This botnet would like to give you a manual and support and help you to install and run "EA FX ROBOT", which is (allegedly) not difficult. #SpamTastic #WeHeardYouLikeBotsSoWePutABotInYourBot
cc: @ZellaQuixote
cc: @ZellaQuixote

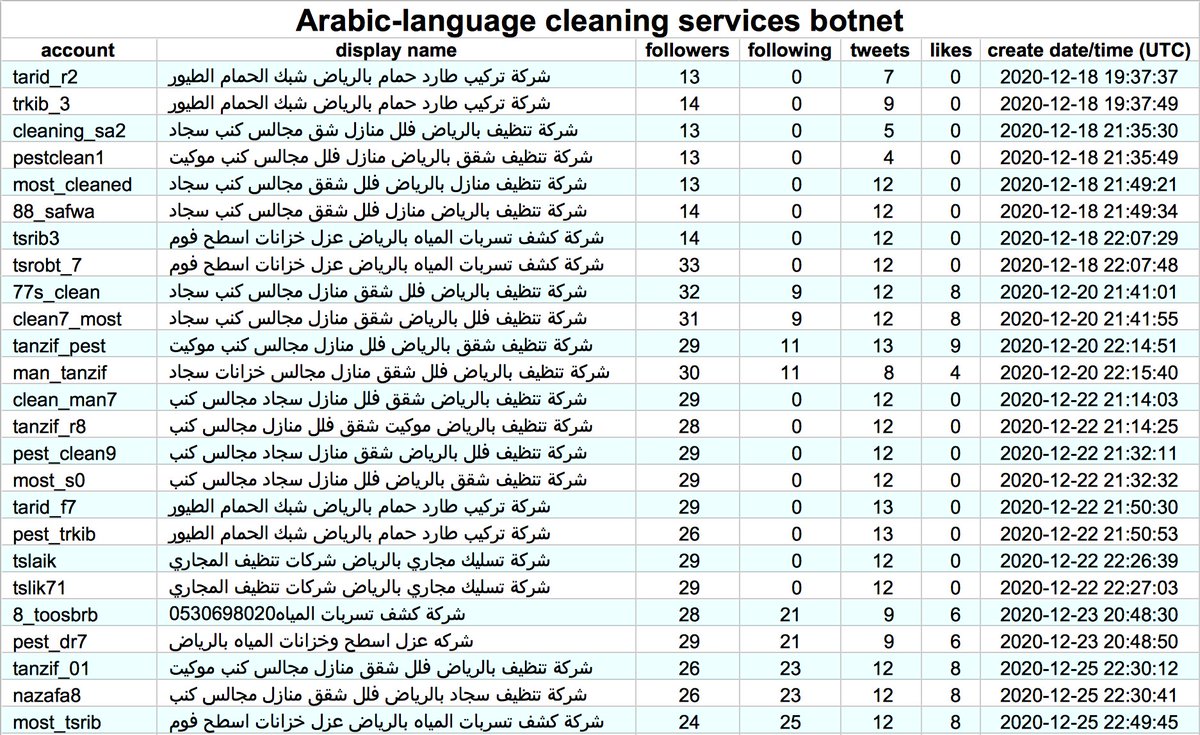
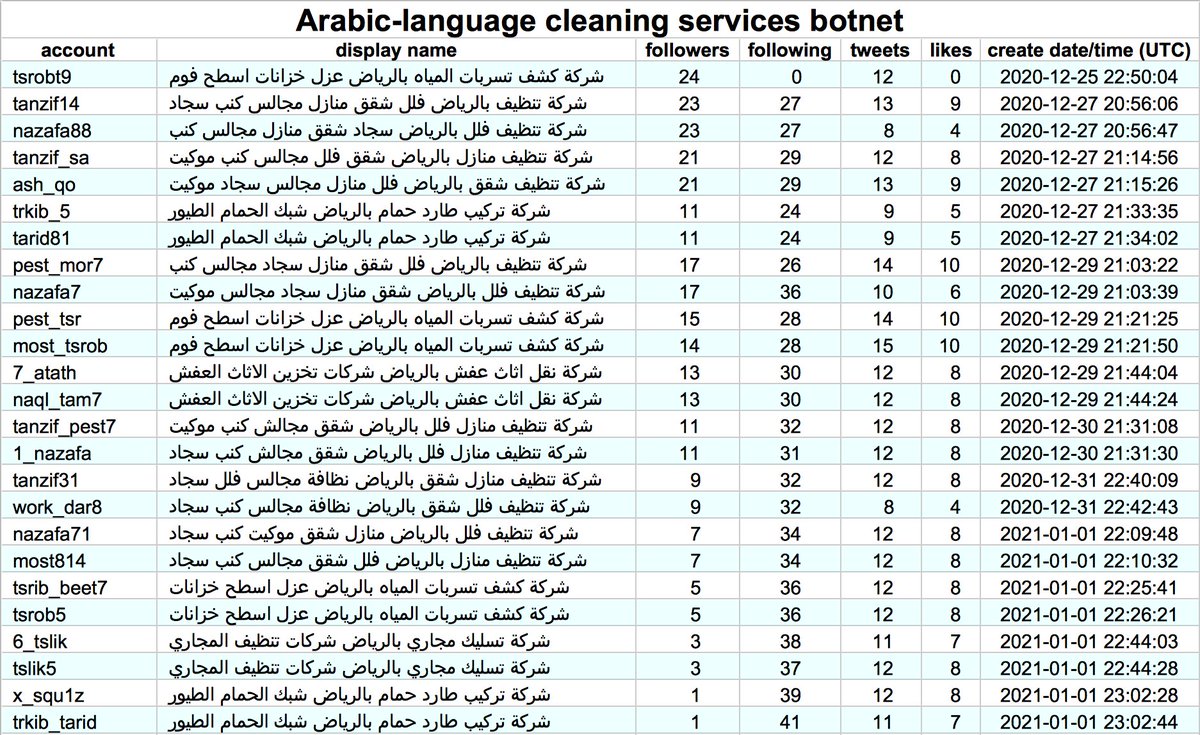
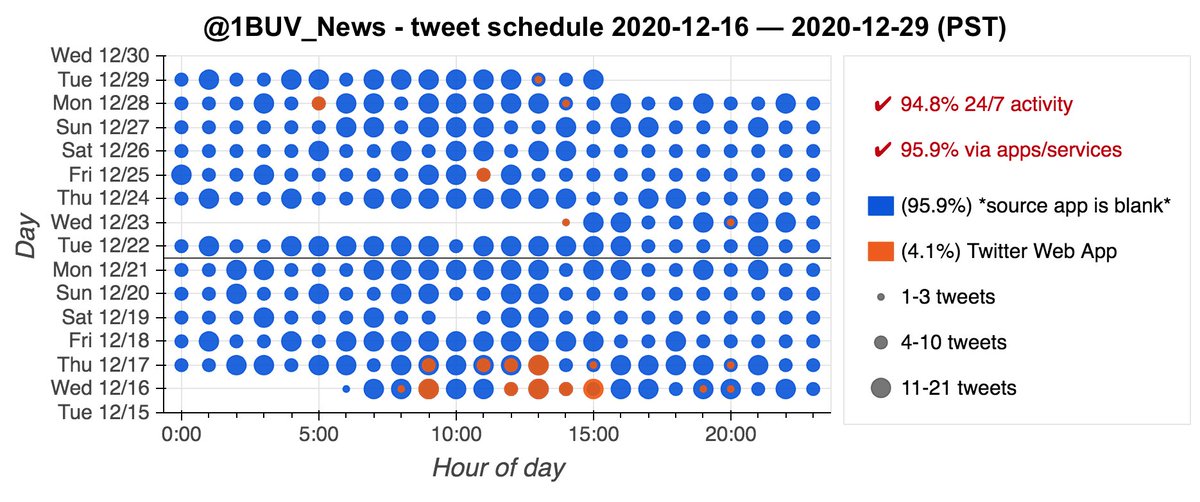
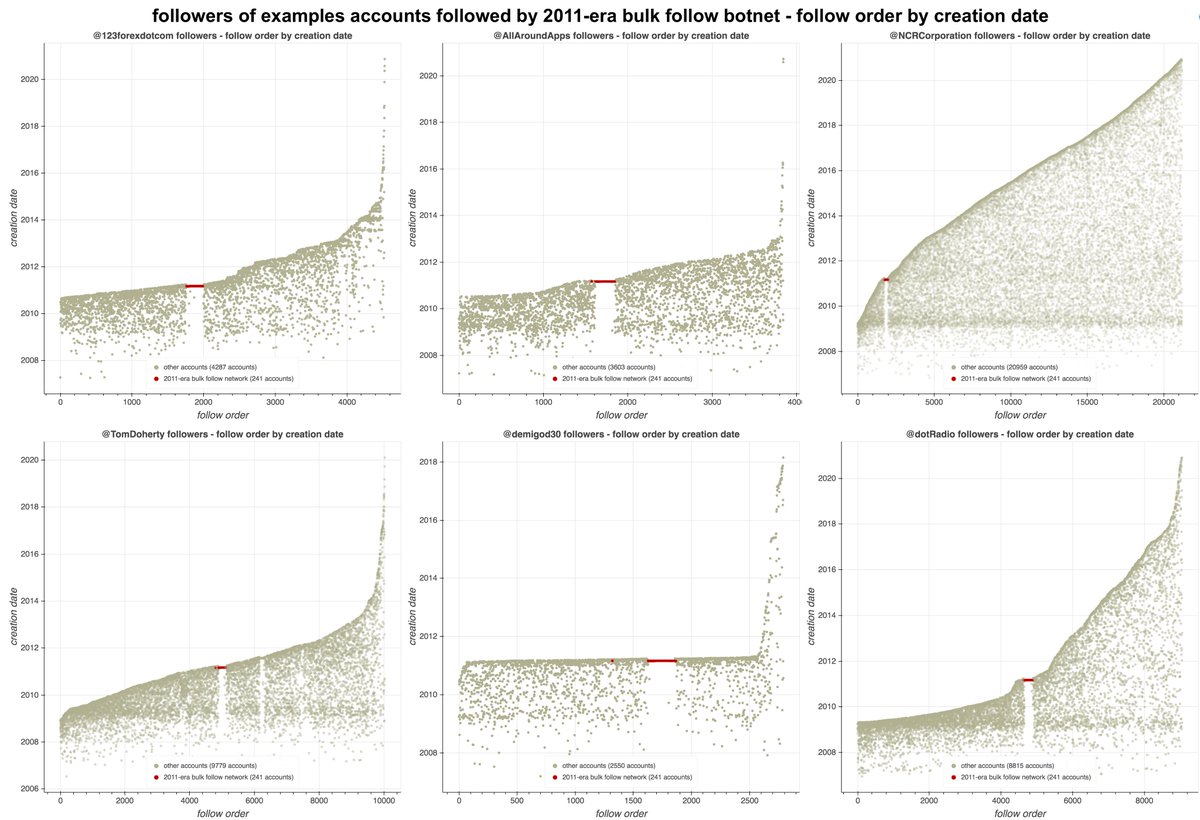
