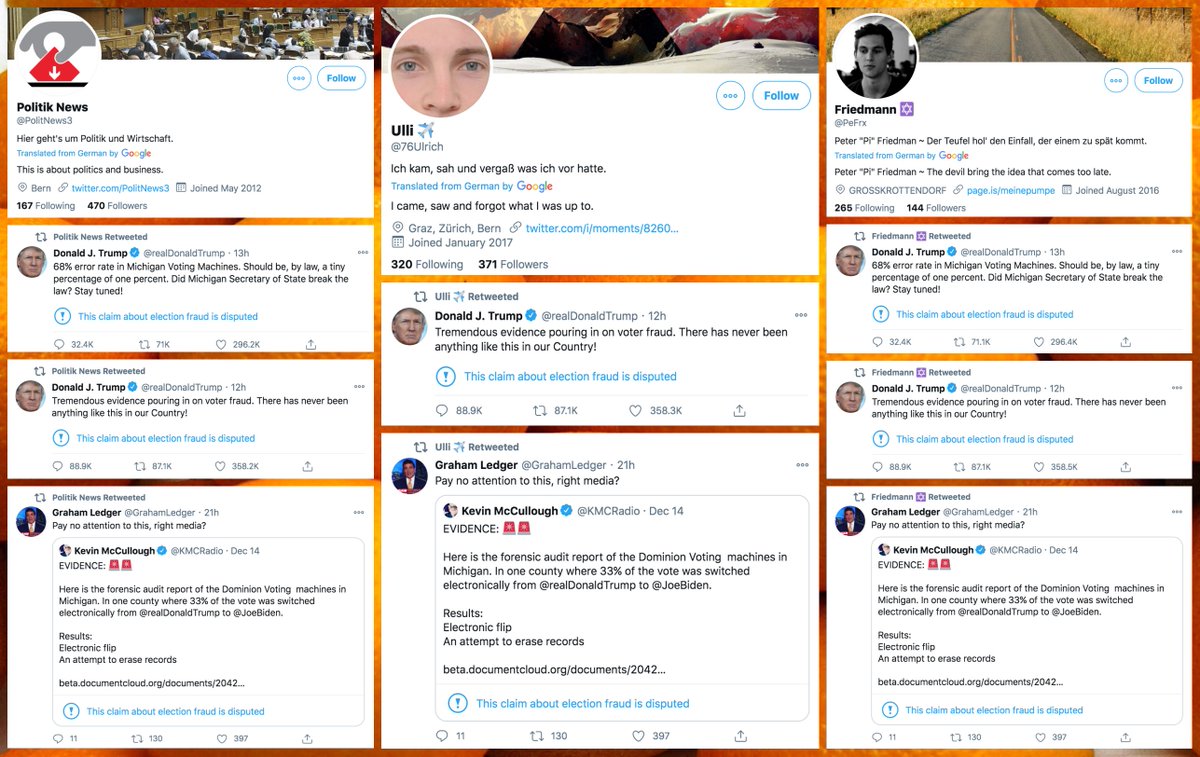
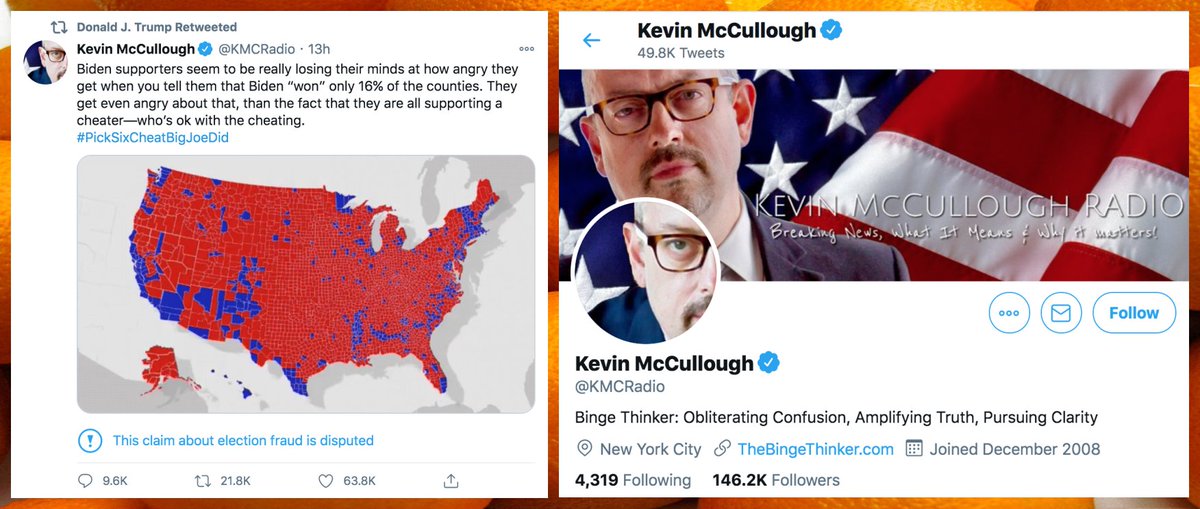
Earlier today, Trump retweeted a @KMCRadio tweet that mostly demonstrates the author's poor understanding of differences in population density in various areas of the USA. This thread, however, is not about that tweet - the topic is @KMCRadio's fake followers.
