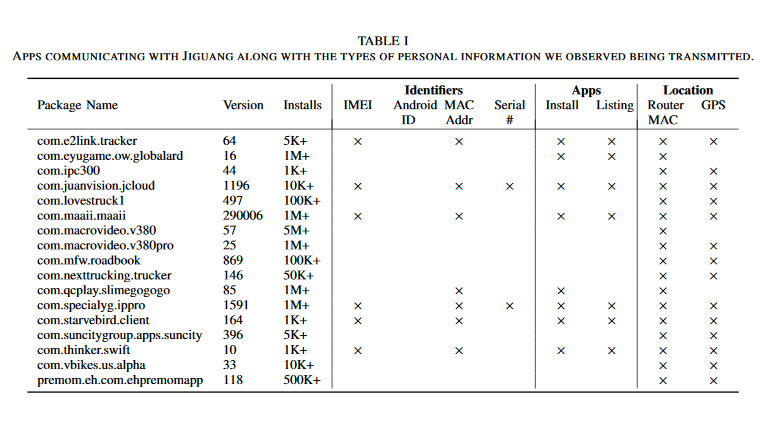
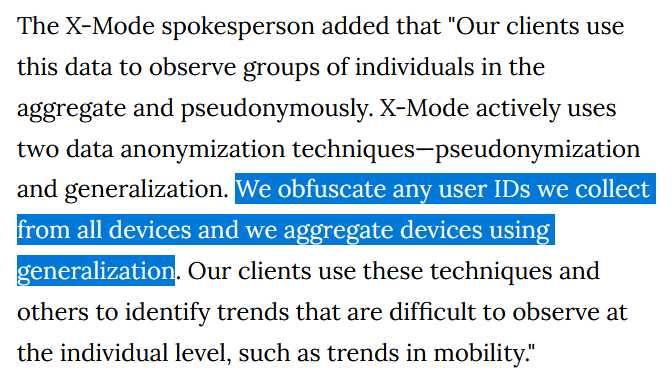
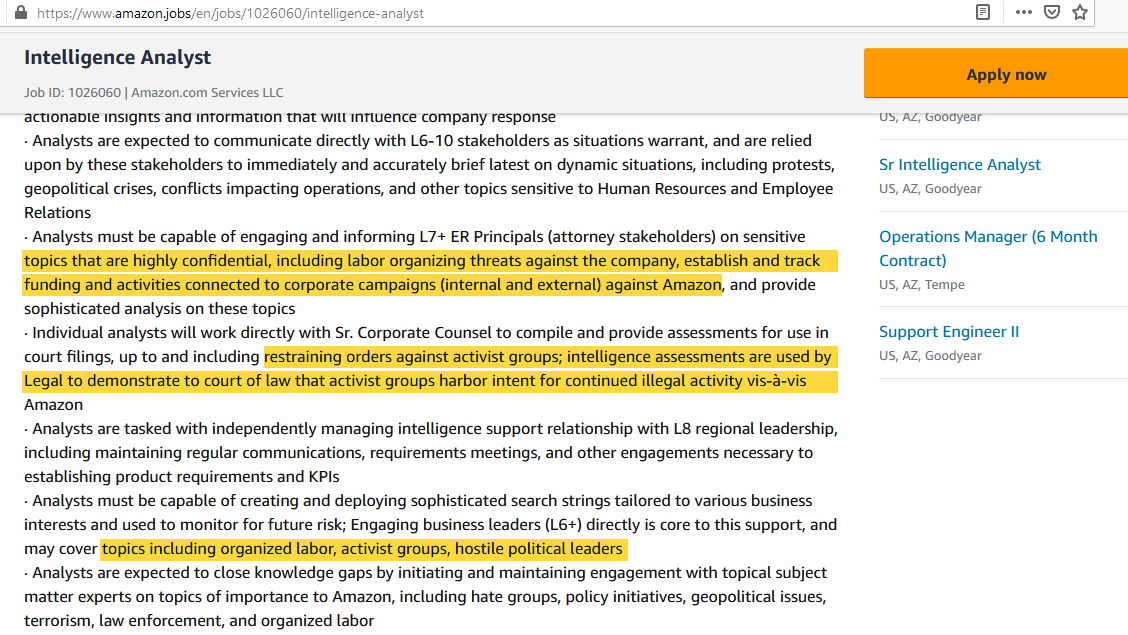
Location data secretly gathered from smartphone apps is potentially flawed, biased, untrustworthy or even fraudulent.