We found a network of 23 accounts promoting something called "EA FX ROBOT", created between October 2016 and March 2017. These accounts are automated, sending all of their tweets via a scheduling app called "Dynamic Tweets". Most of them operate on very similar schedules. 




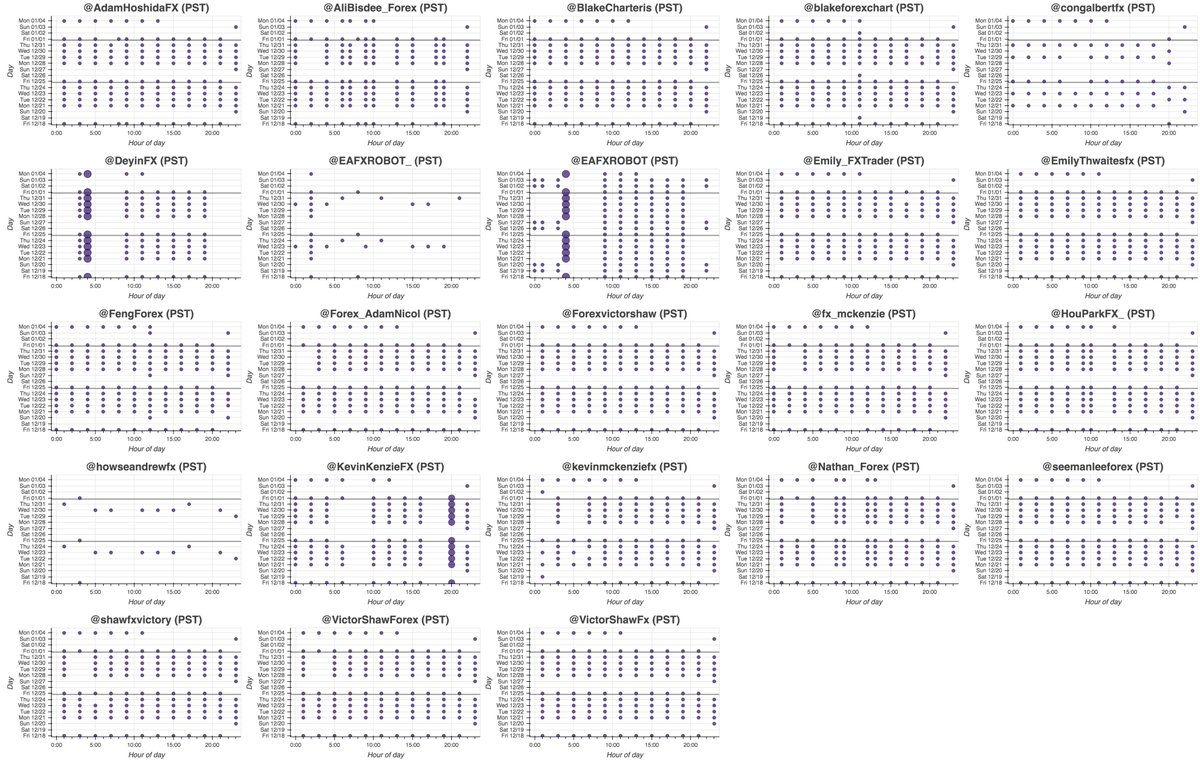
