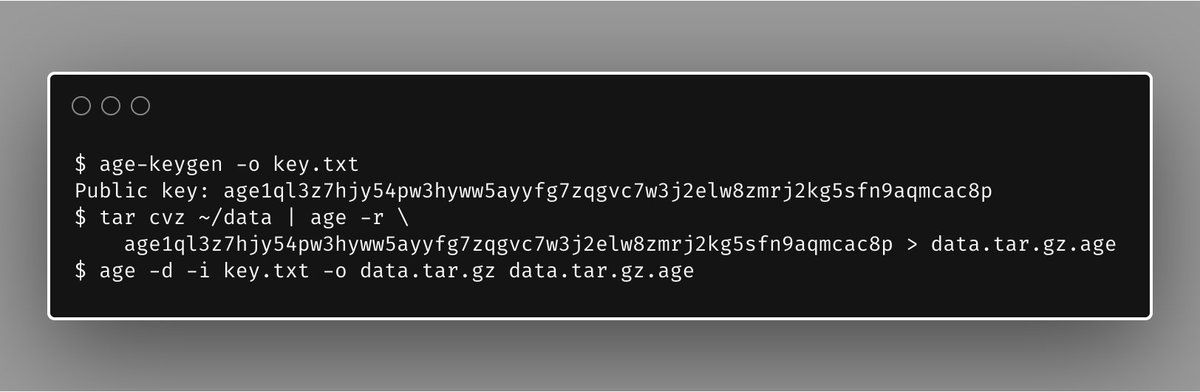
Here we go, let's see how the new M1 chips do on Go benchmarks!
(Might be a good time to mute #M1, I have a new toy and I took time off work until the end of the month.)
First step is
$ GOOS=darwin GOARCH=arm64 ./bootstrap.sh
on my corp MacBook.
(Might be a good time to mute #M1, I have a new toy and I took time off work until the end of the month.)
First step is
$ GOOS=darwin GOARCH=arm64 ./bootstrap.sh
on my corp MacBook.
Well, it couldn't be too easy I suppose.
Ran bootstrap[.]sh (which is just a convenience wrapper for make + mv bin/darwin_arm64/go bin/go + tar), sent it over with webwormhole.io, cleared the quarantine xattr, and...
zsh: killed ./go-darwin-arm64-bootstrap/bin/go
#M1
Ran bootstrap[.]sh (which is just a convenience wrapper for make + mv bin/darwin_arm64/go bin/go + tar), sent it over with webwormhole.io, cleared the quarantine xattr, and...
zsh: killed ./go-darwin-arm64-bootstrap/bin/go
#M1
Frank has it right, after codesigning bin/* and pkg/tool/darwin_arm64/* I got the compiler running.
Still, this needs fixing, it stops "go run" and "go test" from working. I wonder if the dev kits had it disabled.
Still, this needs fixing, it stops "go run" and "go test" from working. I wonder if the dev kits had it disabled.
https://twitter.com/jedisct1/status/1328856883168505856
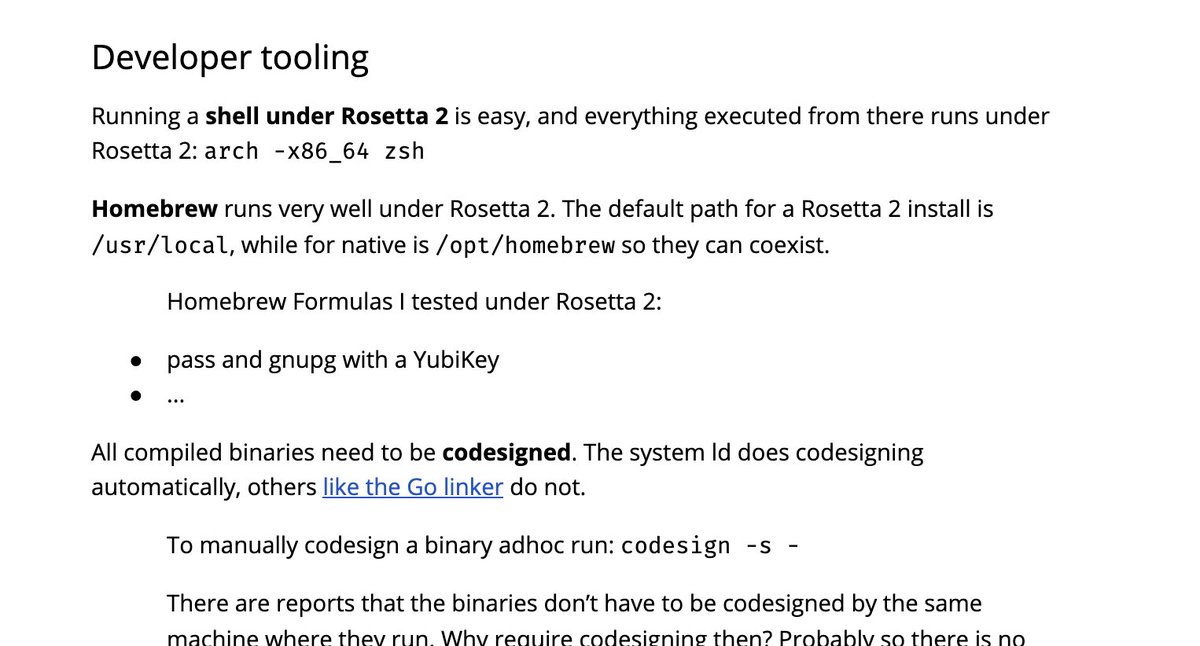
Alright, the friction is high because the Go linker does not automatically codesign binaries like the system linker (which will be a major pain for cross-compiling) but I should be able to get some benchmarks to compile.
