1/9 The Chickens Are Clucking, and the Cows Are Mooing With Delight! Why? Because these CoWs are much hard to become the recipe of sandwiches. Our research shows that 🥪 MEV's impact on
#CoWSwap is One Magnitude Lower Than on Any Other DEX.docs.google.com/document/d/1lu…
#CoWSwap is One Magnitude Lower Than on Any Other DEX.docs.google.com/document/d/1lu…
2/9 🥪 frequency: in 2022, 1.9K 🥪 attacked CoW Swap's 239K trades, meaning sandwich MEV only accounted for about 0.8% of all the transactions on CoW Swap. 

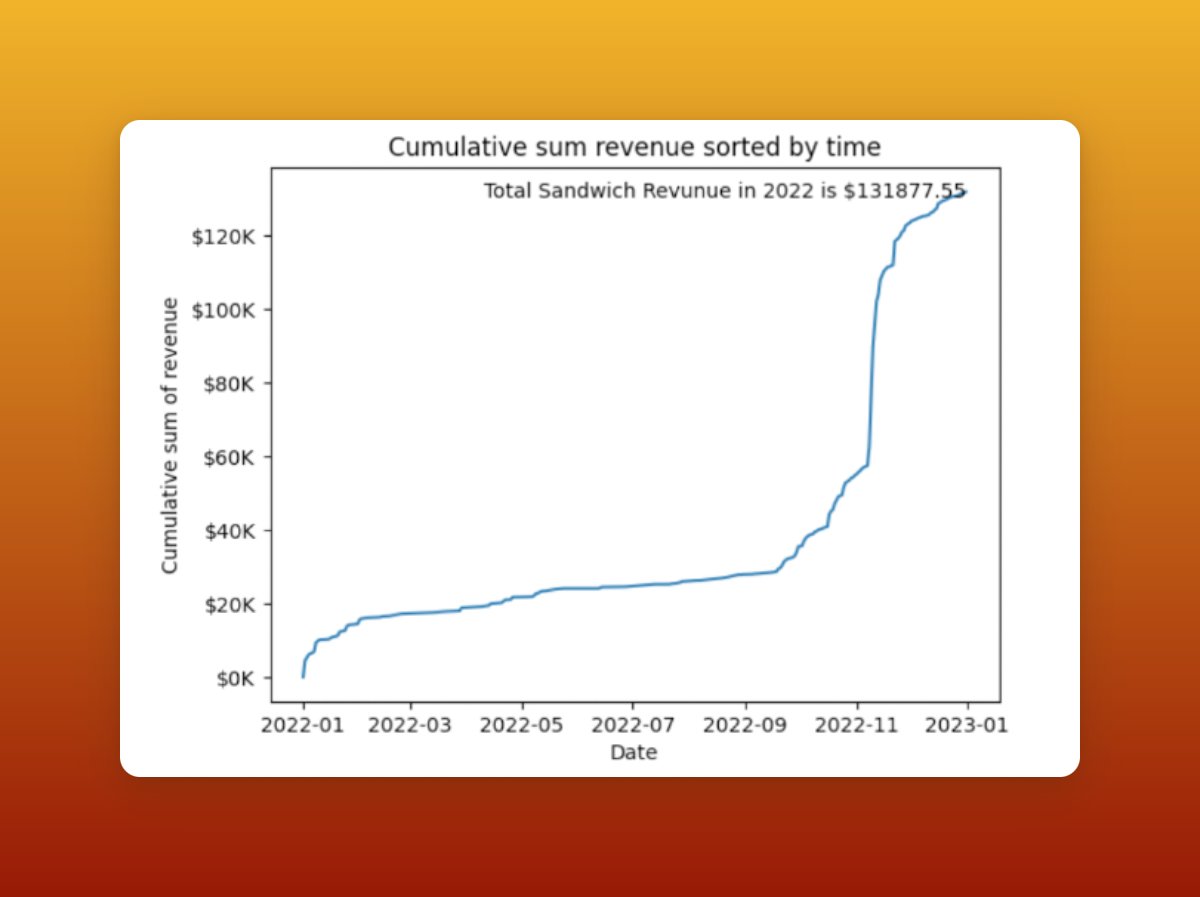
3/9 🥪 revenue: Sandwich attacks extracted $0.13 million from CoW Swap solvers. Compared to CoW Swap's total fee revenue of $8.55 million, sandwich attacks only accounted for around 1.5%. Through CoW Swap, the % of attacks is one magnitude lower than #Uniswap. 
4/9 In 2022, CoW Swap executed approximately 282K trades through Uniswap, 1.3K of which suffered 🥪 attacks in Uniswap pools. The percentage of attacks is 0.047%. In contrast, Uniswap had 39.6M trades in 2022, with attacks on 0.5M. The rate of trades attacked is 1.26%. 

5/9 🥪 Impact on 3 aggregators:
🥪 impacted around 2.7% of all txs through #1inch, attacked volume at 3.2%. Matcha suffered 1.9% on all trades, w/t attacked volume at 6%. Only 0.7% of trades and volume were attacked through CowSwap, the least exploited among the 3 aggregators.

