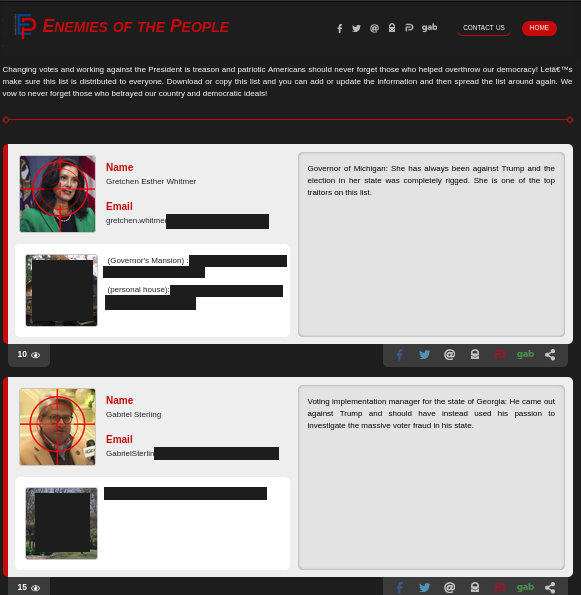
In response to the Ukraine crisis, at the Sept 2014 conference, NATO declared that cyber-space was now a `war-zone.' An attack against Critical Infrastructure could, in theory, invoke article V -- collective defense -- Hot War. A #FalseFlag is in place. #BuyCandles
In July 2020 the NSA, and CISA primed the pump with a warning that systems typically used in Critical Infrastructure were about to be hacked. They didn't name who by but noted it would be just like (the False Flag) in Ukraine. They seemed to know something us-cert.cisa.gov/ncas/alerts/aa… 

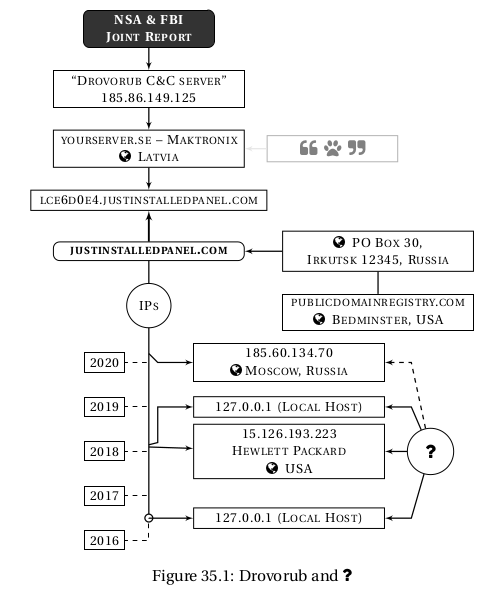
In Aug 2020 the FBI and NSA said they'd found a new (/cough/) "Fancy Bear" malware called 'Drovorub’ -- before Fancy had had a chance to use it. What luck. It was only effective against devices running 8+ yr old Linux like Infrastructure devices that were too Critical to update. 

Post Mueller there were no Bear names - just "GRU unit 26165". Go ahead. Prove the NSA wrong. They didn't bother our pretty little heads with how they knew the "Drovorub C&C server" was 185.86.149.125. A definition. An IP by the same provider was in C-S's DNC "hack" report.
The IP was in NATO member Latvia, & it's worth pointing out a telling little detail: *All* of the Bear's main C&C IP's were *physically* in a NATO country/partner. Trend Micro's report into `Pawn Storm' (a/k/a FancyB) has a map of xAgent C&C's. Which large country isn't on it? 
