1/
I’ve read several misconceptions about how a wallet works. It seems some people thought there is some magic, let me explain how it works.
A thread 👇
I’ve read several misconceptions about how a wallet works. It seems some people thought there is some magic, let me explain how it works.
A thread 👇
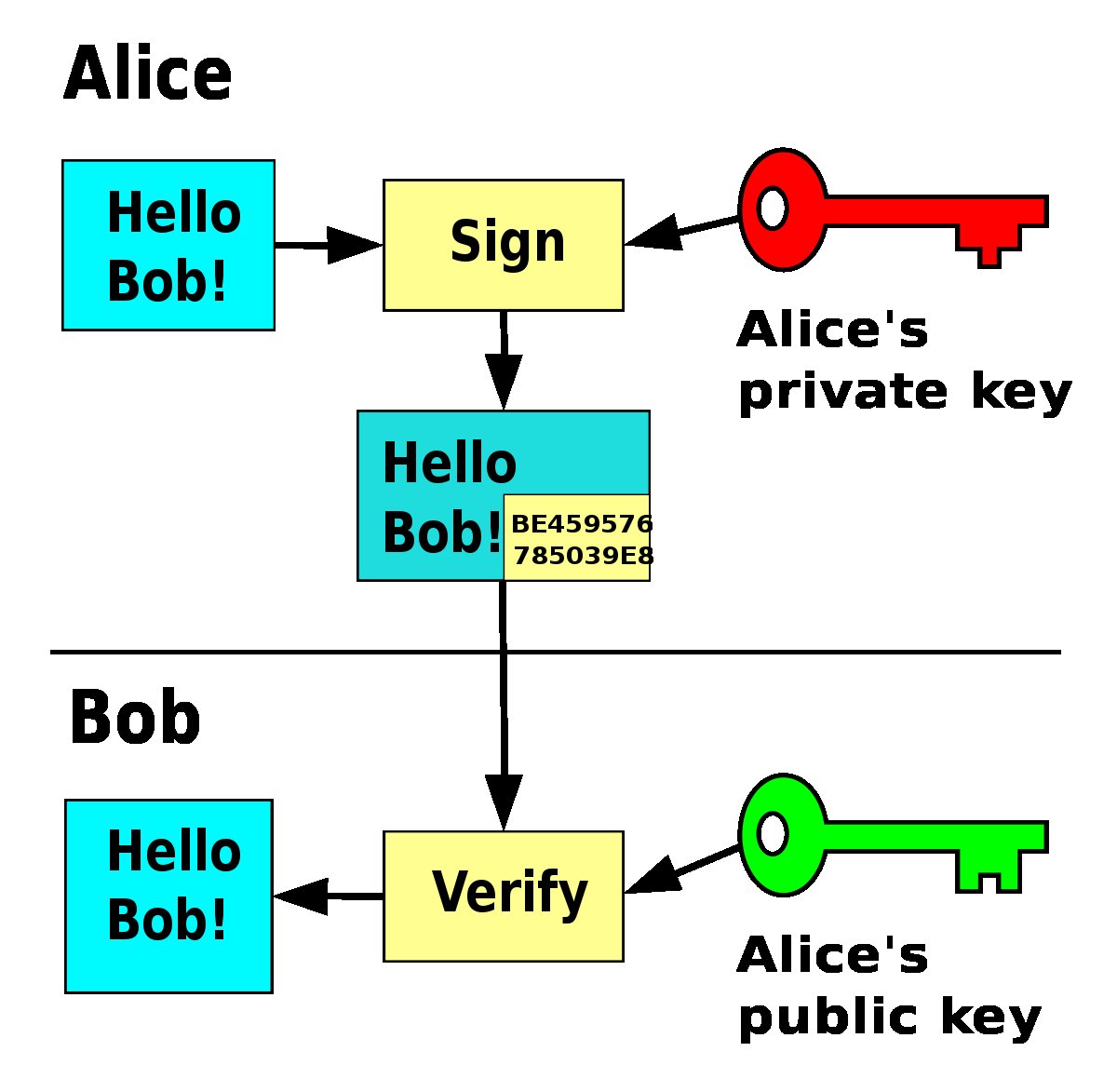
2/ A hardware wallet is mostly used as a signing device.
Your private keys are central to everything, and hardware + firmware work hand in hand to protect it.
Let’s review some fundamental cryptography about all hardware wallets, not just Ledgers.
Your private keys are central to everything, and hardware + firmware work hand in hand to protect it.
Let’s review some fundamental cryptography about all hardware wallets, not just Ledgers.
3/ Asymmetric cryptography.
Protocols such as #bitcoin and #ethereum use an algorithm called Elliptic Curve Digital Signature to essentially prove ownership over a public address.
It’s practically impossible to retrieve the private key knowing the public key (thus asymmetic)
Protocols such as #bitcoin and #ethereum use an algorithm called Elliptic Curve Digital Signature to essentially prove ownership over a public address.