No make.bash timing though :( #M1
github.com/golang/go/issu…
No make.bash timing though :( #M1
github.com/golang/go/issu…
Trying to find apples to apples comparisons since the amd64 assembly in the Go crypto tree is quite a bit better.
In the meantime, the brokenness is noticeable. magic-wormhole doesn't install as PyNaCl doesn't compile. Chrome runs under Rosetta 2 (cool!) but is not fast. #M1
In the meantime, the brokenness is noticeable. magic-wormhole doesn't install as PyNaCl doesn't compile. Chrome runs under Rosetta 2 (cool!) but is not fast. #M1
First Go #M1 benchmarks out the oven!
x/crypto/chacha20poly1305
Open-8192
-18%
x/crypto/curve25519
ScalarBaseMult
-46% (!!)
Pure Go running on a MacBook Pro (13-inch, M1, 2020) vs a MacBook Pro (15-inch, 2017) 3.1 GHz Quad-Core Intel Core i7.
x/crypto/chacha20poly1305
Open-8192
-18%
x/crypto/curve25519
ScalarBaseMult
-46% (!!)
Pure Go running on a MacBook Pro (13-inch, M1, 2020) vs a MacBook Pro (15-inch, 2017) 3.1 GHz Quad-Core Intel Core i7.
(Oh hey, there actually is a native version of Chrome. 9to5google.com/2020/11/17/chr…)
Dependency loop detected: can't work on replacing gpg with age in pass, because I can't access my password-store since gpg does not run on #M1.
https://twitter.com/FiloSottile/status/1323760352585240577
Ok I give up, I have no idea why Apple is requiring codesigning, if you can run binaries signed ad-hoc on a different machine. #M1
Putting in place the infrastructure to do better logic later?
github.com/golang/go/issu…
Putting in place the infrastructure to do better logic later?
github.com/golang/go/issu…
Ok, back on track after a good night's sleep.
Turns out Homebrew runs well under Rosetta 2 on #M1, and gpg can talk to the YubiKey from it.
It's neat, you start an emulated shell with "arch -x86_64 zsh" and then everything you do is emulated.
Turns out Homebrew runs well under Rosetta 2 on #M1, and gpg can talk to the YubiKey from it.
It's neat, you start an emulated shell with "arch -x86_64 zsh" and then everything you do is emulated.
I am keeping a Google Doc with my notes on developing on Apple Silicon if you want to follow along.
I'll be dropping benchmarks there, too. #M1
docs.google.com/document/d/1iW…
I'll be dropping benchmarks there, too. #M1
docs.google.com/document/d/1iW…
#M1 first impressions 24h in:
· this thing is honestly fast
· Rosetta 2 is kind of amazing
· many CLI tools only run under R2 for now, and that's fine
· native makes a difference for heavy apps
· code signing is a bit annoying but makes sense, and hopefully tooling will catch up
· this thing is honestly fast
· Rosetta 2 is kind of amazing
· many CLI tools only run under R2 for now, and that's fine
· native makes a difference for heavy apps
· code signing is a bit annoying but makes sense, and hopefully tooling will catch up
For developing in Go on Apple Silicon, there's two main issues to be aware of:
- arm64 binaries are not codesigned automatically (github.com/golang/go/issu…)
- amd64 binaries need GODEBUG=asyncpreemptoff=1 (github.com/golang/go/issu…)
Read more: docs.google.com/document/d/1iW… #M1 #golang
- arm64 binaries are not codesigned automatically (github.com/golang/go/issu…)
- amd64 binaries need GODEBUG=asyncpreemptoff=1 (github.com/golang/go/issu…)
Read more: docs.google.com/document/d/1iW… #M1 #golang
• • •
Missing some Tweet in this thread? You can try to
force a refresh