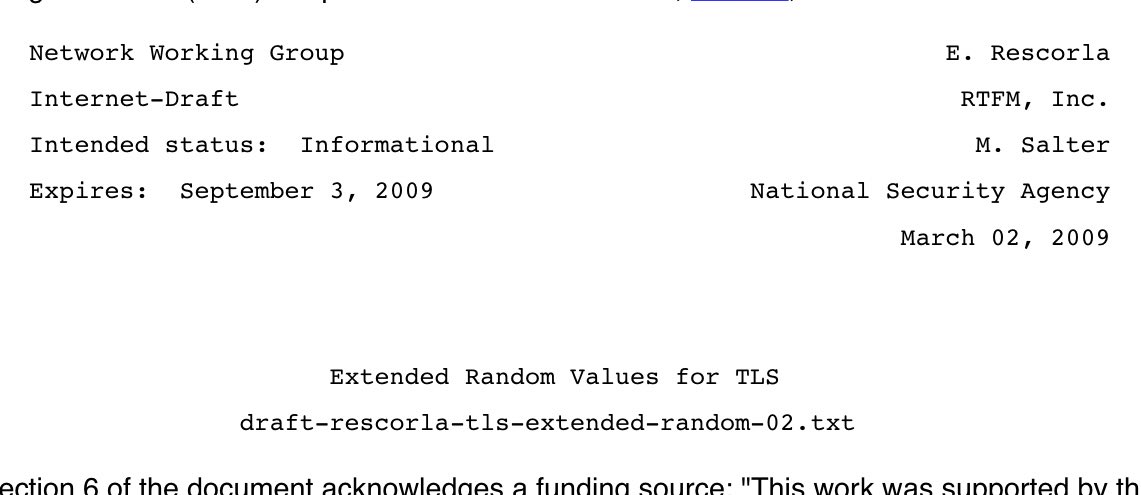
Me: I’ve felt super productive this pandemic!
Department: Doesn’t look like it.
Me: *vanishes into a tailspin of insecurity*
Department: Doesn’t look like it.
Me: *vanishes into a tailspin of insecurity*
Me: surely everyone else has been a little slower on publishing during the pandemic.
Me: *stupidly checks the websites of my theory friends*
Also me: *vanishes into a tailspin of insecurity*
Me: *stupidly checks the websites of my theory friends*
Also me: *vanishes into a tailspin of insecurity*
Advice to new faculty: it is very important to make a friend in your field who will reassure you about why everyone else’s work is easy and yours is both harder and uniquely important. This does not need to actually be true for it to help.
Also, *never* check the websites of your theory friends. Seriously, what are these people eating.
• • •
Missing some Tweet in this thread? You can try to
force a refresh