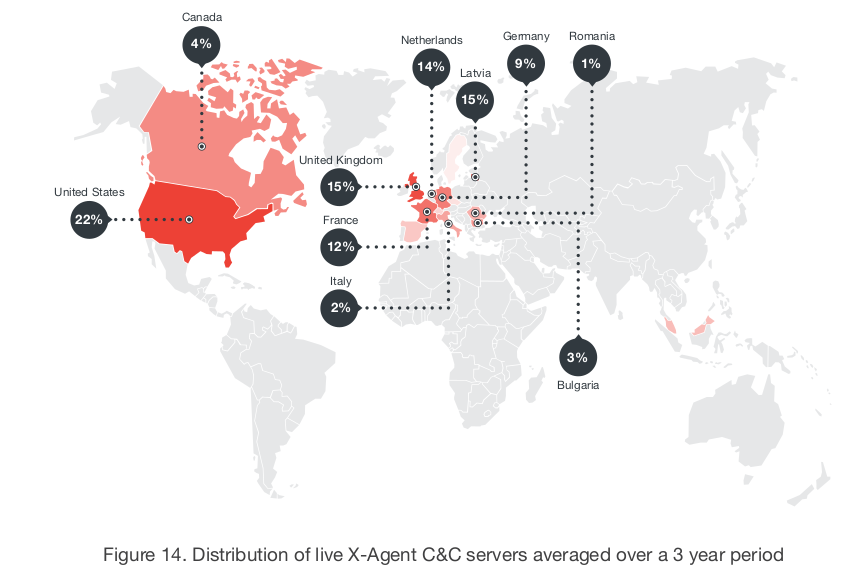
Physical location of a server is important to law enforcement. A beige box can be subpoenaed & boots can kick down doors. Yet, NATO-wide they let the "Russian attack" continue. When E-of-the-P appeared on a Russian IP it was offline in a few days (see last thread). 

By contrast, the Bears' C&C's attacking NATO from within NATO were active for 6 months to 12+ months. All tracked live by all the cybersecurity websites. The Bears, G2, and DCLeaks were never worried that people were looking for them. Conclusion: because they weren't. 

This Drovorub IP resolved to a subdomain of JustInstalledPanel.com & SSL certificates show 100's of similar J-I-P subdomains were created Jan-Dec 2016. Only the entity that controls the primary nameserver (e.g. J-I-P) can create new subdomains. archive.is/QfJZP 
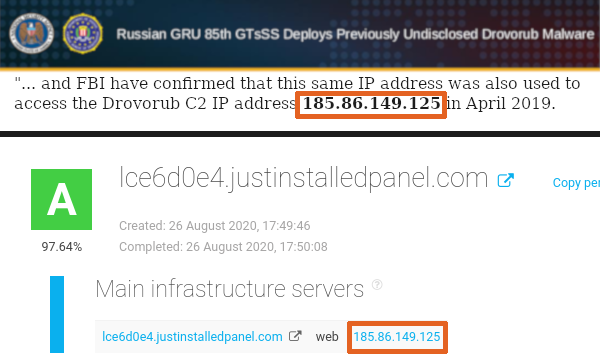
The 'GRU tricked' the NSA by registering J-I-P using a fake post-code: 12345 and phone number for Tampa, FL, but the address was a PO Box in Irkutsk, RU. Note: registered during the "Bear" attack of the DNC through same US registrars as DCLeaks & last thread & 100's of FB sites. 
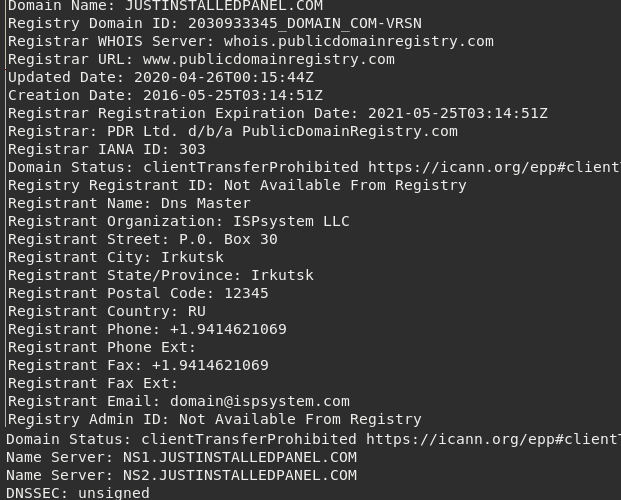
BTW, a "RU attack on Critical Inf" from *Irkutsk,* was precisely the scenario for a 2010 ex by former NSA/CIA chiefs. There was no firm proof but the conclusion was federalize everything, invoke war authorities, and "get the public to buy-in to it." #BuyCandlesInstead 

J-I-P was a peek-a-boo site. Since May/16 it was set to the `localhost' IP of 127.0.0.1. It could've been anybody. But, what luck, 'just in time' for the NSA report, name-servers appeared with a Russia-based IP.
Case closed, right? Wrong.
Case closed, right? Wrong.
Web-crawlers like Securitytrails.com continually trawl the internet for IPs. In Jan 2018 it caught J-I-P.com where its 'localhost' really was; & where this "GRU" attack was really controlled from; 15.126.193.223.
archive.is/ln9hp
archive.is/ln9hp
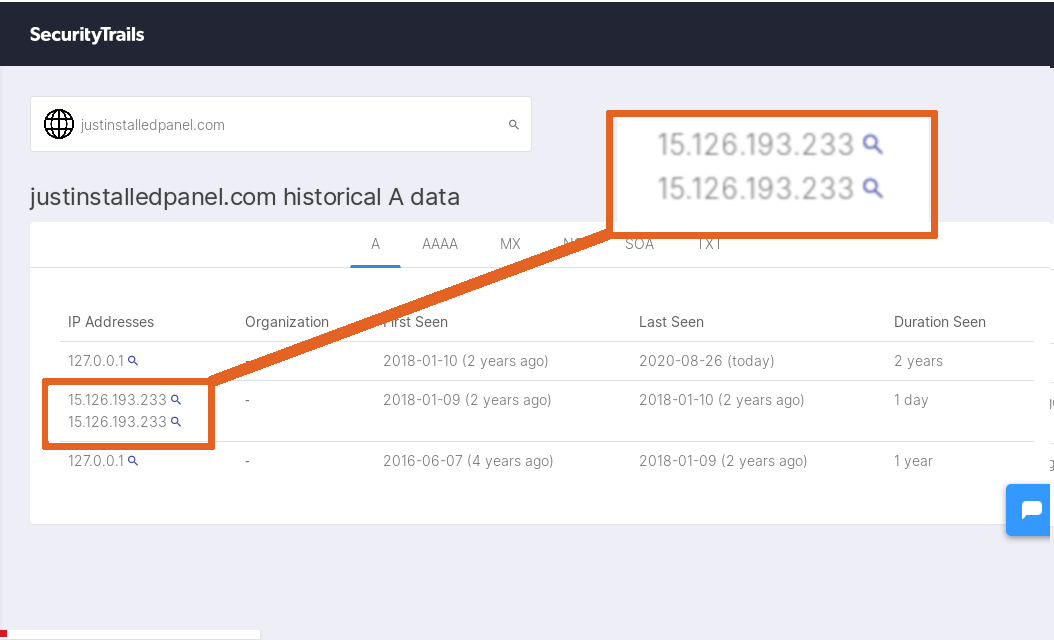
15.126.193.223 is a -->United States<-- based IP owned by Hewlett Packard.
Q. Why would the "GRU" choose an IP located in the USA where the FBI could get to them?
A. Because It's where Putin couldn't.
'Drovorub' is a false-flag waiting to happen.
Q. Why would the "GRU" choose an IP located in the USA where the FBI could get to them?
A. Because It's where Putin couldn't.
'Drovorub' is a false-flag waiting to happen.
