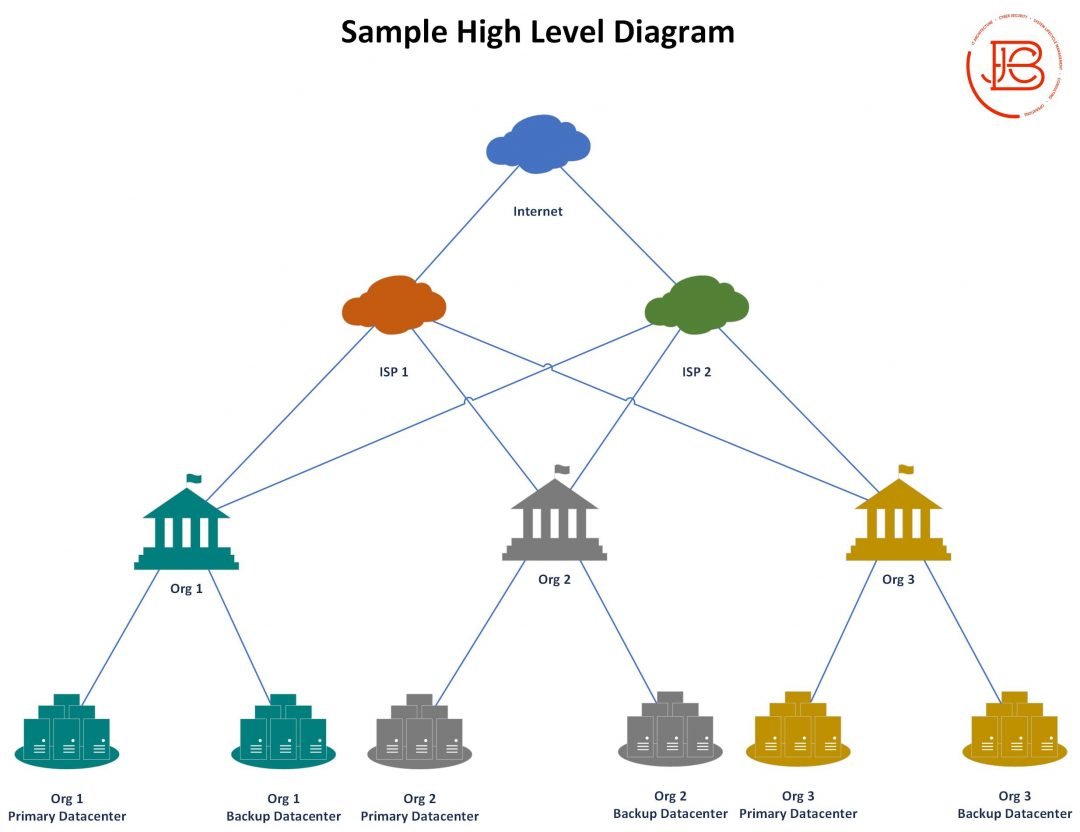
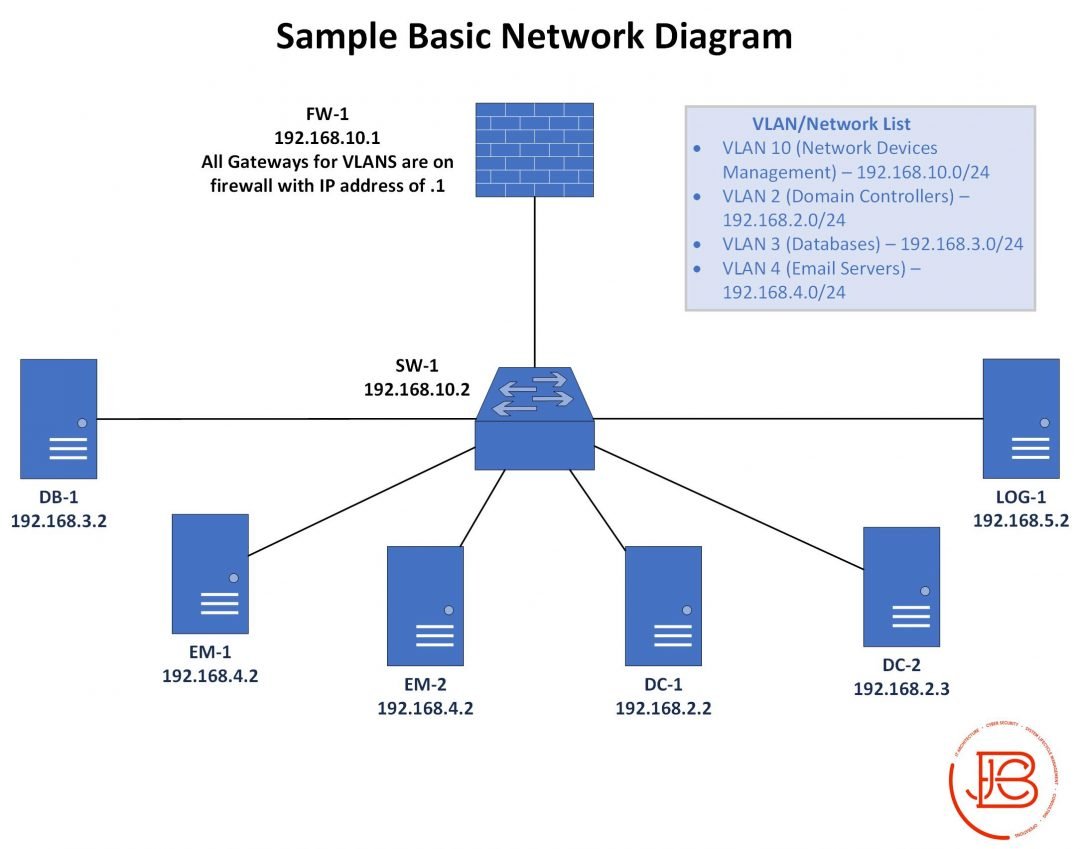
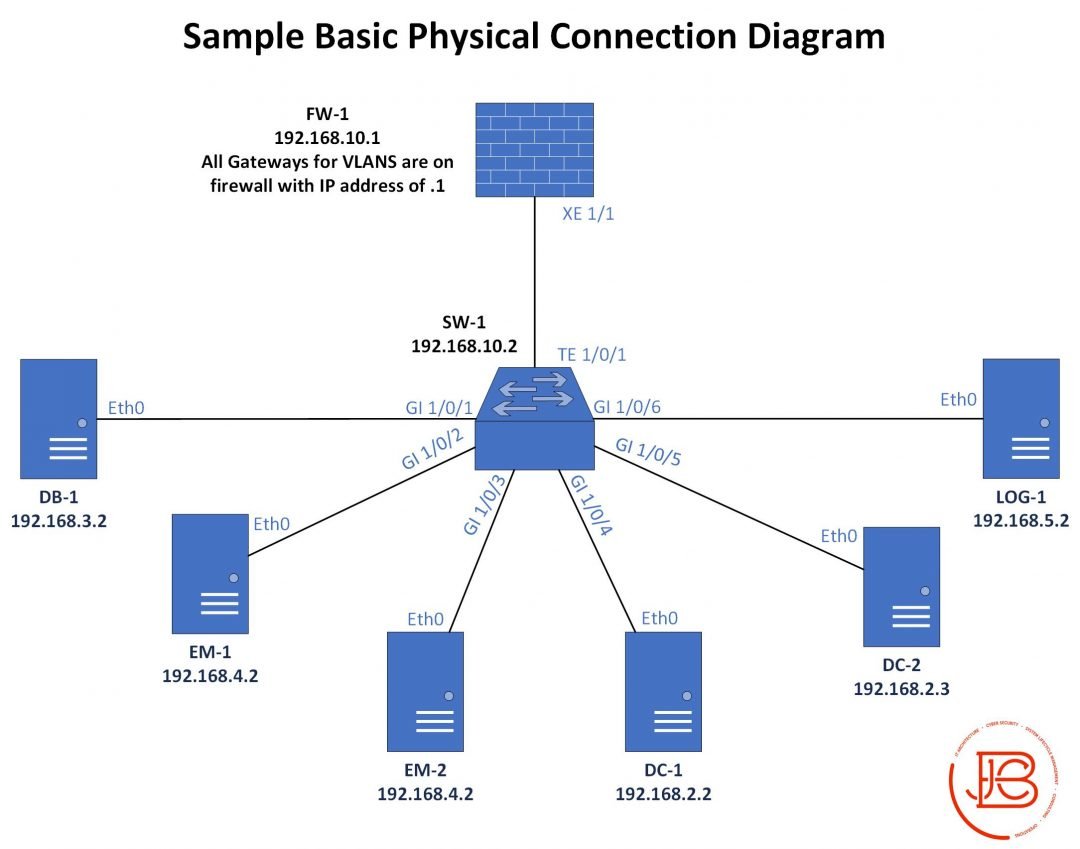
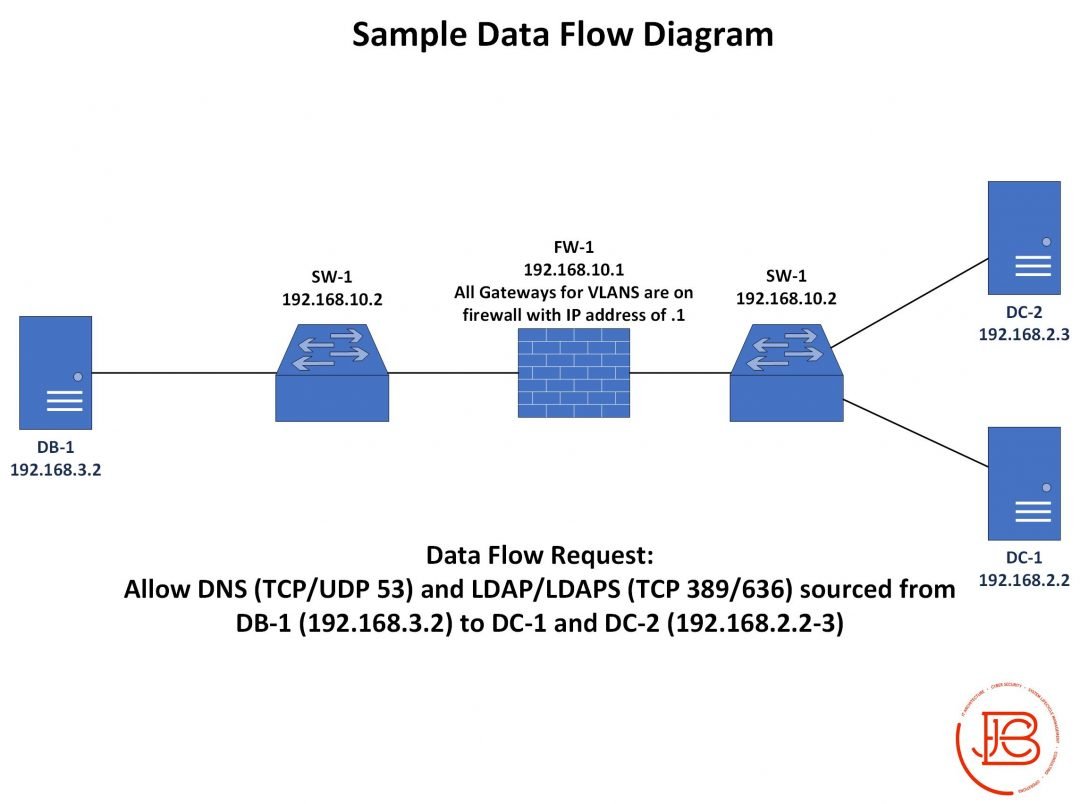
Random thoughts on planning a small office relocation. This is off the top of my head. So might change some steps IRL. Step one is going to be updated asset list/documentation/cable connections. What devices/software/data currently exists and what will need to be moved /1
