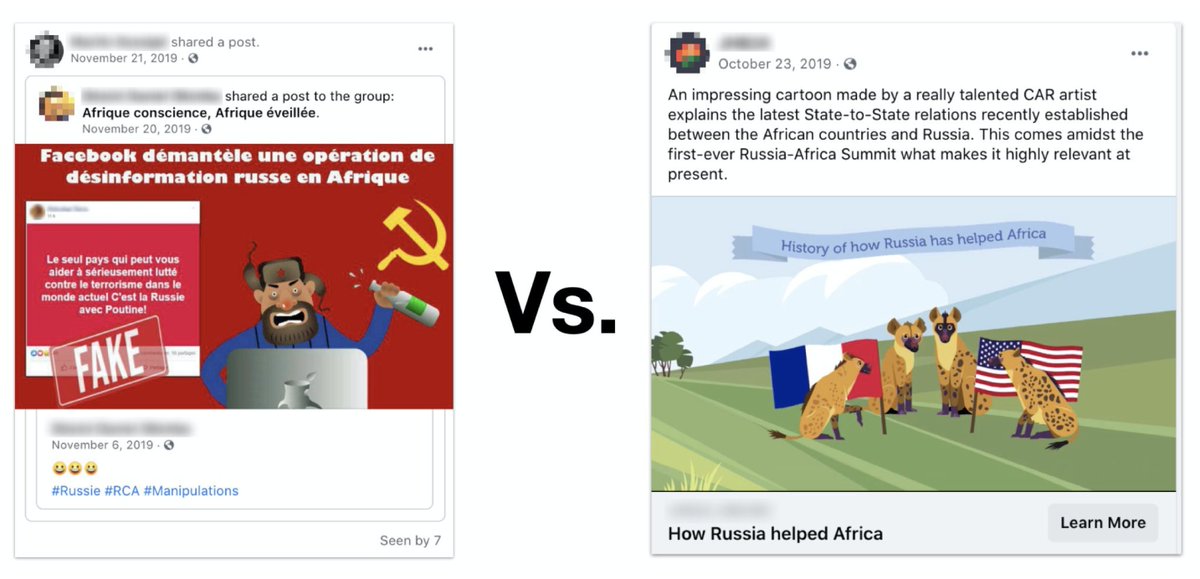
Fun read here from @conspirator0 on a botnet that uses clips from Dracula, for that authentic "I'm a human so I write text" look.
Presumably designed to fool algorithms, as it wouldn't fool a human.
At @Graphika_NYC, we call it "Dracula's botnet".
graphika.com/posts/draculas…
Presumably designed to fool algorithms, as it wouldn't fool a human.
At @Graphika_NYC, we call it "Dracula's botnet".
graphika.com/posts/draculas…
https://twitter.com/conspirator0/status/1339401586108477441
We came across part this botnet in the summer, when it was boosting the pro-Chinese network "Spamouflage."
This, from @conspirator0, is a typical profile. Note the broken sentence and word in the bio. No human typed that... at least not on that Twitter account.
This, from @conspirator0, is a typical profile. Note the broken sentence and word in the bio. No human typed that... at least not on that Twitter account.

Now compare the bio with the version of Dracula that's online at Tallinn Technical University: lap.ttu.ee/erki/failid/ra…
Coincidence?
Coincidence?

Nope, not a coincidence. Here's another from the same collection by @conspirator0 , together with a line from the same e-book. 

In fact, all the bots from this September batch in this image have single lines from the same e-book version.
Looks like we know what text the botnet was set to scrape.
Looks like we know what text the botnet was set to scrape.

So did the July batch, but with a +sign instead of the space - presumably because the automation wasn't all it should have been. 

The one difference between these different sets is what they were posting.
@conspirator0 found the first batch were pornbots, the later ones were cryptocurrency-themed.
@conspirator0 found the first batch were pornbots, the later ones were cryptocurrency-themed.
https://twitter.com/conspirator0/status/1339401586108477441
The ones we found in August, which used the same e-book version for their bios, were amplifying the Spamouflage network, which is pro-China / anti-US / anti-Hong Kong protests. 
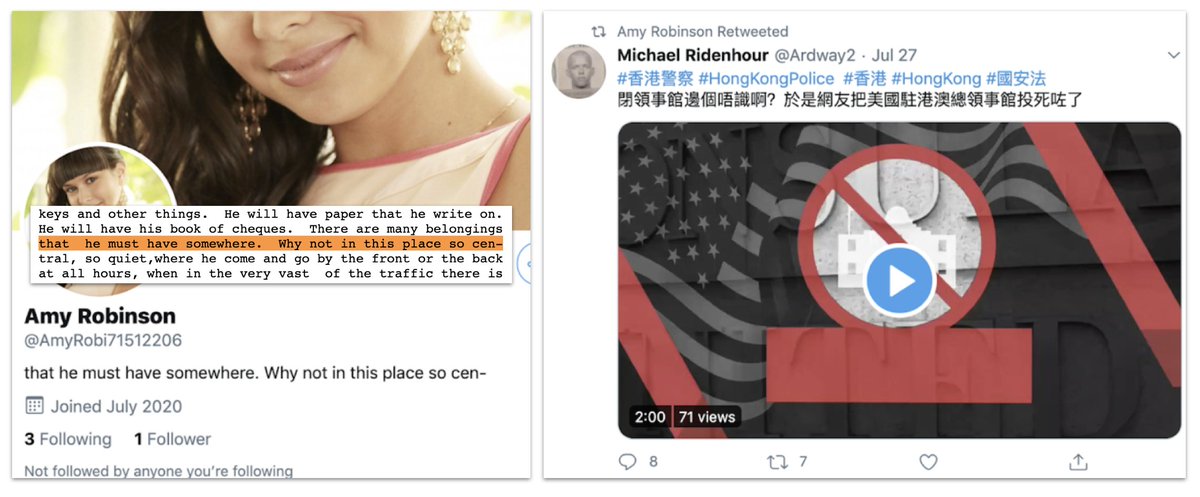
That's the thing with botnets. They can be vacuous, and then switch to propaganda if someone pays. So it's worth being able to spot them.
I wrote this a few years ago, after a little unpleasantness with around 80,000 bots.
Some of the possible clues.
medium.com/dfrlab/botspot…
I wrote this a few years ago, after a little unpleasantness with around 80,000 bots.
Some of the possible clues.
medium.com/dfrlab/botspot…
• • •
Missing some Tweet in this thread? You can try to
force a refresh