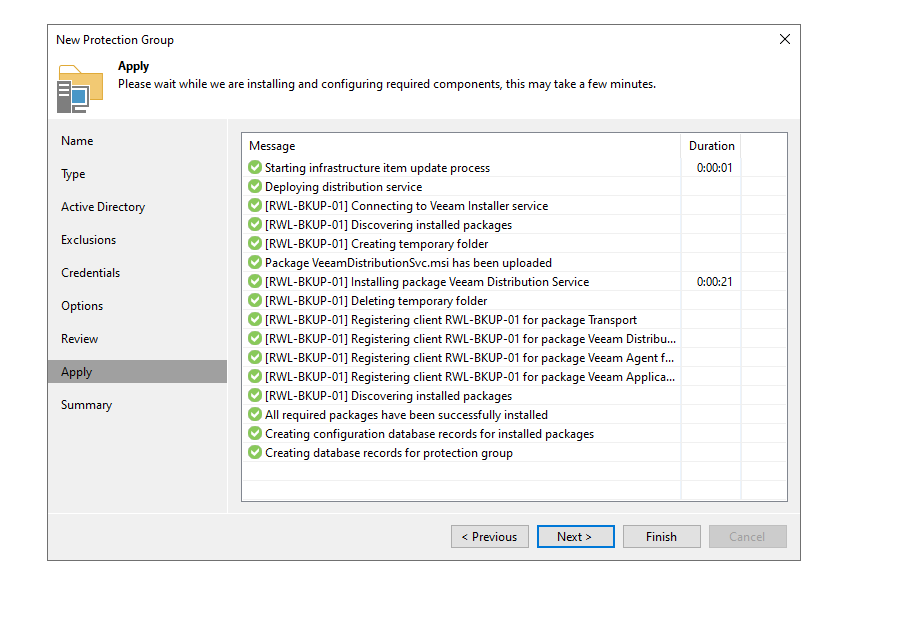
now we need to create a protection group, we are configuring bits and bops (in a not great way on purpose) i'm also doing the DC first because it has the right ports open and i've not domain joined the members yet :D 





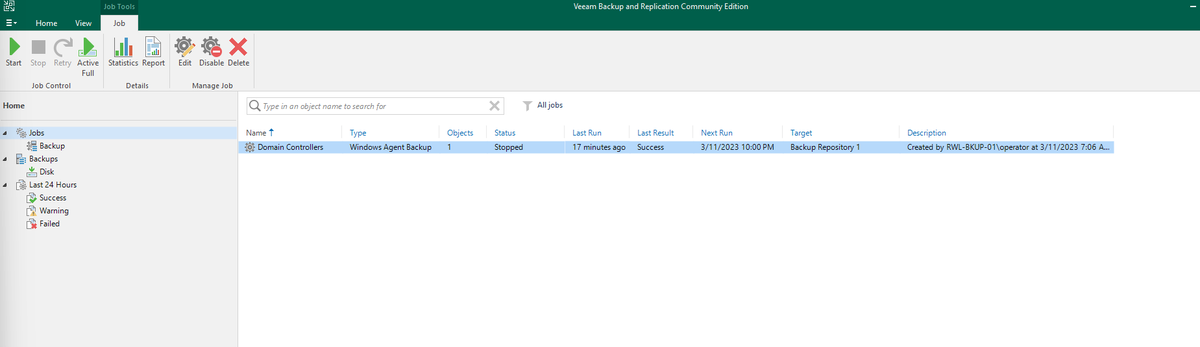
ok we have now deployed the agent from the veeam console and then rebooted the domain controller! #winning 

look frens we haz a Domain Controller backed up! wooohoo!
now let's get some tea and think about what else we need to do!

now let's get some tea and think about what else we need to do!

I can't stress this enough, with most backup products and solutions you can fuck urself by domain joining components or by leaving management interfaces available and having keepass or whatever password storage mechanisms compromised. I know of lots of orgs who have mASSIVE XLS… twitter.com/i/web/status/1…
but it's so easy to do. take people who:
> are time constrained
> are not trained
> are not given specialist security training
> do not have good leadership and management support
and you will get a recipe for a disaster that may come in many shapes and forms!
> are time constrained
> are not trained
> are not given specialist security training
> do not have good leadership and management support
and you will get a recipe for a disaster that may come in many shapes and forms!
now back to the scenario.. we want to ensure we know what can go wrong, but also what can go right! so far we have just setup a workgroup server with REFS storage, but what other options are there? A hardened LINUX repo! cloud object storage! backup copies! 

ok now we have a linux system. we can connect this to Veeam via SSH. We do however need to add some more storage! 

How do I list disks on Linux? I mean I look this stuff up, I can barely remember what day it is :P
lsblk
ok coo look we have a new physical DISK /dev/sdb/
(sda = disk 0)
(sdb = disk 1)
lsblk
ok coo look we have a new physical DISK /dev/sdb/
(sda = disk 0)
(sdb = disk 1)

ok so there's some fun with this... I'm going fast and doing it a bit shitty so don't copy me :P
We now have a hardened linux repo:
#############
lsblk
sudo apt install zfsutils-linux
sudo zpool create pool01 /dev/sdb
df
sudo zfs create pool01/veeam
sudo zfs set quota=95GB… twitter.com/i/web/status/1…
We now have a hardened linux repo:
#############
lsblk
sudo apt install zfsutils-linux
sudo zpool create pool01 /dev/sdb
df
sudo zfs create pool01/veeam
sudo zfs set quota=95GB… twitter.com/i/web/status/1…

• • •
Missing some Tweet in this thread? You can try to
force a refresh