https://twitter.com/GKnutley/status/1358186826700386304
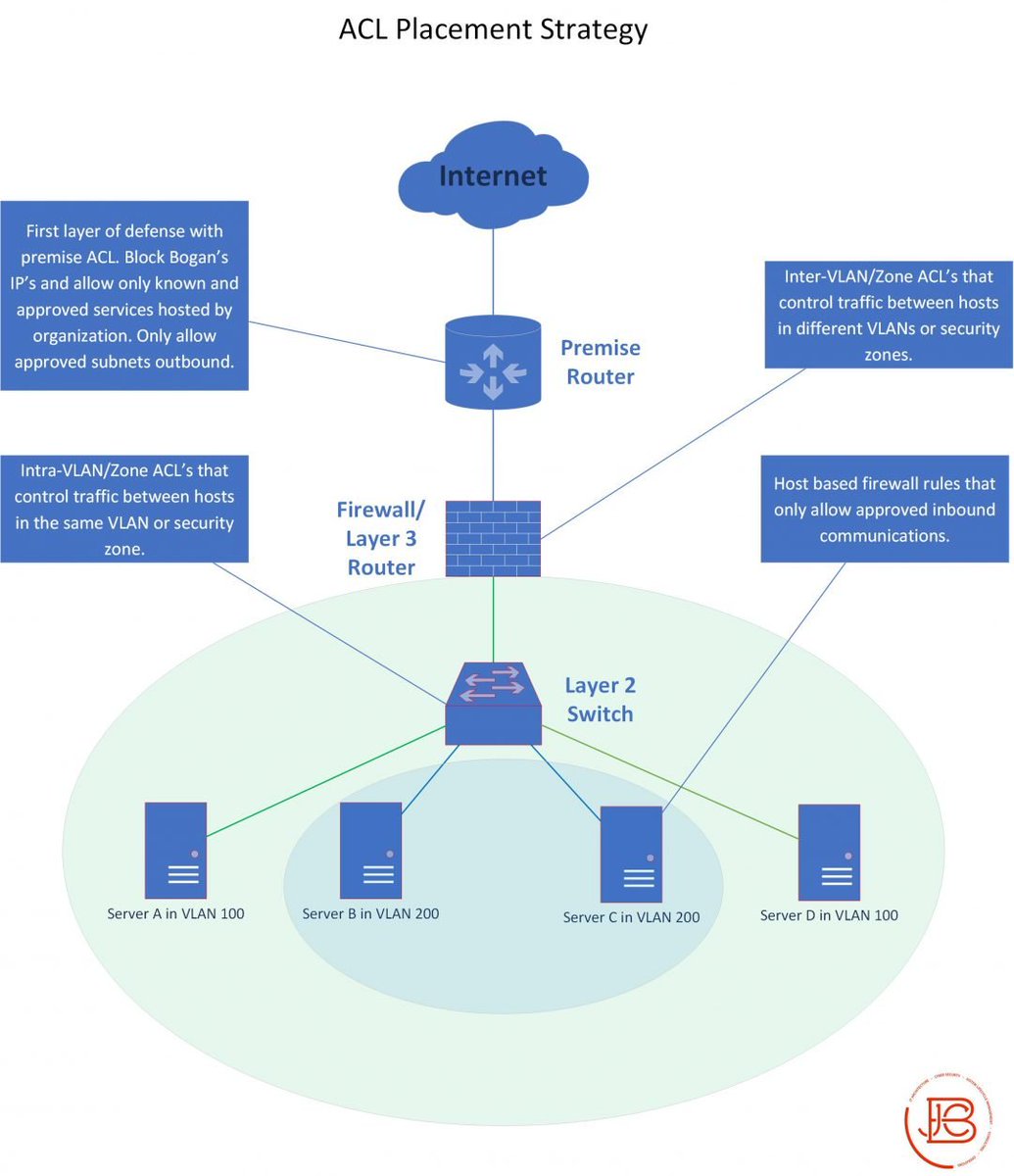
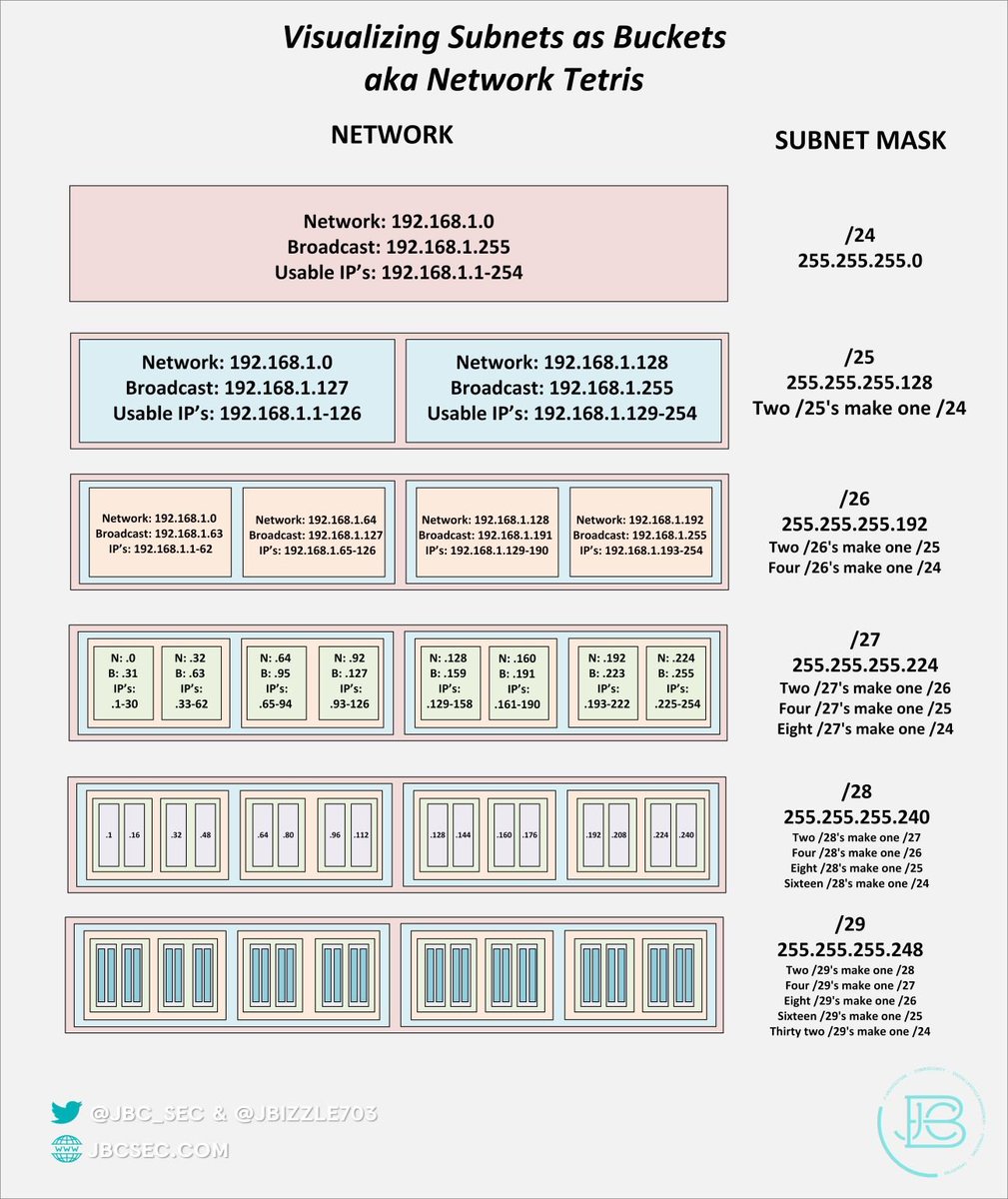
Figure out what IT closets/cabling options are in the new spot and plan accordingly and create transition documentation(cable plan, rack layouts, updated diagrams if needed . Pre-run/label as much as you can. Make sure you test these connections(cable drops to comms closets). /2
