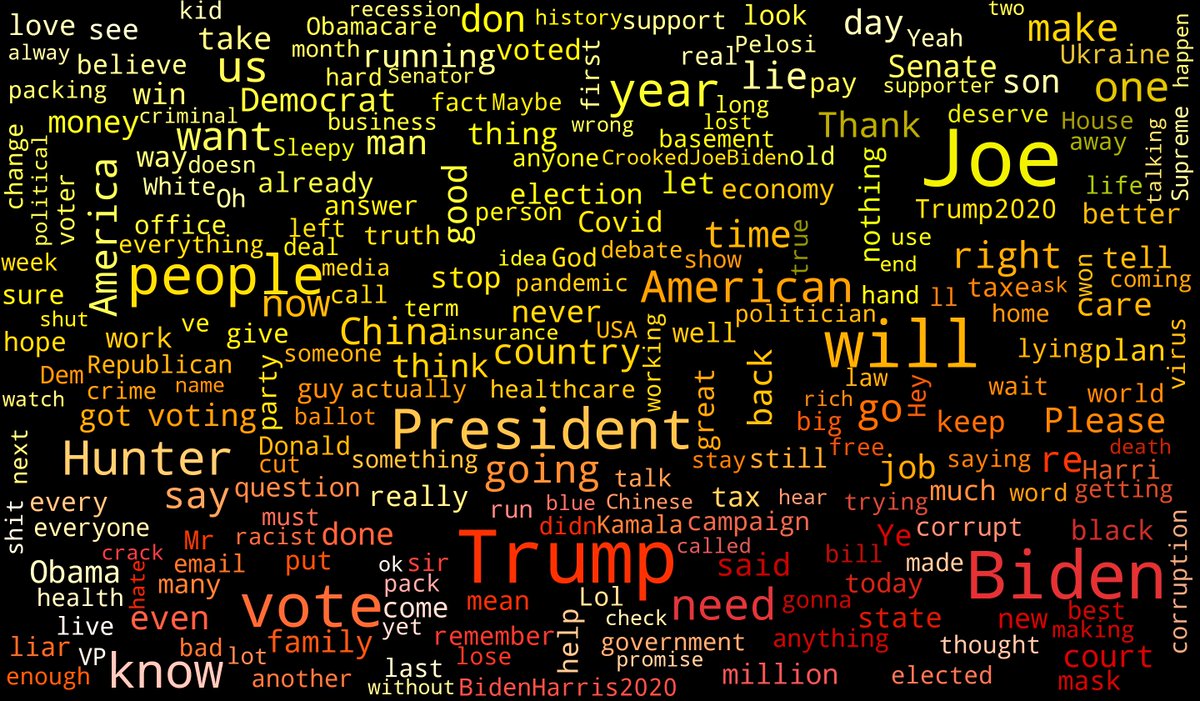
Oh My God! This botnet is really Enormous Graceful Frame!
(We don't actually know what this means, but since it was repeated by seven different accounts, it's clearly important.)
cc: @ZellaQuixote
(We don't actually know what this means, but since it was repeated by seven different accounts, it's clearly important.)
