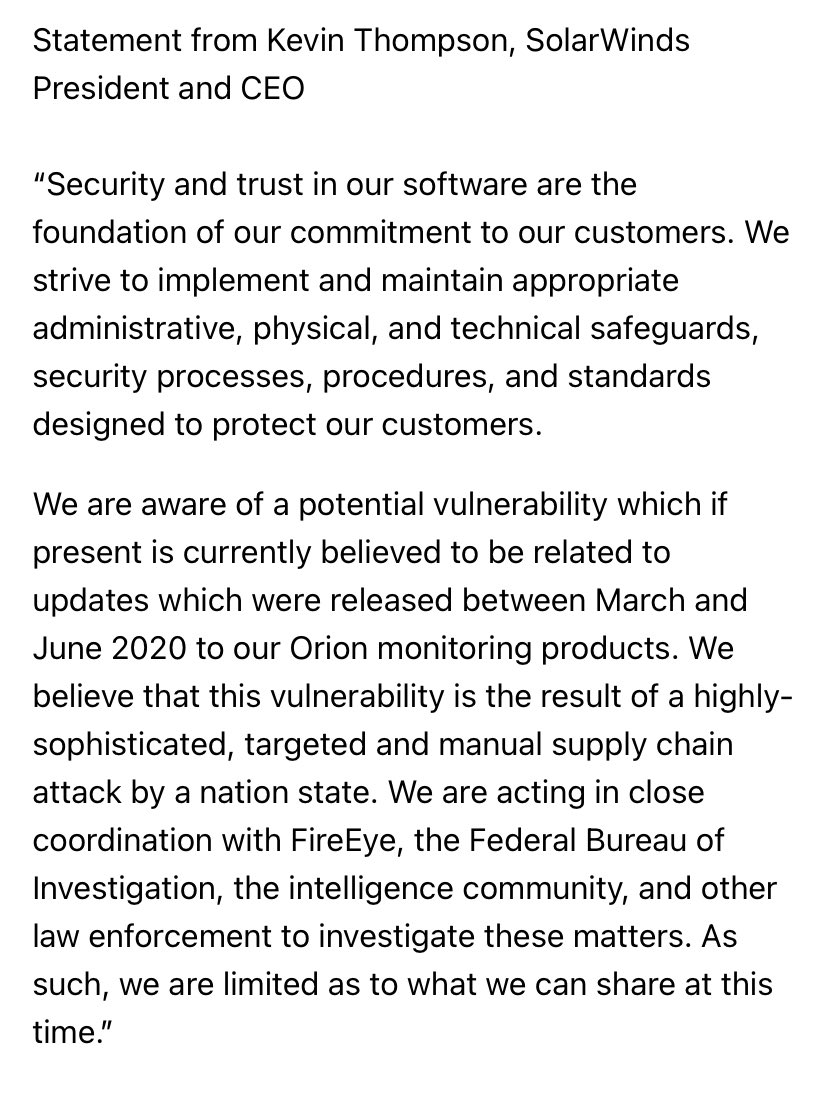
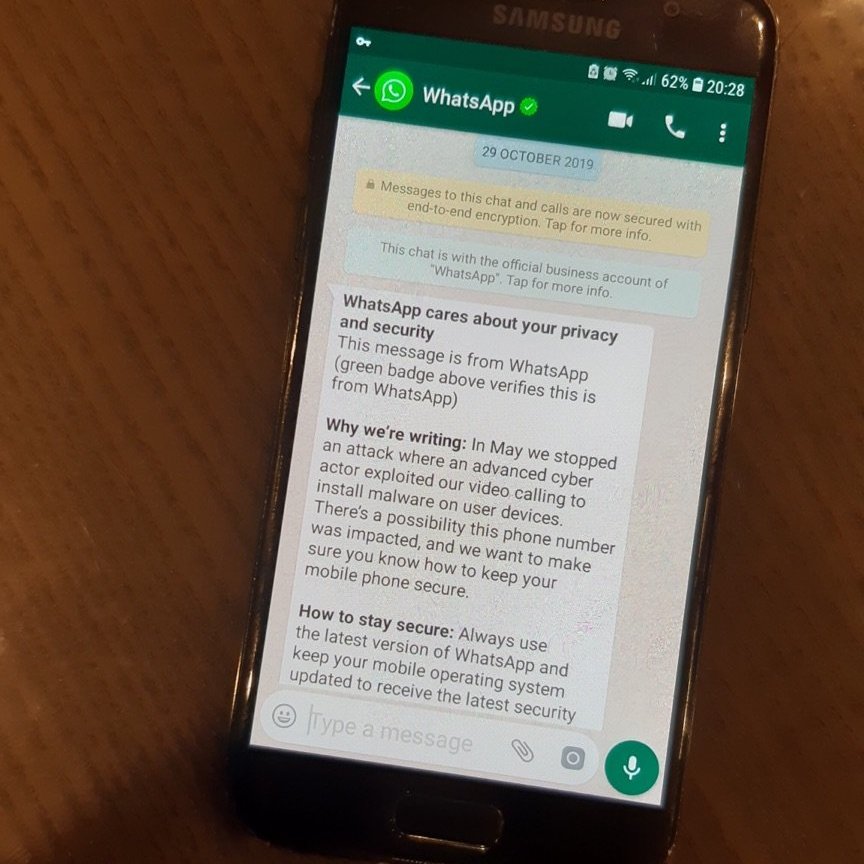
Huge scoop from @Bing_Chris: the US Treasury and the US NTIA have been breached by hackers. A foreign government is suspected and the National Security Council met Saturday to discuss the fallout. reut.rs/3oP3FAs
Advice from the former @CISAgov chief:
https://twitter.com/C_C_Krebs/status/1338271894416601088?s=20
Time to patch that Orion software, folks
https://twitter.com/tsudo/status/1338327495481958400
• • •
Missing some Tweet in this thread? You can try to
force a refresh