🥪 impacted around 2.7% of all txs through #1inch, attacked volume at 3.2%. Matcha suffered 1.9% on all trades, w/t attacked volume at 6%. Only 0.7% of trades and volume were attacked through CowSwap, the least exploited among the 3 aggregators.


6/9 🥪 Volume: $0.12B in vol was affected by 🥪, which accounts for 0.79% of Cow Swap's total vol, w/t orders mostly ranging between $1K-$10K. In addition, the volume of CoW Swap batched value attacked was only 0.78% of the total, also one magnitude lower than other DEXs. 


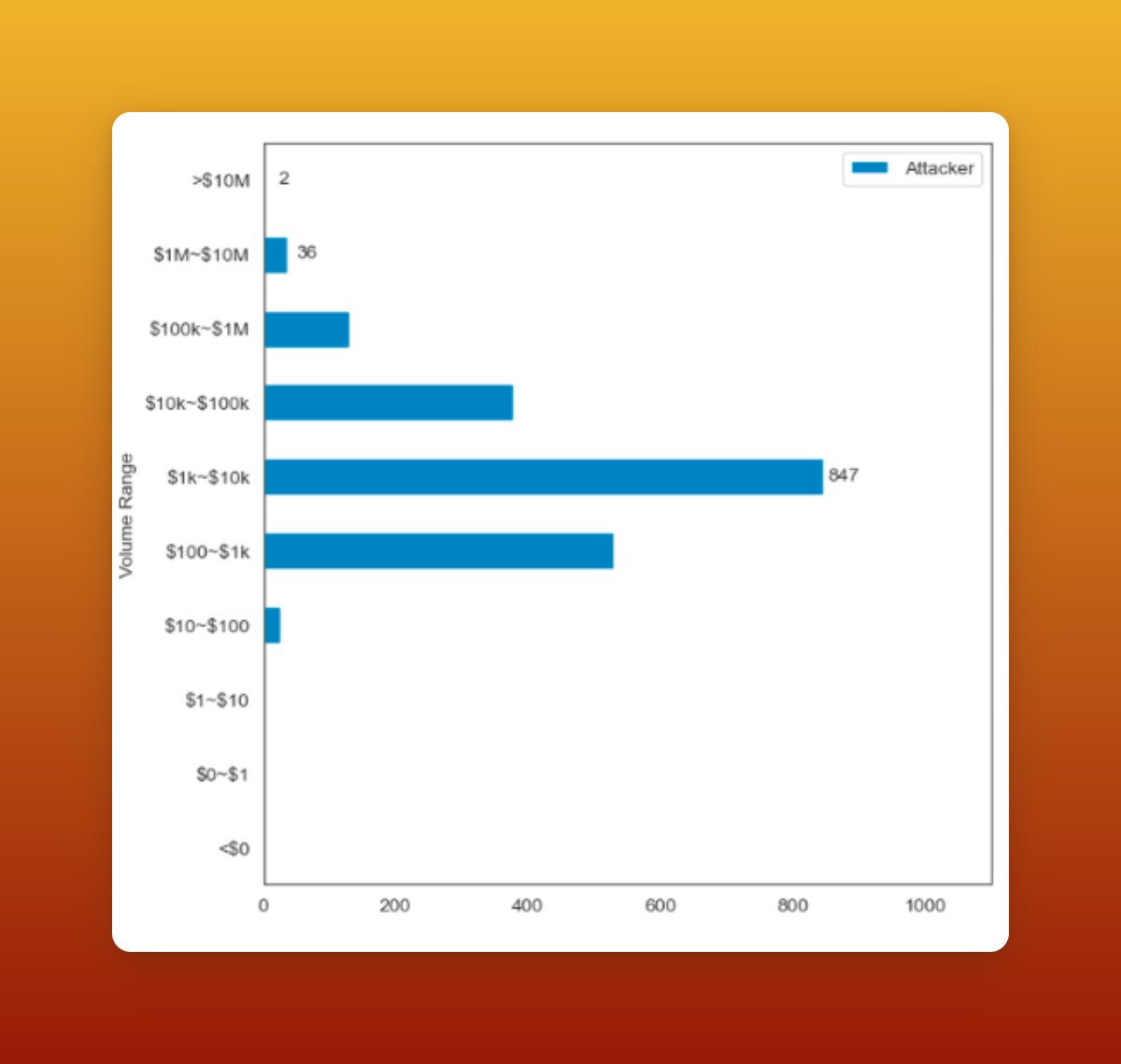
7/9 🥪 details on Solvers: After the Merge, the daily number of solvers attacked increased. We identified 27 solvers under attack in 2022 based on our data. They are ranked based on the number of attacks they have experienced and the total volume attacked. 

8/9 🥪 details on Exploited Protocols: There have been a total of 8 protocols that attackers have targeted. Uniswap v2 and v3 have been the most frequently attacked protocols, as they have a higher total trade volume from CoW Swap than other protocols. 



9/9 The figures and charts above are just drops in the pool of the whole report. To read the full report including data shown below, visit: docs.google.com/document/d/1lu…
HAPPY DIGESTING!! 🐮🤠
HAPPY DIGESTING!! 🐮🤠

• • •
Missing some Tweet in this thread? You can try to
force a refresh

 Read on Twitter
Read on Twitter