cc: @ZellaQuixote
cc: @ZellaQuixote
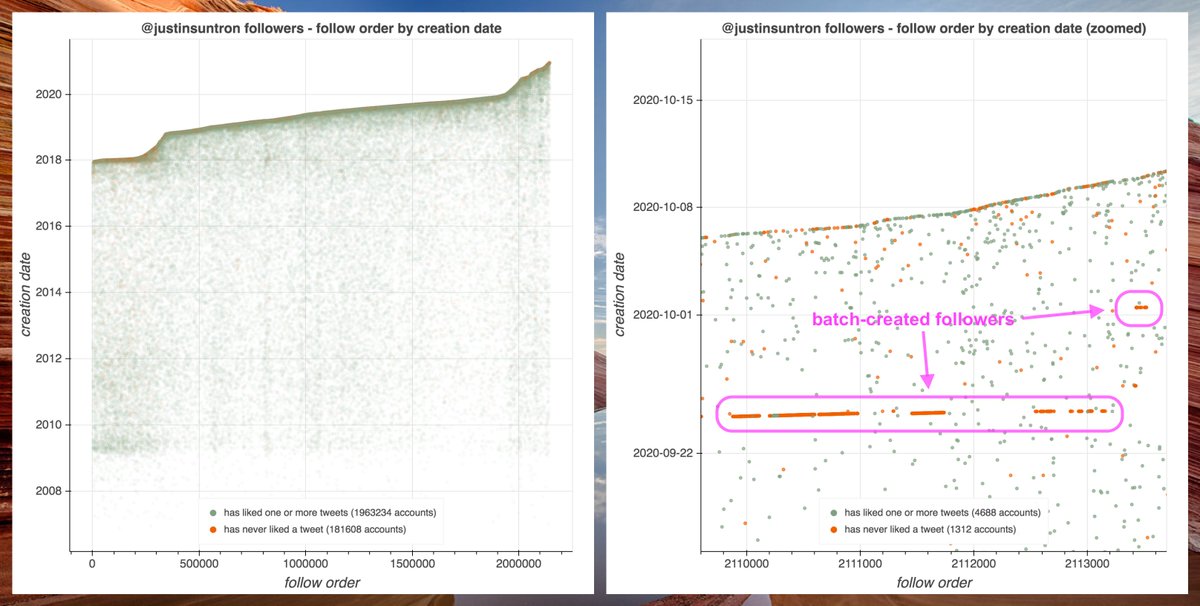
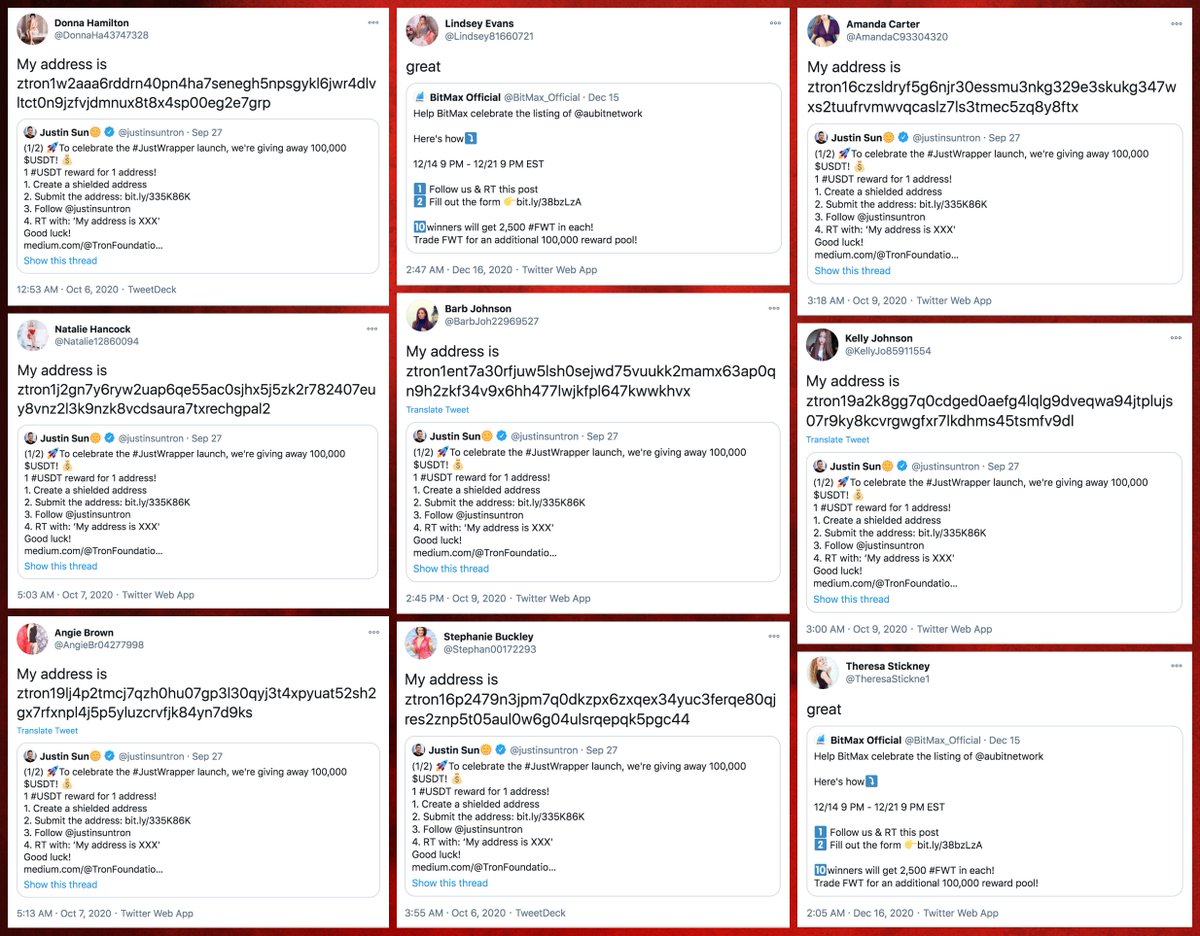
Although @KMCRadio's recent followers mostly look like organic #MAGA accounts, its early followers are anything but. Sometime in mid-2012, it was followed en masse by thousands of accounts created between 2009 and 2011 that have never liked a tweet (among other similarities). 



To find the remainder of this bulk follow network, we downloaded the followers of other accounts followed by @KMCRadio's early bogus followers, and repeated the process until we hit diminishing returns. (We didn't find many more - most of the network appears to follow @KMCRadio.) 