Overview of data harvesting companies who claim to help fighting the virus by providing data on the movements of millions #covidwashing
Ongoing thread:
Overview of data harvesting companies who claim to help fighting the virus by providing data on the movements of millions #covidwashing
Ongoing thread:
Cuebiq, data on Italian smartphone users:
https://twitter.com/WolfieChristl/status/1238601285299048449
Unacast, data on US smartphone users:
https://twitter.com/WolfieChristl/status/1242960702270291970
X-Mode Social, data on US smartphone users:
https://twitter.com/WolfieChristl/status/1243671577398575105
Umlaut, data on German/EU smartphone users (sources in German):
https://twitter.com/WolfieChristl/status/1244349450514030593
Cuebiq, data on US smartphone users:
https://twitter.com/deaneckles/status/1245705660341288960
Foursquare, data on US smartphone users: enterprise.foursquare.com/intersections/…
"For academics, non-profits, and governments, we are actively donating SafeGraph data. Hundreds of these collaborators are actively working with [it] ... researchers have used SafeGraph data to understand coronavirus spread"
SafeGraph, data on US users: safegraph.com/dashboard/covi…
SafeGraph, data on US users: safegraph.com/dashboard/covi…
Placer, another location data company, who claims to track the movements of millions based on data from smartphone apps, provides covid-related analytics mainly for commercial clients, e.g. on visits for pharmacies in the US.
placer.ai/blog/promising…
placer.ai/blog/
placer.ai/blog/promising…
placer.ai/blog/

Cuebiq, Unacast, X-Mode, Umlaut, FourSquare, SafeGraph, Placer and others are tiny to medium-size companies who gather huge amounts of data from apps.
Google is at a completely different level, uses 'data from users who have opted-in to Location History':
Google is at a completely different level, uses 'data from users who have opted-in to Location History':
https://twitter.com/WolfieChristl/status/1246022935170686976
Facebook also provides location data for aggregate analytics ('COVID-19 Mobility Data Network'). The data sharing policy looks at least better than others.
However, Cuebiq and Camber Systems (never heard of this company) are also part of this initiative:
However, Cuebiq and Camber Systems (never heard of this company) are also part of this initiative:
https://twitter.com/WolfieChristl/status/1246206440240492544
"X-Mode is also the source of location data that defense contractor Culmen International is using to map the virus' spread for federal agencies"
@levinsonc's investigation into location data brokers, their data sources, and how they approach app vendors:
@levinsonc's investigation into location data brokers, their data sources, and how they approach app vendors:
https://twitter.com/WolfieChristl/status/1247178365641129984
Gravy Analytics, a marketing data firm whose subsidiary Venntel sold data on the movements of US citizens gathered from smartphone apps to DHS ICE, CBP and DEA: gravyanalytics.com/blog/covid-19-…
PlaceIQ.
They just acquired FreckleIOT, another location data harvesting firm (adexchanger.com/mobile/placeiq…). Oracle (oracle.com/us/solutions/c…) and Adobe (adobe-audience-finder.com/data_partner/p…) resell PlaceIQ data. Experian is a strategic investor (placeiq.com/2019/08/experi…).
They just acquired FreckleIOT, another location data harvesting firm (adexchanger.com/mobile/placeiq…). Oracle (oracle.com/us/solutions/c…) and Adobe (adobe-audience-finder.com/data_partner/p…) resell PlaceIQ data. Experian is a strategic investor (placeiq.com/2019/08/experi…).
https://twitter.com/TradeDiversion/status/1245903691649101824
On covid-related location data/tracking services by Phunware (who was hired by the Trump Campaign and sued by Uber for ad fraud) and Verint Systems (according to the Intercept, the CDC is among their clients):
https://twitter.com/WolfieChristl/status/1248328125324410882
"Flawed, incomplete smartphone location data is being used to fight COVID-19"
Good summary about the use of mobile location data and its problems/implications by @KateKayeReports: fastcompany.com/90489173/flawe…
Good summary about the use of mobile location data and its problems/implications by @KateKayeReports: fastcompany.com/90489173/flawe…
• • •
Missing some Tweet in this thread? You can try to
force a refresh