
How to get URL link on X (Twitter) App


 site:example[.]com - Put your bug bounty target here!
site:example[.]com - Put your bug bounty target here!
 🔍 Google Dork:
🔍 Google Dork:
 🔍 Basic Prompt Injection:
🔍 Basic Prompt Injection:
 Combine:
Combine:
 Combine:
Combine:






 My prompt:
My prompt:
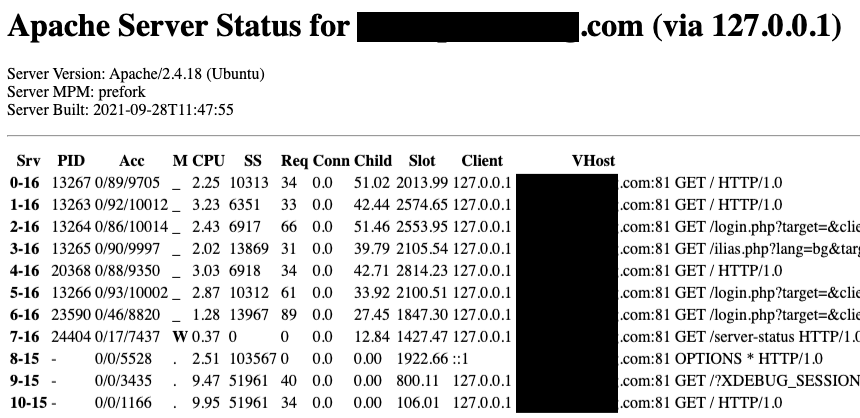
 Medium article w/ Apache server-status breakdown by @ghostlulz: medium.com/@ghostlulzhack…
Medium article w/ Apache server-status breakdown by @ghostlulz: medium.com/@ghostlulzhack…

 Combine:
Combine: