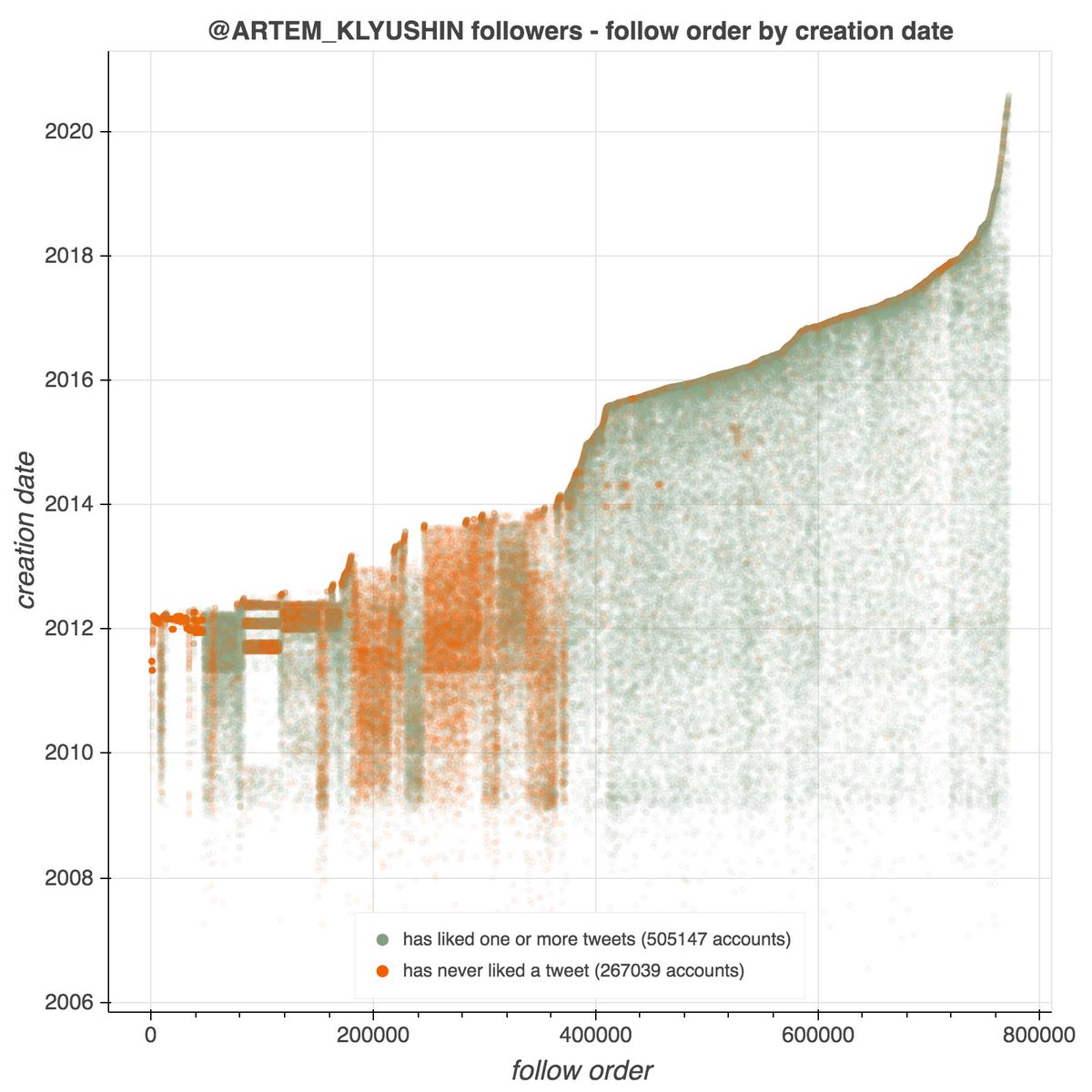
It's a Tuesday in June, and a whole ducking lot of newly-made Twitter accounts are "requesting faucet funds on the #Goerli #Ethereum test network" in a spammy repetitive fashion. #TuesdayAstroturf
cc: @ZellaQuixote
cc: @ZellaQuixote

These tweets are from a network of (at least) 1281 accounts created between June 22 and June 29, 2021. Each account has tweeted exactly once, and all tweets are identical other that the cryptocurrency wallet address. All tweets were (allegedly) sent via the Twitter Web App. 