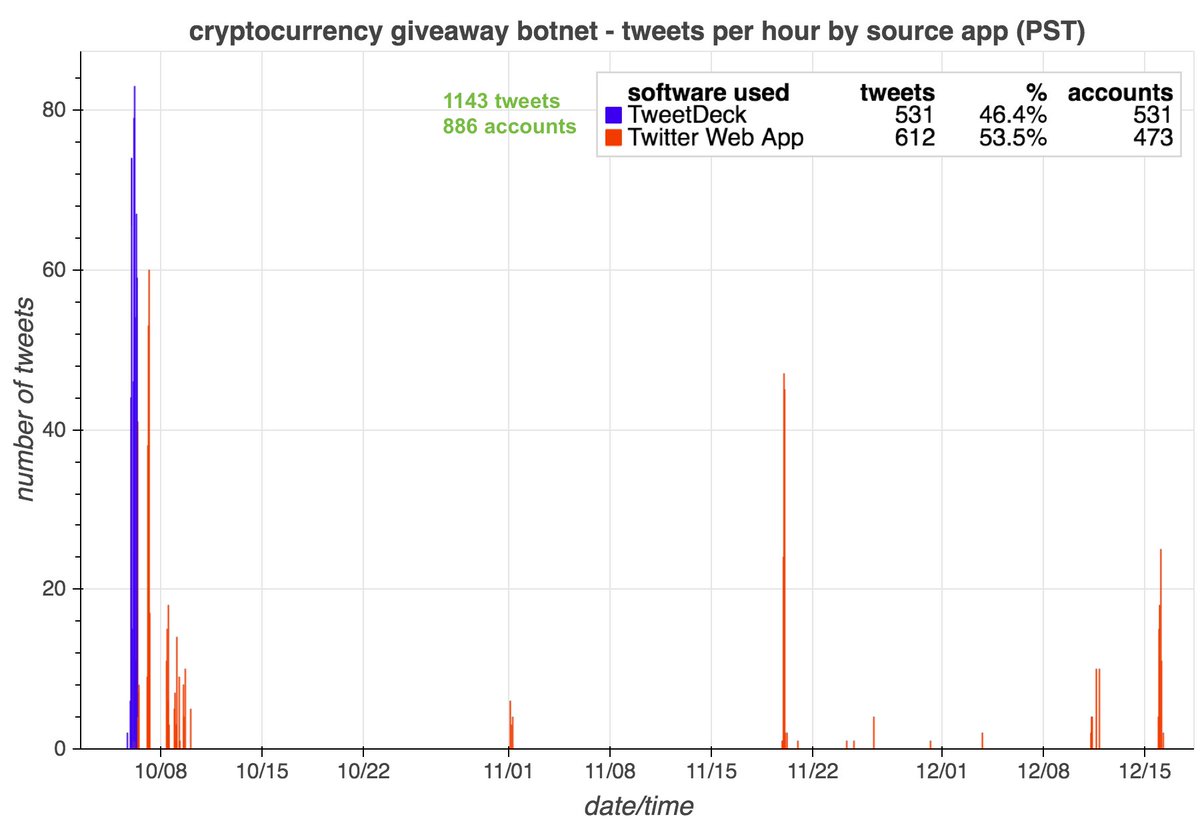
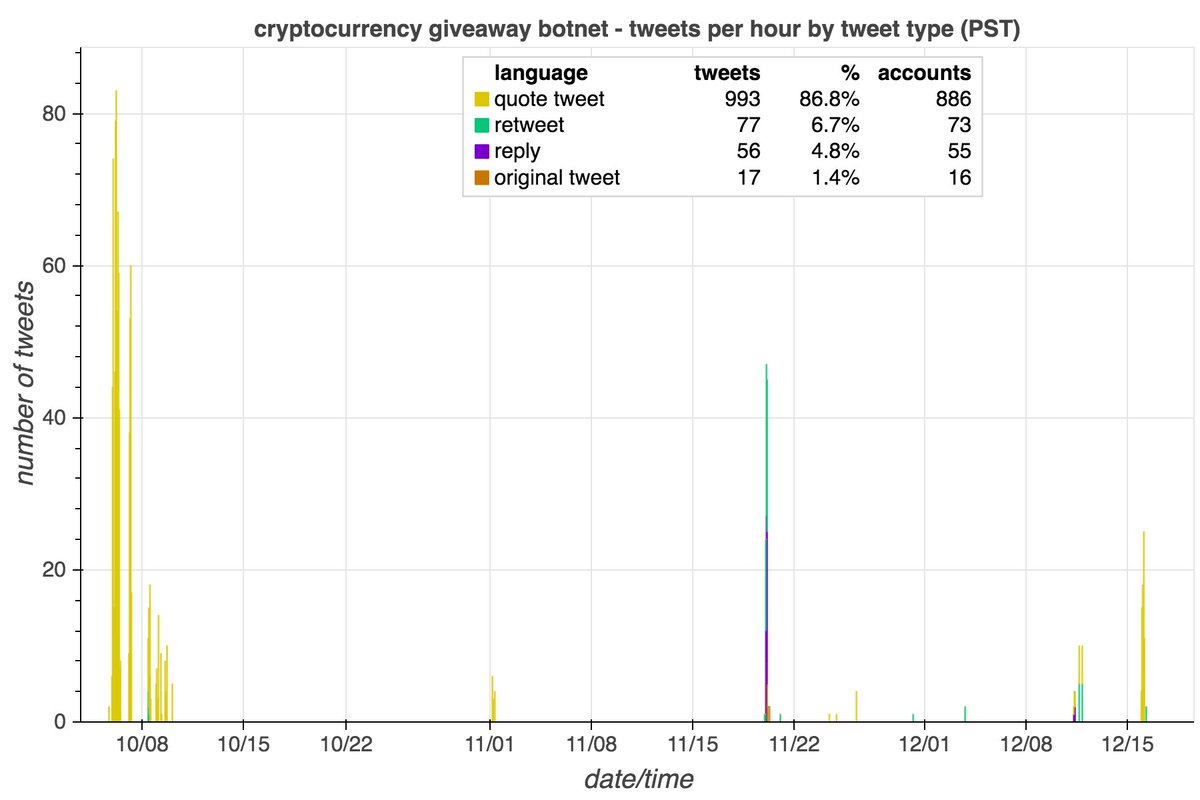
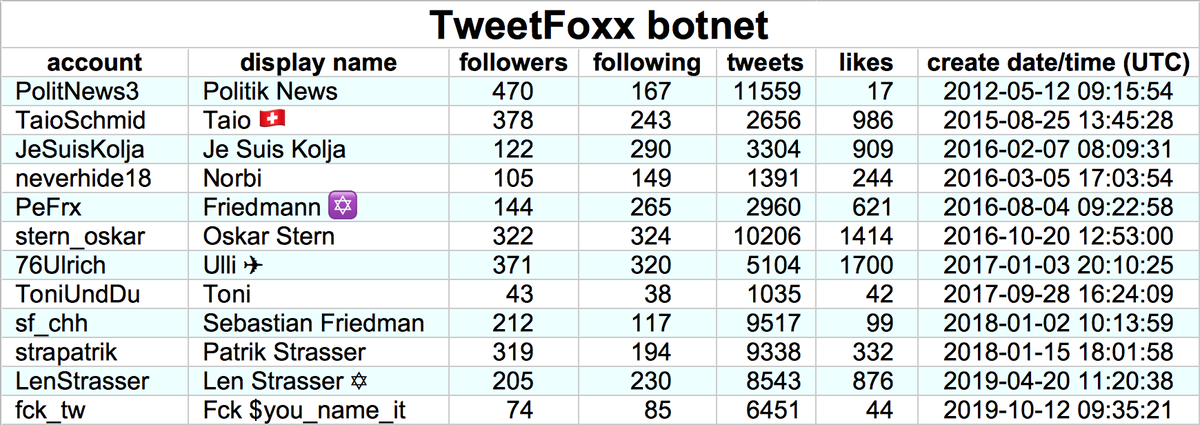
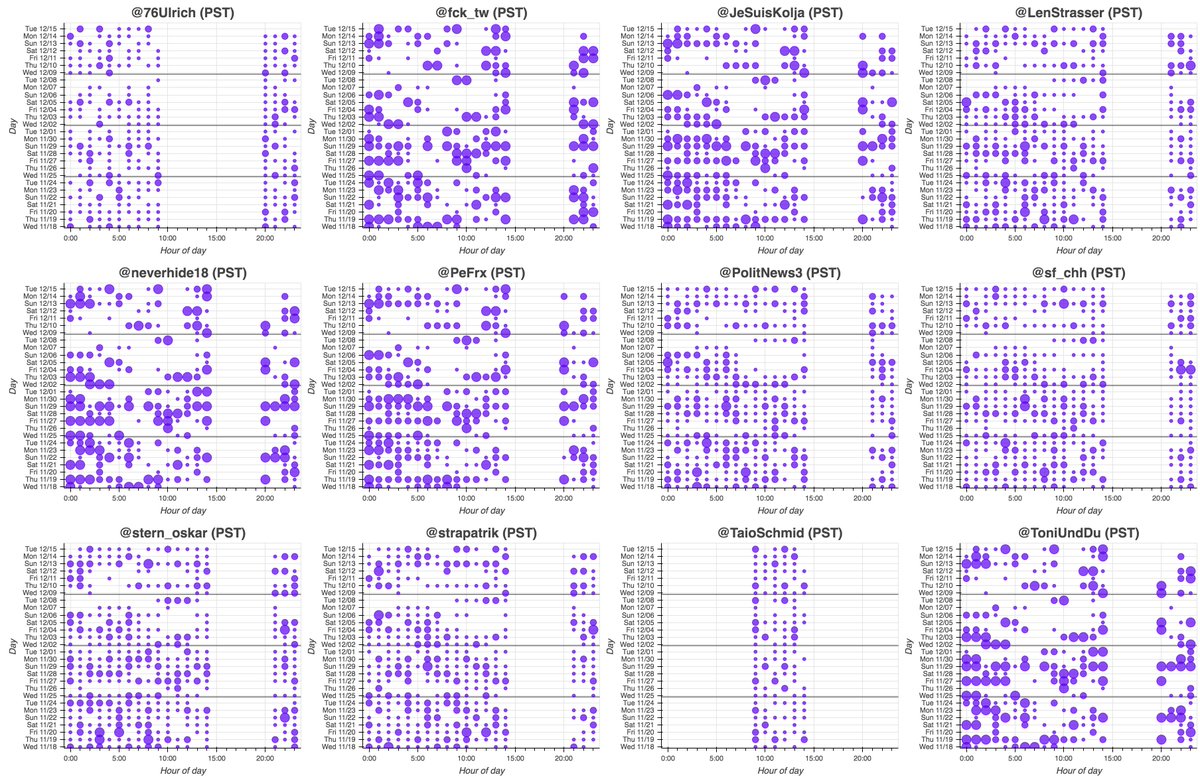
We wound up with 13850 accounts that we believe to be part of a bulk follow botnet, created