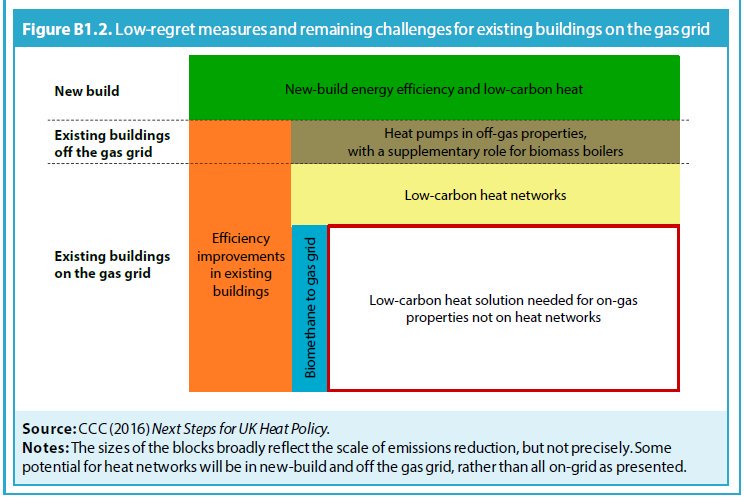
I'll take my time for this, but wanna share some (meaningless) curiosities/spec violations I saw on some test devices (kept addresses visible) ...
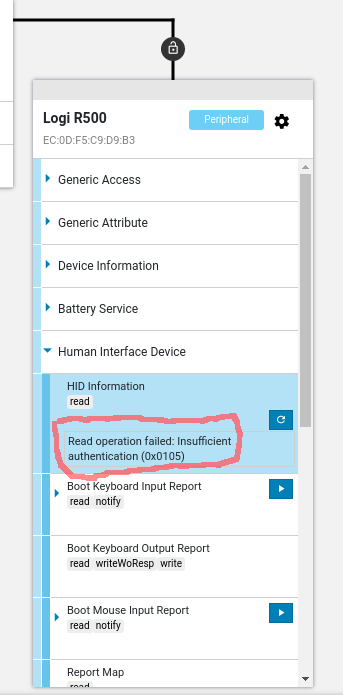
I assume this is true for most devices with IO capabilities "NoInputNoOutput", as it seems to be the only way to make iOS initiate pairing automatically.
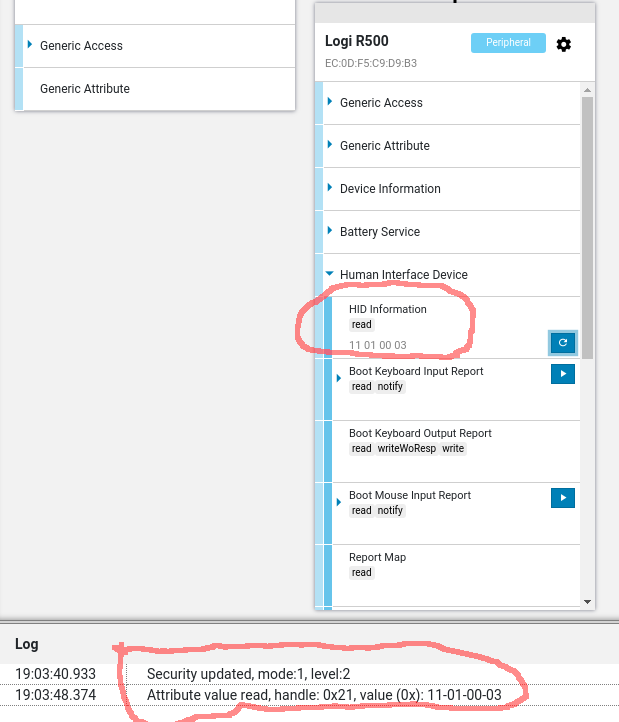
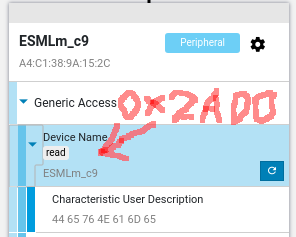
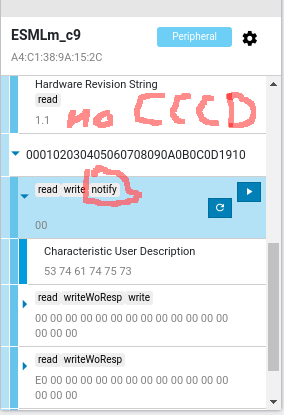
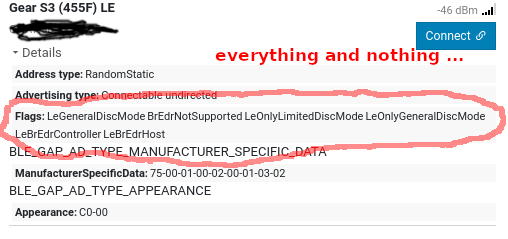
Because I have hard times cloning such weird devices, with a firmware backed by @NordicTweets softdevice, which enforces specs in many cases.
I tested none of those devices for security issues, not even a tiny bit of fuzzing. But products not even able to follow specs, occur a bit fishy security wise.
Just thinking loud 😉
Stay safe