Backup all device configs/critical data as needed. If you can phase deployments, that is cool, but you might have to do a hard cut over. Figure out what you are doing for circuits (new or migrating). /3
Figure out order of operations for powering down devices safely. Don't assume you can just pull plugs, flip switches. Some devices need graceful shut downs to not corrupt data/state. Generally I'd start with end devices first, servers, SANs, then network devices /4
Pack devices carefully. Labeling and planning of what goes in which shipping boxing can make redeployment smoother from a logistical perspective. If you're lucky, data center/infrastructure cable plans stay the same and you can pack the prexisting labled cables. /5
Do the inverse of what the takedown operation was, bring up networks devices, SANs, servers, end devices. The prestaging of labeled cables will save you a lot of time here. Make sure you test as new functionalities are brought back online. /6
Test internal and external connectivity. In the earlier planning parts, it would make sense to have a testing checklist of expected responses for internal/external tools/services/data. /7
Take advantage of the fact that you have the ability to get your documentation 100% correct at this point in time. Ensure in your project planning that you build in the adequate amount of time for testing and documentation. /8
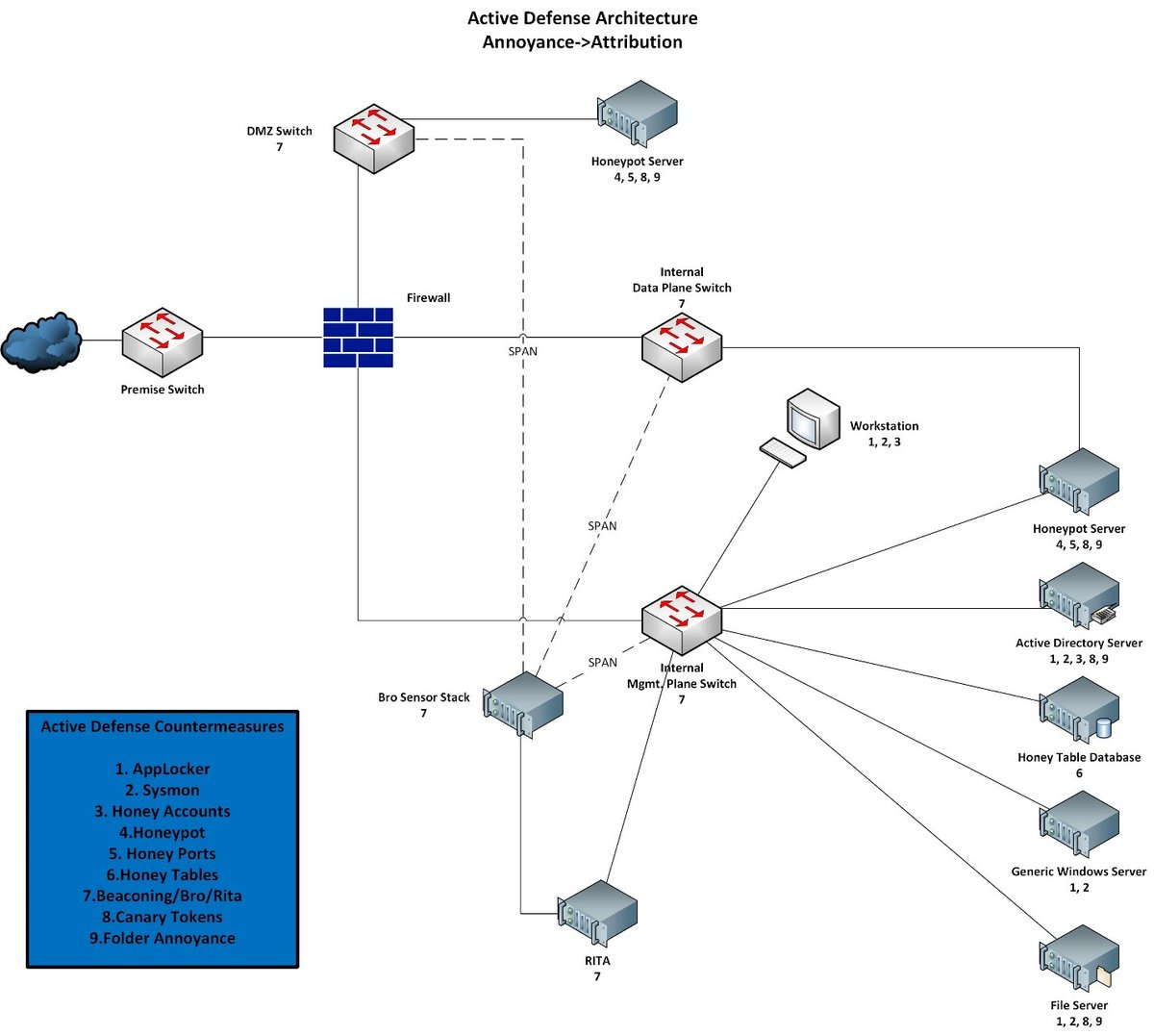
Lastly, don't forget to also do security testing. Yes it should be the same equipment/accounts/data, but maybe you added new security zones/devices/data flows. Validate the security/compliance/vulnerability posture (this may also include the physical security of the new location)
• • •
Missing some Tweet in this thread? You can try to
force a refresh