It’s practically impossible to retrieve the private key knowing the public key (thus asymmetic)
4/
How does it apply to a hardware wallet?
When you set up your hardware wallet, the hardware wallet (In Ledger’s case, its Secure Element chip which uses hardware designed for security and randomness) randomly generates a very large number (256 bits).
How does it apply to a hardware wallet?
When you set up your hardware wallet, the hardware wallet (In Ledger’s case, its Secure Element chip which uses hardware designed for security and randomness) randomly generates a very large number (256 bits).
5/
This number can be put into human readable form (24 words) using BIP-39 standard.
That is your Secret Recovery Phrase.
This is what you write down and should NEVER share with ANYONE, including Ledger.
Ledger does not have access to it, including if you use Ledger Recover.
This number can be put into human readable form (24 words) using BIP-39 standard.
That is your Secret Recovery Phrase.
This is what you write down and should NEVER share with ANYONE, including Ledger.
Ledger does not have access to it, including if you use Ledger Recover.
6/
When you set up a crypto account, private keys are deterministically derived from the seed using the BIP32 standard.
Each blockchain has a different derivation path. From these private keys, it’s possible to compute the public keys and then the public addresses.
When you set up a crypto account, private keys are deterministically derived from the seed using the BIP32 standard.
Each blockchain has a different derivation path. From these private keys, it’s possible to compute the public keys and then the public addresses.
7/
The public addresses then leave the hardware wallet to receive funds for instance.
Your private keys must remain secret.
They are used to compute these digital signatures that are the cryptographic primitives for transactions, staking, smart contract interactions…
The public addresses then leave the hardware wallet to receive funds for instance.
Your private keys must remain secret.
They are used to compute these digital signatures that are the cryptographic primitives for transactions, staking, smart contract interactions…
8/
A digital signature allows you to prove you own the private key corresponding to a public key without revealing it.
A hardware wallet gives more security guarantees since this computation occurs inside it, and it’s not exposed to potential malware on your computer.
A digital signature allows you to prove you own the private key corresponding to a public key without revealing it.
A hardware wallet gives more security guarantees since this computation occurs inside it, and it’s not exposed to potential malware on your computer.
9/
The firmware (in our case our Operating System) and hardware (the Secure Element in Ledger’s case) implement all the necessary functions to interact with blockchains, to secure your passwords, and to upgrade itself securely.
The firmware (in our case our Operating System) and hardware (the Secure Element in Ledger’s case) implement all the necessary functions to interact with blockchains, to secure your passwords, and to upgrade itself securely.
10/
It embeds a Ledger attestation that allows any device to prove it’s a genuine one. Thus it implements a lot of different signatures (compute and verify), encryption/decryption, hash… algorithms with various modes of operation.
It embeds a Ledger attestation that allows any device to prove it’s a genuine one. Thus it implements a lot of different signatures (compute and verify), encryption/decryption, hash… algorithms with various modes of operation.
11/
The blockchain ecosystem is moving fast - new protocols and features pop up everyday.
We would not be able to add Miniscript support for Bitcoin or BLS for Ethereum unless we could upgrade the firmware.
The blockchain ecosystem is moving fast - new protocols and features pop up everyday.
We would not be able to add Miniscript support for Bitcoin or BLS for Ethereum unless we could upgrade the firmware.
12/
Also, security is not static, it’s a never ending journey.
We are always raising the bar for security, sometimes fixing vulnerabilities. It’s important to be up-to-date.
It’s paramount for the firmware to be upgradable.
Also, security is not static, it’s a never ending journey.
We are always raising the bar for security, sometimes fixing vulnerabilities. It’s important to be up-to-date.
It’s paramount for the firmware to be upgradable.
13/
Our OS is an open platform. Anyone can write their own app and load it on the device.
The apps are loaded on the OS and can leverage these cryptographic primitives for their needs. Most of our apps have been written by the community and are open source.
Our OS is an open platform. Anyone can write their own app and load it on the device.
The apps are loaded on the OS and can leverage these cryptographic primitives for their needs. Most of our apps have been written by the community and are open source.
14/
But before being published on the “Ledger Manager”, they go through a security evaluation process.
But before being published on the “Ledger Manager”, they go through a security evaluation process.
15/
In order to provide some isolation, our model is the following:
- The OS has full access to the private key.
- The apps are locked on a list of given derivation paths according to their need
Ie. Bitcoin can only use Bitcoin keys, Ethereum can only use Ethereum keys.
In order to provide some isolation, our model is the following:
- The OS has full access to the private key.
- The apps are locked on a list of given derivation paths according to their need
Ie. Bitcoin can only use Bitcoin keys, Ethereum can only use Ethereum keys.
16/
Whenever a private key is touched by the OS, the user is prompted and their consent is requested:
- When you “allow manager”, you allow the device to mount a SCP with Ledger Hardware Secure Module (HSM). The device proves it’s genuine. The HSM proves it’s Ledger’s HSM.
