Facebook has connected the 'Ocean Lotus' hacking group to an IT firm operating out of Ho Chi Minh City.
In a chat with me today (over FB) the firm insisted that wasn’t true.
“We are NOT Ocean Lotus,” they said.
Story by @jc_stubbs & @pearswick reut.rs/2KdbDo2
In a chat with me today (over FB) the firm insisted that wasn’t true.
“We are NOT Ocean Lotus,” they said.
Story by @jc_stubbs & @pearswick reut.rs/2KdbDo2
Ocean Lotus doesn’t get the same press as Chinese, Russian, or North Korean hacking groups but they’ve posed particular menace to Vietnamese exiles. Would love to learn more about this particular actor.
https://twitter.com/botherder/status/1314250395535933441
Before it was taken offline, I got through to the person running CyberOne’s Facebook page. They had some interesting things to say when I asked them if they ever participated in offensive operations. 

In a conversation — apparently tapped out over the phone — the CyberOne representative denied working for the Vietnamese government. 
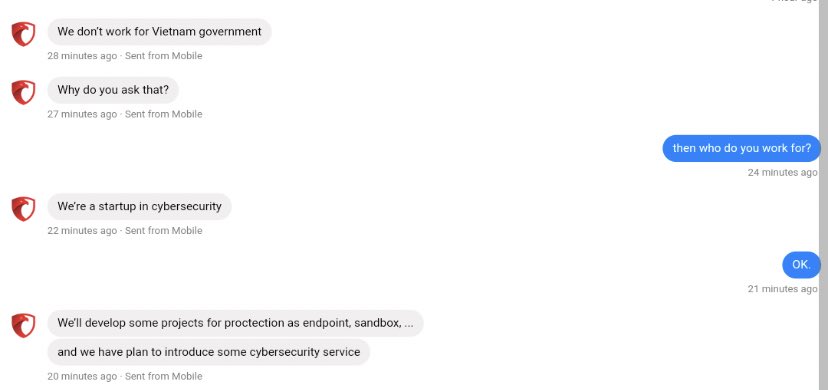
They also sent me an ALL-CAPS denial that they were behind Ocean Lotus — at one point dangling the possibility that they could collaborate with @Reuters to investigate the group. 

I lost touch with the representative — who identified themselves as Hải — when Facebook yanked CyberOne’s account mid-conversation.
Hải, wherever you are, I’m still up for chatting. DM me and we’ll get to the bottom of this.
Hải, wherever you are, I’m still up for chatting. DM me and we’ll get to the bottom of this.

• • •
Missing some Tweet in this thread? You can try to
force a refresh