between Jan 2009 and early Dec 2011. These accounts have been dormant since 2016, but when active tweeted via a mix of Twitter web products and custom apps (no iPhone/Android app.) 



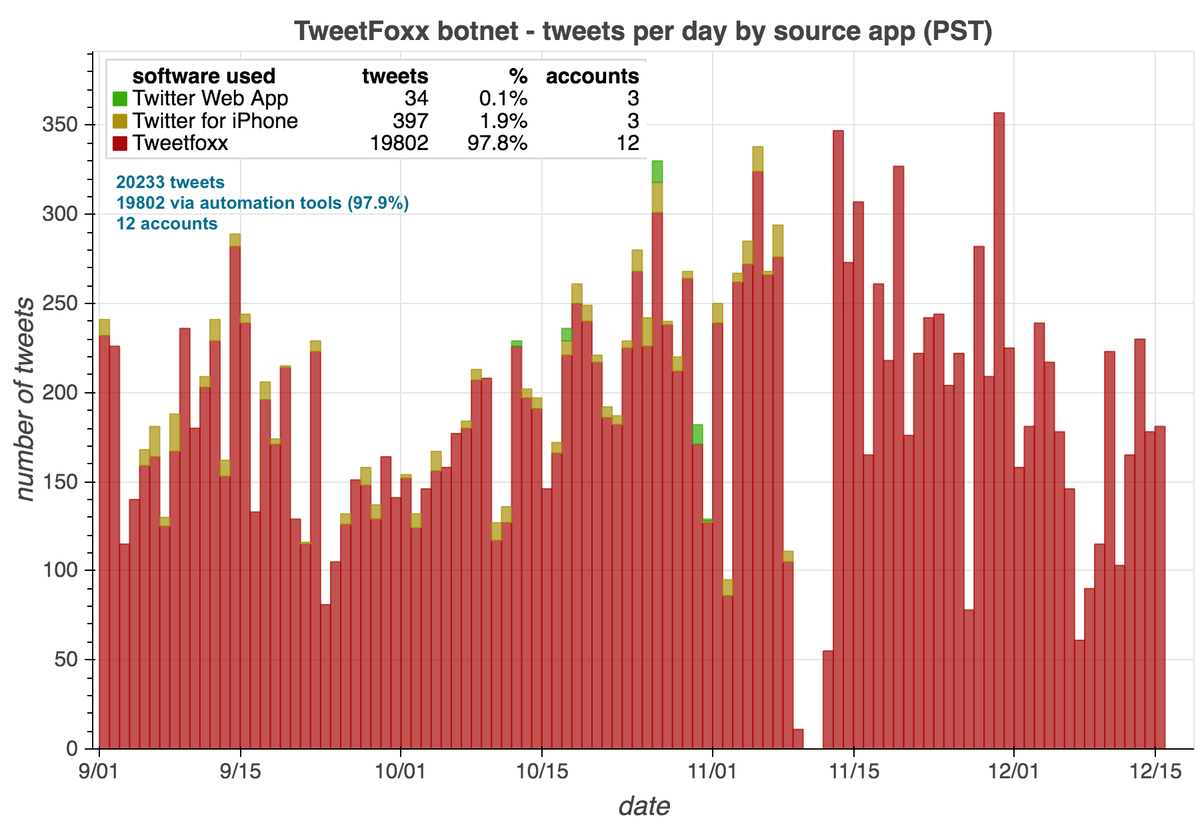
These accounts began their Twitter careers with occasional Portuguese tweets and then increased their volume and swapped to English in mid-2012, following a massive spike of activity in May 2012 that Twitter's language classifier was unable to handle. What happened? 