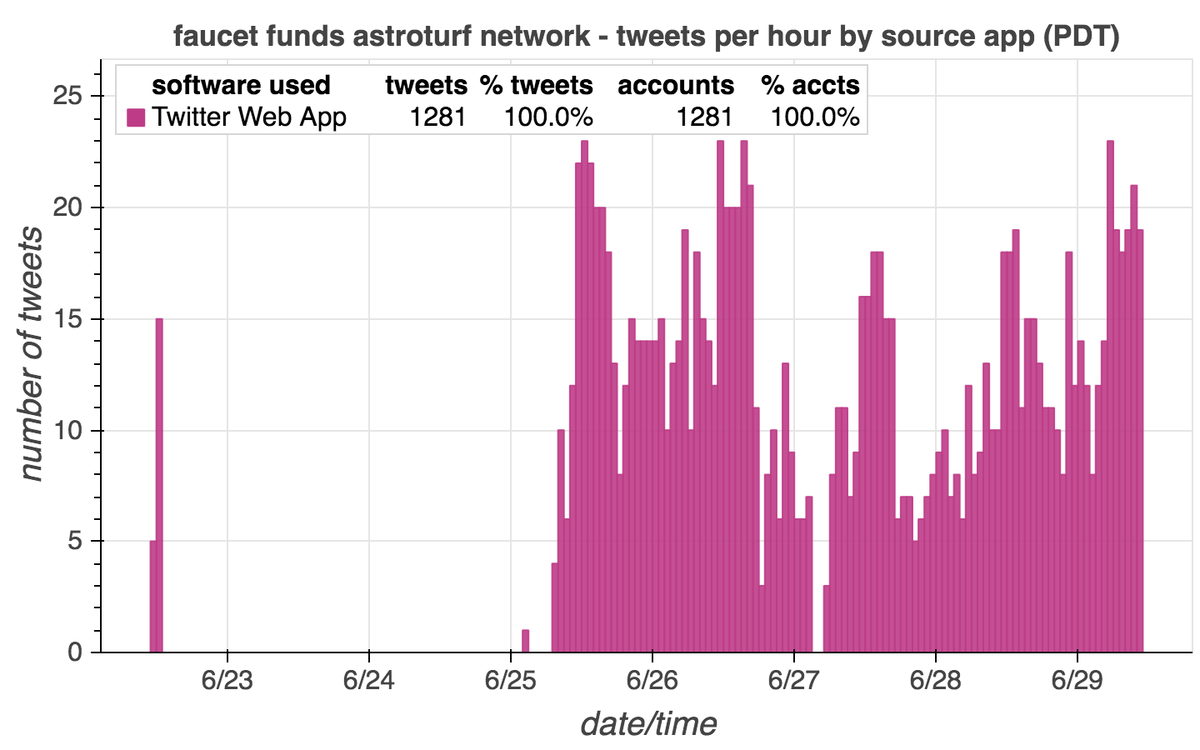
Each account in the network posted its one and only tweet shortly after being created, with an average of 74 seconds and median of 68 seconds between account creation and tweet time. The longest gap between creation and tweet was slightly over ten minutes. 

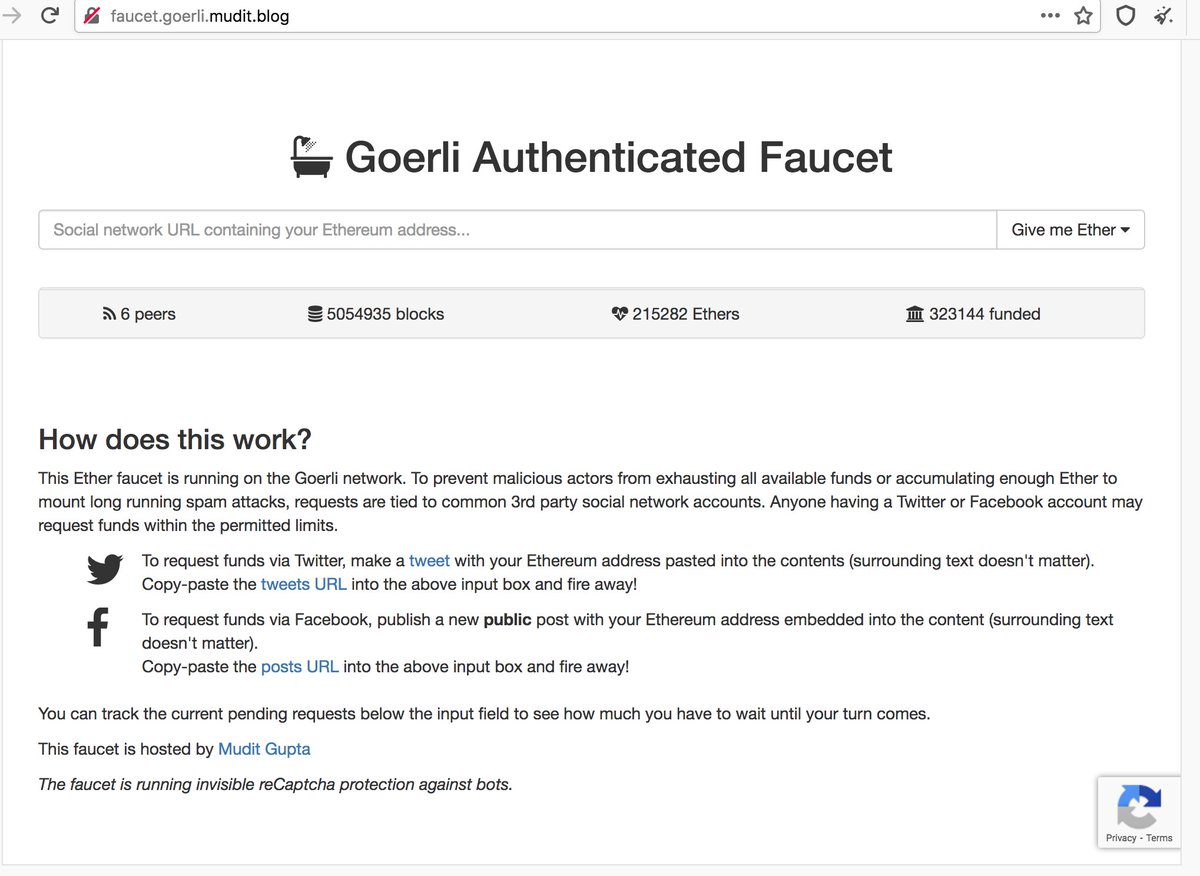
These tweets appear to be an attempt to game a cryptocurrency giveaway hosted at faucet(dot)goerli(dot)mudit(dot)blog. (As