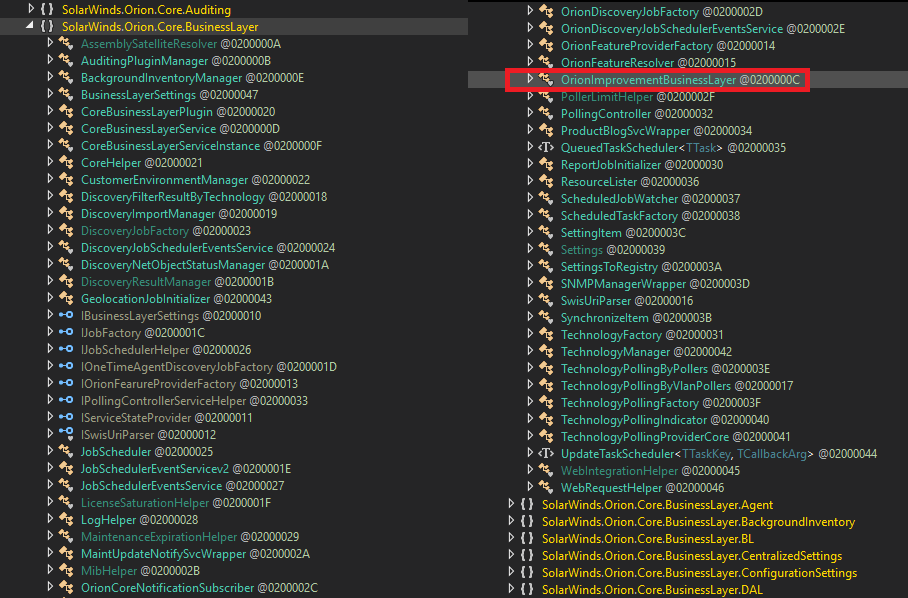
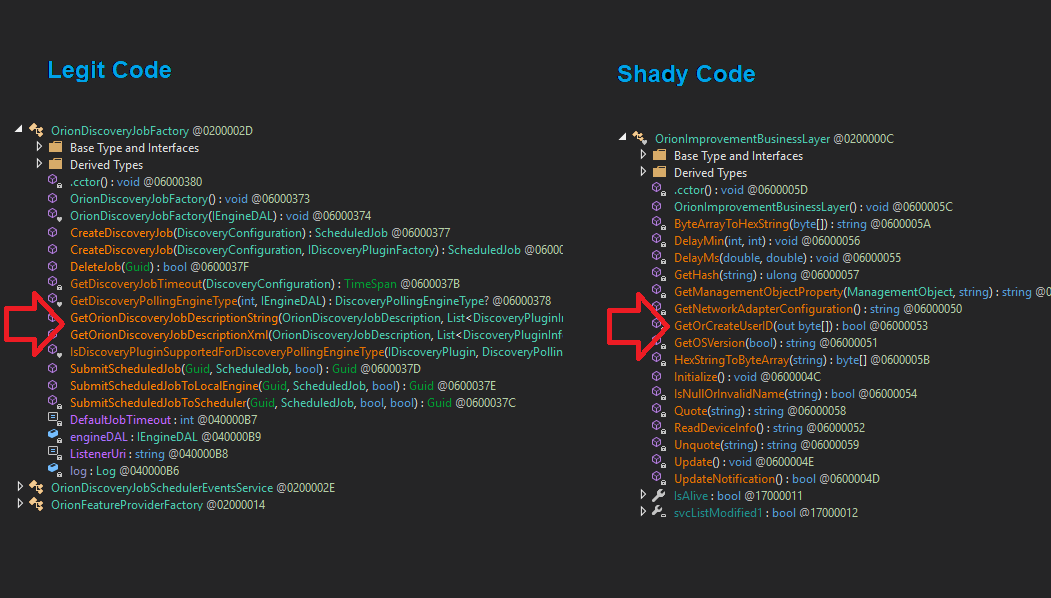
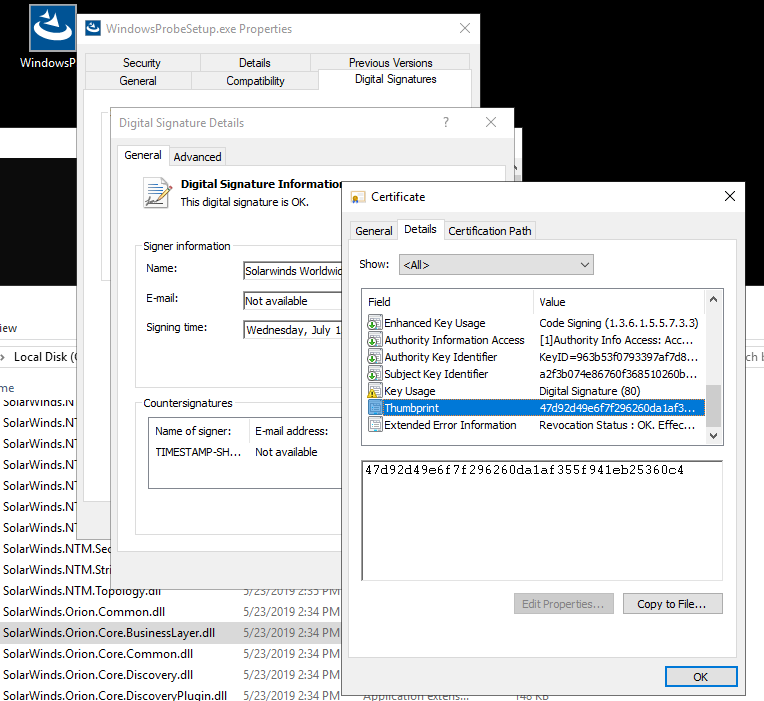
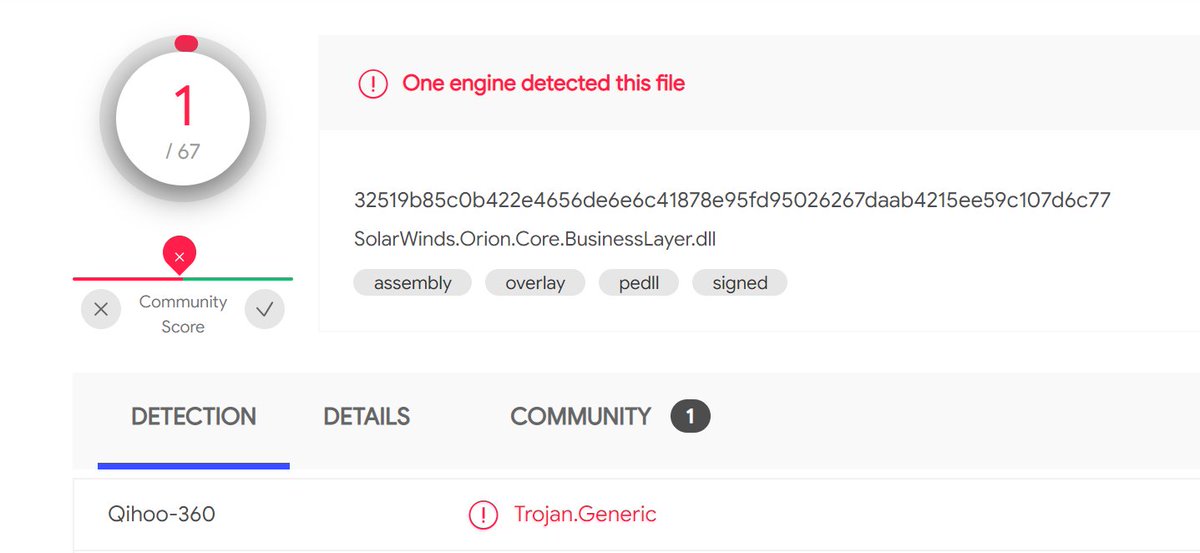
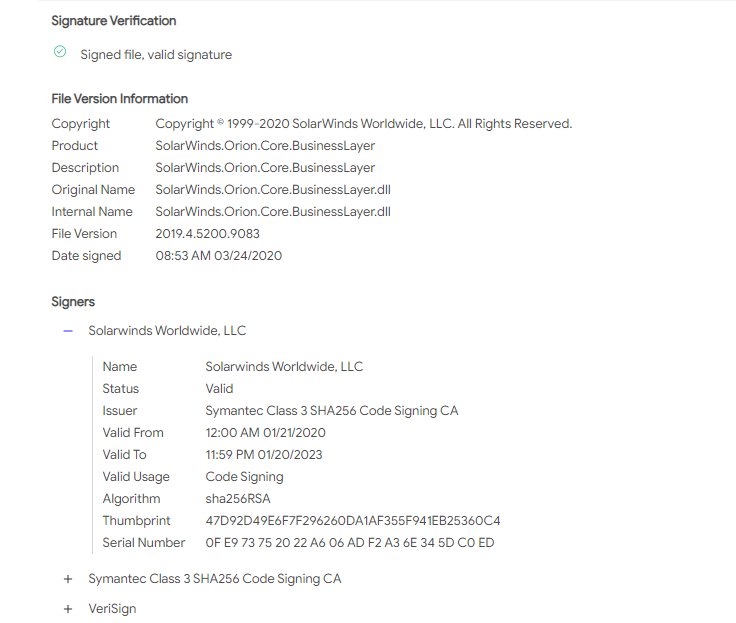
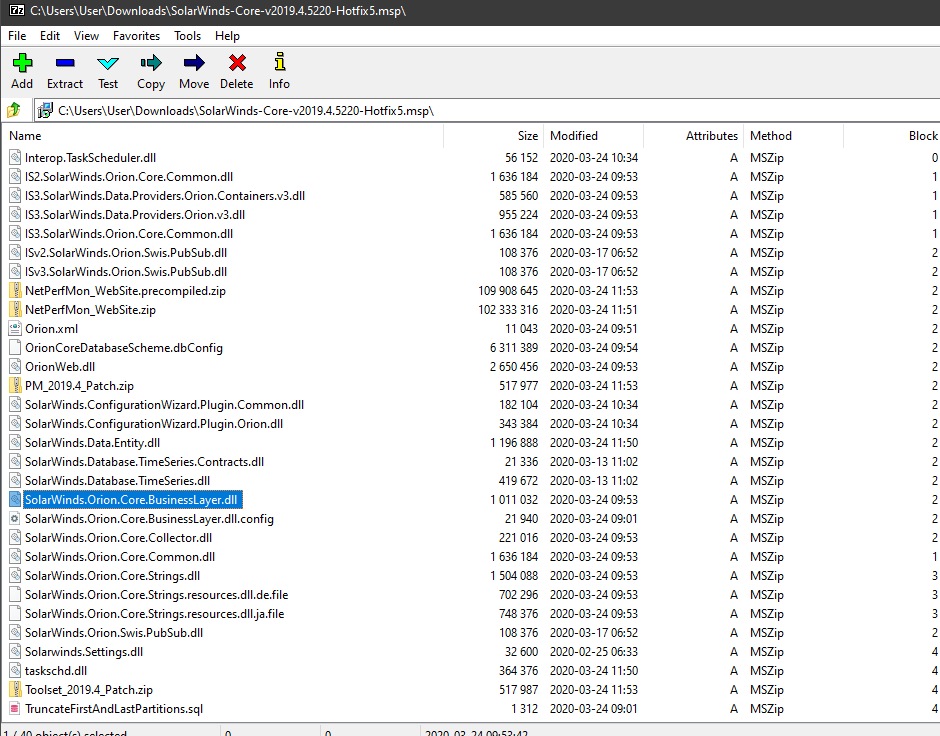
One of the anomalous #SUNBURST DLLs from October 2019 that Microsoft highlighted can be found in the SolarWinds Coreinstall.msi for 2019.4.5220.20161 - hxxps://downloads.solarwinds[.]com/solarwinds/CatalogResources/Core/2019.4/2019.4.5220.20161/CoreInstaller.msi 

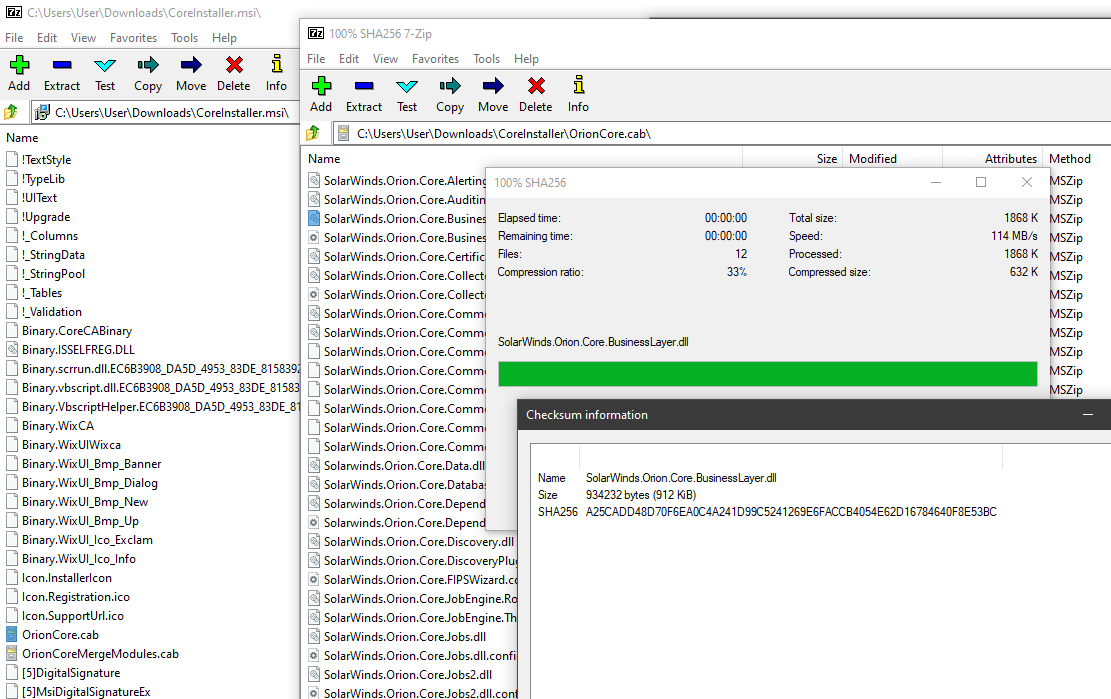
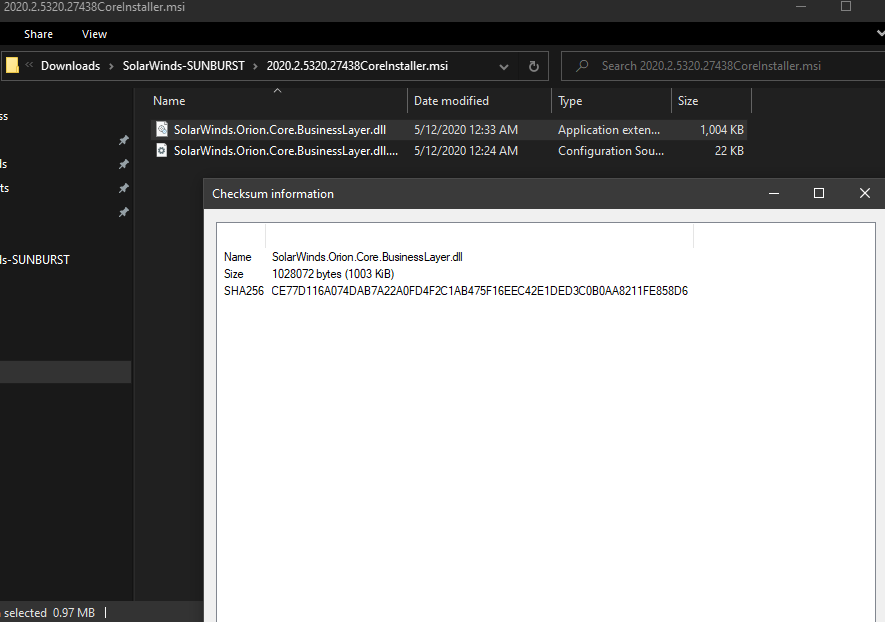
Malicious #SUNBURST DLL CE77D116A074DAB7A22A0FD4F2C1AB475F16EEC42E1DED3C0B0AA8211FE858D6 from May 2020 can be found in CoreInstaller.msi for 2020.2.5320.27438 -hxxps://downloads.solarwinds[.]com/solarwinds/CatalogResources/Core/2020.2/2020.2.5320.27438/CoreInstaller.msi 

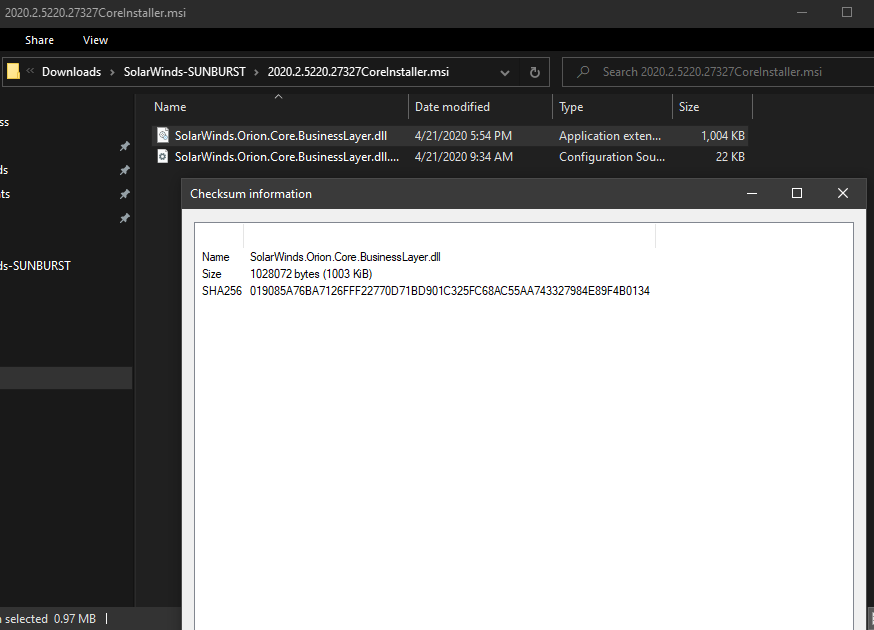
Malicious #SUNBUST DLL 019085A76BA7126FFF22770D71BD901C325FC68AC55AA743327984E89F4B0134 from April 2020 can be found in CoreInstaller.msi for 2020.2.5220.27327 - hxxps://downloads.solarwinds[.]com/solarwinds/CatalogResources/Core/2020.2/2020.2.5220.27327/CoreInstaller.msi 

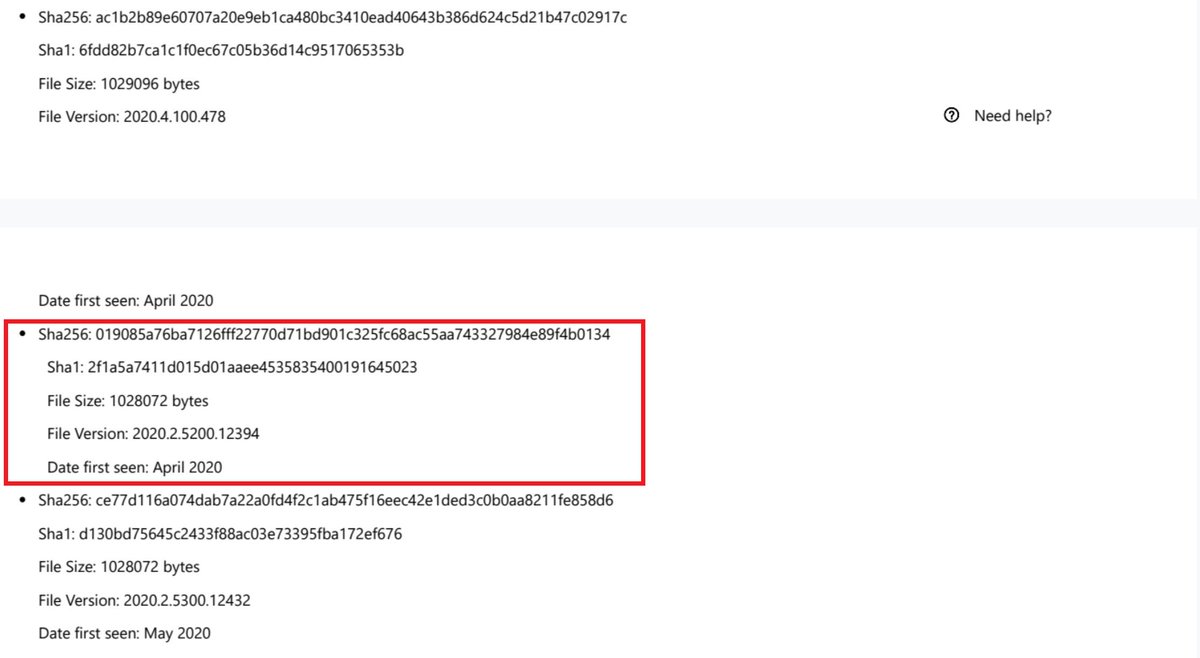
For those asking about the "obfuscation" of strings, here's a quick and dirty way to