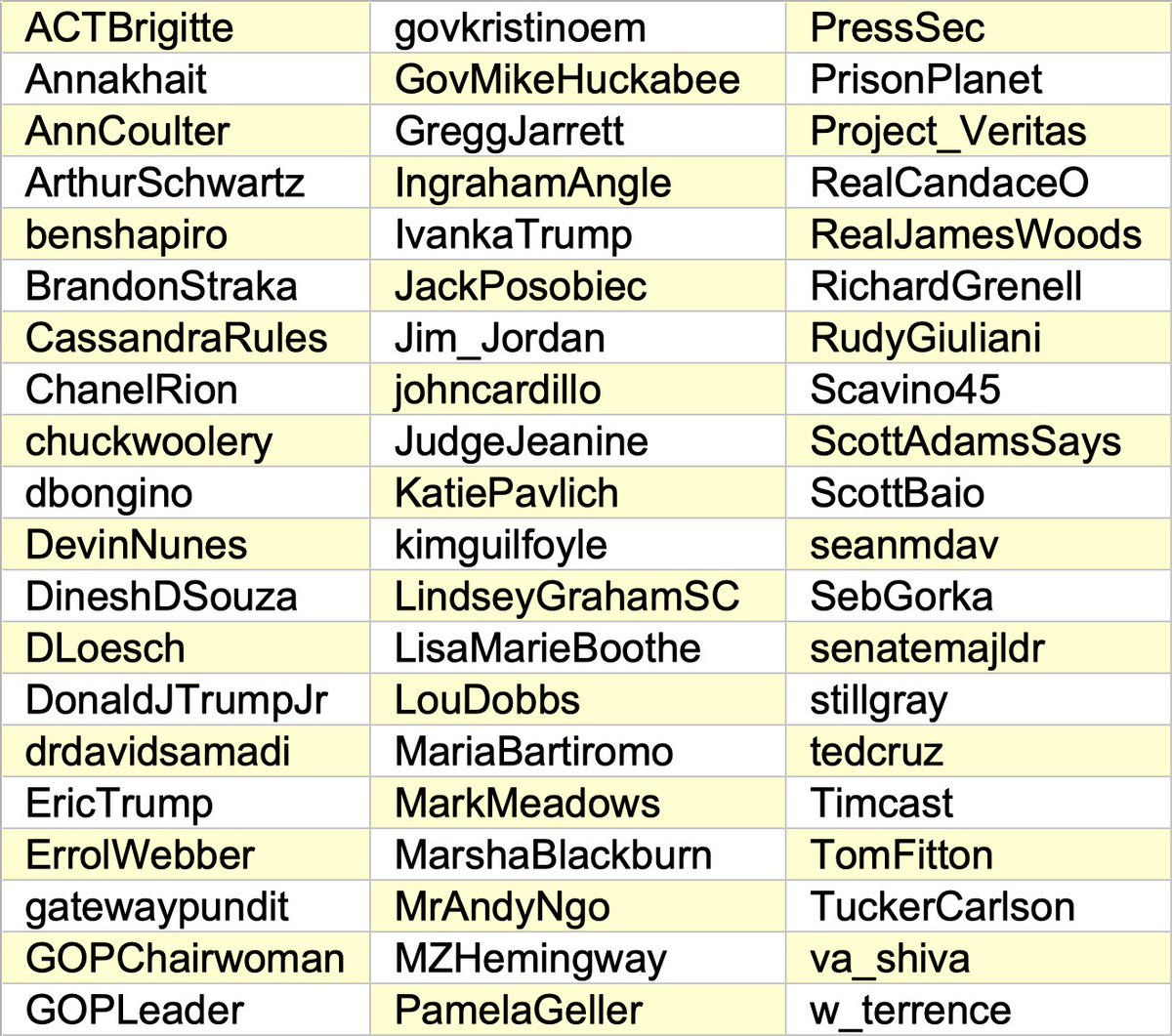
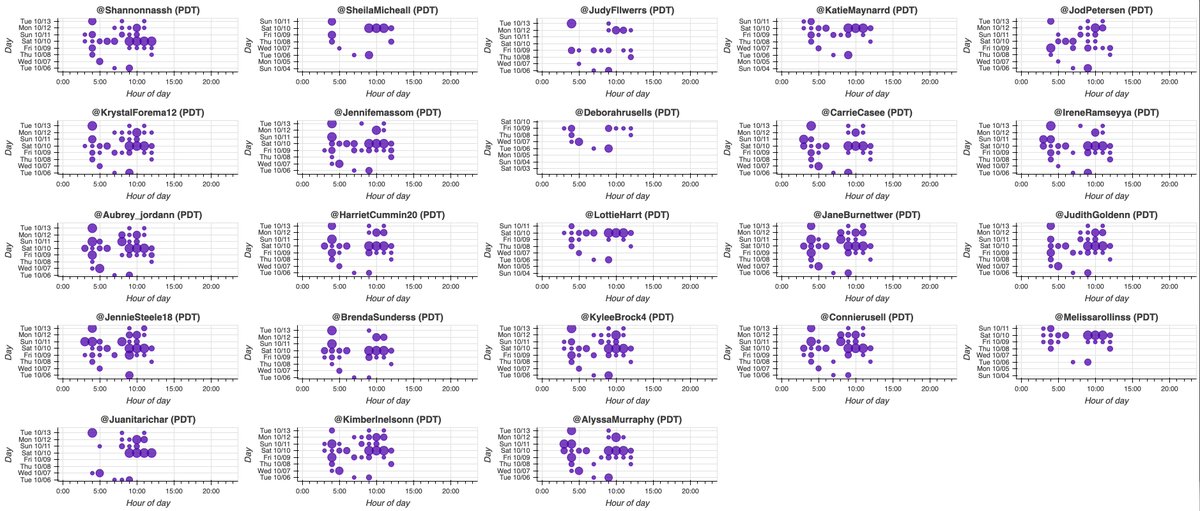
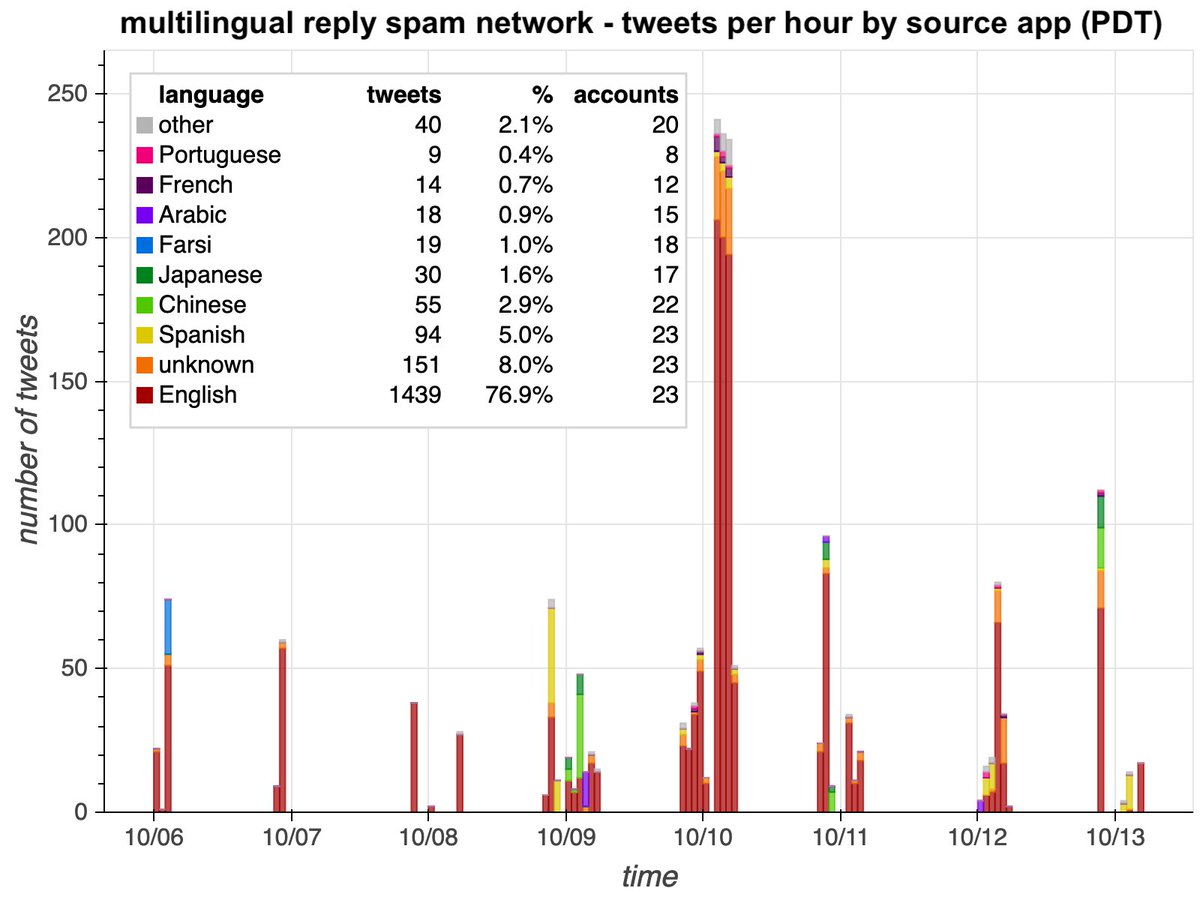