Whenever a private key is touched by the OS, the user is prompted and their consent is requested:
- When you “allow manager”, you allow the device to mount a SCP with Ledger Hardware Secure Module (HSM). The device proves it’s genuine. The HSM proves it’s Ledger’s HSM.
17/
- When you go through a transaction, you consent to “send xxx BTC to yyy address”. Then the Bitcoin app will request the OS to sign the corresponding transaction with your Bitcoin key.
- When you go through a transaction, you consent to “send xxx BTC to yyy address”. Then the Bitcoin app will request the OS to sign the corresponding transaction with your Bitcoin key.
18/
- If you want to use Ledger Recover, you’ll have to consent on your device for the backup or the recovery process
- It’s the same for staking, interacting with smart contracts, and encrypting data with the OpenPGP app…
- If you want to use Ledger Recover, you’ll have to consent on your device for the backup or the recovery process
- It’s the same for staking, interacting with smart contracts, and encrypting data with the OpenPGP app…
19/
Using a wallet requires a minimal amount of trust. If your hypothesis is that your wallet provider is the attacker, you’re doomed.
Using a wallet requires a minimal amount of trust. If your hypothesis is that your wallet provider is the attacker, you’re doomed.
20/
If the wallet wants to implement a backdoor, there are many ways to do it, in the random number generation, in the cryptographic library, in the hardware itself. It’s even possible to create signatures so that the private key can be retrieved only by monitoring the blockchain
If the wallet wants to implement a backdoor, there are many ways to do it, in the random number generation, in the cryptographic library, in the hardware itself. It’s even possible to create signatures so that the private key can be retrieved only by monitoring the blockchain
21/
And open source doesn’t really solve this. It’s impossible to have guarantees that the electronic itself is not backdoored, nor that the firmware that runs inside the wallet is the one you audited.
And open source doesn’t really solve this. It’s impossible to have guarantees that the electronic itself is not backdoored, nor that the firmware that runs inside the wallet is the one you audited.
22/
If you want to be completely trustless, you'll have to learn electronics to build your computer, learn ASM to build your compiler, then build a wallet stack, your own node and synchronizer, you'll have to learn cryptography to build your own signature stack.
If you want to be completely trustless, you'll have to learn electronics to build your computer, learn ASM to build your compiler, then build a wallet stack, your own node and synchronizer, you'll have to learn cryptography to build your own signature stack.
23/
It’s a great journey, I partly went through this one 😅. But it’s a lifetime journey.
It’s a great journey, I partly went through this one 😅. But it’s a lifetime journey.
24/
We want to build a platform that provides strong guarantees about the code running on it from the supply chain to everyday's use and doesn't leak secrets when physically attacked.
Only a smartcard (Secure Element chip) can match those requirements
We want to build a platform that provides strong guarantees about the code running on it from the supply chain to everyday's use and doesn't leak secrets when physically attacked.
Only a smartcard (Secure Element chip) can match those requirements
25/
But smartcards come with restrictive NDAs.
The chip datasheet isn't public, which means there will never be a fully Open Source firmware for a smartcard - however we can gradually go to a Raspberry Pi model, with most of the code open and a small binary blob for the rest.
But smartcards come with restrictive NDAs.
The chip datasheet isn't public, which means there will never be a fully Open Source firmware for a smartcard - however we can gradually go to a Raspberry Pi model, with most of the code open and a small binary blob for the rest.
26/
All our applications are already Open Source, which is quite unique for a smartcard.
Ledger has the largest 3rd party developers ecosystem. And we plan to publish more low level components: we already released part of the crypto lib library, and the dashboard will come next.
All our applications are already Open Source, which is quite unique for a smartcard.
Ledger has the largest 3rd party developers ecosystem. And we plan to publish more low level components: we already released part of the crypto lib library, and the dashboard will come next.
27/
TL;DR:
A hardware wallet is mostly used as a signing device
It generates and safeguards your private keys.
Your private keys never leave the hardware wallet. Whenever they are used, your consent is requested.
TL;DR:
A hardware wallet is mostly used as a signing device
It generates and safeguards your private keys.
Your private keys never leave the hardware wallet. Whenever they are used, your consent is requested.
28/
You want to use Ledger Recover, your seed will be splitted into 3 shards and encrypted before being stored in shards backup providers.
All wallets need access to your seed/private keys in order to interact with blockchain protocols.
You want to use Ledger Recover, your seed will be splitted into 3 shards and encrypted before being stored in shards backup providers.
All wallets need access to your seed/private keys in order to interact with blockchain protocols.
29/
Hardware wallets give a higher level of security since keys are not manipulated in plaintext in a non secure environment.
FIN.
Hardware wallets give a higher level of security since keys are not manipulated in plaintext in a non secure environment.
FIN.
• • •
Missing some Tweet in this thread? You can try to
force a refresh

 Read on Twitter
Read on Twitter