
AI threat intelligence @google
writing & sharing on adversary tradecraft, malware, threat detection, AI-nexus intel and all things #yara
How to get URL link on X (Twitter) App





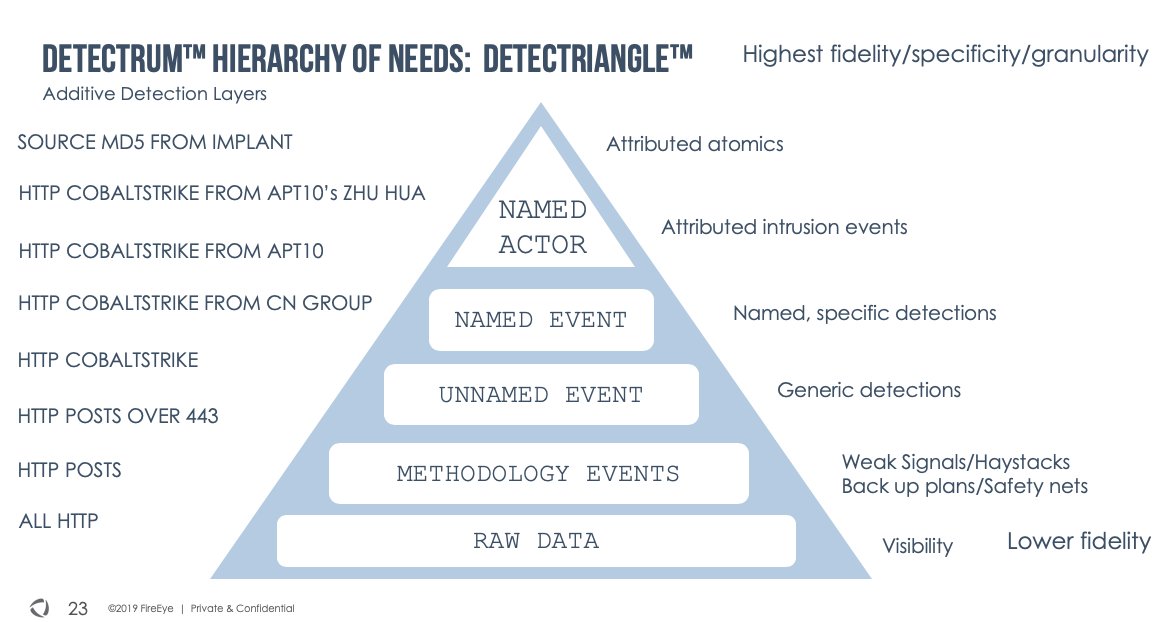
 I think the #DETECTRUM can be used to model both inputs and outputs of the detection engineering process - whether you're plotting "logic designed to find evil," alerts, the tech, or the or the data itself. The graphs might look a bit different, but same ideology might be useful
I think the #DETECTRUM can be used to model both inputs and outputs of the detection engineering process - whether you're plotting "logic designed to find evil," alerts, the tech, or the or the data itself. The graphs might look a bit different, but same ideology might be useful
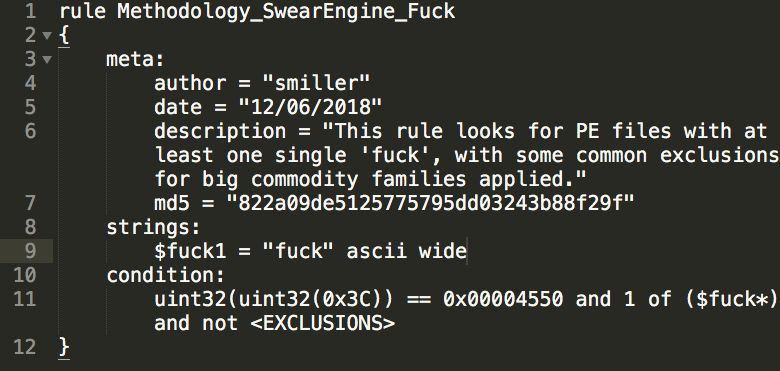
 You may balk at #SwearEngine for being #basic but consider that this rule, looking for PEs with one single "fuck", detects malware samples used by APT5, APT10, APT18, APT22, APT26, Turla, FIN groups, dozens of UNC espionage clusters. Too many to list.
You may balk at #SwearEngine for being #basic but consider that this rule, looking for PEs with one single "fuck", detects malware samples used by APT5, APT10, APT18, APT22, APT26, Turla, FIN groups, dozens of UNC espionage clusters. Too many to list.
https://twitter.com/stvemillertime/status/1061999557205143552The @CrowdStrike report does not discuss the biases nor provide real hard numbers on the TTPs, which I know from experience are hard to deduplicate on intrusions (some are over represented and some are under represented). Maybe @_devonkerr_ or someone can shed some light here.