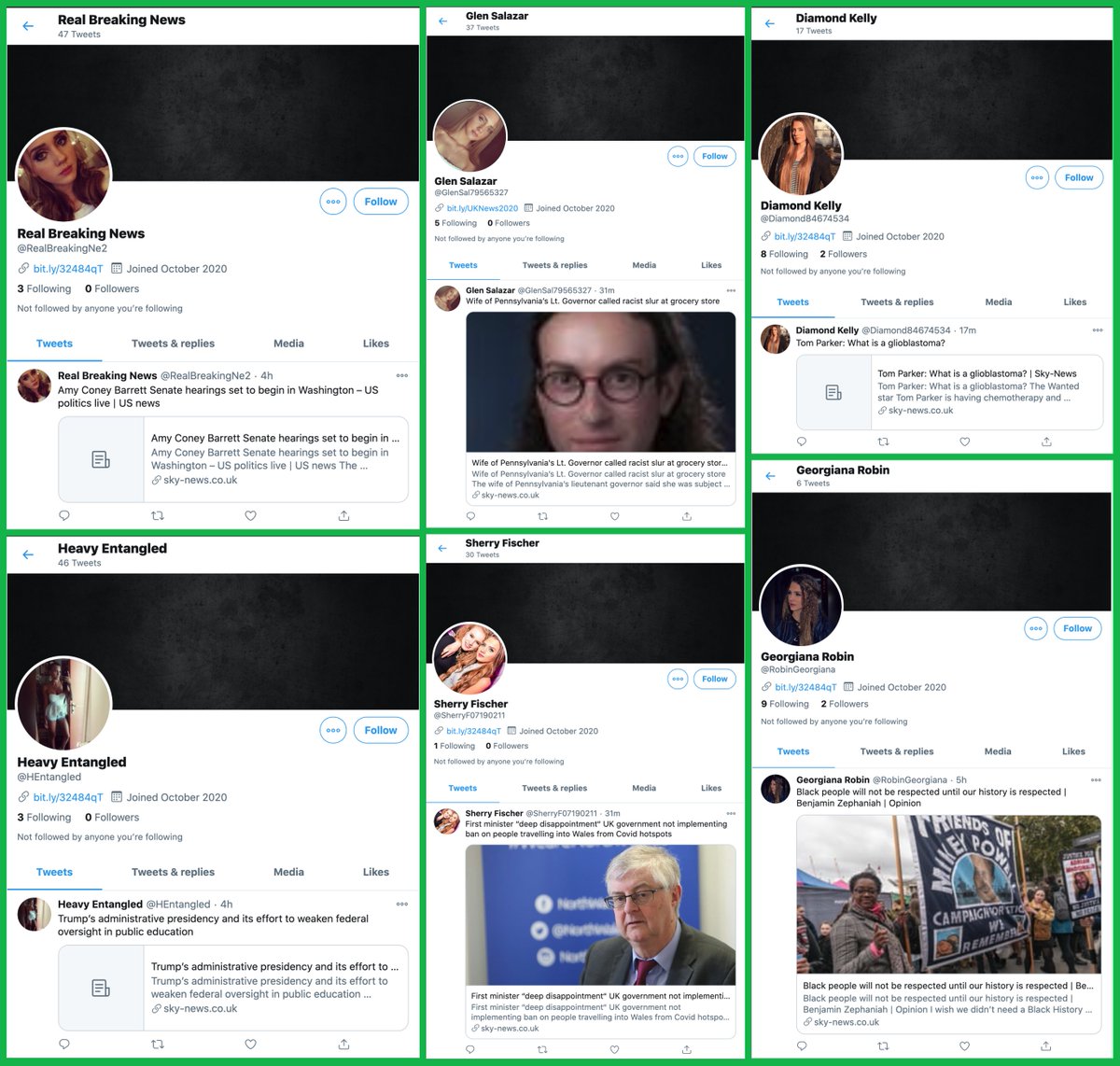
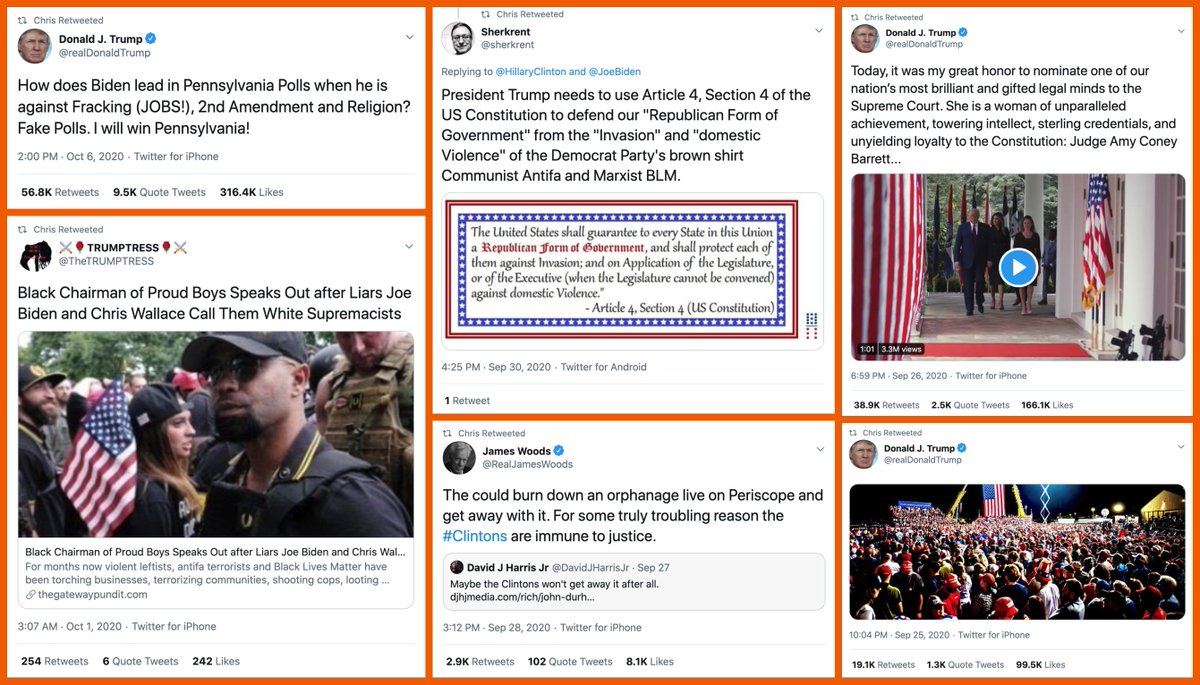
What's up with all these accounts with AI-generated profile pics