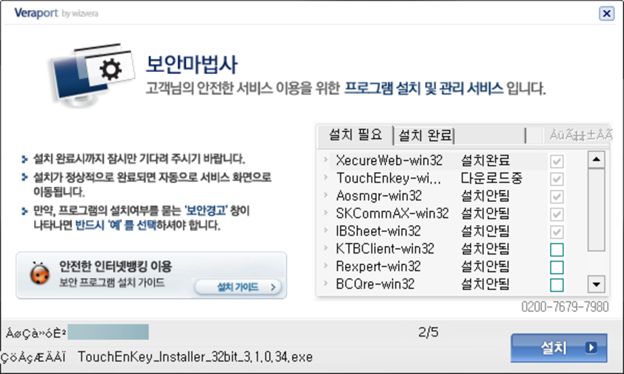
We have received a lot questions about the Silver Sparrow malware for macOS after a publication by @redcanary. #ESETresearch has investigated and found that, far from speculations about nation-state malware, it is likely related to adware and pay-per-install schemes. 1/10 

We have first seen Silver Sparrow in the wild early September. Our telemetry (although limited) showed under 50 instances of this threat, spread all around the globe. We have monitored the configuration file and never seen any actual payload delivered. 2/10
The fact that the configuration file is hosted in AWS S3 bucket means there is no way for the attackers to send different configuration to specific targets. S3 only supports serving static content and cannot generate a dynamic response based on IP or any request parameters. 3/10
One characteristic of Silver Sparrow is that it will uninstall itself in the presence of a ~/Library/._insu file. We found other malicious scripts, used in campaigns, that will refuse to install later staged if this file (or .sum) is present. 4/10 



We suspect that this file is created after a Mac has been monetized and no longer has value to the gang behind this malware. “insu” may be short for “installation successful”. 5/10
Creating the file on your system prevents infection for the current variant, but would be useless since the path will likely change now that is known publicly. The ecosystem for these campaigns of Mac malware is quite confusing. They are known to install multiple persistent 6/10
components. Our example infection chain relates to
👾Mughthesec (objective-see.com/blog/blog_0x20…)
👾Shlayer (intego.com/mac-security-b…)
👾Tarmac (blog.confiant.com/osx-shlayer-ne…) 7/10
👾Mughthesec (objective-see.com/blog/blog_0x20…)
👾Shlayer (intego.com/mac-security-b…)
👾Tarmac (blog.confiant.com/osx-shlayer-ne…) 7/10
It’s also interesting to note that everything in the campaign described is hosted in AWS. They use CloudFront for CDN, S3 for storage, and API Gateway for dynamic content. PPI campaigns has been a thing on Mac for many years. 8/10
Plain text IoCs:
1807eb8c3719c9faa0210d8a5df2068d2c89d90d
f59602e043f9788b5924f8e1c225483f934bf5d8
8abb0defedb0eddb48a14a2c2721c53c8020ad00
8dbc48768edd795b1446e04e5cc2fd9dbf196410
6dcd11b70c535dca09208aaf8168d962a9daa13d
9b0fa382642c721b7bab4891b31d640d9a6e4b33 9/10
1807eb8c3719c9faa0210d8a5df2068d2c89d90d
f59602e043f9788b5924f8e1c225483f934bf5d8
8abb0defedb0eddb48a14a2c2721c53c8020ad00
8dbc48768edd795b1446e04e5cc2fd9dbf196410
6dcd11b70c535dca09208aaf8168d962a9daa13d
9b0fa382642c721b7bab4891b31d640d9a6e4b33 9/10
PDF of event chain: welivesecurity.com/wp-content/upl… #ESETresearch 10/10
• • •
Missing some Tweet in this thread? You can try to
force a refresh