---a thread---
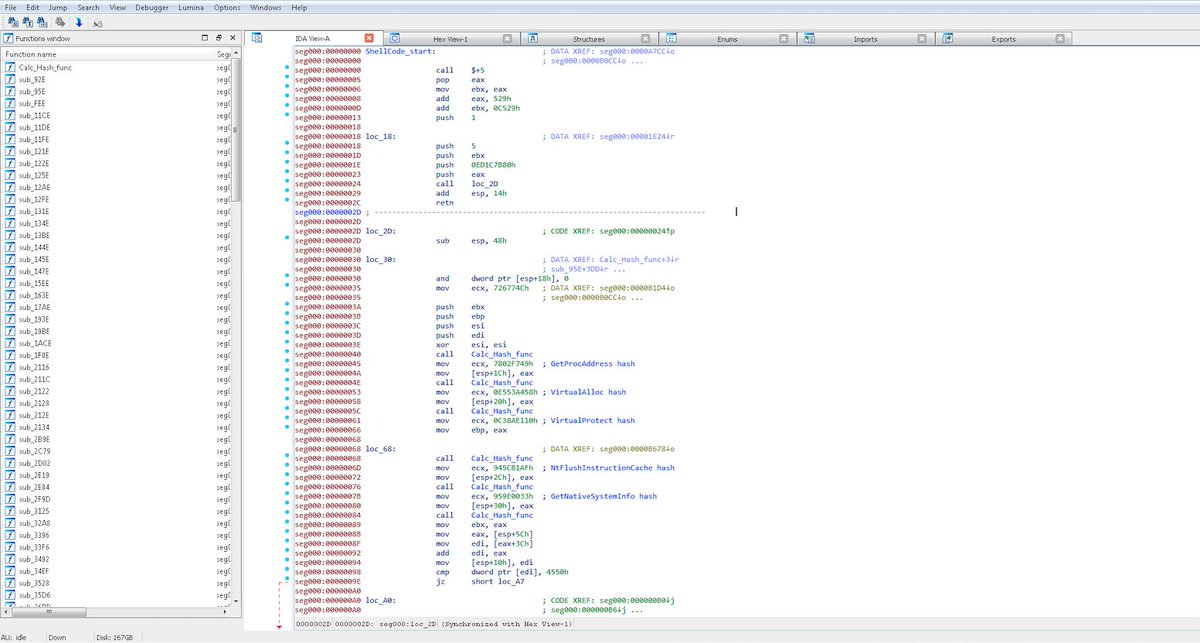
We've discovered that the most recent version of Ryuk shares shellcode with Buer Loader, a malware-as-a-service trojan we've been tracking...
The shellcode is used by droppers for both malware, to inject the malware into memory.
Ryuk in-memory loader:
1/6
We've discovered that the most recent version of Ryuk shares shellcode with Buer Loader, a malware-as-a-service trojan we've been tracking...
The shellcode is used by droppers for both malware, to inject the malware into memory.
Ryuk in-memory loader:
1/6

Ryuk also recently started encrypting text strings—on October 4, the strings within the sample were unencrypted...
3/6
3/6

Buer has been used for some of the most recent Ryuk attacks (as we've reported, and are diving into in Wednesday's post).
This suggests that Ryuk has borrowed some of the code from Buer's dropper—and is also constantly adjusting its tactics to evade new detections.
5/6
This suggests that Ryuk has borrowed some of the code from Buer's dropper—and is also constantly adjusting its tactics to evade new detections.
5/6
FYI to #Sophos customers: Sophos' CryptoGuard still stops Ryuk from encrypting files.
Many thanks to our researcher @AnandAjjan for these findings.
6/6
Many thanks to our researcher @AnandAjjan for these findings.
6/6
• • •
Missing some Tweet in this thread? You can try to
force a refresh