always, caution is recommended when visiting unknown websites linked by spammy accounts.) 
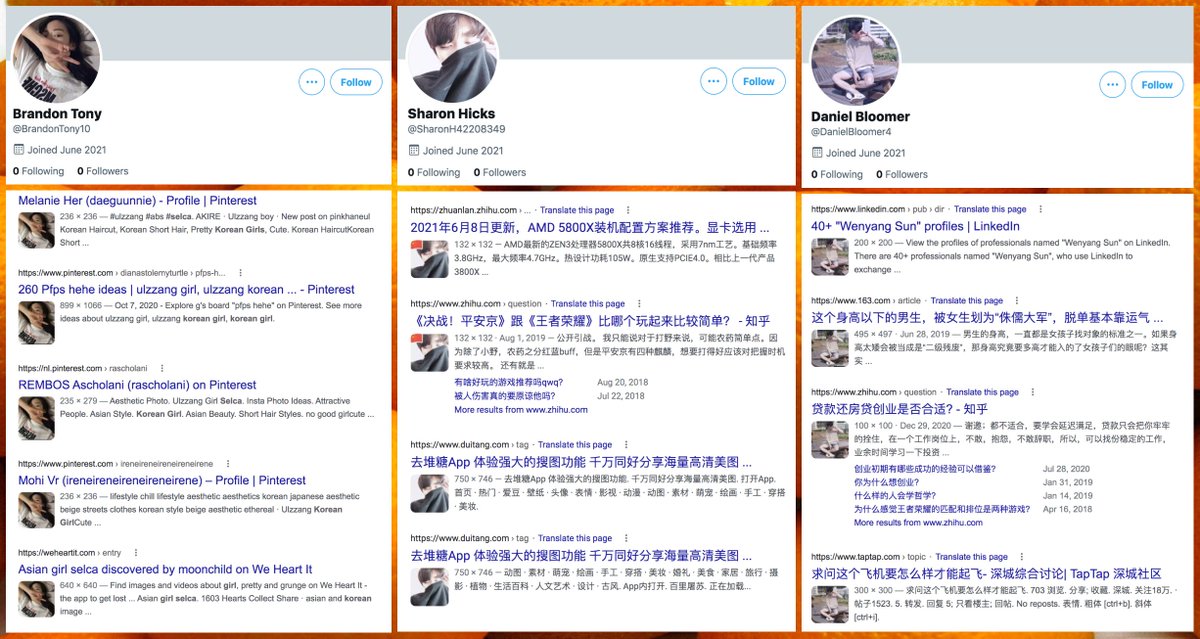
The accounts in this network use photographs of people as their profile pics, but the pics are stolen, as tends to be the case with spammy botnets. Google and TinEye were more effective than Yandex for finding previous uses of these images on the Internet. 
• • •
Missing some Tweet in this thread? You can try to
force a refresh