cc: @ZellaQuixote

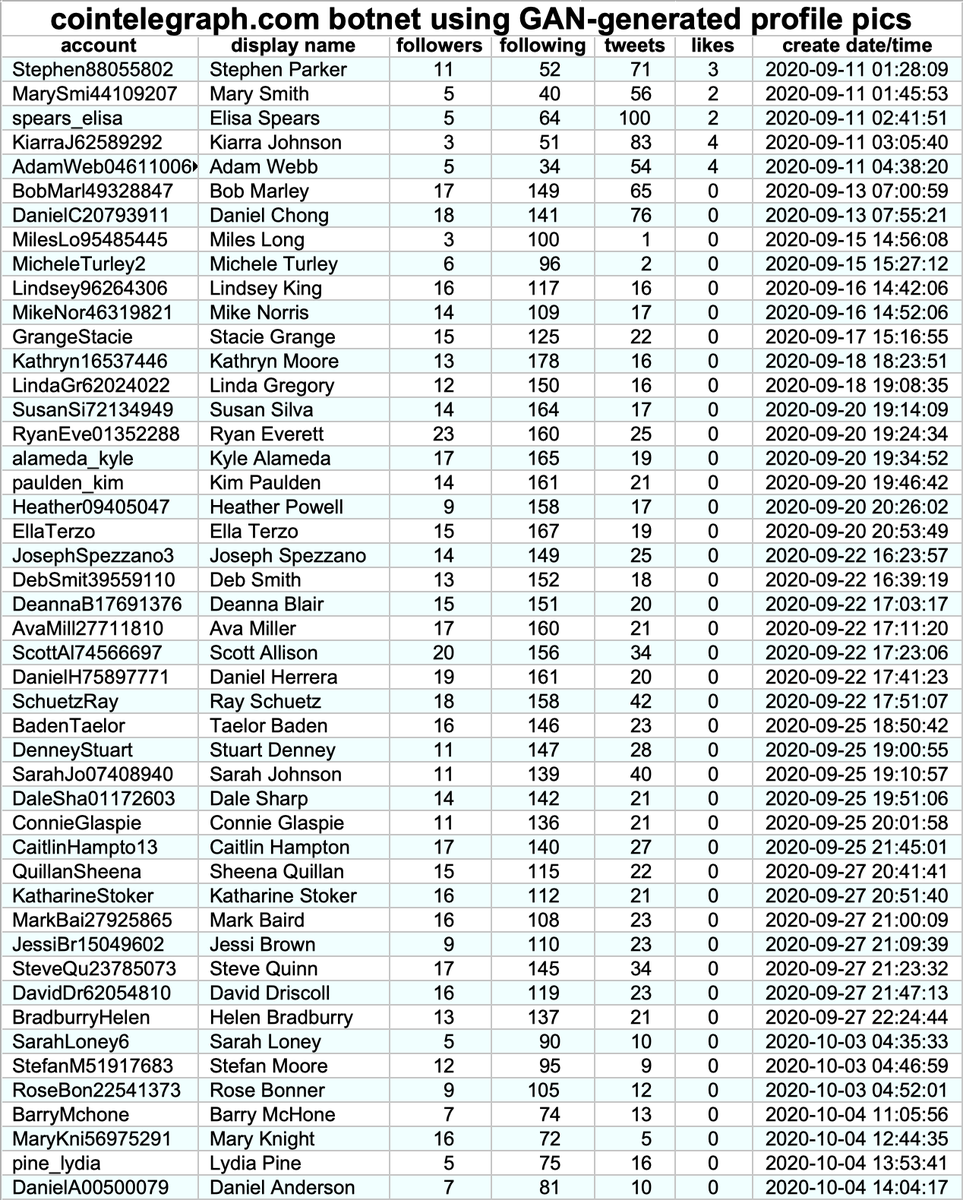
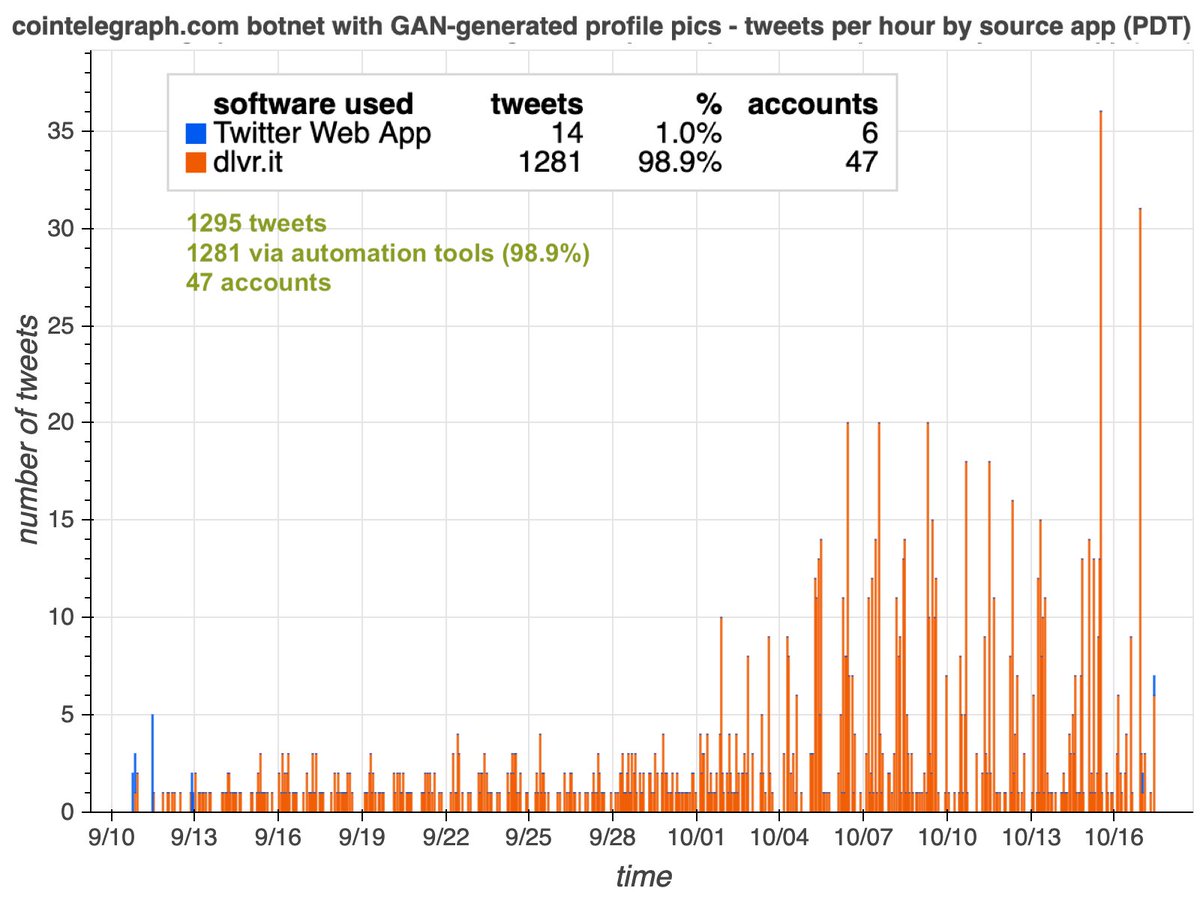
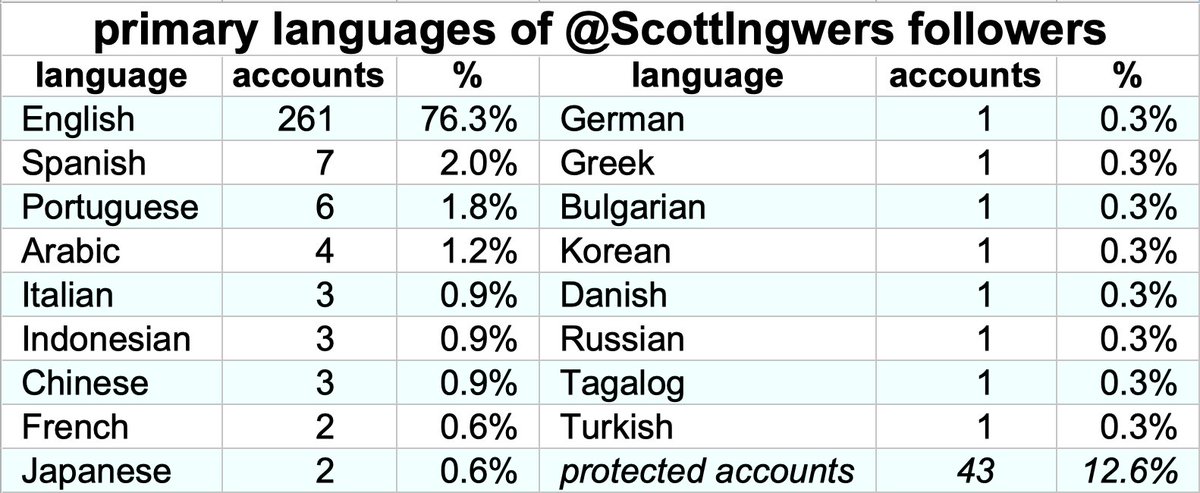
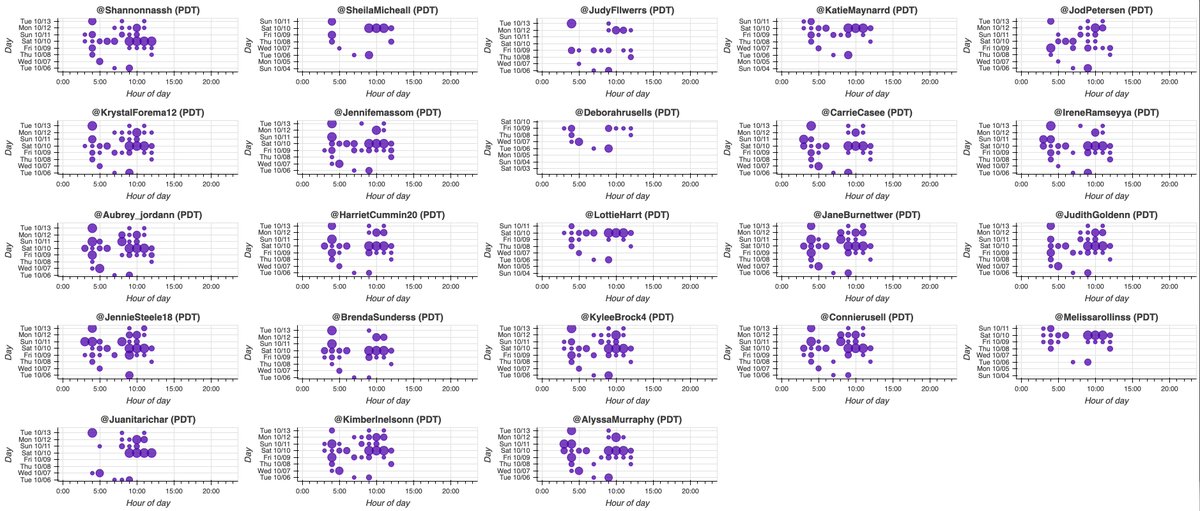
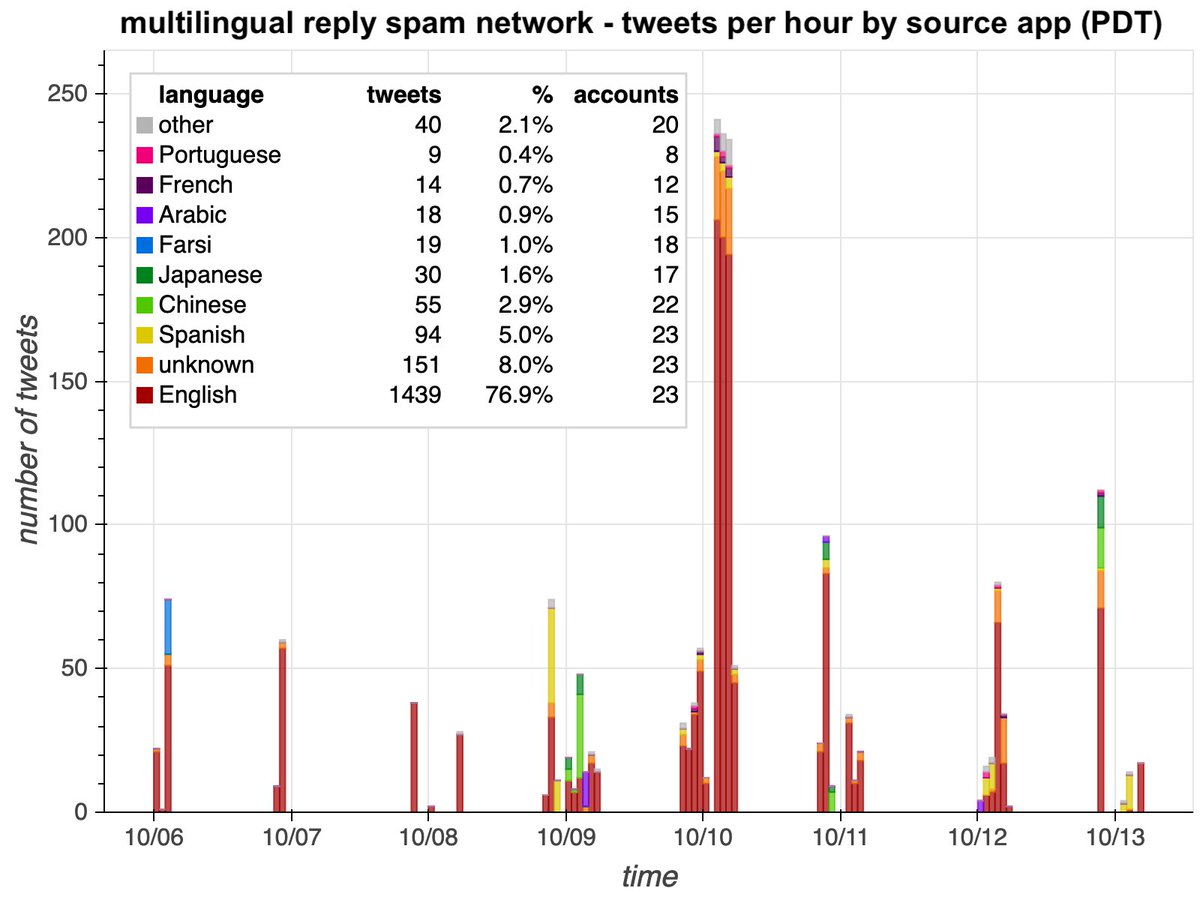
This botnet consists of 35 accounts, all created on either October 