linking the same article on cointelegraph(dot)com at the same time using the same hashtags? #SaturdayShenaniGANs
cc: @ZellaQuixote
cc: @ZellaQuixote
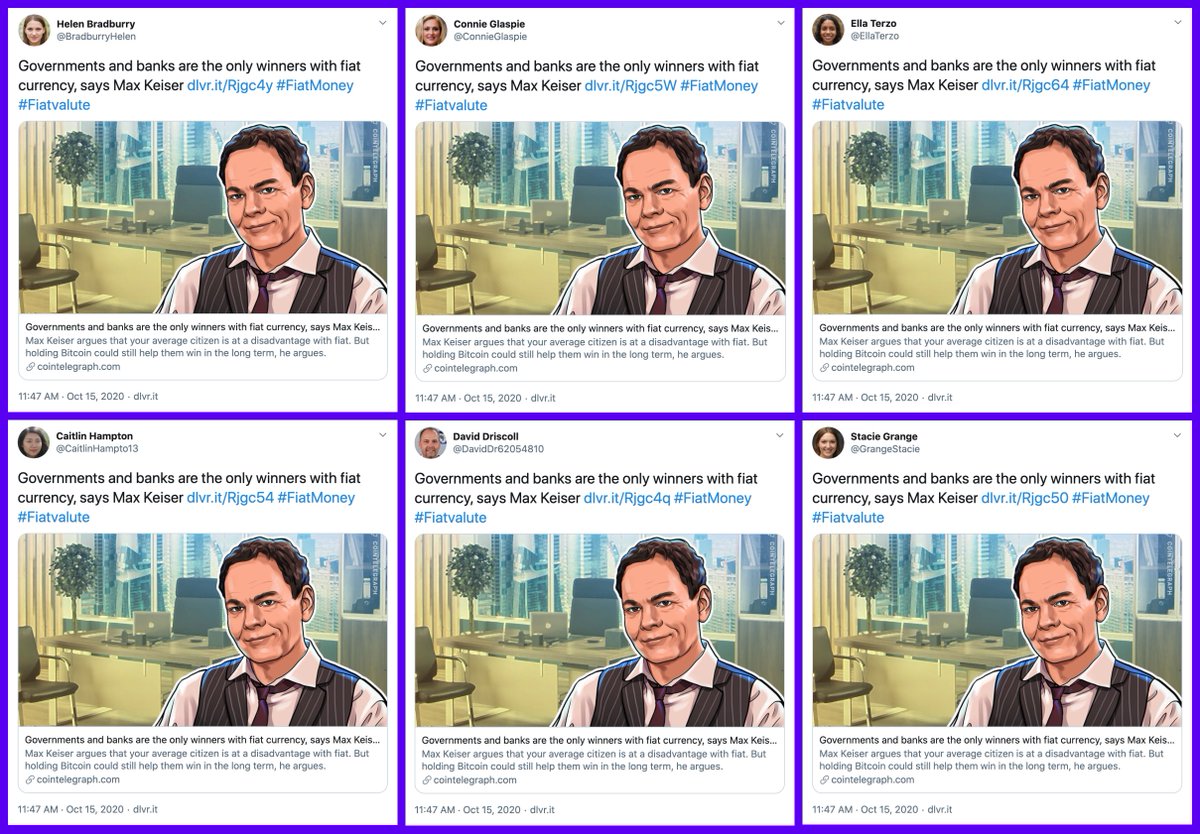
We found a total of 47 accounts spamming links to cointelegraph(dot)com via automation service dlvr(dot)it, all created in September or October 2020. The volume of this botnet has increased as more accounts were added. 