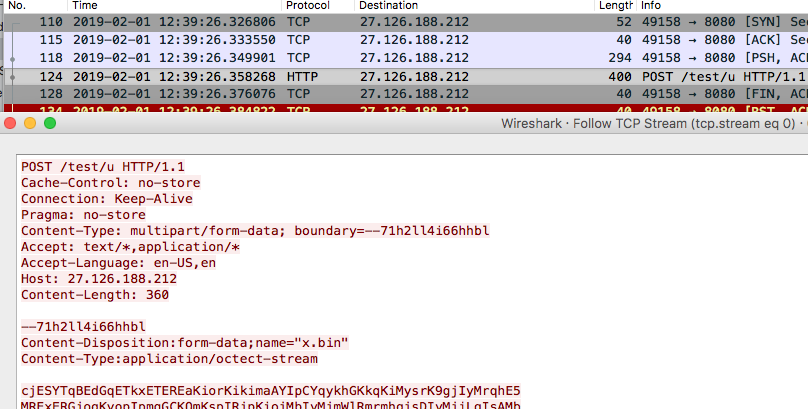
 This network traffic comes from newish backdoor ExileRAT (compiled 2019-01-30T07:05:47Z) 606e943b93a2a450c971291e394745a6 that was hanging (with a multitude of other evil) on recently #opendir "http://27.126.188[.]212" There are ties to a humongous cluster of probs CN espionage.
This network traffic comes from newish backdoor ExileRAT (compiled 2019-01-30T07:05:47Z) 606e943b93a2a450c971291e394745a6 that was hanging (with a multitude of other evil) on recently #opendir "http://27.126.188[.]212" There are ties to a humongous cluster of probs CN espionage. 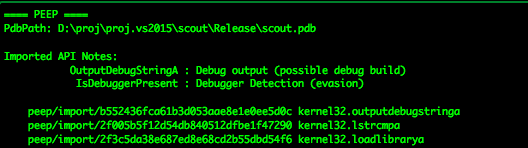
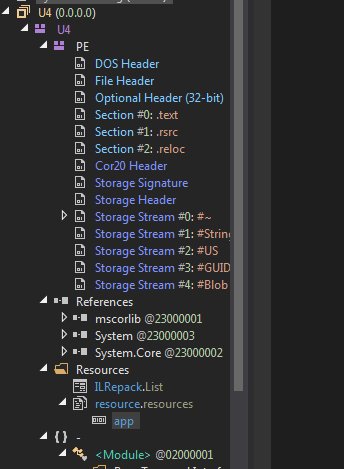
 5bbe762b83e051776f1b5ea30ffc0050 decompressed to the goliath ~8MB ca19c3c3c2ef656b33d7173a49186f5a (application/x-dosexec) which is also a .NET binary. Back in dnSpy, which nearly chokes on the size, we finally get to a main decryption routine.
5bbe762b83e051776f1b5ea30ffc0050 decompressed to the goliath ~8MB ca19c3c3c2ef656b33d7173a49186f5a (application/x-dosexec) which is also a .NET binary. Back in dnSpy, which nearly chokes on the size, we finally get to a main decryption routine. 
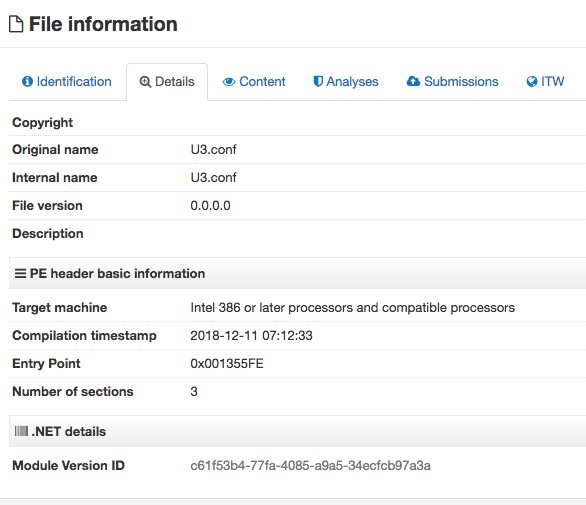
https://twitter.com/issuemakerslab/status/108802774664979251288017e9f2c277fa05ee07ecc99a0a2dc (홍삼6품단가 .xlsx) is a doc that has multiple follow-on payloads including 05683b9a13910d768b7982d013c31cb9 (U3.conf)... see also 홀리데이 와이퍼(Operation Holiday Wiper)로 귀환한 로켓맨 APT 캠페인 by @alac blog.alyac.co.kr/2089