19th or October 20th, 2020. Thus far all of this network's content is replies (no retweets or original tweets), almost all posted via "Mobile Web (M2)". Some of the account biographies are duplicates. 





This botnet is very repetitive, with 77 replies sent at least twice and the most frequent reply ("Oh My God! Your tweet is really Enormous Graceful Frame") used seven times by seven different accounts. (Table includes all replies that were repeated at least three times.) 

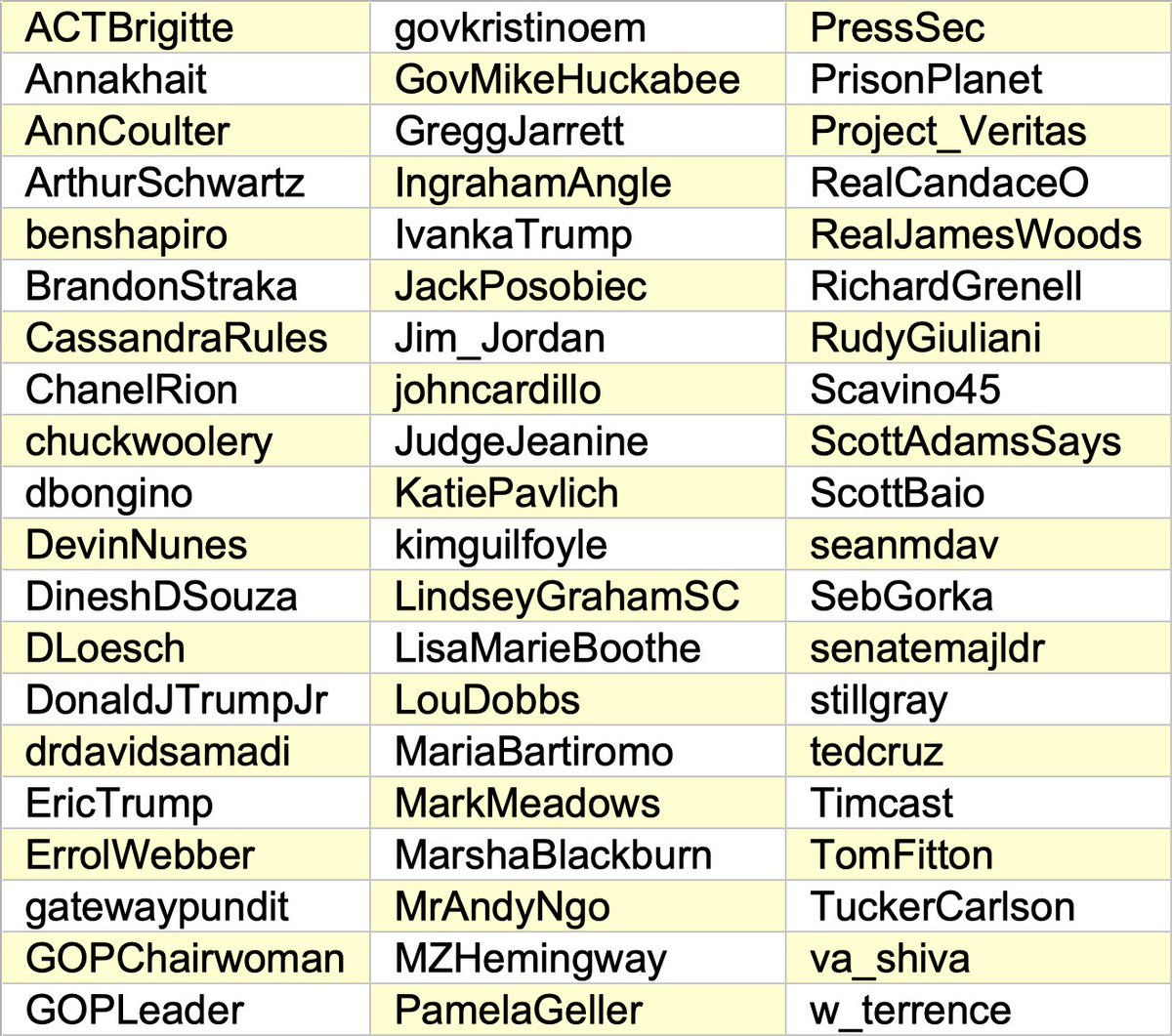
The reply text isn't the only repetitive aspect of this