Answer: the May 2012 spike consists of 39168 tweets that contain links with no associated text (which is why Twitter couldn't determine language). 22 unique sites were linked from these tweets, including at least one (getmorefollows(dot)com) that may have been selling followers. 





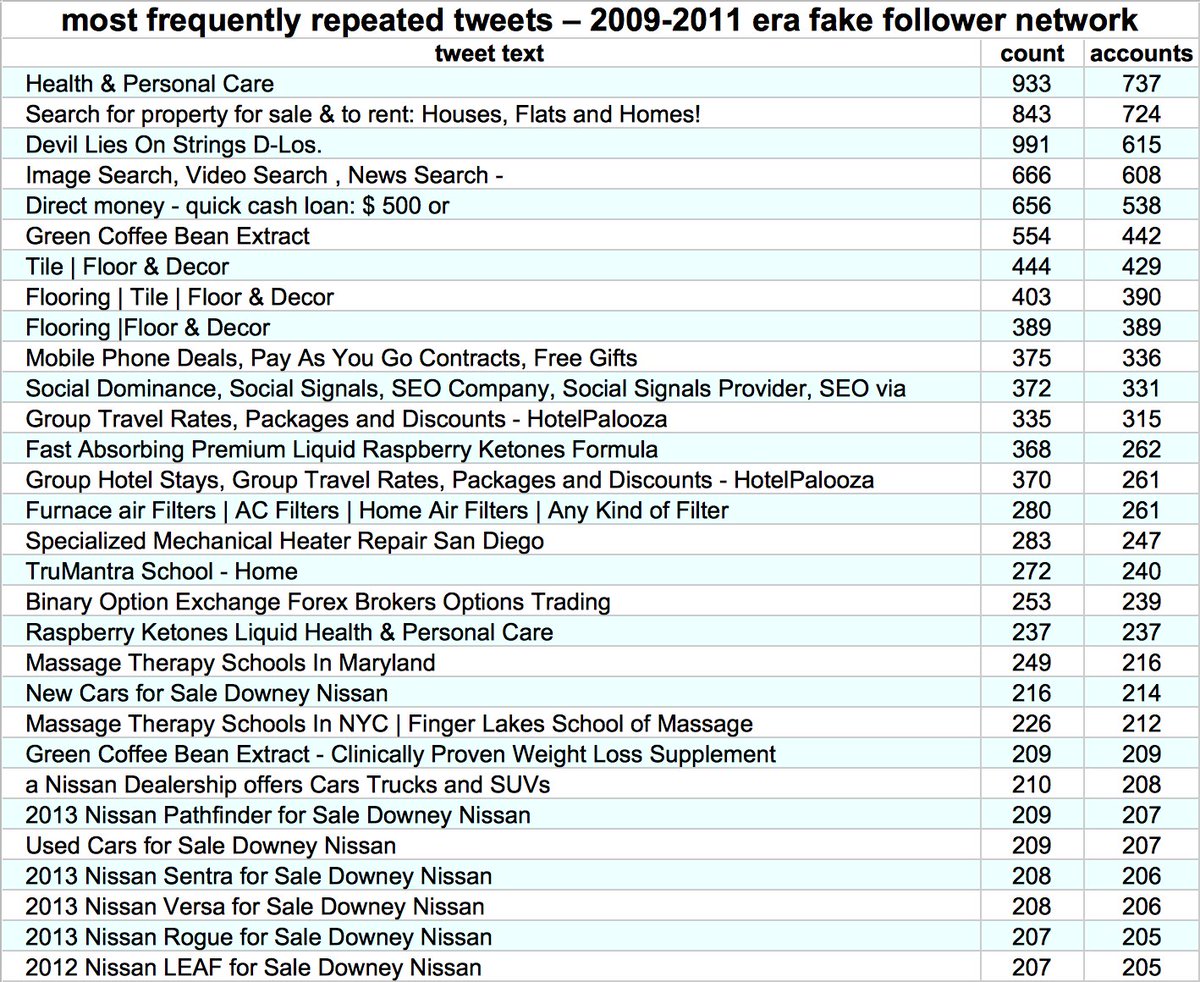
The botnet's tweets outside of the May 2012 spike (mostly subsequent tweets in English) are repetitive, and most appear to be commercial spam hawking various products and services. 
