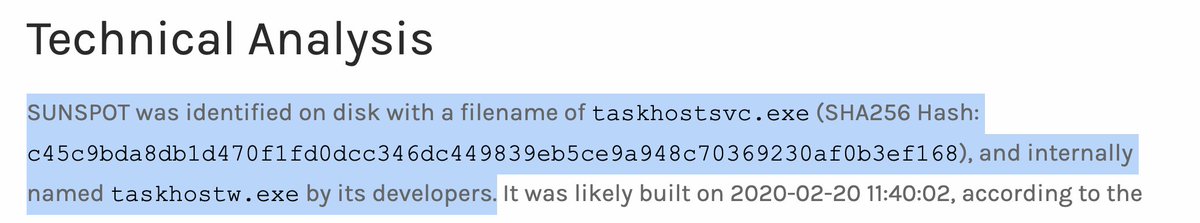
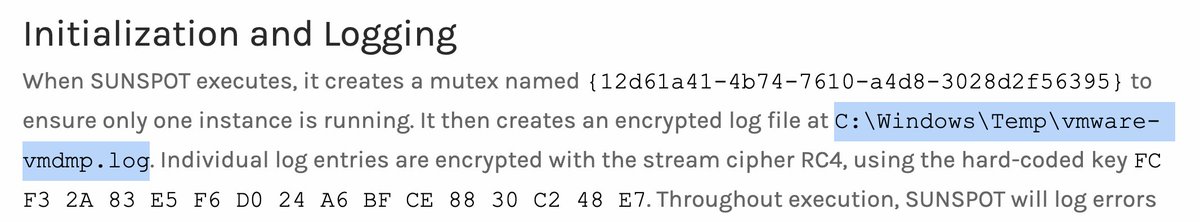
A brief thread on the @CrowdStrike blog on SUNSPOT...as I read it. This confirms CrowdStrike was one of SolarWinds' IR firms, which we'd heard rumblings of before. 

Why do I talk about naming things so much? This is why! CrowdStrike DOES NOT CALL THE ADVERSARY A BEAR. They call this an activity cluster named StellarParticle. This is important. It's also important to note that this is a different name than Solorigate... 

Choosing their own name was a good analytic decision by CrowdStrike because they control what is defined as StellarParticle. So what I would say is that StellarParticle and Solorigate overlap, but they are clusters tracked by two different companies. (see )
This is super important. This, and other details, tell us that SUNSPOT itself was specifically used in the SolarWinds environment. This means that SUNSPOT itself should really only be in SolarWinds' threat model. (However, orgs who could be part of a supply chain compromise... 
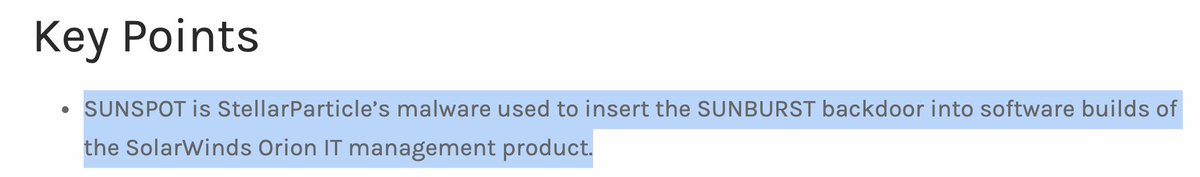
...should look at the behaviors used in this blog and consider how they could detect them in their own environment.
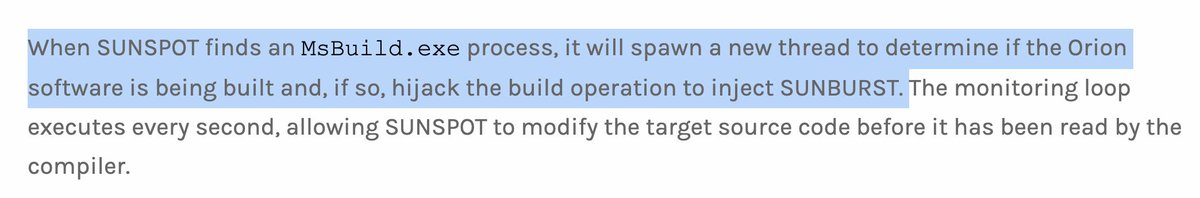
Again, showing pretty clearly that SUNSPOT was targeted at SolarWinds. It injects SUNBURST only if Orion software is being built. This is VERY TARGETED. 
Interesting tidbit here, they found some similarity to this blog: blog.xpnsec.com/how-to-argue-l… - to me this is a great example of why threat intel analysts need to work closely with researchers, because today's research is tomorrow's adversary tradecraft. 