botnet - it also replies to the same accounts and tweets over and over. We've included a collage of the 10 tweets that received the most replies from the botnet. 



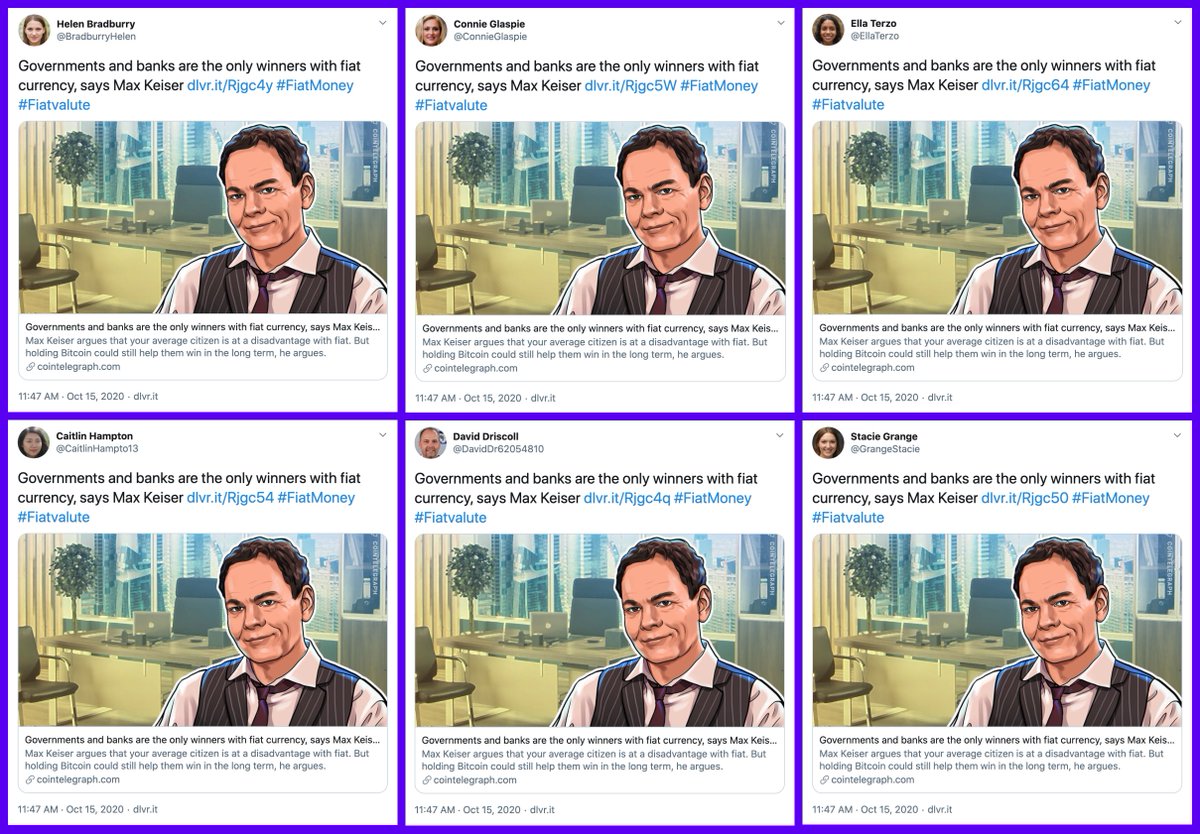
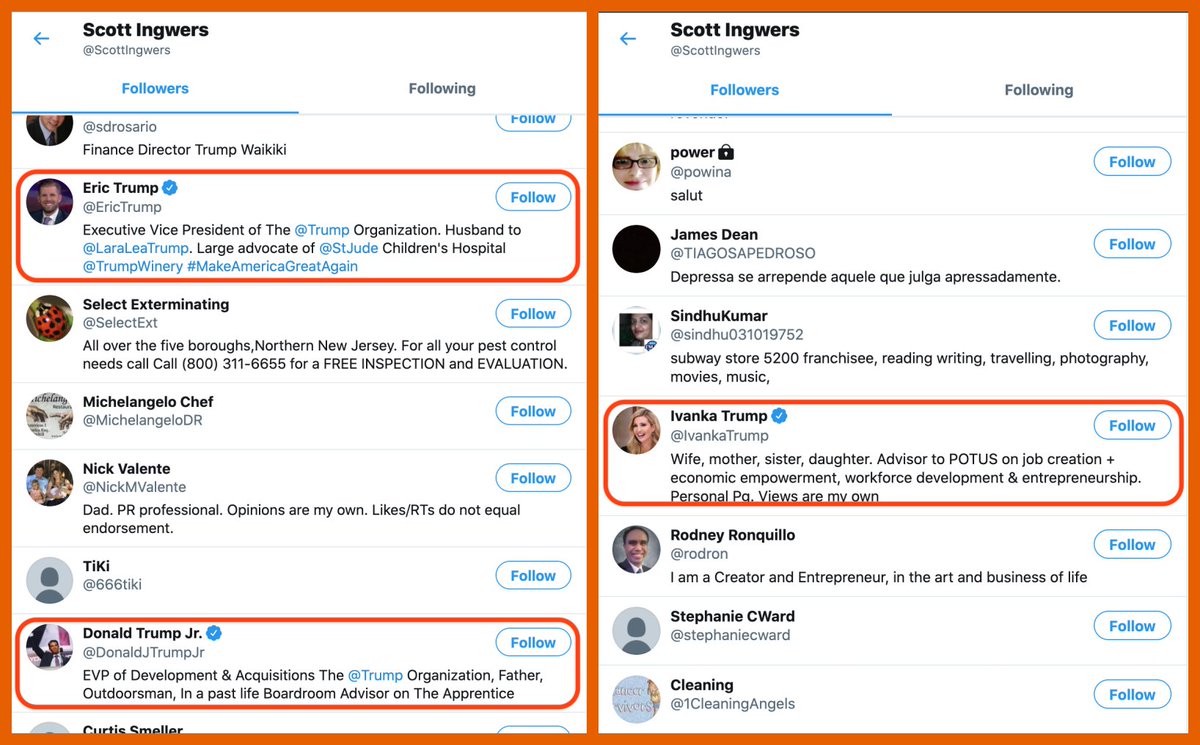
Does this botnet use stolen profile pics? Yup. For the images we were able to confirm were stolen, we found Google and Yandex reverse image searches about equally effective (TinEye wasn't very useful here). 

Footnote: we've seen similar botnets before, including a reply spam botnet we found in early October 2020 (of which this may be a new incarnation) and a now-suspended botnet we found replying to @ARTEM_KLYUSHIN in August 2020.
https://twitter.com/conspirator0/status/1316144852329955328
https://twitter.com/conspirator0/status/1292291516430462976
• • •
Missing some Tweet in this thread? You can try to
force a refresh