convert their base64 into a cleartext result. gist.github.com/KyleHanslovan/… 
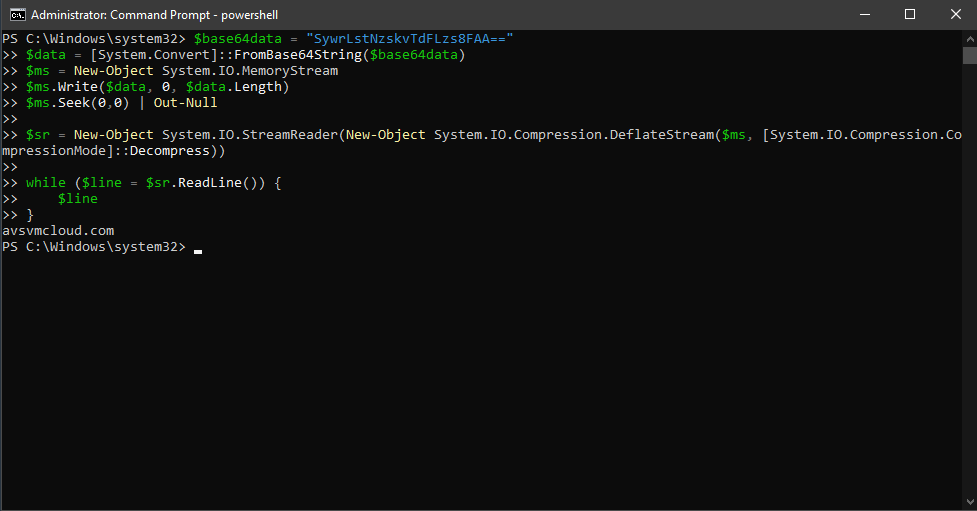
This gist emulates the ZipHelper class method Unzip() which base64 decodes then calls Decompress().
gist.github.com/KyleHanslovan/…

gist.github.com/KyleHanslovan/…
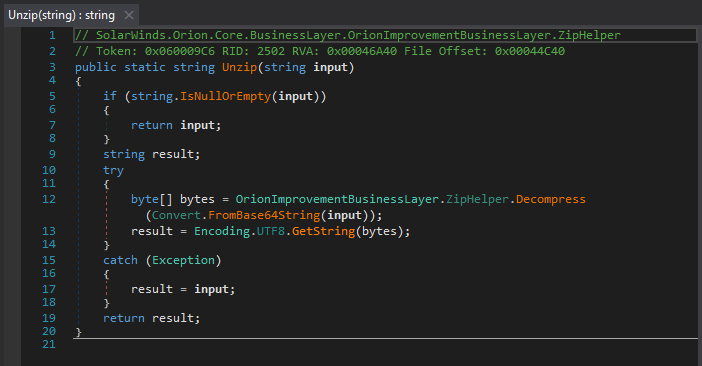