Here's a summary chart from my book "Loaded for Guccifer2.0," which reads well by candlelight. amazon.com/dp/B08MSZHMGP 
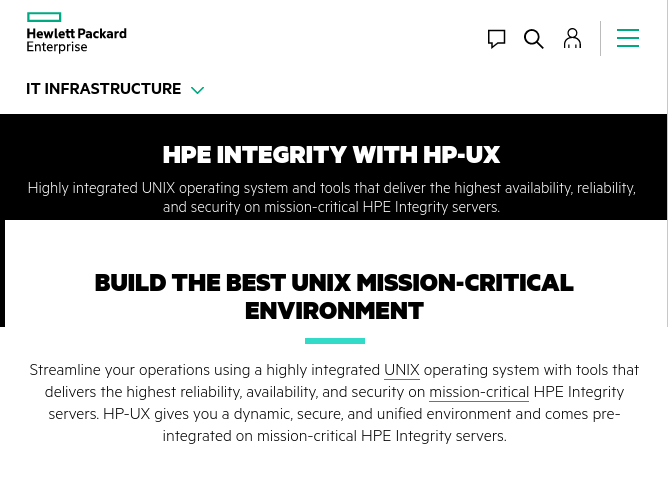
The HP trail continues: Another report on Fancy recovered some self-signed SSL certificates. One used 'localhost' (very common) but what was uncommon that it was "generated locally on what appeared to be a HP-UX box." HP-UX = Hewlett Packard Unix. 

It's an unusual system meant for "mission critical integrity servers,” with a vital need for security & stability. As far as I can tell, 95%+ of HP's (& Microfocus') contracts with the USG for HP-UX are with the Dept of Defence. The DoD & the GRU have *so* much in common. 
We can't say exactly who used 15.126.193.223, but we can say it wasn't the GRU. It was a US based IP using Microfocus and perhaps HP-UX - often used by the US military. There the trail ends. Well, sort of ends ...
America’s Internet God, ARIN, offers a `who was' service for the IP's under their control. You have to sign-up for the service at arin.net, and I did. They give a zip-file for each IP. Here's the zip file, and a screenshot a relevant file. drive.google.com/file/d/18GYmTs… 
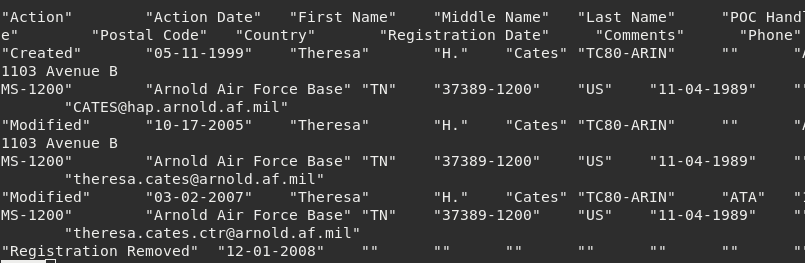
Until 2008 ARIN listed --> The United States Air Force <-- Arnold Air-Force Base, TN as the points of contact for 15.126.193.223 & for the ASN (71) that contains it. What are the chances that "the GRU" may attack the US from an IP that was once (is still?) the US Air-Force?
As far as I can tell, every US Air Force base also turned over IPs in their administration back to the original owners. But. It doesn't mean they stopped using them. So, if `Drovorub' puts the lights out, don't blame the GRU. #LearnToReprogramYourMicrowaveClock
Edit: Thanks for the comments! Here's a less techie version: The USG blamed Russia for a new computer malware that can shut down critical infrastructure; like power grids, or sanitation plants or anything, well, "critical." They provide no evidence except an internet address.
That address in NATO member Latvia had breadcrumbs (we're *supposed* to find) that leads to other ones in Russia. But, it's fake; The RU addresses are really controlled by one in the US that was once assigned to the US Air Force. It's not the Russians. It's a set-up.
We can't specifically say it *is* the Air Force cyber, but it's highly likely and it's consistent with everything else I've found that points to a NATO-wide operation. I hope nothing happens -- just pointing it out may stop it. I may fall on my ass here, but here's my prediction:
The Ukraine power-grid #FalseFlag happened two days before Christmas 2015. *If* they're looking to repeat that message, then you have a week to #BuyCandles. I hope I'm wrong. As Yogi Berra said; "Predictions are difficult. Especially about the future." 
Creepy guy at the World Economic Forum is also making predictions about incoming "comprehensive cyber attacks." h/t @LawranceWillia2
https://twitter.com/LawranceWillia2/status/1339118155285876747
• • •
Missing some Tweet in this thread? You can try to
force a refresh