Hopefully you didn't get your hopes up about installing and running "EA FX ROBOT", because the associated website (eafxrobot(dot)com, the only site linked by the botnet) is no longer online and has been replaced with a generic landing page. The botnet soldiers on, though. 





This botnet is very repetitive, with many tweets repeated across multiple accounts. Most tweets promote "EA FX ROBOT", despite the product in question apparently no longer being available for download. 

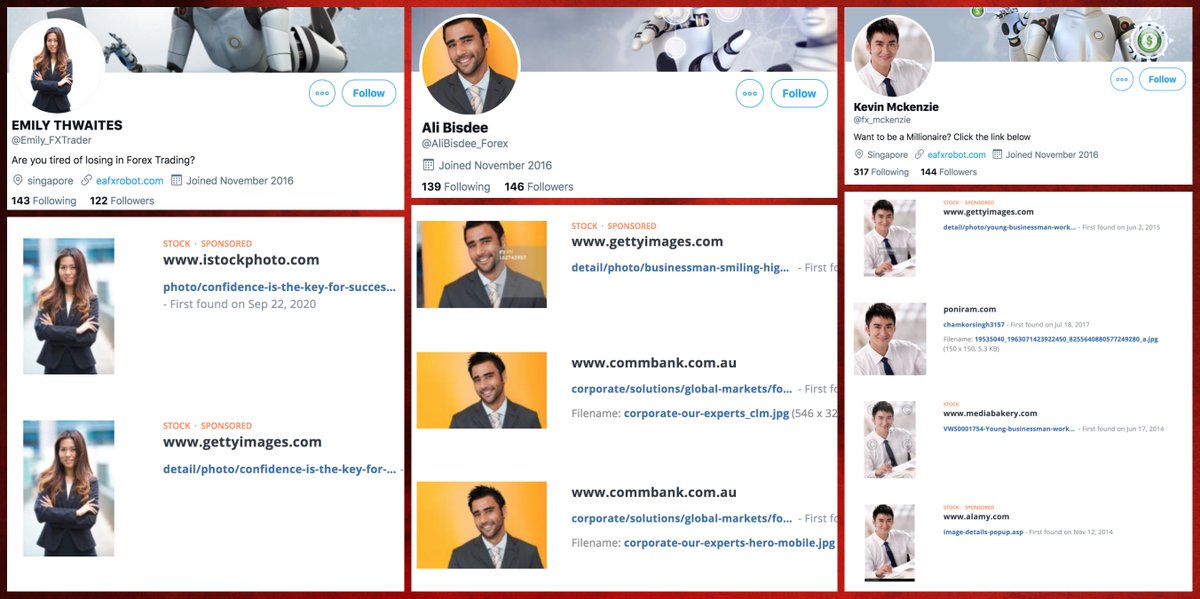
Unsurprisingly the bots in this botnet (at least those with photos of people as profile pics) use stolen profile pics. Based on TinEye search results, most of them likely originated with Getty Images. 
• • •
Missing some Tweet in this thread? You can try to
force a refresh