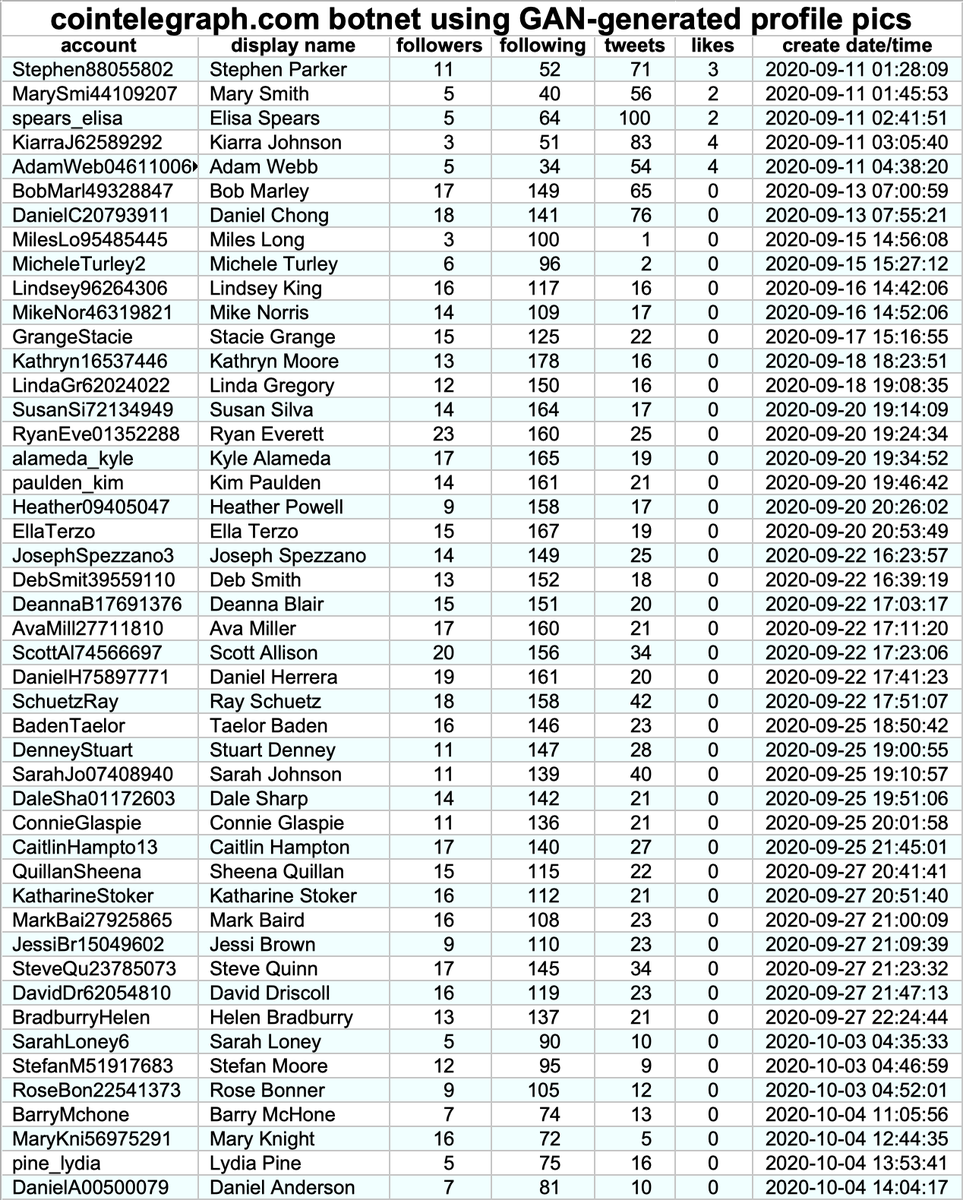
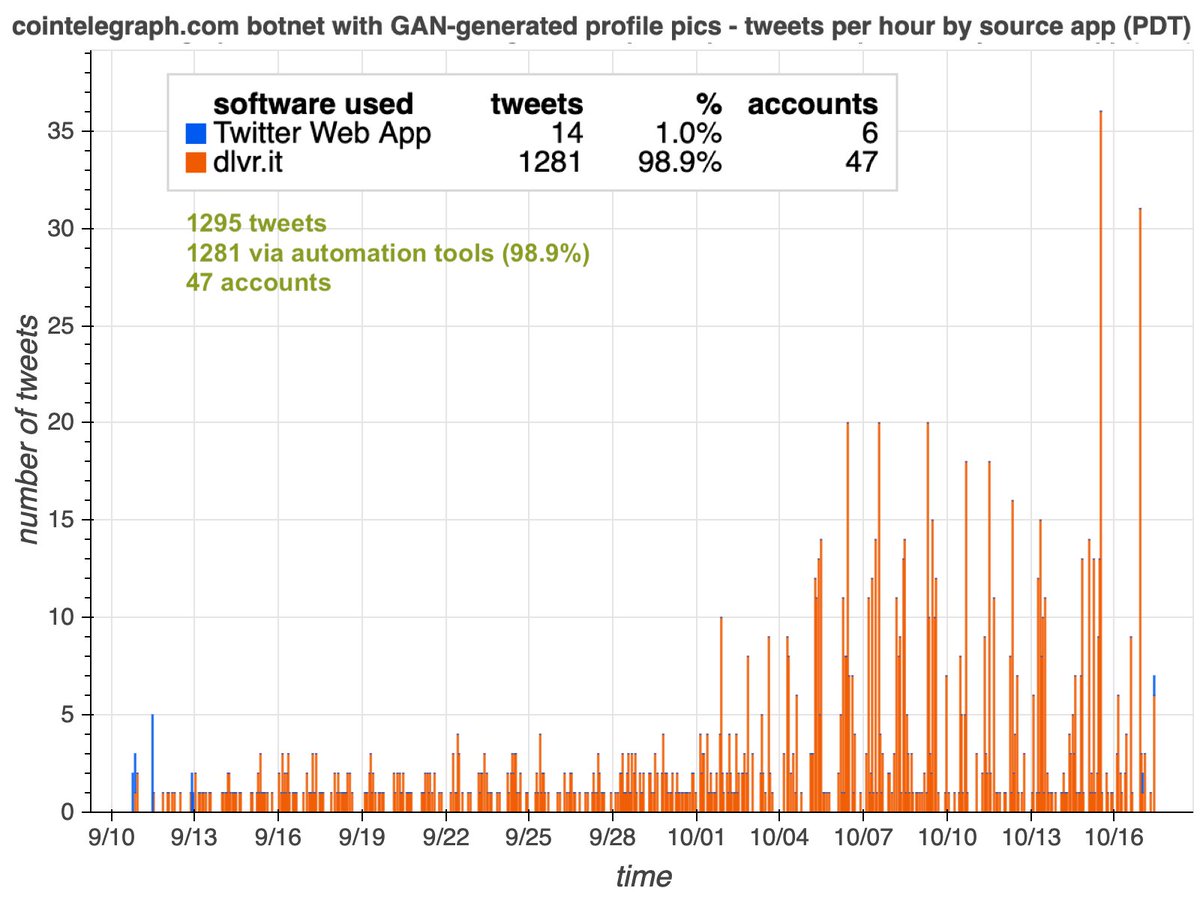
The cointelegraph(dot)com website promoted by this botnet is a cryptocurrency "news" site registered in the Cayman Islands, according to WHOIS records. Almost all of this botnet's tweets (1222 of 1295, 94.3%) contain links to this website. 




All 47 of the accounts in this botnet use GAN-generated profile pics (similar to those produced by thispersondoesnotexist.com). These images have the telltale sign that the eyes, nose, and mouth line up almost perfectly when overlaid/blended.


https://twitter.com/conspirator0/status/1239679687015751686


Animated visualization of blending the profile images of all 47 accounts in the botnet, demonstrating the pattern in facial feature placement. (GAN-generated face pics have other artifacts as well: nonsensical backgrounds/clothing/jewelry, for example.)
• • •
Missing some Tweet in this thread? You can try to
force a refresh