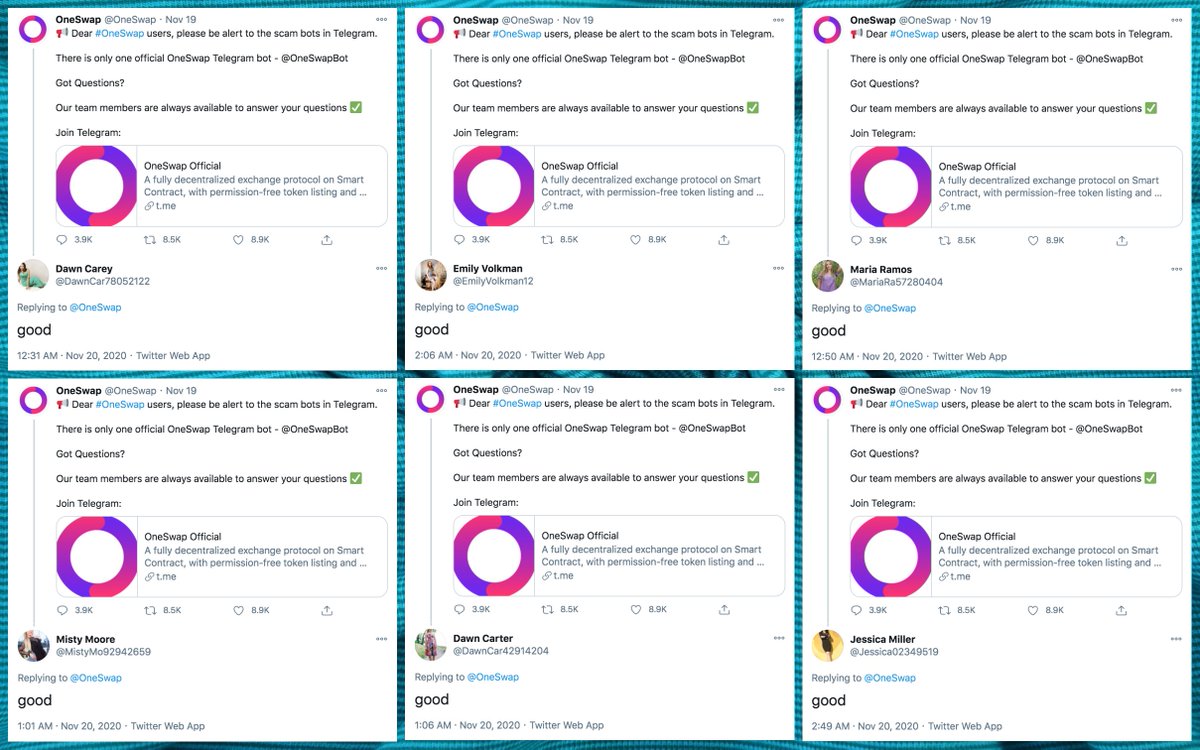
Finally, who does this bulk follow botnet follow? It's kinda all over the place, although most of the accounts appear to be commercial/promotional in nature. Most of the accounts followed by large portions of the network are English-language accounts. 

• • •
Missing some Tweet in this thread? You can try to
force a refresh