Key takeaway from this section is "they were careful to sanitize the code." Honestly, I had to ask friends and do a bit of Googling on this section (not a computer scientist or developer...and that's okay). 
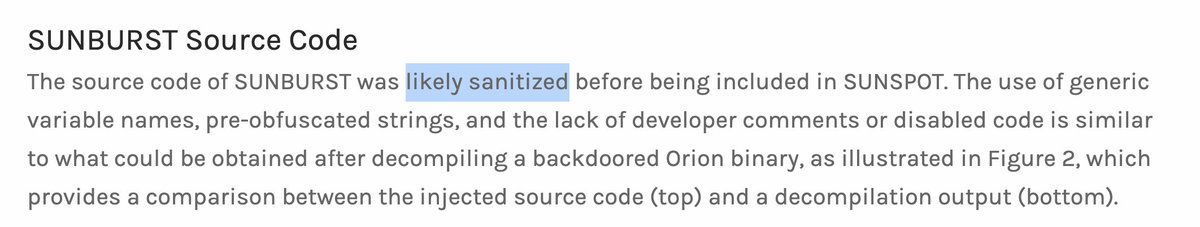
I had to look up pragma statements: en.wikipedia.org/wiki/Directive… - as a friend said, they're basically hints to the compiler, and in this case the hint is "stop putting out warnings for a bit". I understand this, because as I try to code stuff, I get very annoyed with warnings.😂 
This is a BEAUTIFUL summary. This is such a well-written blog. Nice work, @CrowdStrike! 

And hashes for the "hashes or it didn't happen" people. But like...unless you're SolarWinds...you shouldn't expect to see these. 
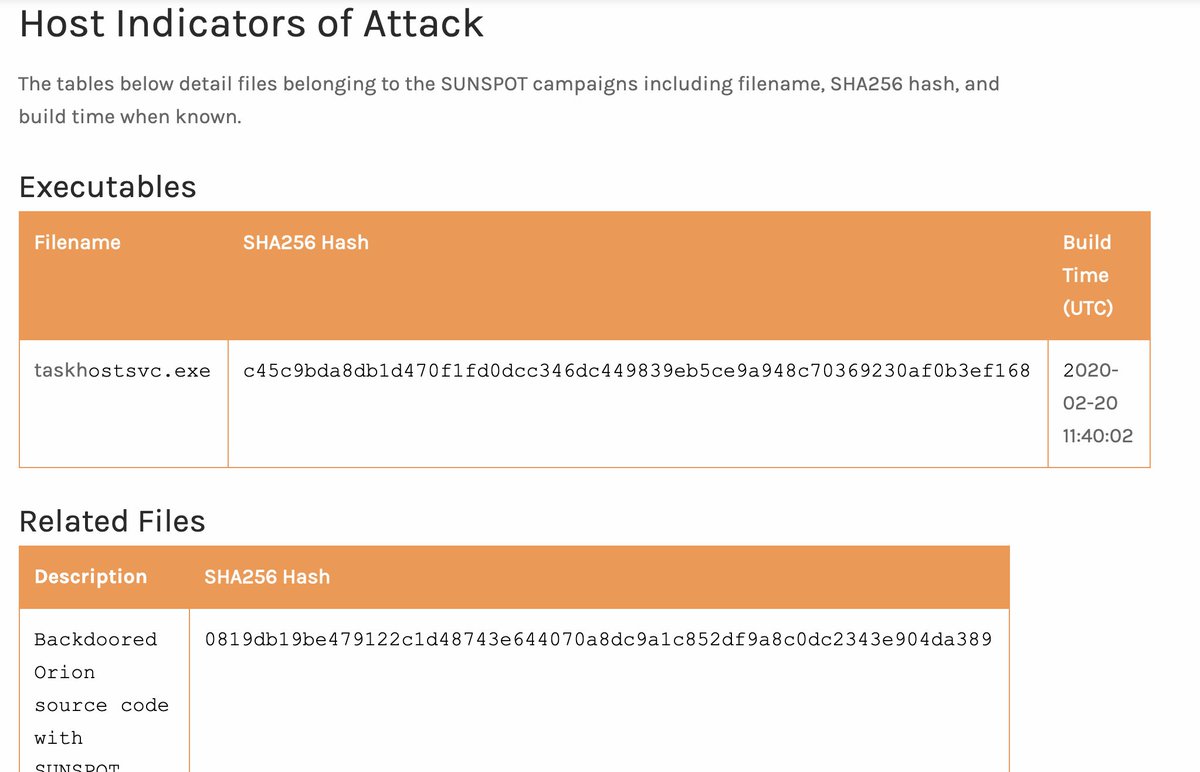
Yayyy YARA rules! Who's going to run them and post any VT links so we don't all have to burn retro hunts? 🙂 
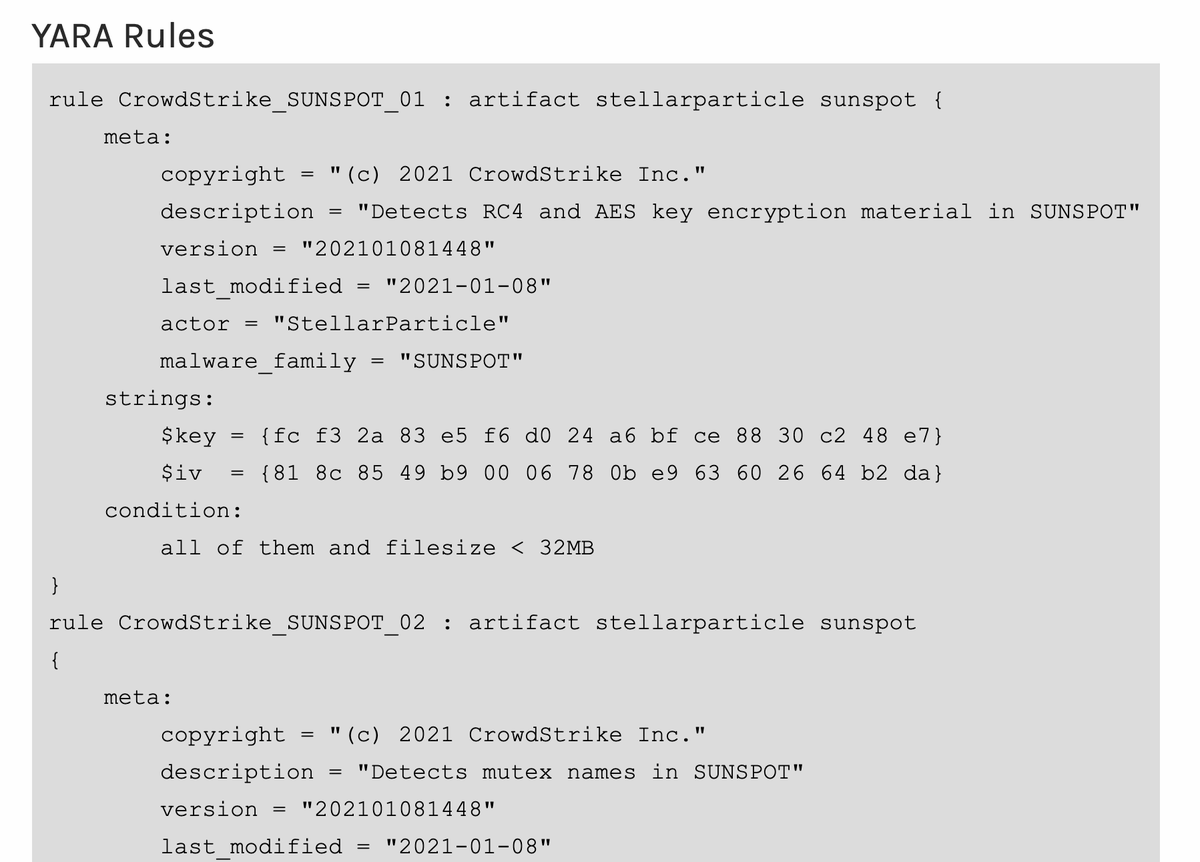
LOOK AT HOW THEY ADDED OBSERVABLES!!!! They didn't just list techniques!!!! I'm so happy I could cry. Plus the new @MITREattack tactics are in here! 

I need to eat dinner, but you should go read this too: orangematter.solarwinds.com/2021/01/11/new…
So much 🤦♀️. Here's the actual blog post. Sorry, I thought I put it in the first tweet!!! crowdstrike.com/blog/sunspot-m…
Adding on this well-phrased tweet from @KimZetter to highlight what's so fascinating about this technique. SUNBURST was injected during the build process - that's really clever.
https://twitter.com/KimZetter/status/1348787435635789824?s=19
Also wanted to highlight this important reply from @Adam_Cyber. While the specific hashes may not be widely useful beyond SolarWinds, the YARA rules certainly are, and the same techniques used by SUNSPOT could be used elsewhere in build processes.
https://twitter.com/Adam_Cyber/status/1348796180810125313?s=19
• • •
Missing some Tweet in this thread? You can try to
force a refresh