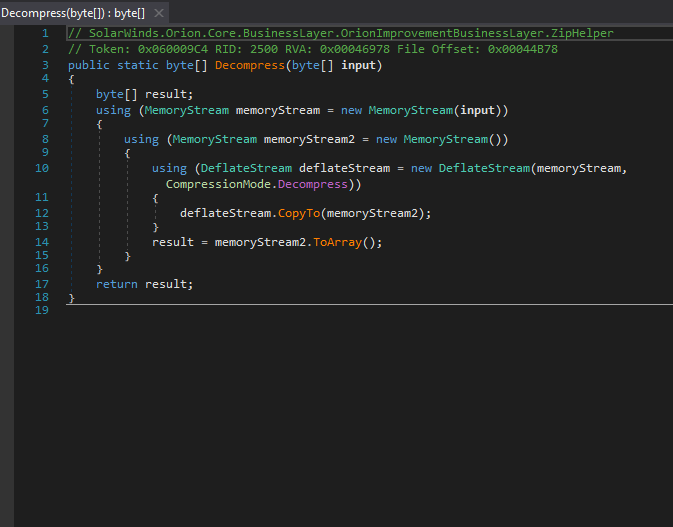
I'm stoked to see the three tainted SolarWinds packages we previously discovered are now removed/offline. Hoping no others exist. Hit me up if you find any additional ones so I can help coordinate with the SW team! 





• • •
Missing some Tweet in this thread? You can try to
force a refresh